- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Incident Response and Forensics
By Oliver Rochford, Applied Research Director, Securonix
Unlock the Power of Capture the Flag (CTF) Exercises in Cybersecurity—your essential strategy to enhance incident response capabilities. In this blog, we uncover how CTF exercises equip security teams with the vital skills needed to counteract cyber threats effectively. Discover the key benefits, essential components, and practical tips to launch successful CTF initiatives in your organization.
A Brief Overview of Capture the Flag in Cybersecurity
Capture the flag (CTF) exercises are a game changer for your incident response strategy. These exercises provide unique types of cyber security challenges that assess an organization’s cyber security readiness and response capabilities. At its core, capture the flag simulations are designed to test your ability to perform digital forensics, analyze network traffic, solve puzzles, and work with your team. These exercises build your team’s problem-solving, critical thinking, and collaboration skills. As an important blue team tool, they put your security team through a series of security scenarios designed to emulate real-world attack tactics, techniques, and procedures (TTPs).
Putting your security team through these high-pressure and realistic situations helps you test your team’s response readiness and challenge them to respond quickly and effectively.
Capture the flag exercises can be used to test a variety of different incident response processes:
- Cyber threat modeling
- Threat hunting
- Risk analysis
- Incident response
- Data collection
- Detection effectiveness
- Forensic evidence gathering
- Critical infrastructure protection
They are particularly useful for testing teams and individuals who are critical to responding to a cyber attack. This could include teams like the cyber incident response team, security operations center (SOC), or threat hunting team.
In this post, we discuss why CTF exercises are important for effective cyber security operations, what makes up a good CTF exercise, and ways you can get started with your own CTF.
Types of Capture the Flag in Cybersecurity Games
Explore the different formats of CTF exercises commonly used in cybersecurity to sharpen skills and prepare for potential threats:
Jeopardy-style CTF
In Jeopardy-style CTF competitions, participants face a broad range of challenges categorized by difficulty and topic area, akin to the “Jeopardy!” game show format. Challenges might include tasks in cryptography, steganography, binary analysis, and web vulnerabilities. Each challenge solved earns points, and the team with the highest score at the conclusion of the competition wins. This format is particularly accommodating for participants of varying skill levels, offering a spectrum of challenges from basic to highly complex.
Attack-Defence CTF
Attack-Defence CTFs are dynamic and interactive, simulating a real-world environment where teams must defend their own network while attacking others’. Each team manages a network or a system, identifying and exploiting vulnerabilities in their opponents’ infrastructure while safeguarding their own against attacks. This type of CTF mirrors the ongoing responsibilities of cybersecurity professionals who must actively secure their systems against threats while also conducting offensive operations.
How to run a successful CTF exercise
Capture the flag exercises can be run in many different ways. Some organizations run their CTFs as a one-off event, while others choose to hold them as an annual challenge like the DEF CON CTF.
No matter what your setup is, these exercises have a few key components that you need to think about before you begin.
Challenges and scenarios
Although many aspects of a CTF exercise are standard, it’s important to design your exercise for your organization. This includes selecting the right scenario and challenge.
The main goal of a CTF is to create a series of challenges for your players to solve. These can be puzzles, riddles, or other activities that test your players’ skills and knowledge. Be sure to make them challenging, but also achievable. You don’t want to frustrate your players or make them feel unable to progress through the game. There should be just enough ambiguity in each challenge that it takes some creative thinking to solve.
You should select a challenge that is relevant to your organization. This could be based on your company’s risk profile, threat modeling exercises, or new and emerging threats. Common scenarios include a simulation of specific threats, threat actors, or attacks and techniques.
There are three common types of CTF scenarios:
Artifact scenario: In this scenario, your players will receive a set of artifacts, for example, packet captures or a set of event logs, that they need to analyze and use to solve puzzles or advance in the game. This is a particularly good scenario if you’re hosting a tabletop CTF or giving a hands-on training exercise.
Real-world scenario: In a real-world scenario, your players will receive access to a real-world environment or a section of a network that they need to complete their challenges. This is a particularly good scenario if you want to simulate a real-life attack.
Simulated scenario: In a simulated CTF scenario, players will receive access to a virtual environment that simulates a real-world network or system. This is a particularly good scenario if you’re hosting an online CTF.
Participants
There are many ways you can choose participants for a CTF exercise. You can choose a representative sample of your organization, use volunteers, or even choose a specific team. Participants don’t always have to be cybersecurity experts — there are other stakeholders in most organizations that will also often be involved in incident response, for example, cloud or IT operations — but they do need to be able to follow the instructions.
Generally, a CTF exercise requires two teams — a red team that exists to attack, and a blue team whose role is to defend. Although in many organizations a purple team, in which a team of experts takes on the role of both the red team and the blue team, is also common.
More recently, breach and attack simulation solutions are being used to take the role of the red team.
Hosting
If you’re hosting your capture the flag exercise online, you’ll need a virtual environment to house it. You may choose to use a platform like Amazon EC2, or you could install a dedicated server. If you’re looking for a free solution, you can also check out options like Digital Ocean or Microsoft Azure.
There are even dedicated platforms for hosting CTF competitions, and also solutions that make it quick and easy to spin up cyber ranges.
Scoring criteria and objectives
Many CTF games have some sort of scoring or leveling system that determines which players advance to the next level. You may also assign a time limit that determines when the game ends. Make sure your scoring and level system is fair, and that there is a logical reason for why your players are advancing or failing.
Another approach is to define CTF objectives, for example, obtaining access to a specific resource or credentials, or identifying Patient X in a malware outbreak.
Benefits of capture the flag exercises
CTF exercises are a great way to add challenge to your red teaming exercises. They’ll push your team to think in new ways and encourage communication while also creating an adrenaline-pumping exercise that will get everyone excited about coming back for more. CTF exercises are also a great way to practice your cyber security skills, learn new ones, and stress test the strength of your team. Other benefits of CTF exercises include:
CTFs assess an organization’s readiness and response capabilities
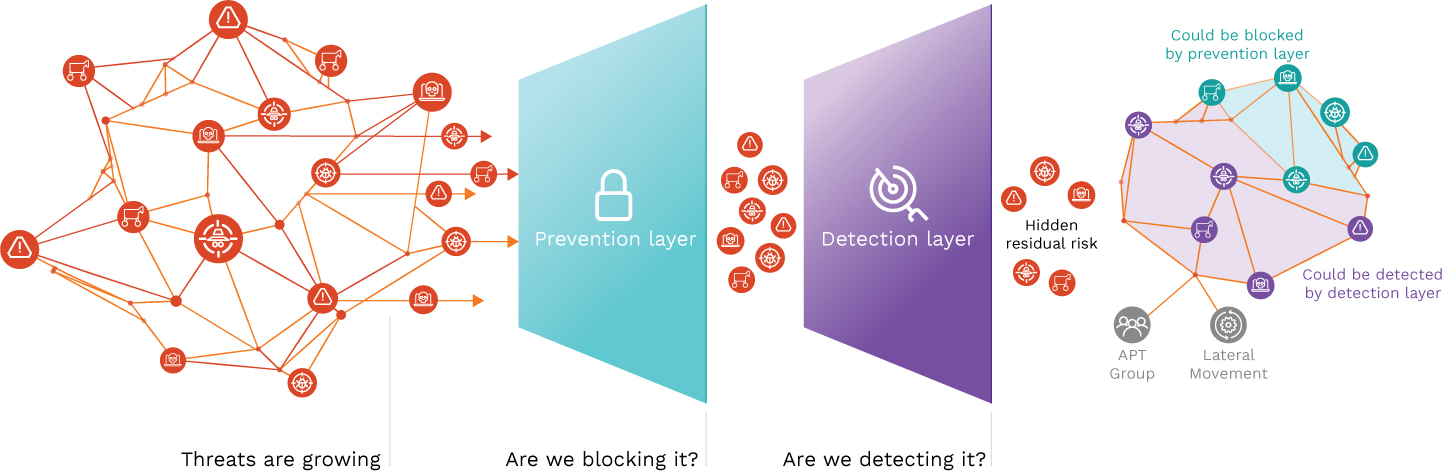
CTFs test a variety of cyber security capabilities and best practices, including threat detection, incident response, and organizational resilience. A good CTF exercise will include a variety of scenarios that test your team’s ability to defend against a wide range of attacks.
Threat detection effectiveness: How quickly can your team detect threats? Can they identify potential attacks before they hit your network? CTFs will test your team’s skill in identifying malicious activity, including malware infections, suspicious outbound connections, and actions such as privilege escalation and lateral transfer.
Incident response readiness: How effective is your team at responding to incidents? Can they contain threats before they spread throughout your network? CTFs will challenge your team’s ability to respond to infections, terminate threats, and contain the damage caused by malicious actors.
Organizational resilience: Can your team withstand cyber attacks? Do they have the resources, skills, and knowledge necessary to bounce back after an attack? CTFs will test your team’s readiness to withstand cyber threats and maintain operations (to the best of their ability) after an attack.
CTF exercises help build a robust response team
One of the best ways to build a robust response team is through CTF events. Learning new skills is a crucial part of any employee’s development and CTFs are an effective way to foster collaboration, build expertise, and train new employees through real-world scenarios. CTFs test your team’s skills and apply the knowledge they’ve acquired through classes and training.
CTF exercises are incredibly valuable for onboarding, training, and assessing new employees
Newer members of your security team will likely participate in CTF exercises as part of their onboarding process. CTFs are valuable for both the organization and new employees because it allows the company to gauge the skill level and provides them with the opportunity to test their skills in a real-world scenario. In addition, CTF exercises help foster a collaborative, creative culture among your team members. Because they’re tested under pressure and often in an unfamiliar environment (i.e. they don’t have access to their usual tools, equipment, or workflows), CTFs require team members to work together and think outside the box.
Maximizing Cybersecurity Through CTFs
Capture the flag exercises are designed to challenge your team’s problem-solving and collaboration skills, but most importantly, they are a proactive way to test your incident response readiness and processes. When conducted in production environments combined with red teaming or breach and attack simulation solutions, they can validate the effectiveness of your security detection and response architecture. They can also be a fun way to engage with your employees and give them a taste of red teaming.
CTFs are pretty straightforward to get set up, too. However, they need to be planned and executed well to ensure they’re as effective and worth your effort. That’s why it’s important to think through your setup and decide what type of CTF you want to run. That way, you can make sure you’re getting the most out of your event and that your team members are getting the experience they need to be better prepared for real-life attacks.
Or, of course, you can leave the work to us, sign up for our Securionix CTF event, hone your skills and learn new expertise without any additional work at all.

Finding the Signal Through the Noise: Quantifying SIEM Effectiveness
Learn More