- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
By Augusto Barros, VP, Security Evangelist, Securonix
We have been putting a lot of work on reengineering our SOAR product, primarily with the goal of making it an integral part of our core products, Next-Gen SIEM and Open XDR. That means having SOAR capabilities that are not pieced together and bolted on to the SIEM but having them become part of the SIEM. The difference is subtle, but it is there, and it is really a game changer. Here is a picture that illustrates what we are talking about:
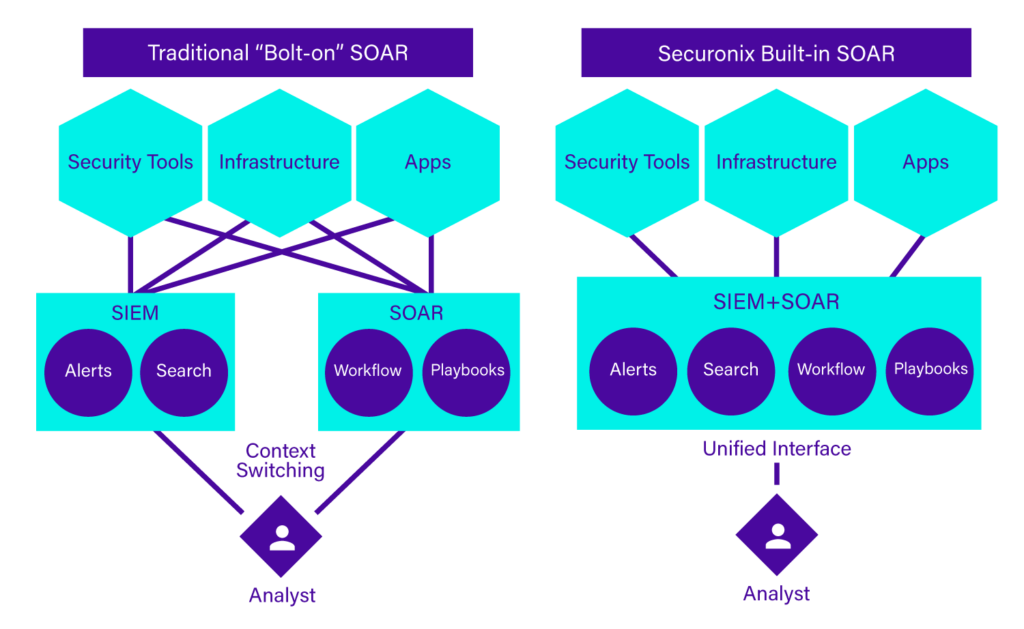
If we look back at how the Securonix platform has evolved, we will see that something similar happened with UEBA. The SIEM and UEBA capabilities merged into a single solution, instead of an architecture where the SIEM and UEBA are integrated by connecting one to the other. These architecture choices are deliberate and follow the evolution of our solutions. We are creating a platform, not a portfolio of integrated products.
Why does it matter? It matters a lot when we look at our primary objectives: Detect and respond to more threats, in a more efficient and cost-effective way.
Let’s look at the convergence of SIEM and UEBA. I can provide two examples of “typical” SIEM and UEBA use cases:
- SIEM: Generate an alert when an internal host establishes a connection with a known bad IP address.
- UEBA: Generate an alert when a user authenticates from an unusual location at an unusual time.
Pretty simple, right? But what if these two events are related to the same threat? The same attack can trigger these two alerts as it moves through the kill chain. If these systems are operating independently, how do you know these alerts are related to the same attack? It makes sense to have these events in a single place so they can be tied together, using an entity such as the user as the correlation point. Putting this integration in place is not easy; you need to forward the events from one system to the other, ensure the correlation entities are aligned in both sides (user identification is the same, or there is a dictionary or lookup table in place to do that), and there is also a way to determine the importance of each event coming from the upstream system.
It doesn’t stop there. The downstream system will present this chain of correlated events to the analyst; what if they want to drill down on those events, or expand their investigation to events related to the affected entities? Some data will be in one system, some on the other. Wow, it seems that integrating a SIEM and a UEBA solution is not simple!
That’s why it makes much more sense to make them the same, unified solution. There is no need to define how they will talk to each other, because there is no “other.” A unified SIEM and UEBA solution (I will call it next-generation SIEM, or NGSIEM, when referring to a converged, instead of integrated solution) has the tools in place to implement use cases from both spaces, so it becomes far easier to perceive that certain observables are related to the same (malicious) activity. I believe this is one of the major reasons why Securonix captured the “most visionary” position in the Gartner Magic Quadrant for SIEM. While others have built, or acquired, two separate components, we made one that does the job of two, in a much better way.
Now we are doing the same with SOAR. The benefits may not be as obvious as in the case for SIEM and UEBA, but they are there. First, the analyst will have one less tab open on their browser. Let’s look again at an example; how integrated, but still separate NGSIEM and SOAR solutions would normally operate:
- The NGSIEM generates an alert when suspicious activity indicates an ongoing threat related to a user.
- On the SOAR side, the alert comes from the NGSIEM and triggers a playbook, which collects additional evidence and context for enrichment purposes. It shows everything to the analyst, who must decide if a response playbook should be executed.
- The analyst is still not sure, so they go back to the NGSIEM (Pivot 1 – click!) to look at some additional logs. They confirm it is indeed a threat. But they also find out about a couple of other affected entities, so they write the IP addresses and usernames on a piece of paper (!)
- Back to the SOAR UI (Pivot 2 – click!), the analyst proceeds with the execution of the response playbook. But what about those other entities they identified during the investigation on the SIEM? They search for the right playbook to use and execute it for each entity.
You may think I’m exaggerating with this “writing on a piece of paper” part, but investigations will often find new evidence at points where the current response playbook is past the point where it can receive input. That’s just one example of “out of the standard process” situations that may require the analyst to move back and forth between the SOAR and the NGSIEM.
But, again, what if the SOAR is a fused element of the NGSIEM? In the scenario above, the analyst never has to leave the single, consolidated UI. As they investigate, any entity on the screen that can be used as input can be pushed as such to a playbook action. The analyst becomes more efficient, with less friction, their job less painful and the incident response faster.
Check how we put these two capabilities sets elegantly together in the same UI:
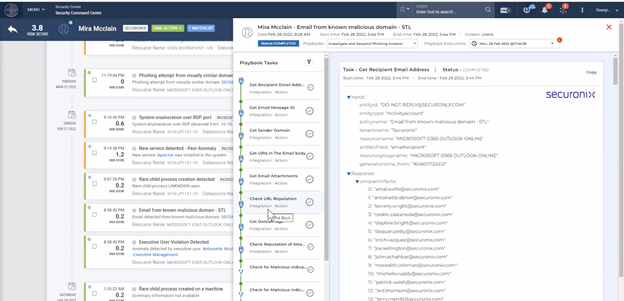
A solution with this broader but unified set of capabilities required by every security operations team is, in fact, a full-blown security operations platform. It is unlikely that we will ever be able to deliver all pieces of the security infrastructure puzzle, especially those systems at the edge, such as endpoint, network, or cloud security tools. Integration with external components is very important as they act as telemetry providers and also as response actors. But consolidating the analytics, orchestration, and response capabilities reduces context switching and the complexity of integrations. You integrate the edge tools with the platform, and it’s done. No need to integrate each one of them with a SIEM, an UEBA, and a SOAR.
Finally, this consolidated platform allows us to have detection and response actions as part of an end-to-end set of content. Vendors such as Securonix can codify much more domain knowledge in out-of-the-box content, reducing time to value for the solution and increasing the efficiency of the customer’s security operations team.
Analyst firms have been actively discussing the evolution of threat detection and response. New acronyms and terms are everywhere: XDR, SOAPA, SIAM, TDIR, just to mention a few. But paraphrasing Shakespeare (achievement unlocked!), what’s in a name? That which we call a SIEM by any other name would perform as efficiently. And that’s what we aim to deliver: threat detection and response efficiency.
Related Articles
Rethinking SOAR: Why Automation Needs To Be an Innate Characteristic, Not a Bolted-on Afterthought
Built-in, Not Bolted On: Experience a New Kind of SOAR at Securonix







