- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Company Insights
Summary:
As a follow-up to the March 16th threat advisory which was based on the observations of the Securonix Threat Reasearch Team, around the global emergency caused by COVID-19. We continue to search the wild for new threat vectors and indicators. As time progresses, we have started to see a new trend of threat vectors and scenarios that have proven to be challenging to security operations teams. This advisory details the latest development and updates around the research, findings, and recommendations from the Securonix COVID-19 Task Force.
Observation #1: Malware Domain Activity
With the notable increase in the number of domains created using the words “corona” or “covid19” , the Securonix team confirmed that the following domains are malicious:
insiderppe[.]cloudapp[.]net, coronavirusstatus[.]space, coronavirus-map[.]com, blogcoronacl.canalcero[.]digital, coronavirus[.]zone, coronavirus-realtime[.]com, coronavirus[.]app, bgvfr.coronavirusaware[.]xyz, coronavirusaware[.]xyz, corona-virus[.]healthcare, survivecoronavirus[.]org, vaccine-coronavirus[.]com, coronavirus[.]cc, bestcoronavirusprotect[.]tk, coronavirusupdate[.]tk, Coronavirusapp[.]site, Gulf-builders[.]com, marchadvertisingnetwork*[.]com
Traffic has been observed on a subset of these domains at a few customer organizations. Upon further research and collaborated investigations with some of our customers, we have noticed attempts at accessing the registry settings for applications installed on the endpoints with an intention of stealing credentials and other information stored in the user browsers.
Another domain featured in the Securonix advisory “coronavirusapp[.]site” was also found to distribute a fake Coronavirus outbreak tracker app (Covid 19 Tracker), which provides users with tracking and statistical information about COVID-19 and heat-map visuals. However, upon installation and execution, the application locks the screen of the device and shows a ransom note claiming that the phone has been encrypted, and coercing the victims to pay $100 in Bitcoin within 48 hours. Our research reveals that the author of the malware had implemented no obfuscation in the source code, and we find the decryption key to recover the contents as
“4865083501”.
Securonix Threat Research predicts the increase of ransomware and keen on researching on “Maze threat actors“. Maze and other ransomware have struck again recently, stealing data from healthcare and hospitals and then publishing it online to get them to pay the ransom demanded.
Recommended Actions:
- Enable proactive block rules on firewalls, proxy devices, and other in-line security tools to stop communication with these domains.
- Reset passwords for the users who have visited such domains.
- Over the past few days, we have seen some of these domains categorized in Virustotal and other Proxy/Firewall solutions. Some of the malicious-phony COVID-19 domains are new, relying purely on community-based threat intelligence services may not provide you with complete visibility. We have had investigations closed as non-concerns at one engagement based on threat intelligence feeds. The categorization for one such domain identified earlier by Securonix “coronavirus-map[.]com” has since changed from “Miscellaneous/Unknown” to “Phishing” as of 3/18/2020. Our recommendation is to initiate a block action on some of these domains irrespective of the Threat Intelligence score.
Observation # 2: Phishing Activity
On the phishing front, Securonix detected multiple campaigns and identified emails impersonating official organizations, containing updates and recommendations connected to the disease, and in certain cases, including malicious attachments. For instance, we noticed an organization that detected up to five different phishing campaigns in the first week of officially notifying employees to work remotely. Legitimate-looking emails containing embedded links/attachments were received from domains such as:
antiviruscorona[.]icu,
anticoronaviruspro[.]icu,
coronaclean[.]icu,
coronasolve[.]xyz,
coronaviras[.]rest
Other typo-squat variants of these domains have also been on the rise in the last few days, and organizations have not been able to be proactive in monitoring or blocking these domains, for fear of not communicating information that could be valid and relevant about the pandemic.
Recommended Actions:
In the cases above where blocking is prohibitive, enabling use cases that track increased activity to these newly registered domains or rare domains, and any signs of beaconing or C2-like behavior, can be an effective way of identifying early indicators of suspicious activity.
Observation #3: Remote/VPN Activity
Greater challenges arise with this increased activity such as a higher volume of logs observed in 2FA/MFA application logs. At one of the organizations, we have noticed an unusual number (8-10x increase) of MFA enrollment requests in just the last 72 hours.
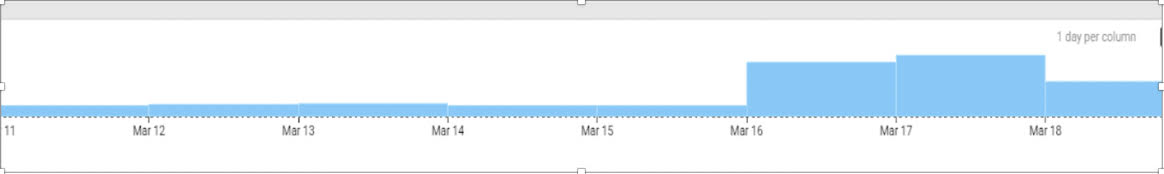
In addition to the above example, employees and remote workers (contracted vendors and partners) have also bombarded technical support teams to assist them in this process of enrollment. Attackers have also started to identify this as a potential vulnerability, and have begun impersonating users (social engineering techniques) based on the basic information they extract from LinkedIn and other platforms, and use this information to trick support teams into allowing “one-time passcodes” ,or in some cases registering their devices for MFA approvals.
In one such case, Securonix identified a successful attempt at enrolling a device for MFA approvals from the Czech Republic for a user based out of the United States. In another similar scenario, four instances of accounts possibly being compromised were found where devices were registered to accounts that allowed users to push their own MFA approvals. In one case, we noticed a threat model alert involving a user account coming in simultaneously from a Windows 7 machine as well as from a MacBook Pro. Approvals authorized from devices with phone numbers – +91 XXX XxxxxxX as well as 213-Xxx-xxx3 quickly alerted the analysts to reach out to the user to get the accounts reset.
Recommended Actions:
- It is vital that organizations collect and enable use cases which identify any behavior anomalies with geo-locations associated to user accounts with the mode of MFA used, as well as the devices from where these accounts are seen accessing your network.
- We also recommend a training refresher to all support desk teams to protect against scammers gaining access to the environment via social engineering.
- Due to the multiple nation-wide initiatives to encourage users to work remotely, we have noticed up to 50-100% increase in the volume of VPN and other remote authentication logs. In these scenarios, it is extremely important to monitor not just VPN behavior anomalies, but all activity following VPN or remote authentication.
Observation #4: User Account Misuse Activity
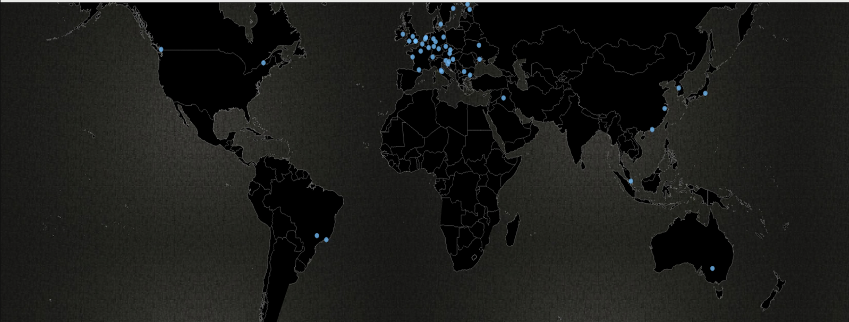
In one scenario, as evidenced from the image below, Securonix detected a contractor account authenticating successfully over VPN from multiple different countries. The user account was seen from locations that are typically unusual to the parent organization. There was a total of 26 different countries from where this account was used in the last 14 days. Considering the recent shift toward working remotely due to the COVID-19 global pandemic, this account could have been compromised, and resulted in usage from different geo-locations.
At another organization, Securonix identified a user authenticating from two locations within a short time span, United States and Germany, of which Germany was seen as a rare country login for the user. Additionally, the user was then observed aggregating a large number of files over the content management system “SharePoint”, which was followed ultimately by the user exfiltrating data over email to a recipient domain that included the user’s last name. This scenario was identified while monitoring anomalies over remote authentication, content management systems, and email. A threat model tied these scenarios together, which is where identity-based correlation helps identify cases of Insider Threat/IP theft spanning across multiple disparate data sources.
We have detected six confirmed cases in the last two weeks with regard to password sharing scenarios, which has made it relatively easy for the SOC given the travel restrictions imposed by many countries. In the other scenario, an employee was taking advantage of the work from home policy by traveling to a French Polynesian island and using a Private VPN to log into a USA location, where he would then log into the corporate environment.
At another organization, Securonix identified a user authenticating from a rare geo-location which was attributed to a blacklisted IP address. Following this anomalous authentication, the SOC is still investigating the scenario. We have seen an increase in custom messenger applications like the following:
- Line
- Miranda IM
- Telegram
These applications are being used more frequently to make use of the flexible and free teleconferencing and instant messaging options that these platforms provide. There has been at least a 5-7% increase in custom IM/teleconferencing applications that were installed in the last week by employees, due to scalability challenges with enterprise applications. This change has posed the risk of users installing unauthorized or unsigned versions of these applications on their corporate endpoints.
Another example of our observation occurred at an organization where a non-enterprise version of a popular IM application launched command prompt (cmd.exe), which is unusual for these types of applications. The SOC is still investigating this scenario. The lack of endpoint solutions on some of these BYODs has made this investigation extremely challenging.
Recommended Actions:
- Enable user-based monitoring use cases to look for suspicious login patterns based on geography and frequency of logins.
- Reiterate guidelines on password sharing and misuse with all users, especially given that the work from home reality is likely here to stay for a while.
- Enforce strong endpoint controls to prevent use of unauthorized or unsigned versions of custom messenger applications on corporate endpoints.
Other Security Monitoring Recommendations:
In addition to the recommendations above, the Securonix Threat Research Team suggests monitoring the following data sources and activities:
- With the majority of the workforce working from home, VPN security has now become paramount. VPN ports associated with VPN like OpenVPN (1194) or SSL VPN (TCP/UDP 443, IPsec/IKEv2 UDP 500/4500) needs to be carefully monitored. We strongly recommend enabling a multi-factor authentication (MFA) solution to protect VPN accounts, and integrating those logs to your analytics-driven SIEM/UEBA will be imperative. The Securonix Threat Research Team predicts possible DDOS attacks on VPN servers in coming weeks; a further advisory will be issued in forthcoming weeks.
- We strongly urge integrating EDR (endpoint) logs to apply newer threat models such as process executions for unusual parent/child process relationships, and network connections made by processes, especially over DNS and HTTP(S), as well as any file creation/modification, to speed up the investigation and remediations. Securonix also recommends that organizations implement an application locker or a centralized SCCM process to control or restrict custom applications from being installed on corporate endpoints.
- In addition to the data sources covered in this update, the Securonix Threat Research Team recommends that customers closely monitor activities on the following devices:
- Cloud infrastructure and application
- Authentication devices
- Business critical applications
- Identity and access management tools
- Misuse of devices and user permissions is the biggest challenge in remote/work from home scenarios. The Securonix Threat Research Team recommends correlating the activities with user and asset information to establish that only authorized actors and entities are active in your environment.







