- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Are you feeling less than enthusiastic about your current SIEM solution? You aren’t alone. You may have been sold on the idea of a single vendor that can help you store, manage, and protect the entirety of your security data in a harmoniously unified platform. Despite these big promises, many of these large SIEM providers are falling behind in today’s cybersecurity landscape. With increasing data volumes from security tools, the migration of workloads to the cloud, and the rise of sophisticated threats (like insider threats), legacy SIEMs are struggling to meet the demands of modern security teams. The good news is that you aren’t locked in to your legacy SIEM solution and switching is easier than you may think.
It’s important to find the middle ground between having everything in one place for ease of use and making sure your security measures can be customized and adjusted as needed. That’s why Securonix offers robust log management and industry-leading AI and analytics in a unified experience with the flexibility to play nice with other complementary solutions.
Here’s why organizations are making the switch to our platform.
Our learning curve is more of a straight line
Bigger is not always better. In fact, larger platform solutions tend to be overly complex and require you to hire specialized experts to handle and keep your systems running smoothly. This makes retaining skilled staff members difficult because these experts are in high demand by your competitors too. Adding to the complexity, you may also find yourself relying on support tickets to make even simple updates to your backend.
Additionally, integrating a legacy SIEM with your existing security infrastructure (such as endpoint detection and response (EDR) systems or threat intelligence feeds) often requires custom development or third-party connectors. This integration complexity can add to your overall deployment and maintenance overhead. Unlike legacy systems pieced together through acquisitions, our platform offers a unified user experience, eliminating the frustrations of fragmented workflows. In other words, you don’t need to be a rocket scientist to learn how to manage our SIEM.
Cybersecurity use cases are our bread and butter
Unlike legacy SIEM vendors who are focused on expanding their platform, we offer a different approach—one that champions quality over quantity. When you take a platform approach with a large legacy vendor you may end up having to make compromises on essential elements like EDR.
Securonix is designed specifically for security analytics and offers best-in-breed threat detection that works alongside other security vendors. Unlike many large vendors that offer general data analytics platforms, Securonix focuses on analytics and AI specifically for cybersecurity use cases. In fact, we were among the first to provide UEBA (User and Entity Behavior Analytics) to the market. This means Securonix has a proven record of applying AI technology to cybersecurity problems such as threat detection, analyzing user behaviors, and managing compliance.
We’re truly integrated and cloud-native
Many SIEM vendors have struggled to move to a cloud-based system. They have shifted their product lineup gradually, which means customers who want to switch to the cloud end up having to manage and maintain a hybrid deployment. This can result in dealing with disconnected sets of data.
In contrast, Securonix offers a fully integrated platform that’s built for the cloud across all our products. Unlike other competitors, our SIEM, UEBA, and SOAR deliver a unified experience in the cloud. All data is collected and stored just once, so all of these features can access the same dataset.
Making the Switch
If you are among the many customers looking to make a change our professional services team is highly skilled and ready to help you migrate without the migraine.
Having invested significant time and money in deploying your security solution, changing vendors can seem like a daunting task. However, Securonix’s SIEM migration experts have simplified the process by developing an easy migration method that allows adoption to happen as fast as 6-8 weeks.
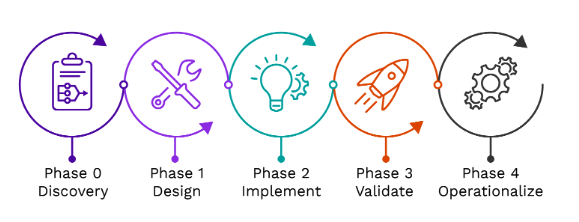
Migration Steps
Discovery: In the first phase, our team of experts will help you analyze and review your architecture and develop a roadmap for adoption. We’ll look at your existing MITRE ATT&CK coverage and identify use cases and data sources to address any gaps in detection. You will walk away with a project plan and a gap analysis report.
Design: In this phase, we will work with you to develop a comprehensive implementation plan that integrates all of your chosen data sources. We will prioritize and map your existing use cases, workflows, reports and dashboards utilizing in-house migration tools. We will then provide you with both high and low-level design documentation and details around use case mapping.
Implement: Next, our experts will deploy Securonix Hub and configure your out-of-the-box connectors to ensure all of your data sources (and contextual feeds) are integrated. In this phase your use cases, dashboards, etc. are migrated over to the Securonix platform so you can access real-time context and analytics to meet your business needs.
Validate: In this phase, we continue to optimize and validate your use cases, threat models and conduct kill chain analysis. We will test your MITRE coverage and give you a holistic understanding of any gaps.
Operationalize: In the final phase, we conduct workshops to help you refine your incident management processes. We continue to partner with you after deployment to help create and deploy playbooks and refine your workflow automation rules. This enables CyberOps teams to build tailored content and ensures quick adoption among your security team.
Next Steps
Organizations with specific security-focused requirements may find Securonix to be a better fit for their needs, particularly in terms of advanced threat detection, compliance management, and user behavior analytics. If your large security vendor is letting you down, let’s talk.
Contact us to request a demo or learn more.







