- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
While much of the cybersecurity media and attention focuses on external cybersecurity threats such as ransomware, APTs, and nation-state actors, insider threats continue to plague organizations not only in numbers but in impact. According to Verizon’s 2022 Data Breach Investigations report, the number of database records compromised by the average insider breach since 2008 has surpassed those of the average outsider attack by anywhere from 5-10 to 1. Ponemon’s 2022 Cost of Insider Threats Global Report pegs the average annual insider threat remediation cost for 55% of the sample set at $15.4 million each over a 12-month period.
The insider threat is only one of the subjects covered in depth in Securonix’s recently released “2022 Threat Report”, which analyzes trends in cybersecurity threats and how customers use SIEM to protect their data. The report offers insight and advice, and compelling real-life stories of techniques from the trenches that would be useful for any SIEM-enabled organization.

Download the 2022 Securonix Threat Report
The report is divided into four sections: insider threats, cloud infrastructure, ransomware, and a brand-new section on the internet of things (IoT), which we tackle for the first time.
Aside from diving into each of these categories, the Threat Report demonstrates how they all work together to challenge the organization’s security strategy. For example, the move to the cloud has made protection from insider threats and ransomware more problematic as organizations attempt to find the perfect balance between easy cloud accessibility and necessary security controls and policies. The combination of the cloud and the growth of remote and work-at-home users has widened the geographical impact of misconfigurations of cloud infrastructure, objects, and privileges.
In this post we’ll examine the insider threat findings and tackle the other categories in future articles.
Overall, it’s no surprise that threats in general are on the rise, both according to the NIST National Vulnerability database and our customers’ experiences with our newest offering, Autonomous Threat Sweeper (ATS). Through ATS Securonix has alerted customers of a total of 867 threats from January to July of 2022, which is a 482% increase over the same period in 2021, with 35,776 known indicators of compromise, 380% more than last year. We have used ATS to investigate and protect customers from 582 threats, which is 218% more than this period (January-July) in 2021. This is in line with NIST reporting 2,000 more vulnerabilities so far this year than were discovered in the same period last year.
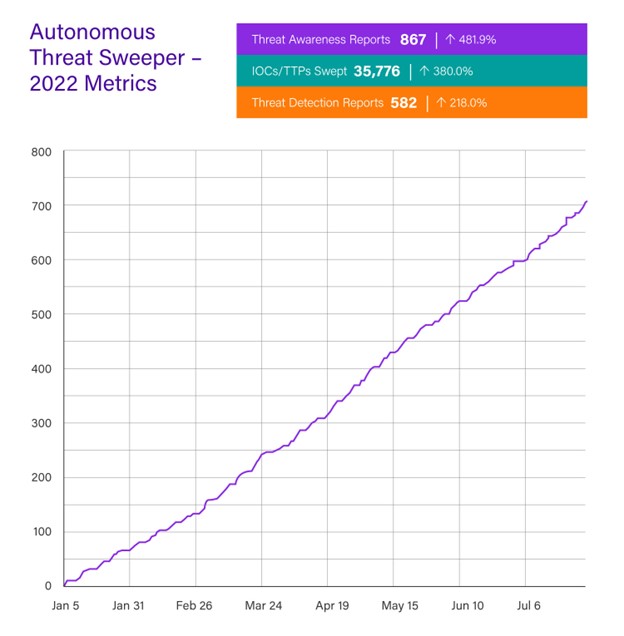
Securonix Autonomous Threat Sweeper metrics January through June 2022
Insider threats
Insider threats can be particularly damaging, as employees often know where the most valuable data lies and exactly how to get to it. One of the trends that has complicated insider threat protection for most organizations, according to the report, is the increasing use of cloud collaboration tools such as Google Drive and DropBox, which have made it easier for users who have the right data access permissions to share sensitive data with those who don’t. As organizations have implemented successful policies to prevent data theft through corporate emails and USB drives, insiders have turned to cloud collaboration and personal cloud-based email, such as Gmail, as the means to accomplish the same ends.
The report recommends grouping SIEM insider threat alerts into inherent risk, data collection, data exfiltration, and impact categories. Focusing on inherent risk factors such as users exhibiting flight risk, users with upcoming termination dates, or users on watch lists for poor performance or not sharing the organization’s core values can help an organization narrow the focus of its data collection and exfiltration alerts. The latter include users accessing files, shares, or network locations they haven’t accessed before; downloading an abnormal amount of data; sending files and emails to their personal email account; or deleting critical files.
Overall, the report found that customers who were doing well focused on the right users and their behavior, with risk-aligned use cases enabled in 85% of customer SIEM environments.
It’s about data sets
Choosing the right data sets to ingest into the SIEM is one of the most effective ways for organizations to protect themselves. For example, while the report found that about 60% of organizations were ingesting key sabotage-related data sources such as cloud application audits, email security, and content management systems, only 13 percent ingested cloud application security broker (CASB) data. This indicates a security gap, as most insider threat SIEM policies leverage CASB data sets.
Nevertheless, at 89% of recommended data sets, organizations have good data source coverage for detecting sabotage activities, followed by exfiltration at 78% and inherent risk at 68%.
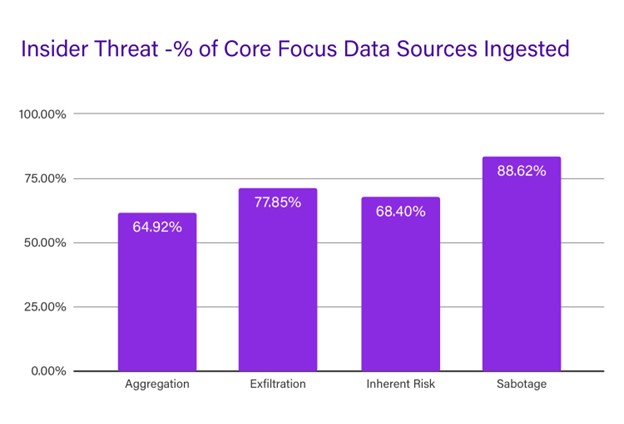
Leading at 88%, the percentage of sabotage- related data sources that are ingested in the data set provide significant coverage for detecting related activities. Exfiltration and inherent risk data sources follow at 77.85% and 68.40%, with 64.92% having aggregation-related data sources ingested by their SIEM.
When it came to data exfiltration, the report found that most exfiltration incidents involved sensitive documents being made public, which reflected organizations’ difficulties implementing the most effective cloud controls. Users emailing sensitive files and data to personal cloud-based email accounts such as Gmail was also common. Luckily, a hefty 68% of organizations were ingesting email and email security data.
Overall, the report indicates that customers are effectively leveraging the SIEM to detect insider threats, but more of them should consider ingesting CASB data sets.
In the next post we’ll discuss the report’s findings on cloud infrastructure threats, followed by posts on ransomware and IoT/OT findings.








