- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs, Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
TL;DR
Today ransomware continues to gain traction and organizations are faced with a barrage of constantly evolving tactics. There are however, several tried-and-true methods of detection or indicators of compromise (IoCs) that many ransomware variants have been using for years with no sign of letting up, relying on the fact that new users will fall for the same old tricks. In this post, we will take a look at the five most commonly used ransomware IoCs, proven tactics as well as some early detections to help you stay one step ahead.
These five are as follows and are based on our team’s research gathered over the last six months, and in some cases over the last few years beginning when Vssadmin was popularized by WannaCry. Read more below for details on each IoC.
- Vssadmin: shadow copy delete
- Windows Management Instrumentation (WMI): shadow copy delete
- Wbadmin: delete backups
- BCDEdit: disable system recovery
- PowerShell: shadow copy delete
Introduction
As we jump into 2023, no doubt the subject of ransomware will be a heavily discussed topic for cybersecurity defenders. The global disruptions caused by ransomware in 2022 were relentless, and if the trend continues, organizations impacted by ransomware will only increase.
It seems that variants are ever changing and making headlines, “Blue Teamers” or those responsible for monitoring organizational security, are forced to constantly remain on high alert. With so many variants, each targeting different sectors and maintained by unique APT groups, how can we as defenders stay current and ensure we have the proper detections in place?
Figure 1: Cerber ransomware, a desktop wallpaper
Ransomware is simply a form of malware that has one goal: destroy as much and as quickly as possible. Fortunately for us, with this goal in mind we can focus our detections on reliable TTPs that the ransomware “strain” of malware will leverage.
From eight-year-old ransomware variants such as WannaCry, to today’s versions such as Moisha and Bluesky, they all operate very similarly which is something that we can use to our advantage.
Breaking down the attack chain…
Ransomware for the most part operates in three unique phases. This is important as knowing what each phase does will help us narrow our detections for better accuracy and reliability. The three “typical” phases we see are: initial infection and persistence, inhibit recovery, and the data destruction phase.
When it comes to building detections, clearly the “data destruction” phase would be a poor target as a starting point. An alert to the SOC at this point means that the damage has been done and, depending on the ransomware variant, system logging and AV services have already been stopped. However, any alert is better than none. While the damage has already been done to the alerting host, containment could still be possible to reduce the risk of ransomware spreading to other networked systems.
Our best bet to reduce the overall impact of ransomware is the use of timely and valid detections during the first two phases of the attack chain.
Ransomware Attack Chain: Initial Infection [MITRE: TA0001]
This phase, while related to the ransomware’s overall attack chain, is typically not executed by the ransomware itself. This phase is normally responsible for a “loader” malware such as Emotet, Qakbot, Trickbot, or more recently Bumblebee.
Building detections around this stage will provide the earliest detection, thus increasing the time needed to mitigate the threat. TTPs during this stage tend to vary depending on the loader used and original delivery method.
Ransomware Attack Chain: Inhibit Recovery [MITRE: T1490]
During this stage, the ransomware will attempt to make key system configuration changes which will prevent a system administrator from being able to recover files. From the perspective of the attacker, this phase is ultra critical as, if the encrypted files could easily be recovered, they’re not getting paid.
Detections in this phase are also good because generally this phase makes a lot of noise from a logging perspective. After having detonated ransomware many times in a lab environment, based on our observations, the data destruction phase is right around the corner and the odds of stopping the third phase is less likely.
However, even in this stage, detections are still crucial. While a single system may be lost, simply being aware of the infection via quality detections could prevent the spread of the ransomware to other network hosts, reducing the overall impact.
Ransomware Attack Chain: Data Destruction [MITRE: T1485]
As the name implies, the data destruction phase, or encryption phase encompasses the time in which the ransomware process is looping through files on the filesystem, encrypting them, and deleting the originals.
Detections at this point are the least impactful as it is possible that with the host in a compromised state, logs may not even be sent.
In summary, with the first initial compromise phase primarily handled by the loader malware the attacker opted to use, and the final phase not being a great option for detections due to timing and unreliability, let’s focus our efforts on the second phase: Inhibit Recovery.
Inhibit Recovery: Ransomware, what are you doing?
Ideally, our detections during the initial compromise phase would have prevented the loader from executing or downloading the ransomware payload. However, as firm believers in the “Defense in Depth” principle, it’s critical to have a good set of plan Bs in place, and in our case those will be quality detections in the Data Destruction phase.
During this phase there are some typical activities we have observed ransomware performing that can produce very reliable detections. Detections for Securonix customers will be listed at the conclusion of the article.
Next we’ll go over common TTPs ransomware used to inhibit system recovery. Each variant discussed will include links from this year highlighting the fact that these techniques are still in practice today.
Vssadmin: shadow copy delete
Believe it or not, at the time of writing this article, ransomware is still leveraging the Windows administration tool vssadmin.exe to delete system shadow copies. Modern variants such as Hive Ransomware, HavannaCrypt, Agenda, and Black Cat ransomware are still leveraging this tried-and-true way to inhibit recovery by deleting Windows shadow copies.
While the technique is ancient as far as active TTPs go, dating even before the infamous WannaCry ransomware strain from 2017, we still highly recommend looking for vssadmin usage.
Example ransomware commands:
vssadmin delete shadows /all /quiet
vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB
vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded
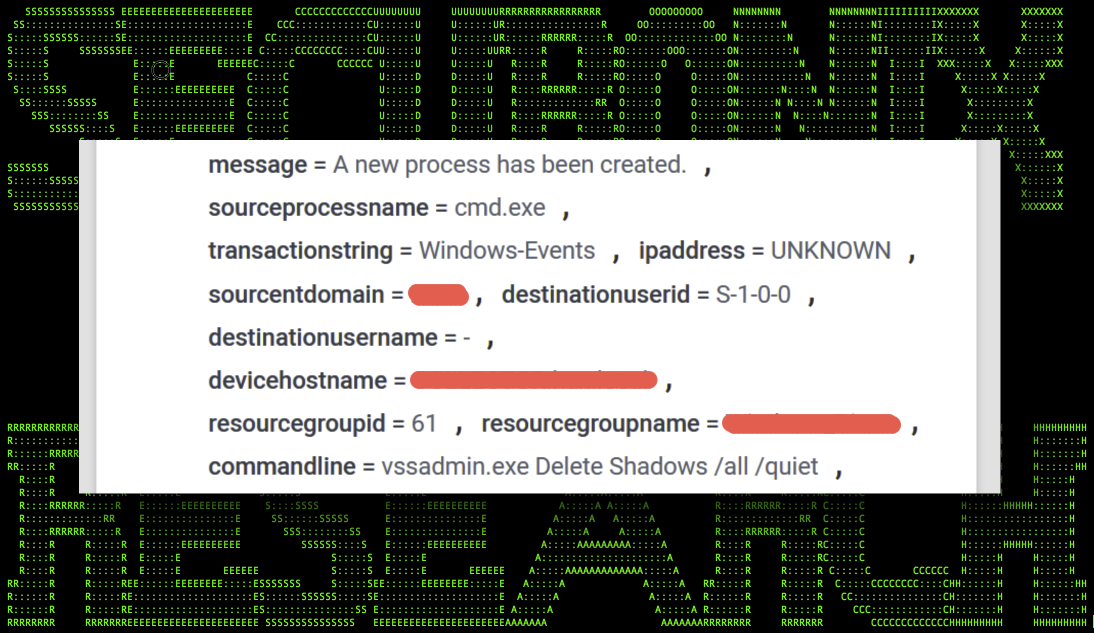
Figure 2: vssadmin.exe ransomware event
These commands can produce some easy wins as far as detections go. The usage of the “/all /quiet” flag proves that there is an attempt to conceal the command from the user. It is unlikely that an administrator or routine script would run the command with those parameters.
Windows Management Instrumentation (WMI): shadow copy delete
Once again, we observe ransomware authors attempting to delete Windows shadow copies, however this time using the Windows administration tool wmic.exe. This tool can be used to accomplish the same result as vssadmin discussed previously.
This technique is also not new though it is still heavily used today with modern ransomware strains such as Loki Locker, Ragnar Locker, and modern versions of Lockbit ransomware such as Lockbit 2 and Lockbit 3.
Example ransomware command:
wmic shadowcopy delete
select * from Win32_ShadowCopy | Win32_ShadowCopy.ID
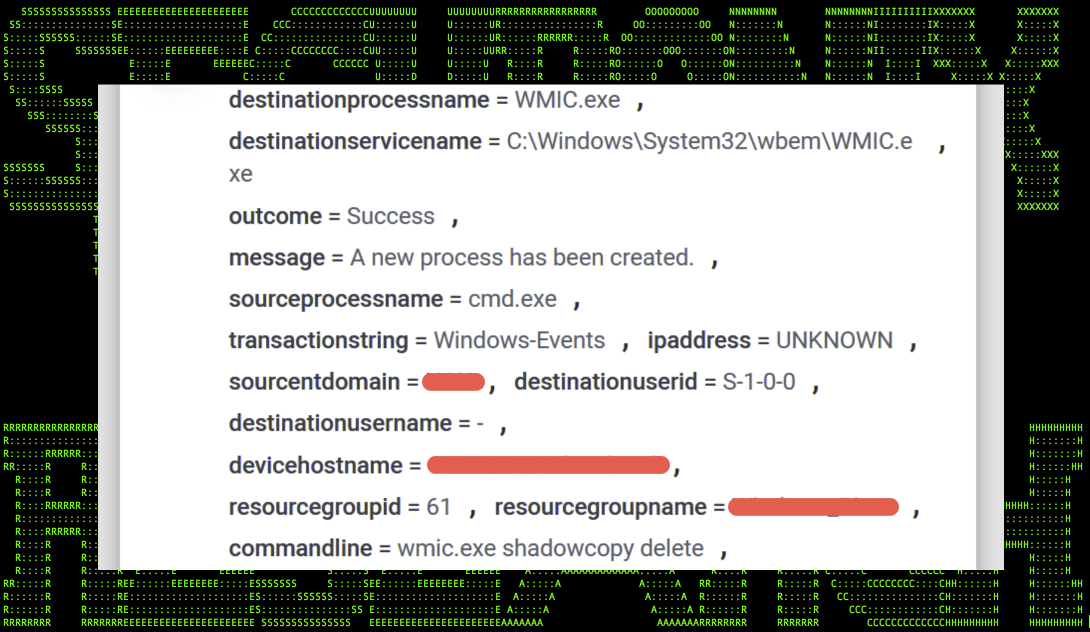
Figure 3: wmic.exe ransomware event
While the command is simple, it would provide an interesting and easy detection, it should be noted that it could produce false positives as there is nothing inherently sneaky about this particular command.
Wbadmin: delete backups
The Windows tool wbadmin.exe is a command line utility that administrators can use to manage Windows backups and backup related settings. The threat actors behind the ransomware don’t want you to easily restore the affected host via Windows backup, so they’ll typically use standard wbadmin.exe commands to delete any and all backups, regardless of whether or not they exist.
While also not a new tactic we’re still seeing this tactic being utilized by modern ransomware variants such as MedusaLocker, Ako, and AVADDON ransomware.
Example ransomware commands:
wbadmin delete catalog -quiet
wbadmin DELETE SYSTEMSTATEBACKUP
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
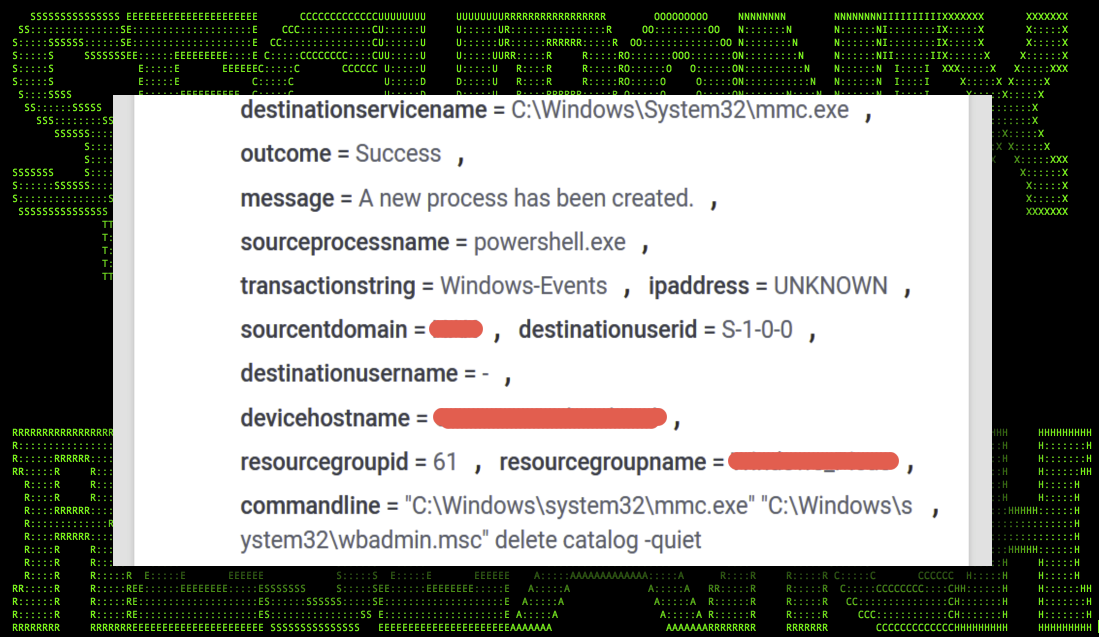
Figure 4: wbadmin.exe ransomware event
Detections across multiple strains for wbadmin.exe are very consistent and legitimate usage of this tool along with the associated commands should be very uncommon.
BCDEdit: disable system recovery
The Windows utility bcdedit.exe is a command line tool which allows system administrators to modify the host’s boot configuration. From the perspective of a threat actor, it can be used maliciously to prevent Windows from booting into the recovery console. This again assists in increasing the overall success factor of the ransomware on making the target’s data unrecoverable.
Example ransomware commands:
bcdedit.exe /set {default} recoveryenabled No
bcdedit /set {default} bootstatuspolicy ignoreallfailures
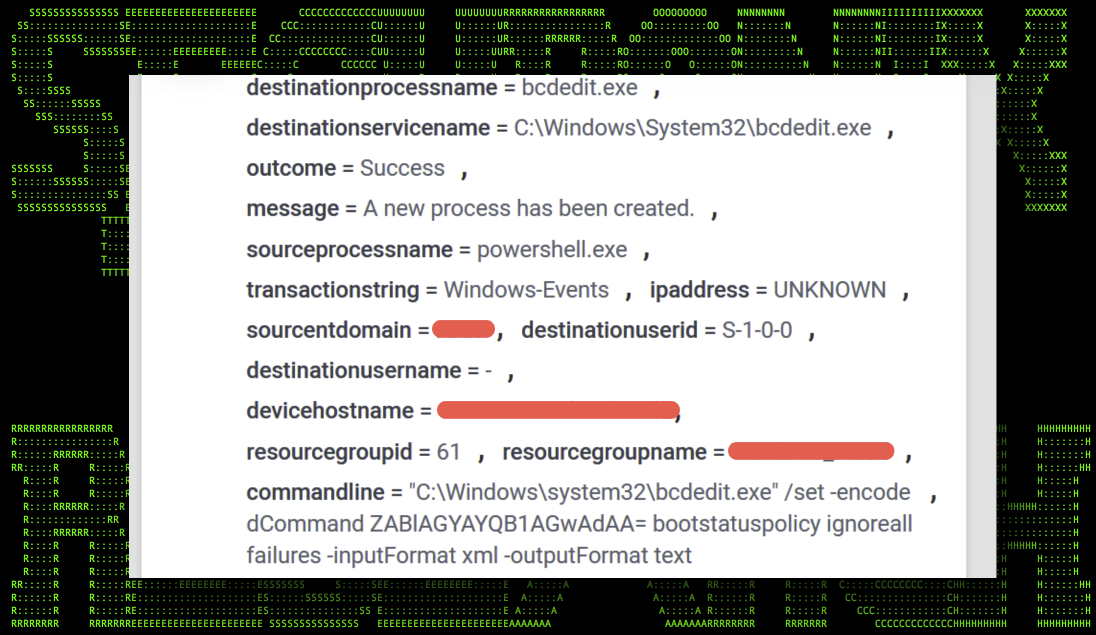
Figure 5: bvdedit.exe ransomware event
The usage of bcdedit.exe is also not new. It was heavily leveraged years ago by the popular Sodinokibi, RobinHood, and WannaCry ransomware strains. Today it still remains commonly used and is seen as leveraged by Lemty, RansomEXX, and Zeppelin ransomware variants.
PowerShell: shadow copy delete
Similar to the goals we saw earlier with vssadmin.exe and wmic.exe, attackers can also use PowerShell commands to delete system shadow copies using the cmdlet “Get-WmiObject” or “Get-CimInstance”. This command effectively gets each stored shadow copy and deletes them.
Example ransomware command:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
powershell.exe Get-CimInstance Win32_ShadowCopy | Remove-CimInstance
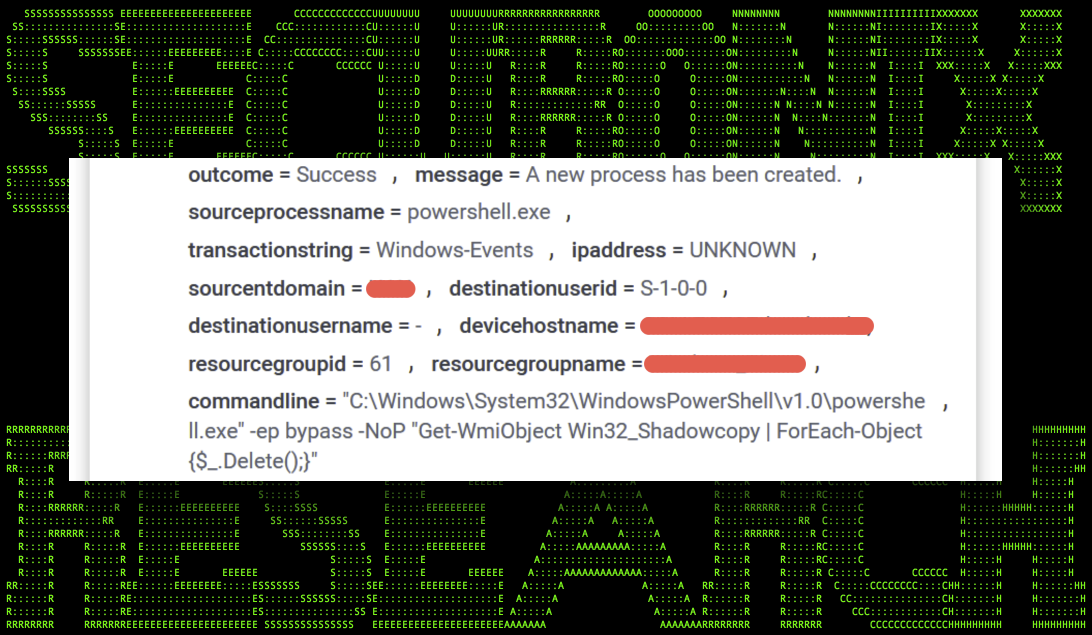
Figure 6: powershell.exe ransomware event
This tactic was popularized by Sodinokibi, Darkside, and Grandcrab but can still be seen today leveraged by modern variants such as Midas (Thanos) and BlackByte ransomware.
Detections for this command should produce very few false positives as the command is quite specific and likely not used by system administrators.
Ransomware detection: timing is everything
From the moment the hypothetical user enables macros from that malicious email attachment, time is critical when it comes to mitigating a ransomware infection. Some ransomware can take mere minutes, others can take hours depending on the variant and the volume of data to be encrypted.
Knowing this is critical when it comes to stopping the spread of infection. Detections of reliable, actionable ransomware related activity would need to be responded to, and isolation steps taken immediately during any stage of the attack.
As we covered earlier, common ransomware will leverage a loader malware variant to initiate the infection. Like ransomware, loaders can also follow predictable IoCs. The advantage of leveraging detections around initial loader IoCs could shave off a minute or two off the detection time. This is vital when time is of the essence. The most common ransomware today originate from phishing or spear phishing attacks and include:
- OneNote code execution
- Archive (.zip or .iso)
- .lnk file (shortcut) code execution
- Common LOLbin usage to bypass AWL or AV detections
Conclusion
It should be noted that by the time the detection of the common IoCs we discussed are responded to by the SOC, the host is likely currently being encrypted, or has been compromised. At this point the organization’s goal should be to isolate and to prevent the ransomware from spreading to other hosts. Detections at any stage in the attack chain could make the difference between a compromised endpoint versus a compromised domain.
So far, we’ve proved that detection of ransomware during the “inhibit recovery” phase of the attack chain is not only valid, but extremely reliable. Using these five IoCs for a ransomware compromise is not only reliable across time, but also across variants. Meaning we don’t need to build individual detections per ransomware strain.
It is also very likely that with any given ransomware variant, two or more of these methods can be used in conjunction. An extreme example is the Epsilon Red ransomware which will execute all five of the IoCs we highlighted!
Securonix Detections
Host-based command line logging will be the best method for catching the aforementioned IoCs. Microsoft’s Sysinternals: Sysmon, event ID 1 will record process start events along with the associated command line arguments.
Additionally, process start events can be logged into the Microsoft Security log under event ID 4688. If you don’t already, we strongly recommend enabling host-based command line logging via GPO for enhanced and early threat detection.
Detection of PowerShell-based commands, such as our last example where Get-WmiObject is used to delete shadows, MS PowerShell Operational log can be used. EVID 4104 (scriptblock logging) or EVID 4103 (module logging) can log the execution of the command.
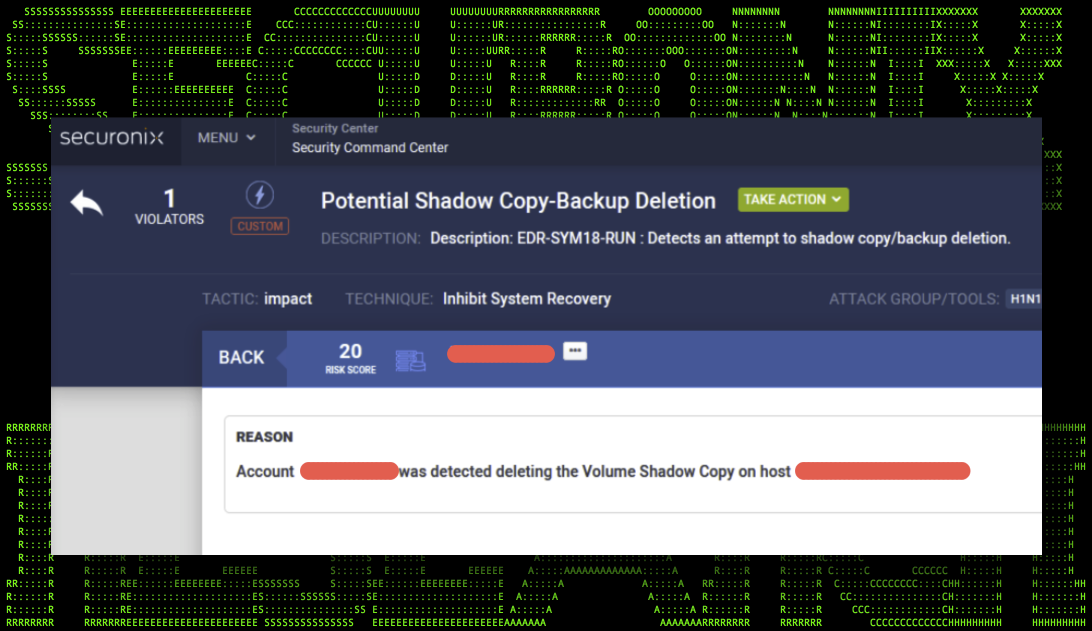
Figure 7: Securonix violation
Below are queries and detections that Securonix customers can leverage to assist in detections.
Relevant Spotter queries
- rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND ((resourcecustomfield1 CONTAINS “vssadmin” AND resourcecustomfield1 CONTAINS “delete” AND resourcecustomfield1 CONTAINS “shadow”) OR (resourcecustomfield1 CONTAINS “wbadmin” AND resourcecustomfield1 CONTAINS “delete” AND resourcecustomfield1 CONTAINS “catalog”) OR (resourcecustomfield1 CONTAINS “wmic” AND resourcecustomfield1 CONTAINS “shadow” AND resourcecustomfield1 CONTAINS “delete”) OR (resourcecustomfield1 CONTAINS “vssadmin” AND resourcecustomfield1 CONTAINS “resize” AND resourcecustomfield1 CONTAINS “shadowstorage”) OR (resourcecustomfield1 CONTAINS “Get-ComputerRestorePoin” AND resourcecustomfield1 CONTAINS “Delete-ComputerRestorePoint”))
- rg_functionality = “Microsoft Windows Powershell” AND (message CONTAINS “Get-CimInstance” OR message CONTAINS “gcim” OR message CONTAINS “Get-WmiObject” OR message CONTAINS “gwmi”) AND (message CONTAINS “Remove-CimInstance” OR message CONTAINS “rcim” OR message CONTAINS “.Delete()” OR message CONTAINS “Remove-WmiObject” OR message CONTAINS “rwmi”) AND message CONTAINS “Win32_ShadowCopy”
- rg_functionality = “Microsoft Windows Powershell” AND message CONTAINS “Get-WmiObject” AND message CONTAINS “Win32_Shadowcopy” AND message CONTAINS “ForEach-Object” AND message CONTAINS “Delete”
- rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname = “cmd.exe” AND resourcecustomfield2 CONTAINS “bcdedit” AND resourcecustomfield2 CONTAINS “/set” AND ((resourcecustomfield2 CONTAINS “bootstatuspolicy” AND resourcecustomfield2 CONTAINS “ignoreallfailures”) OR (resourcecustomfield2 CONTAINS “recoveryenabled” AND resourcecustomfield2 CONTAINS ” no”))
Relevant Securonix Detection Policies and their associated functionalities: (Ransomware)
- WEL-ALL-996-RU – Microsoft Windows
- EDR-ALL-718-RU – Endpoint Management Systems
- EDR-ALL-18-RU – Endpoint Management Systems
- CEDR-ALL-18-RU – Cloud Antivirus / Malware / EDR
- PSH-ALL-312-RU – Microsoft Windows Powershell
- PSH-ALL-10-RU – Microsoft Windows Powershell
- EDR-ALL-727-RU – Antivirus / Malware / EDR
- EDR-ALL-27-RU – Endpoint Management Systems
- CEDR-ALL-27-RU – Cloud Antivirus / Malware / EDR
Additional Securonix Detection Policies and their associated functionalities: (Initial Loaders)
- EDR-ALL-1088-RU – Endpoint Management Systems
- EDR-ALL-1098-RU – Endpoint Management Systems
- EDR-ALL-730-ER – Antivirus / Malware / EDR
- EDR-ALL-30-ER – Endpoint Management Systems
- CEDR-ALL-30-ER – Cloud Antivirus / Malware / EDR
- EDR-ALL-1139-RU – Endpoint Management Systems
- EDR-ALL-950-RU – Endpoint Management Systems
- EDR-ALL-923-RU – Endpoint Management Systems
- EDR-ALL-984-RU – Endpoint Management Systems
- EDR-ALL-798-RU – Antivirus / Malware / EDR
- EDR-ALL-98-RU – Endpoint Management System
- CEDR-ALL-98-RU – Cloud Antivirus / Malware / EDR
MITRE ATT&CK
| Tactics | Techniques |
| Impact | T1486: Data Encrypted for Impact T1490: Inhibit System RecoveryT1485: Data Destruction |
| Execution | T1047: Windows Management Instrumentation
T1059.001: Command and Scripting Interpreter: PowerShell |
References:
- Check Point Research: Third quarter of 2022 reveals increase in cyberattacks and unexpected developments in global trends
https://blog.checkpoint.com/2022/10/26/third-quarter-of-2022-reveals-increase-in-cyberattacks/ - Securonix Threat Labs Initial Coverage Advisory: Analysis and Detection of BumbleBee https://www.securonix.com/blog/securonix-threat-labs-initial-coverage-advisory-analysis-and-detection-of-bumblebee-loader-using-securonix/
- Election Security Spotlight – Defense in Depth (DiD)
https://www.cisecurity.org/insights/spotlight/cybersecurity-spotlight-defense-in-depth-did - Inside the Ragnar Locker ransomware
https://www.itworldcanada.com/article/inside-the-ragnar-locker-ransomware/501193 - Trend Micro researchers warn of a new ransomware family called Agenda
https://securityaffairs.co/wordpress/134911/cyber-crime/agenda-ransomware.html - The many lives of BlackCat ransomware
https://www.microsoft.com/security/blog/2022/06/13/the-many-lives-of-blackcat-ransomware/ - WannaCry, Petya, NotPetya: how ransomware hit the big time in 2017
https://www.theguardian.com/technology/2017/dec/30/wannacry-petya-notpetya-ransomware - New Ransomware Family Identified: LokiLocker RaaS Targets Windows Systems
https://blogs.blackberry.com/en/2022/03/lokilocker-ransomware - HavanaCrypt Ransomware Masquerading as Google Update
https://www.cybereason.com/blog/threat-alert-havanacrypt-ransomware-masquerading-as-google-update - How LockBit 2.0 Ransomware Works and Indicators of Compromise
https://blogs.blackberry.com/en/2021/08/threat-spotlight-lockbit-2-0-ransomware-takes-on-top-consulting-firm - MedusaLocker Ransomware Analysis, Simulation, and Mitigation
https://www.picussecurity.com/resource/medusalocker-ransomware-analysis-simulation-and-mitigation - One Source to Rule Them All: Chasing AVADDON Ransomware
https://www.mandiant.com/resources/blog/chasing-avaddon-ransomware - Ako Ransomware: Another Day, Another Infection Attacking Businesses
https://www.bleepingcomputer.com/news/security/ako-ransomware-another-day-another-infection-attacking-businesses/ - Nemty Ransomware – Learning by Doing
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/nemty-ransomware-learning-by-doing/ - Ransomware Spotlight – RansomEXX
https://www.trendmicro.com/vinfo/nz/security/news/ransomware-spotlight/ransomware-spotlight-ransomexx - Zeppelin Ransomware Analysis, Simulation, and Mitigation
https://www.picussecurity.com/resource/zeppelin-ransomware-analysis-simulation-and-mitigation - Indicators of Compromise Associated with BlackByte Ransomware – ic3.gov
https://www.ic3.gov/Media/News/2022/220211.pdf
https://www.zscaler.com/blogs/security-research/midas-ransomware-tracing-evolution-thanos-ransomware-variants- How to remove Epsilon Red ransomware and decrypt .epsilonred files
https://www.computips.org/how-to-remove-epsilon-red-ransomware-and-decrypt-epsilonred-files/ - Greater Visibility Through PowerShell Logging
https://www.mandiant.com/resources/blog/greater-visibility - This is how fast a ransomware attack encrypts all your files
https://www.zdnet.com/article/this-is-how-fast-a-ransomware-attack-encrypts-all-your-files/ - An Empirically Comparative Analysis of Ransomware Binaries
https://www.splunk.com/en_us/pdfs/resources/whitepaper/an-empirically-comparative-analysis-of-ransomware-binaries.pdf - Increasing The Sting of HIVE Ransomware
https://www.rapid7.com/blog/post/2023/01/11/increasing-the-sting-of-hive-ransomware/







