- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in July. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In July 2023, Threat Labs analyzed and monitored major threat categories, including the zero-day vulnerability (CVE-2023-36884) that affects Microsoft Windows and Office products, the emergence of new variants of the TrueBot malware, Jumpcloud system breach, a highly evasive Blank Grabber returns, and a campaign where a Chinese threat actor was targeting government entities in Europe, with a focus on foreign and domestic policy entities.
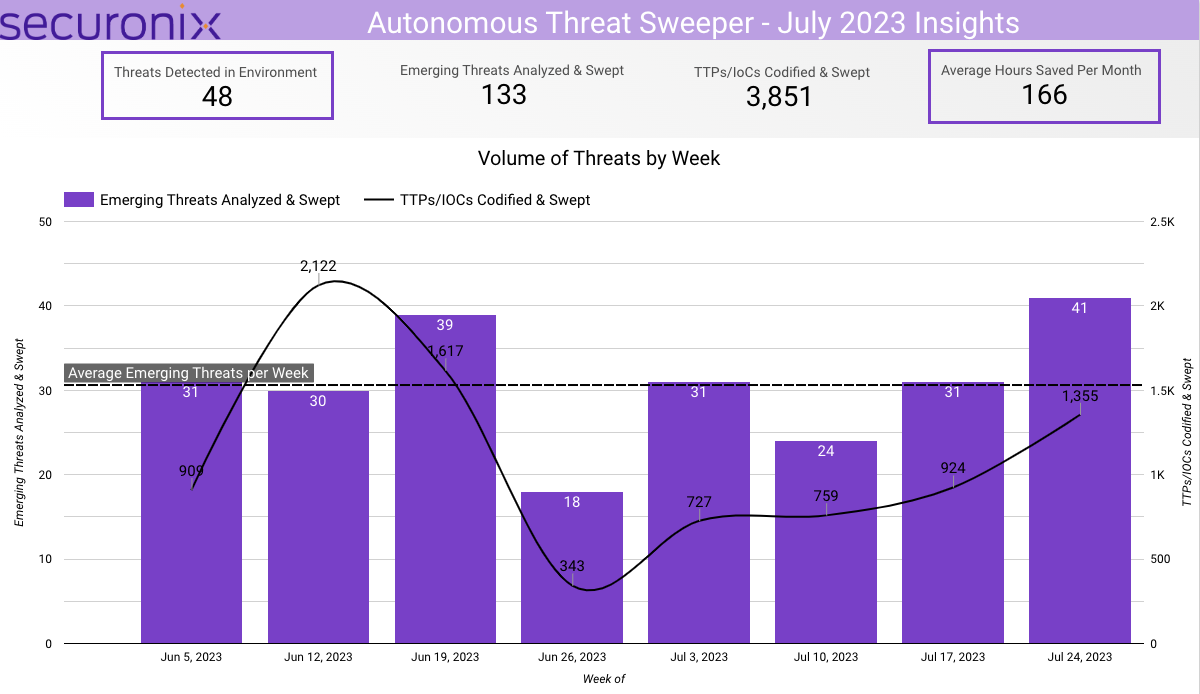
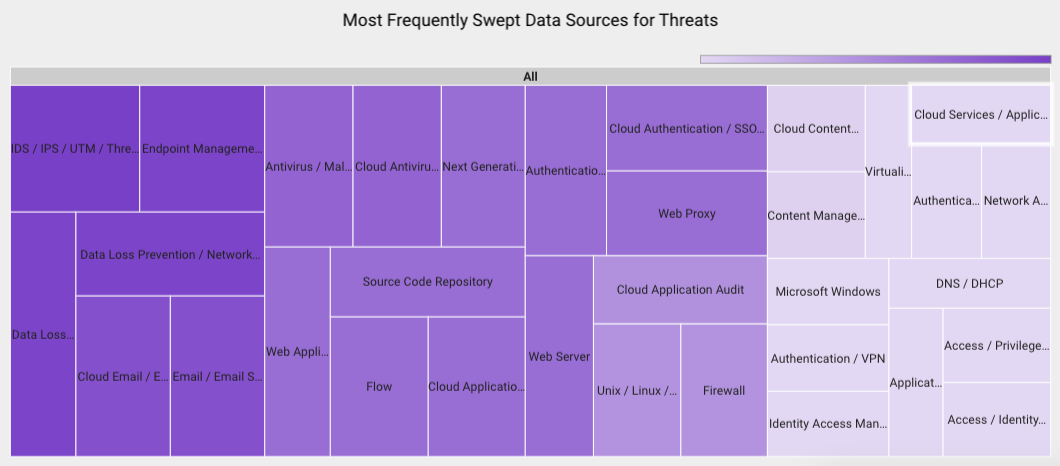
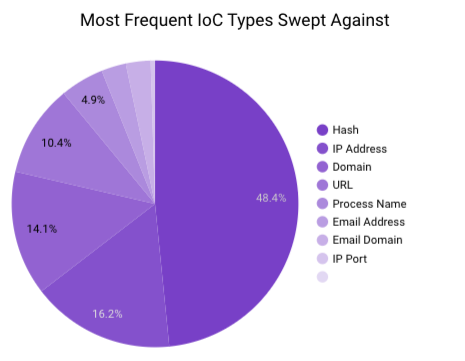
In July 2023, Securonix Autonomous Threat Sweeper identified 3,851 TTPs and IoCs, 133 distinct threats, and reported 48 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
Increased Truebot activity (Originally published in July 2023)
CISA researchers have warned about the emergence of new variants of the TrueBot malware. These variants specifically target organizations in the United States and Canada, aiming to extract sensitive data from compromised networks.
In the recent attacks, new Truebot variants are being installed on victim machines that were compromised by CVE-2022-31199. CVE-2022-31199 is a critical remote execution vulnerability in Netwrix Auditor software. This vulnerability allows threat actors to use malicious code with SYSTEM user privileges. This threat was observed and used since at least May 2023.
Truebot, aka Silence.Downloader, is a downloader that is linked to a threat actor called Silence Group. It is often used by threat actors to steal sensitive information that can be used for extortion. TA505 also was observed using Truebot in combination with deploying Cl0p ransomware since at least late 2022. The threat actors used FlawedGrace RAT to escalate privileges, maintain persistence and they also installed a Cobalt Strike beacon to use for follow on activity.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this vulnerability.
- Implement application controls to manage and control execution of the software. Disable command-line and scripting activities and permissions.
- Limit the use of RDP and other remote desktop services.
- Restrict the use of PowerShell through Group Policy.
- Enable enhanced PowerShell logging.
- Review domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts.
- Maintain offline backups of data and regularly maintain backup and restoration.
Require phishing-resistant multi factor authentication for all services to the extent possible, particularly for webmail, virtual private networks, and accounts that access critical systems.
- Keep all operating systems, software, and firmware up to date.
- 186 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat Actor: Silence Group (TA505) | Threat Actor Location: Possibly Russia | Attack: New variants of the TrueBot malware.
Microsoft zero-day HTML vulnerability (Originally published in July 2023)
Attackers are making use of a zero-day vulnerability (CVE-2023-36884) that affects Microsoft Windows and Office products. The exploit has so far been applied in extremely targeted attacks against businesses in the European and North American government and defense sectors.
On July 11, Microsoft released information about a vulnerability that allowed an attacker to remotely execute code on a target computer using a specially crafted Microsoft Office document. The victim needs to open the infected file for the exploit to work. For the flaw, no patch has yet been made available. Microsoft said a patch might be released as an out-of-cycle security update or as part of its monthly release process, but it is still looking into the problem.
In a recent advisory,the Securonix Threat Research Team explores how security analytics can be used to identify current and future attack variations and assist in defending against RomCom RAT and CVE-2023-36884.
Phishing emails are still a fairly common way for threat actors to spread malware. Be extremely cautious if you get an unsolicited email, especially if there is a sense of urgency present. Despite the fact that the majority of threat actors have moved away from Office document files, it’s still crucial to be extra watchful.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against RomCom RAT and CVE-2023-36884.
- Avoid opening any attachments, particularly those that are unexpected or are from outside the organization. MS Office files in particular should be avoided as they are being used in this campaign.
- Use the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key to implement Microsoft’s mitigating measure.
- Increase log detection coverage by deploying extra process-level monitoring, such as Sysmon and PowerShell logging.
- 10 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
Tags: Attack Type: Phishing | Threat Actor: Storm-0978 | Target Sector: Government Entities | Target Location: Europe, North America | Vulnerability: CVE-2023-36884 (Remote Code Execution) | Malware: RomCom
Jumpcloud system breach (Originally published in July 2023)
According to JumpCloud, a state-sponsored hacking gang infiltrated its networks as part of a highly specific attack targeted at a small number of users. On June 27, the business learned of the problem, one week after spear-phishing attackers had infiltrated its systems. JumpCloud made the decision to rotate credentials and repair the compromised infrastructure even though it did not discover any evidence that its customers had been impacted at the time.
JumpCloud, in conjunction with IR partners and law enforcement, was looking into the incident on July 5 when it found “unusual activity in the commands framework for a small set of customers” and was looking through logs for indications of malicious activity. To safeguard the organizations of its clients, the company rotates all admin API keys on the same day and reminds them to produce new keys.
Researchers claim that the organization transmitted a list of related indications of compromise (IOCs) with attribution to a “sophisticated nation-state sponsored threat actor” who went nameless. After looking over the most recent compromise signs, they connected the cluster of threat activity to a North Korean state-sponsored APT.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this breach.
- The attack on JumpCloud is an example of the cascading effects of these operations to gain access to service providers in order to compromise downstream victims. As reported earlier this year the DPRK supply chain compromise affected the Trading Technologies X_TRADER application and 3CX Desktop App software.
- Both activities may be connected to DPRK actors who are motivated by money, which suggests that DPRK operators are using supply chain TTPs to target specific businesses as part of expanded attempts to target cryptocurrency and fintech-related assets.
- 83 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Attack Type: Spear-Phishing | Affect Product: JumpCloud
Evasive Blank Grabber returns (Originally published in July 2023)
CYFIRMA researchers have identified an infostealer builder known as ‘Blank Grabber’. The malware was released in 2022, but since then has been frequently updated with 85 contributions to the project in the last one month alone. The infostealer targets Windows operating systems and possesses a wide range of capabilities aimed at stealing sensitive information from unsuspecting users.
Some things about this infostealer, include
- The malware builder is written in Python 3, and the compiled malware is written in C++.
- The malware uses the WMI command-line (WMIC) utility to identify and display various system information, including OS, CPU, GPU, and disk drive names; memory capacity; display resolution; and baseboard, BIOS, and GPU driver products/versions. Some of these commands were used by Aurora Stealer in late 2022/early 2023.
- Blank Grabber has evolved and become far more sophisticated, with feature additions improving its scope.
Once installed, Blank Grabber can achieve unauthorized access and theft of important information, like user credentials, intellectual property, and sensitive data, with potential damage, including financial losses, reputational harm, and compromised business operations.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this campaign.
- Mitigating this threat requires a multi-faceted approach, including robust endpoint protection.
- Conduct employee awareness training on a regular basis.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against infostealers like the Blank Grabber
- 12 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
Tags: Malware: Blank Grabber | Target: Windows operating systems | Attack Type: Infostealer
Increased SmugX attack campaigns from Chinese threat actor (Originally published in July 2023)
Checkpoint researchers have identified a campaign where a Chinese threat actor is targeting government entities in Europe with a focus on foreign and domestic policy entities.
The campaign, called “SmugX” engages HTML smuggling, a technique in which malicious payloads are hidden within HTML documents to avoid network-based detection measures.
The attacks, which were observed since December 2022, plan on fresh delivery methods to install a variant of PlugX, a commonly used implant associated with some Chinese threat actors.
The campaign is linked to a previously reported campaign attributed to Chinese APTs RedDelta and Mustang Panda (aka Camaro Dragon or Bronze President), although there is “insufficient evidence”per Checkpoint to definitively link SmugX to either group, according to the research.
SmugX shows a shift in targeting for Chinese threat actors, which used to target Russia, Asia, and the US in their threat campaigns. A new campaign linked to Mustang Panda to use USB drives to distribute self-propagating espionage malware already showed that these groups engaged in threat activity in Europe as part of their global intent.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these campaigns.
- Employees should always be wary of clicking on unknown links or files when using a corporate network or on personal devices, and check with IT departments before downloading anything new from the Internet
- Implement a comprehensive combination of threat emulation and endpoint detection strategies against SmugX attacks.
- 47 IoCs are available on our Threat Labs home page and have been swept against Autonomous Threat Sweeper customers.
Tags: Target Location: Europe | Target Sector: Government Entities | Campaign: “SmugX” engages HTML smuggling technique
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R
Search Query References:
Note: These queries in silo July be prone to false positives and we recommend leveraging it with other stages of the attack progression to increase the likelihood of true positives