- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs
Threat Research: Den Iuzvyk, Tim Peck
Introduction
Attacks against ICS (industrial control system) environments are on the rise and several new variants have been identified targeting the Ukrainian power infrastructure. ICS controls are heavily used in security-hardened SCADA environments which would require specialized SCADA-specific malware for the threat actor to accomplish their goal.
The security company ESET, working closely with CERT-UA identified the malware and performed an initial analysis of the first identified variant. Some time later, other variants began to emerge. Each variant appears to be targeted towards specific environments as the usage of hard-coded IP addresses are present, which we’ll discuss later in the detailed analysis portion of the article.
The malware used in these attacks leverage a combination of Industroyer2 and CaddyWiper which are aimed purely at causing destruction by wiping affected systems. Industroyer (also known as Crashoverride) is an ICS-targeted malware first discovered when it was used against Ukraine’s power grid on December 17, 2016. Industroyer2 appears to be the next variant iteration and was seen this month by CERT-UA and ESET researchers attacking high-voltage electrical substations in the same region.
Attack Chain Overview
The main purpose of the malware is aimed at disruption. The wiper malware is designed to destroy affected systems as quickly as possible. The usage of multiple wipers is leverage depending on the target OS. For Windows ICS systems, the combination of Industroyer2 and CaddyWiper are used and on Linux and Solaris systems, ORCSHRED, SOLOSHRED, and AWFULSHRED are used.
The overall attack chain is detailed in Figure 1.
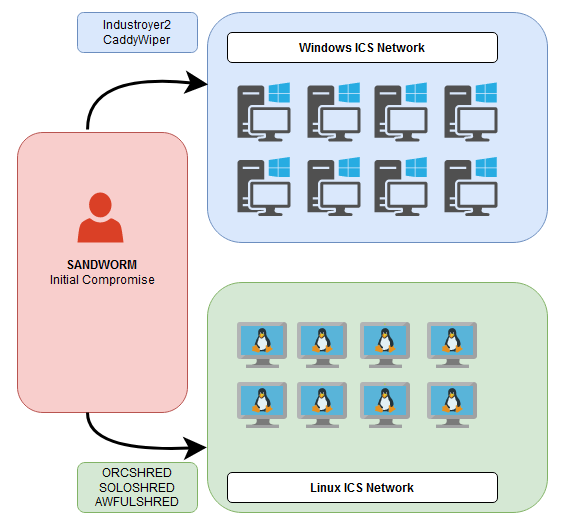
(Figure 1)
Initial Infection
At this point, the initial infection by Sandworm is still unknown. The attackers were able to infiltrate the ICS network from the IT network. Once persistence is made into the network, wiper malware will be deployed onto the affected Windows domain controllers and spread via GPO as a scheduled task.
Detailed Analysis: CaddyWiper
CaddyWiper was first discovered earlier this year targeting Ukrainian banks. Its main purpose is to quickly and stealthily wipe entire systems, including the boot loader thus rendering the entire system useless.
CaddyWiper is deployed via GPO to affected systems in the domain. Once executed as administrator, the system will immediately crash, generally between 5 and 20 seconds.
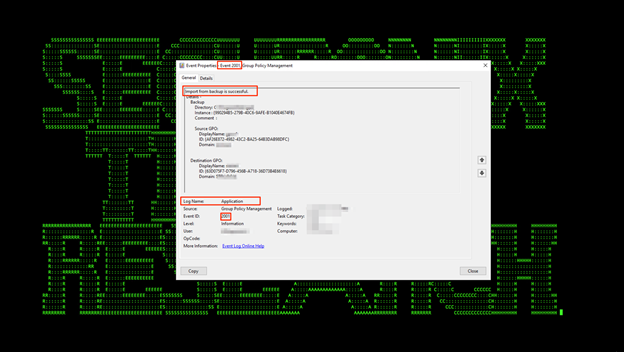
(Figure 2)
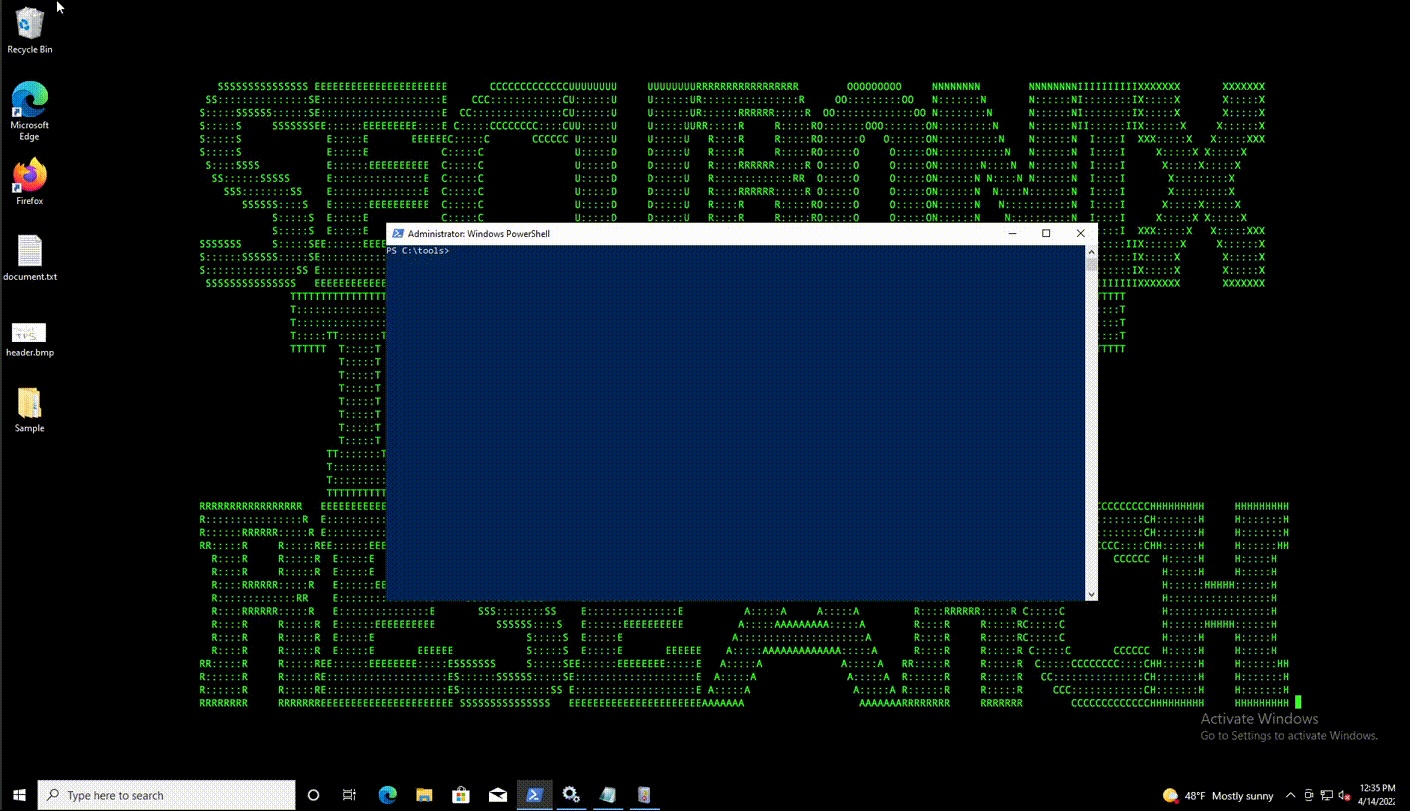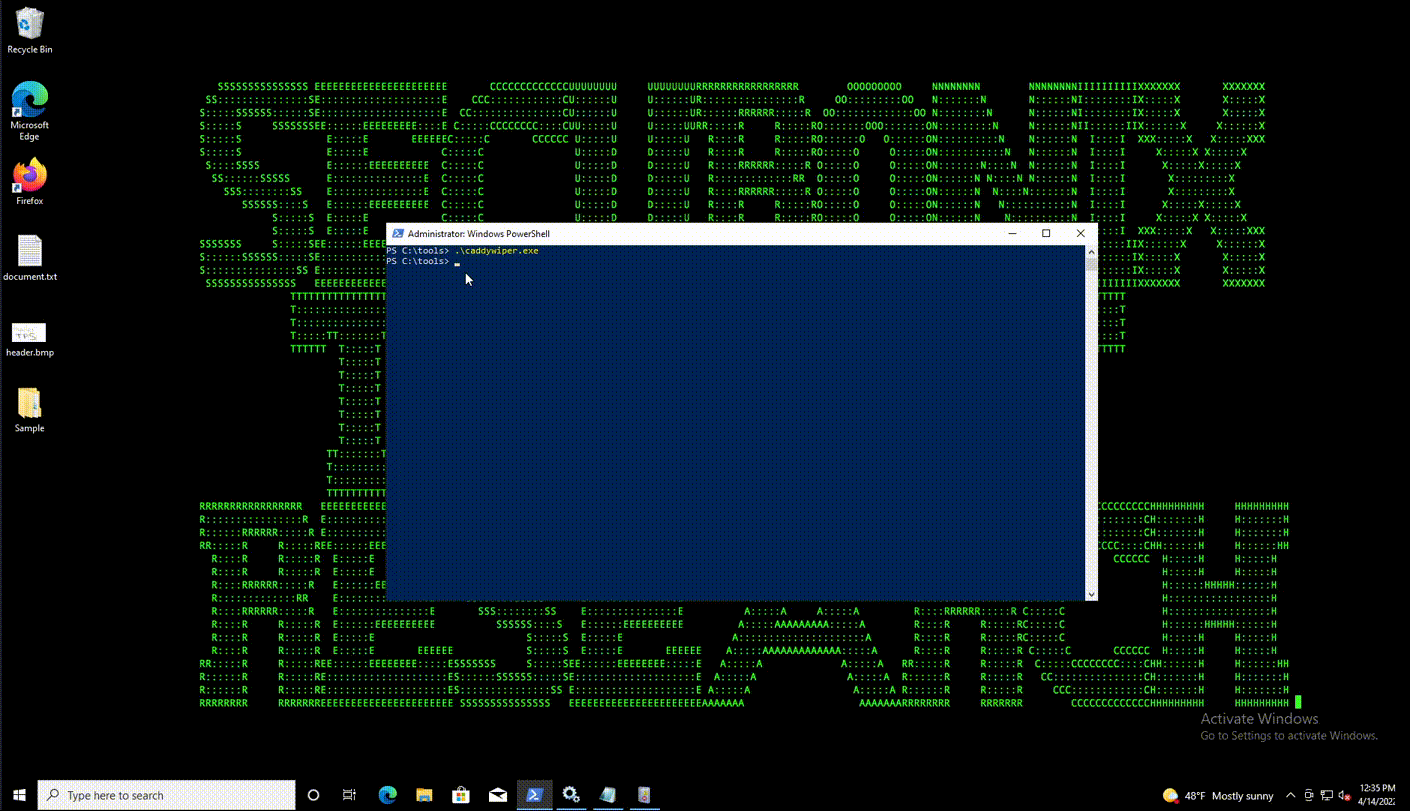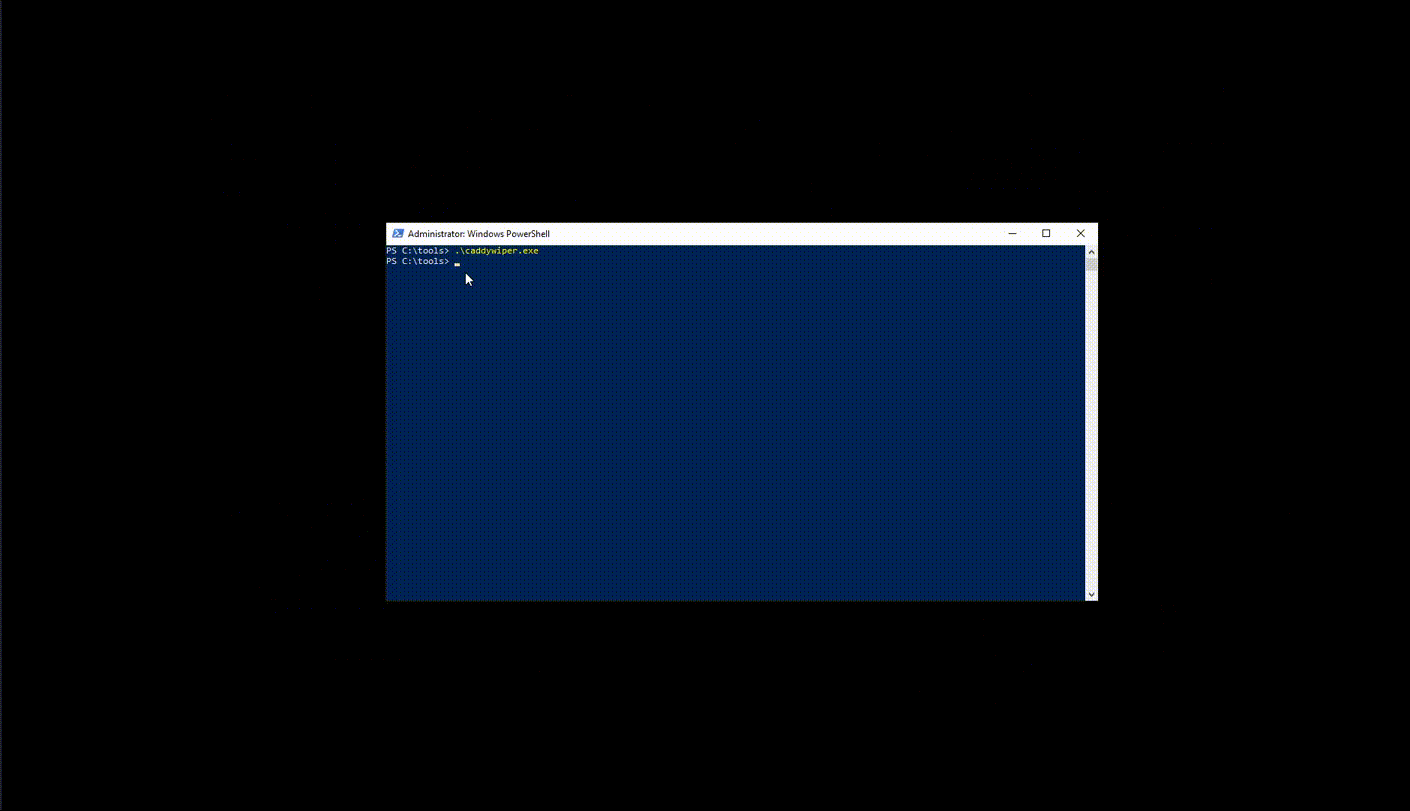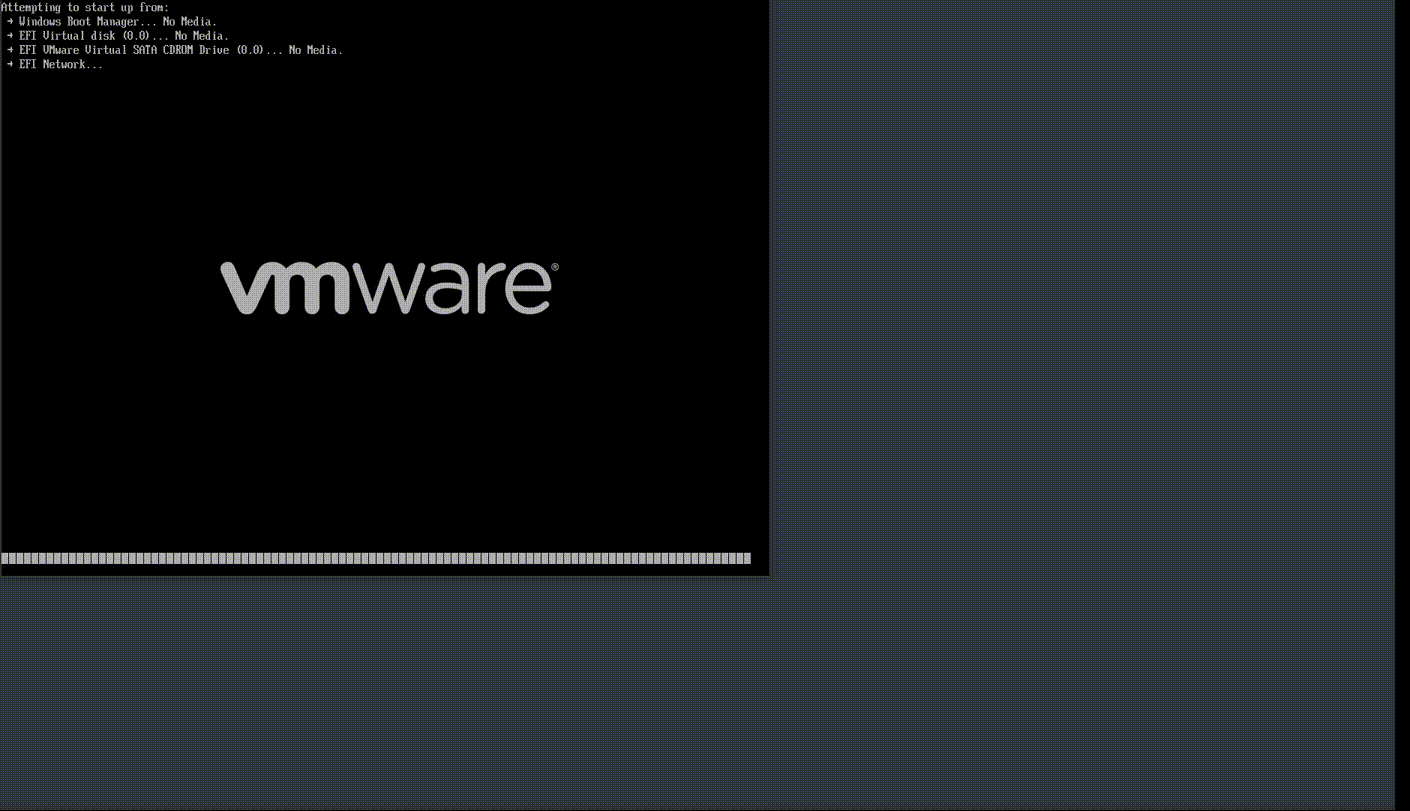
We can see how quickly the malware works on a Windows 10 virtual machine in Figure 3 below. Notice now after the system crashes, Vmware finds no boot device, confirming that the boot loader was indeed wiped.
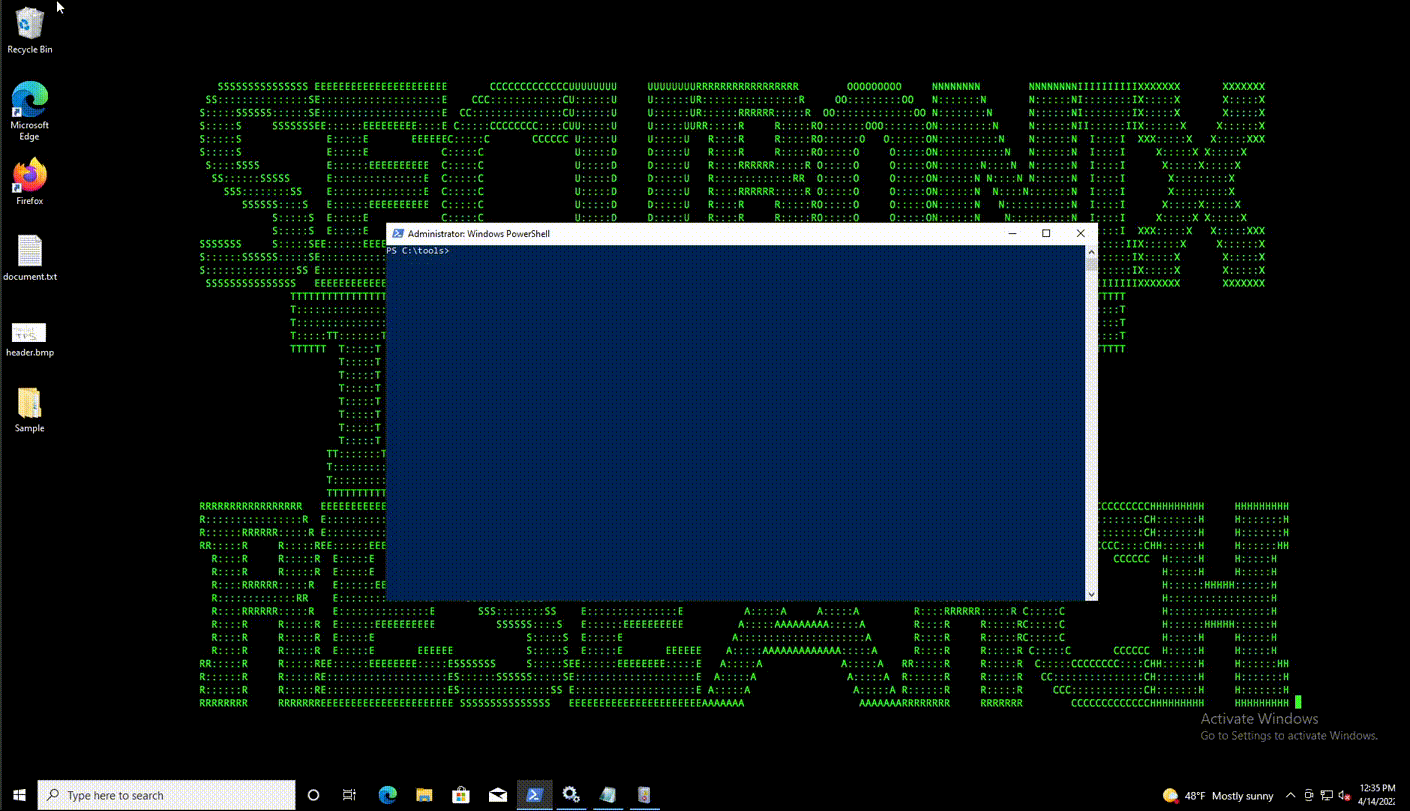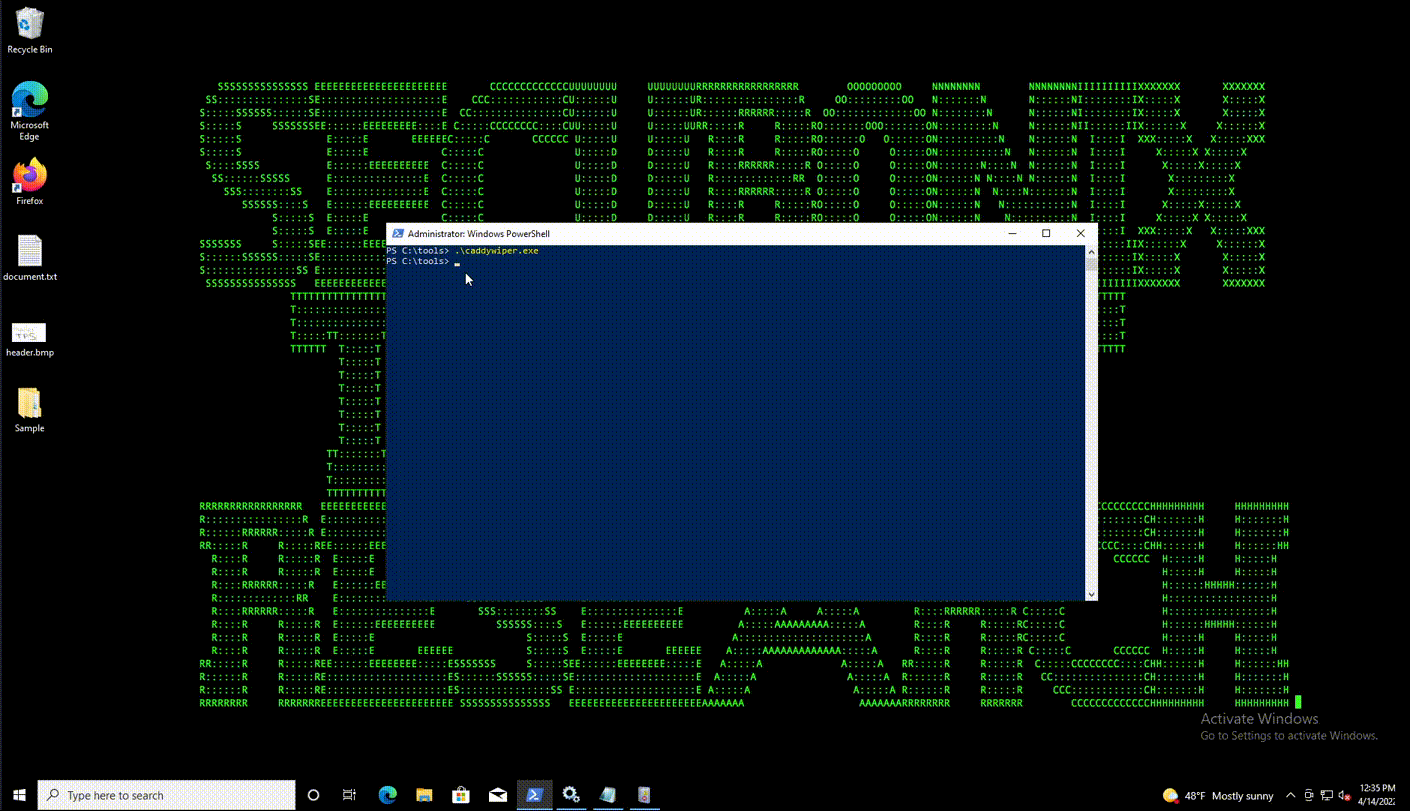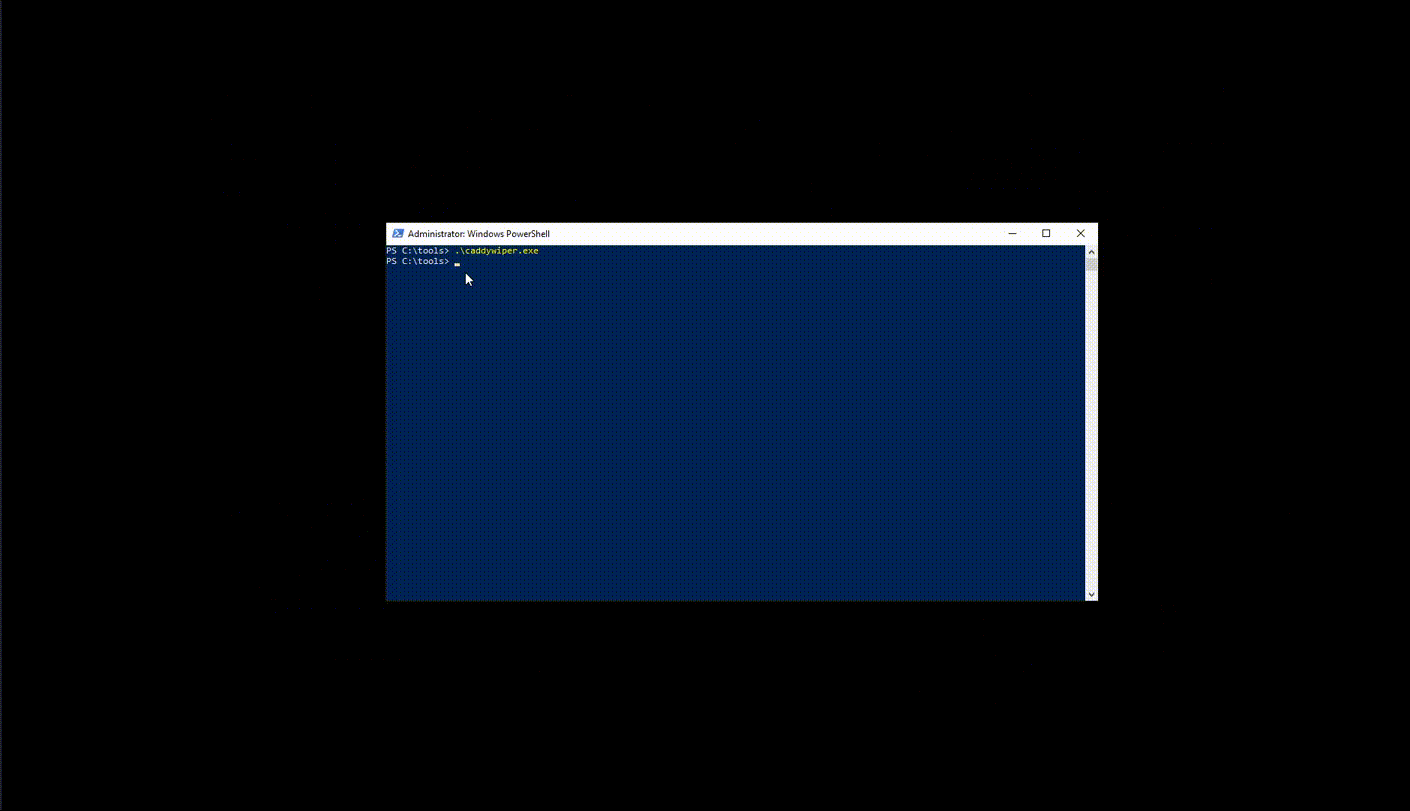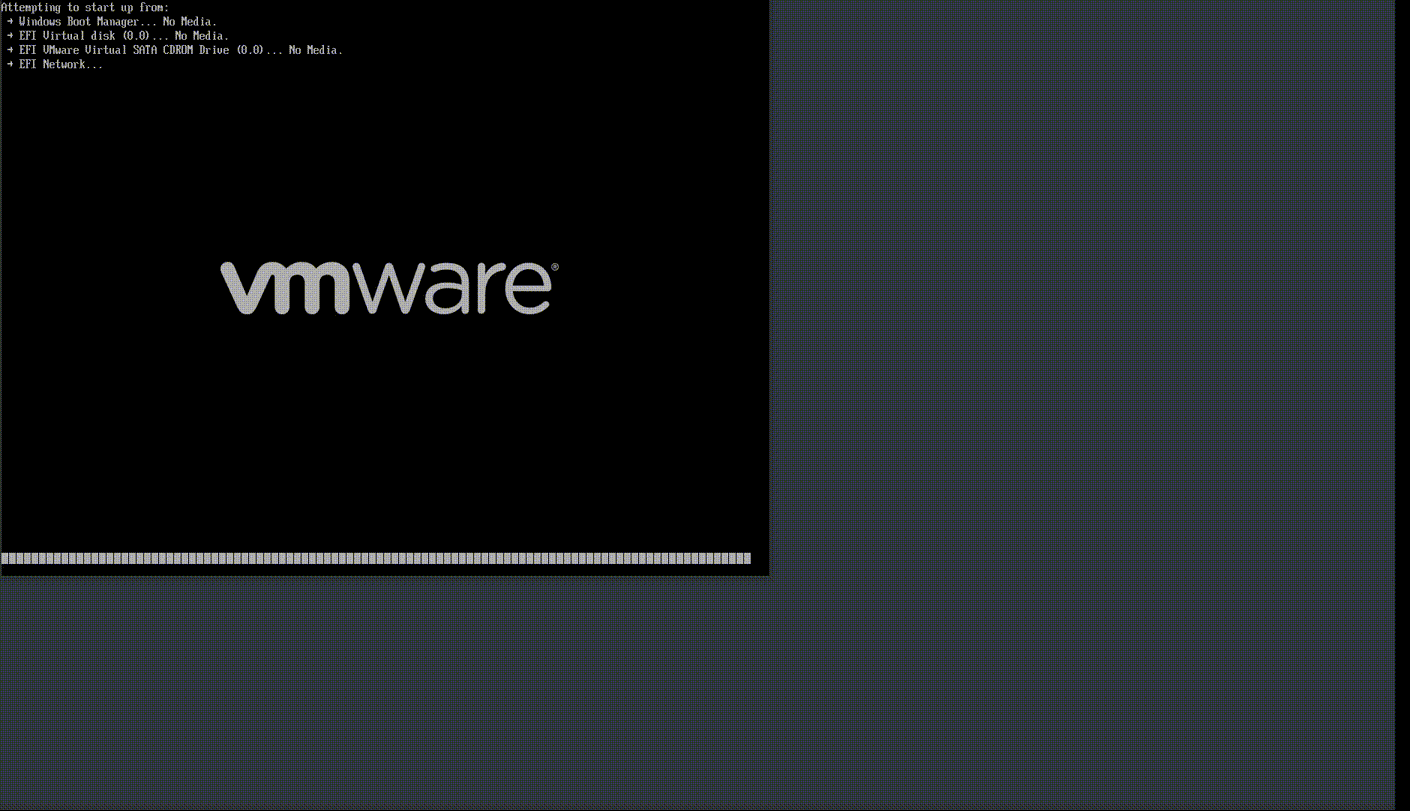
(Figure3)
The CaddyWiper binary is encrypted in an attempt to thwart static analysis. The malware is executed via a loader, ARGUEPATCH in this case a modified version of IDA Pro software’s IDA debugger server: win32_remote.exe (peremoga.exe in this case) which is used for reverse engineering executables, including malware. This was an interesting choice of software to weaponize, however it might just be a jab at future threat researchers.
The loader executes CaddyWiper, along with the decryption key.
C:\Users\peremoga.exe JRIBDFIMCQAKVBBP C:\Users\pa1.pay
Taking a detailed look into the CaddyWiper executable, it’s overall very small at only 9KB. The binary is a 32-bit PE (packed executable) designed to run on Windows operating systems.
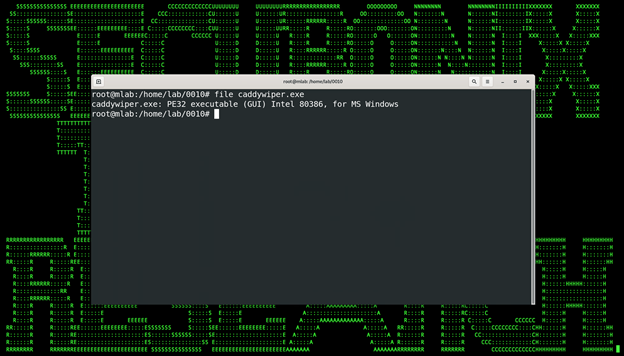
(Figure 4)
Running “strings” on the file produces nothing useful as it’s encrypted.
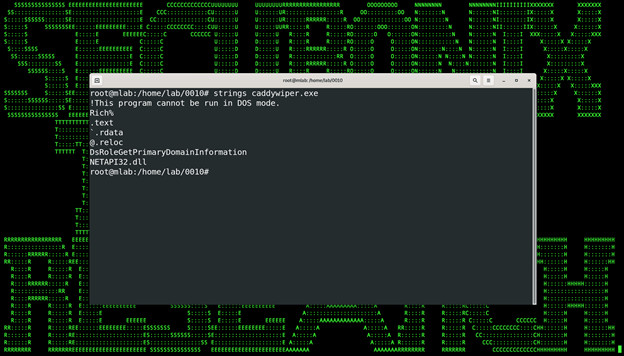
(Figure 5)
However, things get interesting when we run the binary against Floss, a utility designed specifically for decrypting encrypting binaries and payloads:
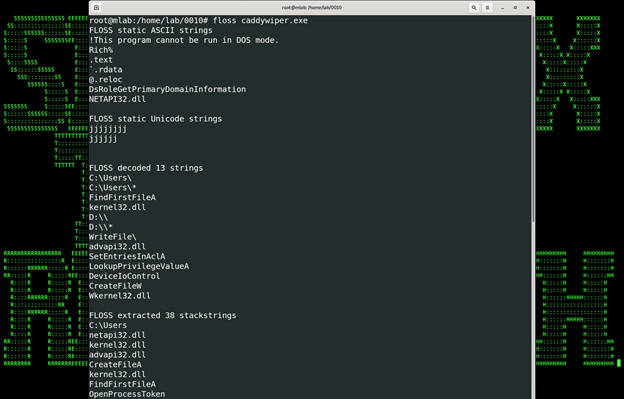
(Figure 6)
With the strings decrypted, we get a better idea as to what the binary might be doing. Briefly, information such as Windows Win32 APIs and loaded DLLs can be identified. We have other information such as file paths and physical path locations such as \\.\PHYSICALDRIVE9.
Opening the binary in a decompiler, it’s obvious that there is obfuscation at play here. The binary uses what’s called “stacked strings” in order to hide its original code. This methodology can be seen in Figure 7.
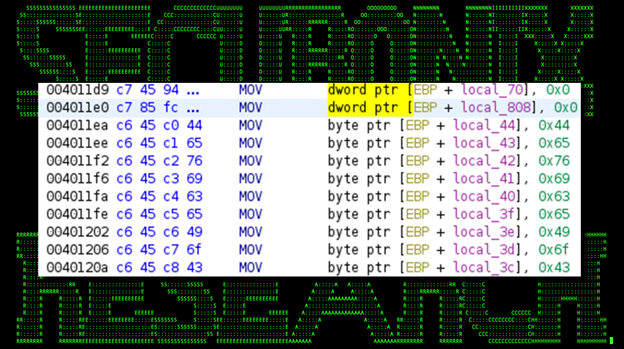
(Figure 7)
There are a few decryption functions found within the program that will decrypt after execution. Figure 8 is an example of one such function.
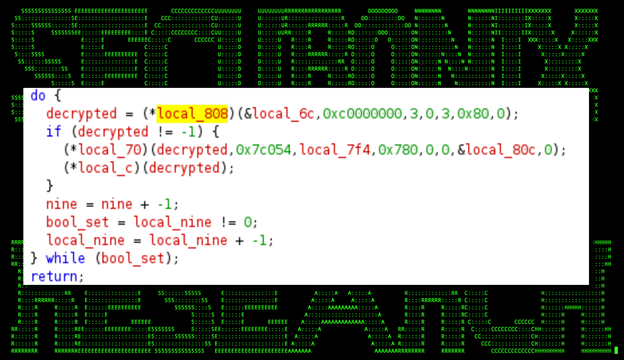
(Figure 8)
CaddyWiper Impact
The intent of the CaddyWiper malware is clear, destroy as much as it can as quickly as possible. It manages this by wiping all contents in C:\Users and all attached disks from D:\ to Z:\. It also wipes all physical disks ranging from \.\\PHYSICALDRIVE0 to \.\\PHYSICALDRIVE9. This includes the Windows MBR (Master Boot Record) and GPT (GUID Partition Table).
It accomplishes this by filling all affected destinations by zero-filling. Once completed, the system will inevitably crash and will be unable to reboot.
Detailed Analysis: Industroyer2
Industroyer2 is a single executable at around 37Kb which when it was initially discovered was named 108_100.exe. Its execution is deployed via compromised domain controller GPO where a scheduled task was created to load the binary.
The malware is engineered to target specific ICS systems that leverage the IEC 60870-5-104 protocol for SCADA communication.
The specific binary featured in this analysis varies slightly from the original Industroyer2 binary discovered by ESET and CERT-UA. The overall intent appears to be the same, however, like the original binary, hardcoded IP addresses and ports were found pre-compiled, meaning that the attackers had at least limited knowledge of their target as seen in Figure 9:

(Figure 9)
Upon execution, the application does a few interesting things. Before establishing connections using ICS protocols, it terminates a few processes which may interfere with its execution or attempted connection. These include:
- PService_PPD.exe
- PServiceControl.exe
We can confirm this by renaming the Industroyer2 malware to one of the executable names and then watching it kill itself as seen in Figure 10:
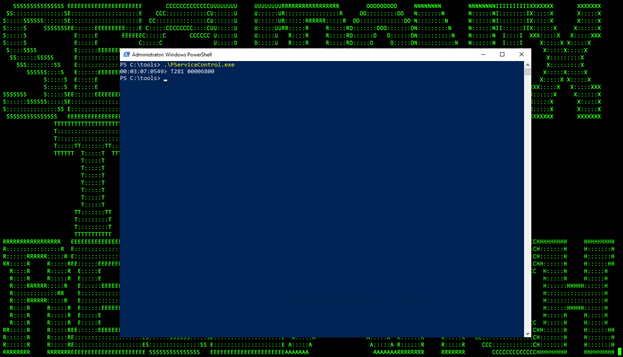
(Figure 10)
It’s clear that the malware attempts to communicate with ICS systems as upon inspection of the binary we can find several instances of ICS commands getting issued (Figure 11). These include:
| ICS COMMAND | DEFINITION |
| STARTDT con | Start Data Transfer |
| STARTDT act | Response |
| STOPDT con | Stop Data Transfer |
| STOPDT act | Response |
| TESTFR con | Test Communication |
| TESTFR act | Response |
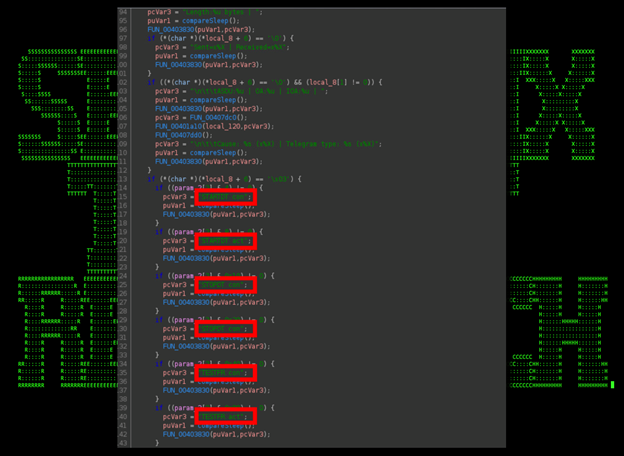
(Figure 11)
Communication to ICS software attempted to access any of the hard-coded IP addresses over port 2404. This port is typical for SCADA protocol communication.
In an effort to see in greater detail what exactly would happen if the Industroyer2 malware were able to successfully connect, a virtual machine running virtualized IEC104 SCADA software was deployed, hopefully mimicking the actual intended target. In the end communication was indeed established and confirmed at both ends as seen in Figure 12:
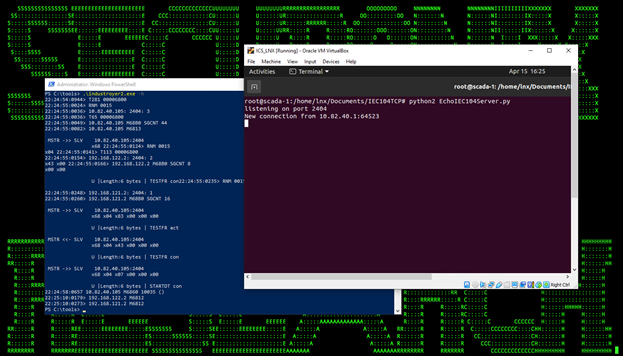
(Figure 12)
Conclusion
Industroyer2 and other associated ICS-specific malware is certainly on the rise and appears the be yet another major known strain following other ICS targeted malware such as STUXNET, BLACKENERGY2, INDUSTROYER(CRASHOVERRIDE), and the more recent PIPEDREAM.
At this point in time, while Ukraine is at the epicenter of many of these targeted attacks, originations should remain on high alert and continuously monitor related IoC’s and detections.
We will continue to cover other possible related variants and wipers as we learn more.
Mitigations – Securonix Recommendations
- Ensure proper isolation between SCADA/ICS and other networks
- Ensure anti-malware definitions are up to date, and an offline backup plan is in place
- Closely monitor ICS port communication and baseline deviations
- Implement an application whitelisting policy to restrict the execution of unknown binaries
Related Detection Policies:
- WEL-OTH5-RUN Successful GPO Import From Backup Application Analytic
- WEL-ACC52-RUN Network Shares Create On Domain Controller CommandLine Analytic
- WEL-ACC53-RUN Scheduled Tasks Deployment Using GPO Share Name Analytic
- MODEL-CAB-L16 Potential Malicious Mass Deployment through GPO Sequence – Modality
- EDR-SYM352-RUN Possible Credential Dumping Registry Analytic
- EDR-SYM146-RUN Process Dump Using Service DLL CommandLine Analytic
- EDR-SYM260-RUN Potential Impacket’s Lateral Movement Process Creation Analytic
- EDR-SYM314-RUN Potential Usage Of Impacket Command Line Analytic
- WEL-SHR11-RUN Potential Impacket SecretDump Activity Analytic
Hunting Queries:
Omega_id: WEL-OTH5-RUN Windows Application logs
Title: Successful GPO Import From Backup Application Analytic
baseeventid = “2001” AND devicecustomstring1 CONTAINS “Import from backup is successful.”
Omega_id:WEL-ACC52-RUN
Title: Network Shares Create On Domain Controller CommandLine Analytic
rg_functionality = “Microsoft Windows” AND baseeventid = “4688” AND destinationprocessname ENDS WITH “net.exe” AND resourcecustomfield1 CONTAINS ” share ” AND resourcecustomfield1 CONTAINS “=”
Omega_id:WEL-ACC53-RUN
Title: Scheduled Tasks Deployment Using GPO Share Name Analytic
rg_functionality = “Microsoft Windows” AND baseeventid = “5145” AND accountname ENDS WITH “$” AND devicecustomstring2 = “\*\SYSVOL” AND ^str_devicecustomstring4_relativetargetname ENDS WITH “\Preferences\ScheduledTasks\ScheduledTasks.xml”
Omega_id:EDR-SYM352-RUN
Title: Possible Credential Dumping Registry Analytic
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND resourcecustomfield1 CONTAINS “Get-ItemProperty” AND (resourcecustomfield1 CONTAINS “hklm:\sam” OR resourcecustomfield1 CONTAINS “hklm:\system” OR resourcecustomfield1 CONTAINS “hklm:\security”)
Omega_id:EDR-SYM146-RUN
Title:Process Dump Using Service DLL CommandLine Analytic
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname ENDS WITH “rundll32.exe” AND resourcecustomfield1 CONTAINS “comsvcs.dll” AND resourcecustomfield1 CONTAINS “minidump”
Omega_id:EDR-SYM260-RUN.yml
Title: Potential Impacket’s Lateral Movement Process Creation Analytic
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND (sourceprocessname ENDS WITH “wmiprvse.exe” OR sourceprocessname ENDS WITH “mmc.exe” OR sourceprocessname ENDS WITH “explorer.exe” OR sourceprocessname ENDS WITH “services.exe”) AND resourcecustomfield1 CONTAINS “cmd.exe” AND resourcecustomfield1 CONTAINS “/Q” AND resourcecustomfield1 CONTAINS “/c” AND resourcecustomfield1 CONTAINS “127.0.0.1” AND resourcecustomfield1 CONTAINS “&1”
Omega_id:EDR-SYM314-RUN
Title: Potential Usage Of Impacket Command Line Analytic
(rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”)) AND (resourcecustomfield1 CONTAINS ” /Q ” AND resourcecustomfield1 CONTAINS ” /c ” AND resourcecustomfield1 CONTAINS “__” AND resourcecustomfield1 CONTAINS “ADMIN$”) AND (destinationprocessname ENDS WITH “cmd.exe” OR sourceprocessname ENDS WITH “cmd.exe”)
Omega_id:WEL-SHR11-RUN.yml
Title: Potential Impacket SecretDump Activity Analytic
rg_functionality = “Microsoft Windows” AND baseeventid = “5145” AND devicecustomstring2 CONTAINS “\ADMIN$” AND ^str_devicecustomstring4_relativetargetname CONTAINS “SYSTEM32” AND ^str_devicecustomstring4_relativetargetname CONTAINS “.tmp”







