- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
By Augusto Barros, VP, Cyber Security Evangelist
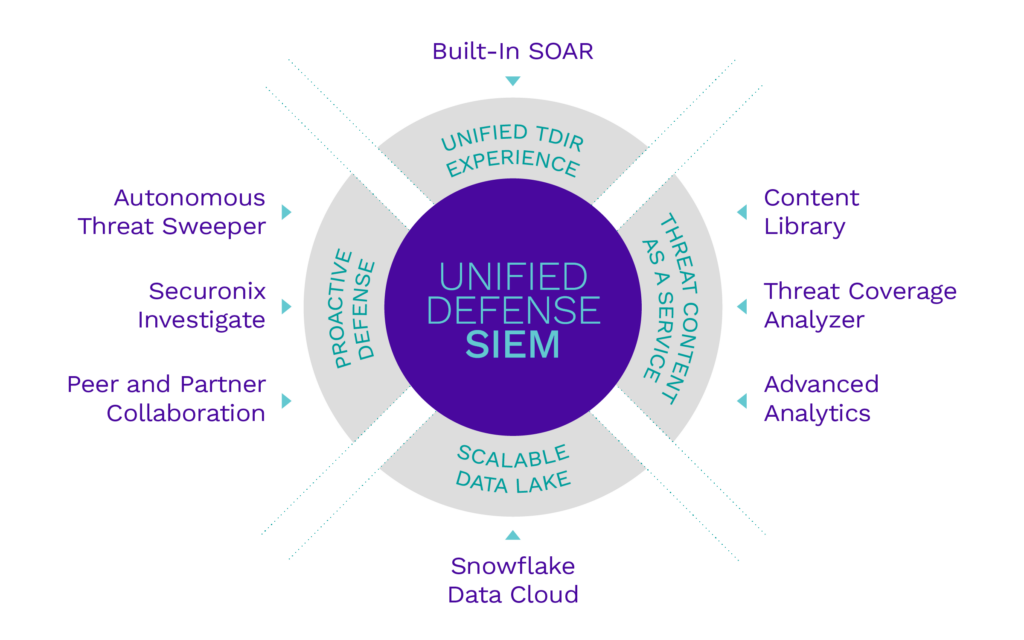
Securonix has recently announced its new product, Securonix Unified Defense SIEM. This is the first product aligned with our new vision for the future of Threat Detection, Investigation and Response (TDIR). This is exciting news as we are bundling many evolutionary and revolutionary improvements to our platform. I want to go over some of those and what they mean for our customers.
The most important improvement to our platform is in our backend; Securonix has now completely embedded the powerful Snowflake Data Cloud in our SaaS SIEM. This means customers can get many of the benefits Snowflake provides, without the need to buy, deploy and manage it. But you may be wondering, how does this benefit me?
The first, clear benefit it provides is that we are now offering it as a key component of our standard package to deliver 365 days of hot data for search. When I say search, I mean the “technical” capability of search,which can be used for multiple use cases, from simple reporting to investigations and threat hunting. Before embedding Snowflake, we offered a multi-tier storage system, with “hot”, “warm” and “cold”, aka where logs go to die, the archive. Our customers would usually have some days on hot, about three months on warm and one year on cold. With Snowflake, things are now simpler (and much faster). One year of data with the fastest available search. With so many breaches being discovered months after the initial compromise, having one year of data readily available for investigations is critical.
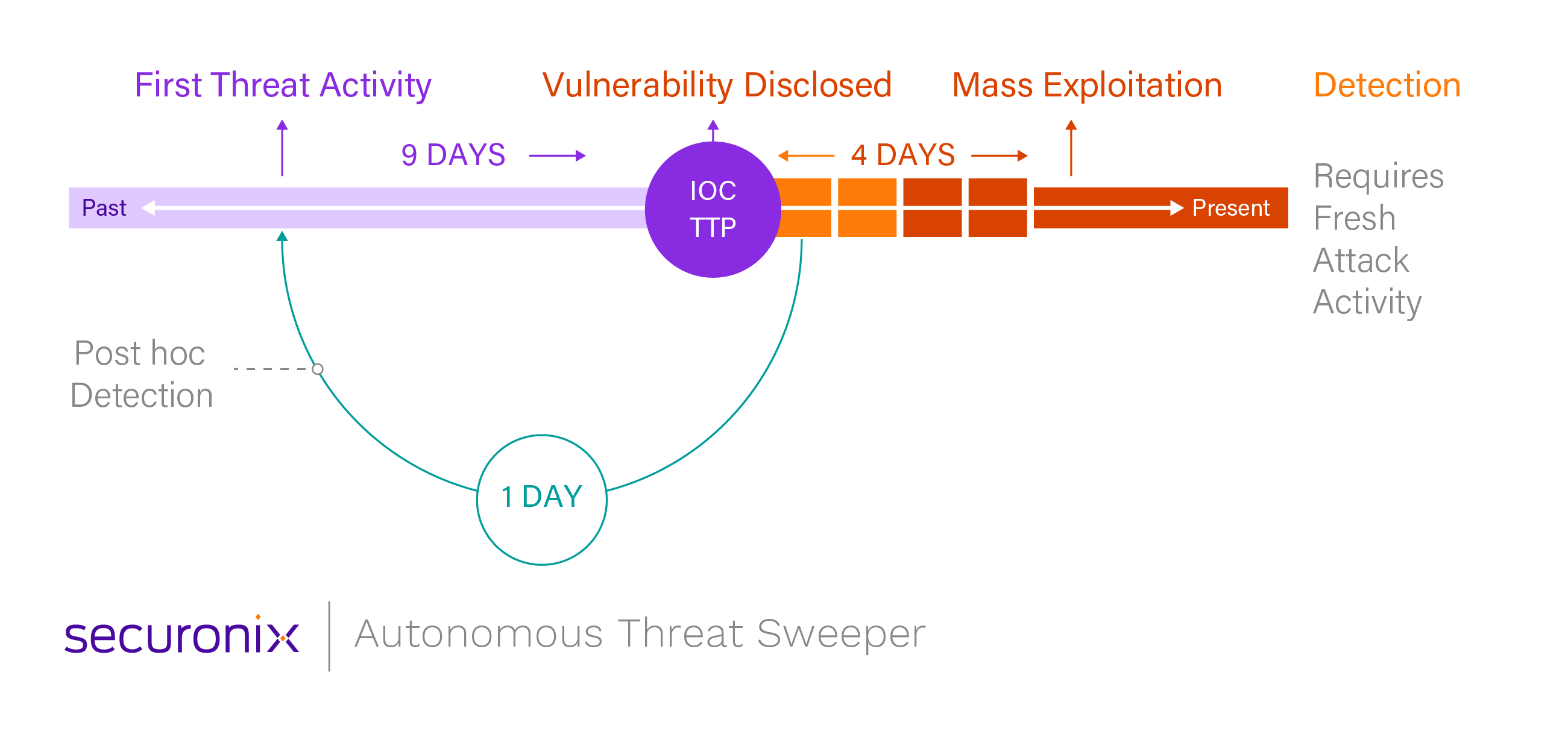
But we are not stopping at the backend. We are also introducing the concept of proactive defense, where we focus on increasing the value of shared knowledge and threat intelligence. Last year we introduced Autonomous Threat Sweeper (ATS), which automatically sweeps historical data for signs of compromise, leveraging intelligence from multiple sources and curated by Securonix’s global team of industry experts. Within our Unified Defense SIEM, ATS really builds on top of Snowflake Data Cloud, enabling customers to find threats effortlessly even if traces of the attacks are buried under months of logs. We are also introducing capabilities to empower customers to collaborate with peers and partners, expanding the universe of intelligence that ATS can use.
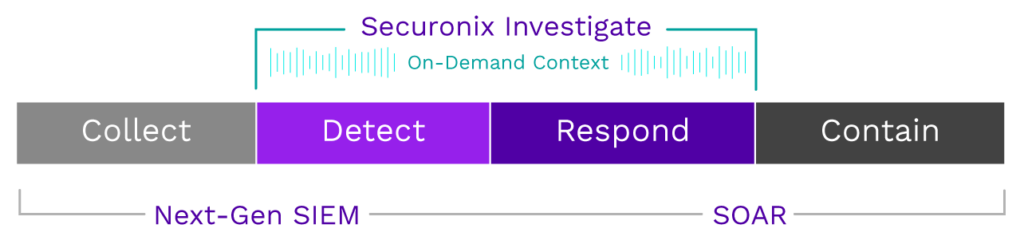
The same curated intelligence and collaboration is available at analysts’ fingertips via Securonix Investigate. Investigate provides on-demand access to context necessary to speed up investigations and responses, and enables collaboration among analysts who can share information about the entities being investigated. This consistently updated context and cross-team collaboration is all done without ever leaving the investigation. It also allows organizations to store insights and findings to be leveraged against future investigations. Securonix Investigate makes the security team more efficient and effective by transferring knowledge from seasoned analysts to junior or new analysts.
Two other areas in which the Unified Defense SIEM is pushing boundaries are content and user experience. Our content-as-a-service approach is expanding to make content selection and deployment even easier and more straightforward. The analytics sandbox, for example, is fully integrated into the framework to ensure the technology is well prepared to support the organization’s Detection Development Life Cycle (DDLC). But the gamechanger here is our Threat Content Analyzer: A tool to support organizations in assessing their content coverage and allows them to plan the evolution of their deployment, select data sources and new content pieces that will give the best results in terms of threat (or compliance) coverage. Content is one of the most important pieces of a SIEM, and having new capabilities to support its management and deployment is critical for success and ensures customers will realize the return on their investment in our platform.
Finally, the unified TDIR experience is a change we are most proud of.
Many organizations have decent detection, investigation and response practices in place, but the pressure to scale up is forcing them to find ways to make those practices more efficient. The boundaries between these processes, for instance, are not as clear as we would hope. Some organizations run investigations as part of the “Detection” phase, while others think investigations are part of their “Response” process.
Trying to establish the boundaries between detection, investigation and response is an artificial and unnecessary exercise. We need to treat detection, investigation and response as a continuum. The excessive fragmentation creates many handovers where the process can break, and it also reduces security operations jobs into roles full of toil and that are prone to attrition by analyst burnout. They also lead to a sprawl of tools and UIs, with many moving parts and duplication. But for processes to be treated as a unified continuum, a single workflow must be in place, to control all steps from early detection to the last steps of response. There is a lot of room to optimize interfaces and also opportunities to reduce toil. This is what we are doing with Unified Defense SIEM and its built-in SOAR capabilities.
Using the same platform across security operations processes provides more than just efficiency gains. It also enables the full integration of threat hunting with detection engineering and other detection-related processes. Threat hunters operating on the same platform can leverage all the data enrichment used for detection, and detection engineers can operationalize hunts for online detection. Hunters save time leveraging work from the detection processes, and detection engineers save time leveraging work done by the hunters.
It’s hard to say which part of Unified Defense SIEM we are more excited about. The incredible performance and capacity gains delivered by Snowflake, or the evolution of the platform as the most efficient security operations toolset in the market. But that’s only about this release. Many of these new capabilities are laying the groundwork for even more exciting things to come, such as improvements in our detection analytics and threat hunting capabilities. Stay tuned, and you will see how Securonix Unified Defense SIEM is (I know it’s a cliché, but oh boy, it applies very well here) changing the game of Threat Detection, Investigation and Response.