- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
By Securonix Threat Labs, Threat Research: Den Luzvyk, Tim Peck
Updated May 12, 2022
Introduction
A new critical CVE has just come to light which targets a vulnerability in iControl REST functionality in F5 systems. The critical CVE (CVE-2022-1388) which is classified as an authentication bypass vulnerability carries a 9.8/10 severity rating. The overall impact is vast as it affects the current line of network appliances such as the F5 BIG-IP systems. These include modern firewalls and network monitoring and performance hardware.
Currently, the vulnerability has been patched and F5 has disclosed in its latest KB update. F5 customers should patch immediately as it is currently being exploited in the wild.
Attack Chain & Scope
The scope of the vulnerability is not limited to just authentication bypass. Properly exploited, an attacker has the ability to execute UNIX-based commands remotely which could give them full control over the appliance. Affected versions include:
| Appliance Version | Status |
| F5 BIG-IP: 16.1.0 – 16.1.2 | Patched in 16.1.2.2 |
| F5 BIG-IP: 15.1.0 – 15.1.5 | Patched in 15.1.5.1 |
| F5 BIG-IP 14.1.0 – 14.1.4 | Patched in 14.1.4.6 |
| F5 BIG-IP 13.1.0 – 13.1.4 | Patched in 13.1.5 |
| F5 BIG-IP 12.1.0 – 12.1.6 | UNSUPPORTED |
| F5 BIG-IP 11.6.1 – 11.6.5 | UNSUPPORTED |
Overall, the exploit is incredibly easy to run against remote F5 systems. In fact several PoC scripts written in Python or even using the CMD command Curl have been spotted in the wild. At this point it’s almost point and click to execute root commands in the remote F5 appliance which can be seen in Figure 0 below.
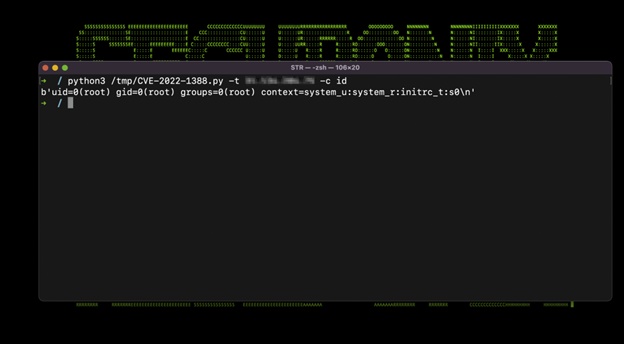
Figure 0
The exploit requires very little data and takes advantage of the iControl REST to allow for authentication bypass and eventually remote code execution (RCE). As you can see in the exploit code below, an attacker would need very little information about the target system (figure 1).
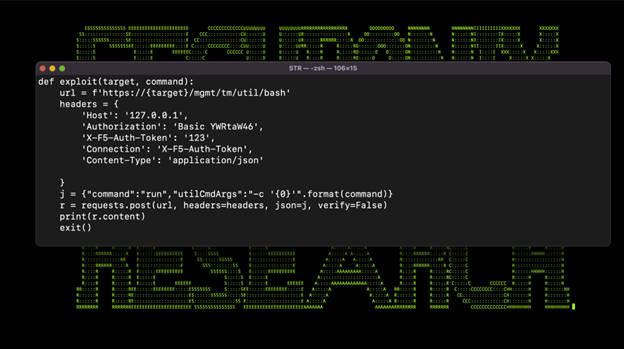
Figure 1
According to public information available on sites such as Shodan, we see a large number of public facing sites that fall under this target category (figure 2).
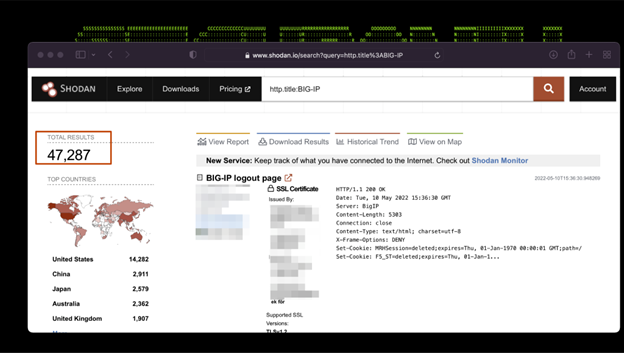
Figure 2
Conclusion
The overall impact could be incredibly detrimental to the organization’s network integrity. Given the exploit carries both an authentication bypass as well as remote code execution techniques, we advise organizations to take extra precautions and to implement mitigation strategies we recommend below.
Securonix Recommendations & Mitigations
- Patch affected systems to the latest KB provided by F5
- Block iControl REST access through local IP address ranges (ie: 127.0.0.1)
- Restrict management interface to trusted management networks or vLANs.
- Perform forensic analysis to ensure no past compromise
- /var/log/audit
- /var/log/restjavad-audit.0.log
Detections
Seeder Hunting Queries:
- rg_functionality=”Next Generation Firewall” AND requesturl CONTAINS “/mgmt/tm/util/bash”
- rg_functionality=”Firewall” AND requesturl CONTAINS “/mgmt/tm/util/bash”
- rg_functionality=”Web Proxy” AND requesturl CONTAINS “/mgmt/tm/util/bash”
- rg_functionality = “Traffic Manager” and rg_vendor = “F5 Networks” and deviceseverity = “notice” and resourcecustomfield2 = “Command OK” and resourcecustomfield4 CONTAINS “cmd_data=run” and resourcecustomfield4 CONTAINS ” -c “
Securonix Coverage:
- Possible CVE-2022-1388 Exploitation Attempt F5 Audit Analytic
- Possible CVE-2022-1388 Exploitation Attempt URLs Access Analytic
References
- [1] https://cve.mitre.org/cgi-bin/cvename.cgi?name=2022-1388
- [2] https://support.f5.com/csp/article/K51812227
- [3] https://support.f5.com/csp/article/K23605346







