- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in April. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
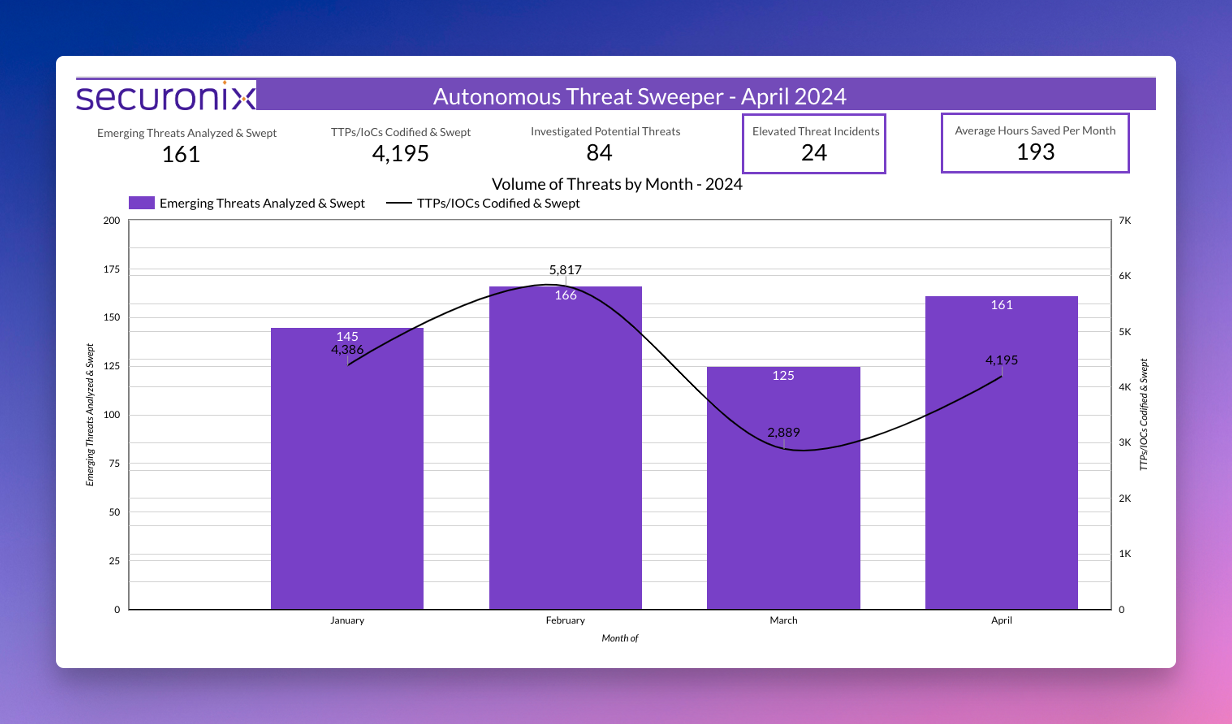
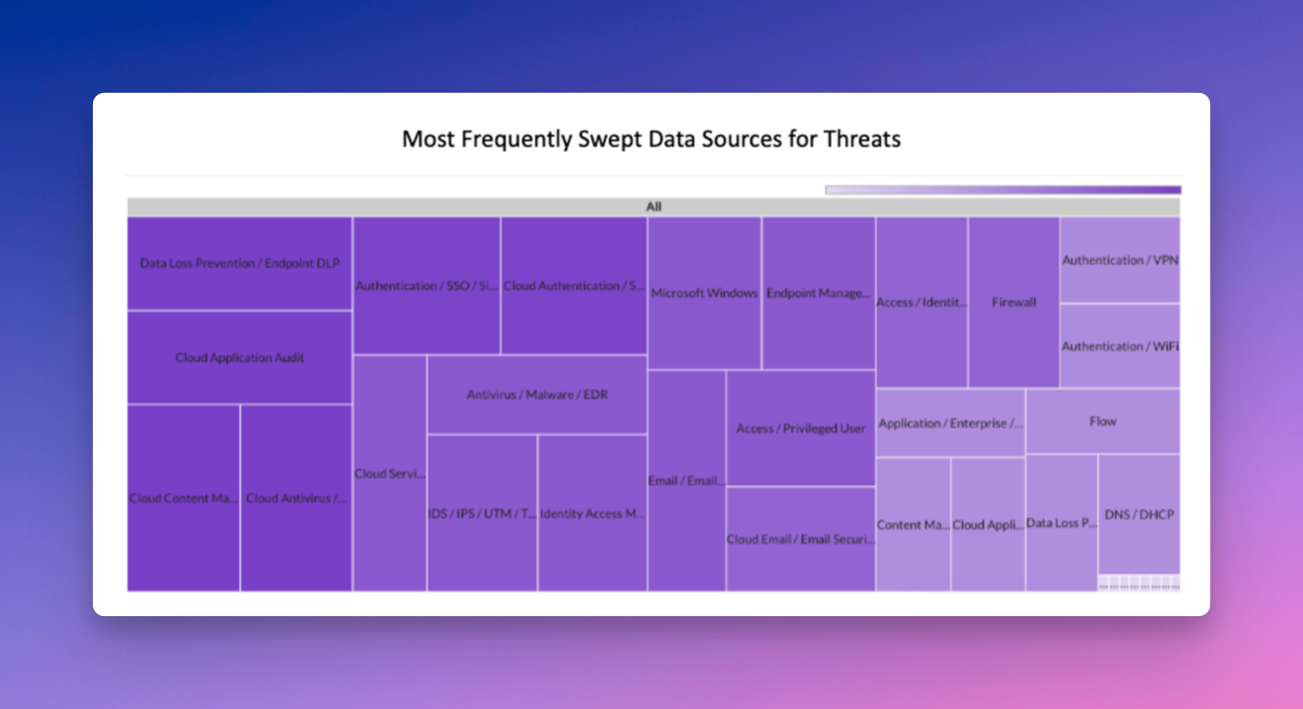
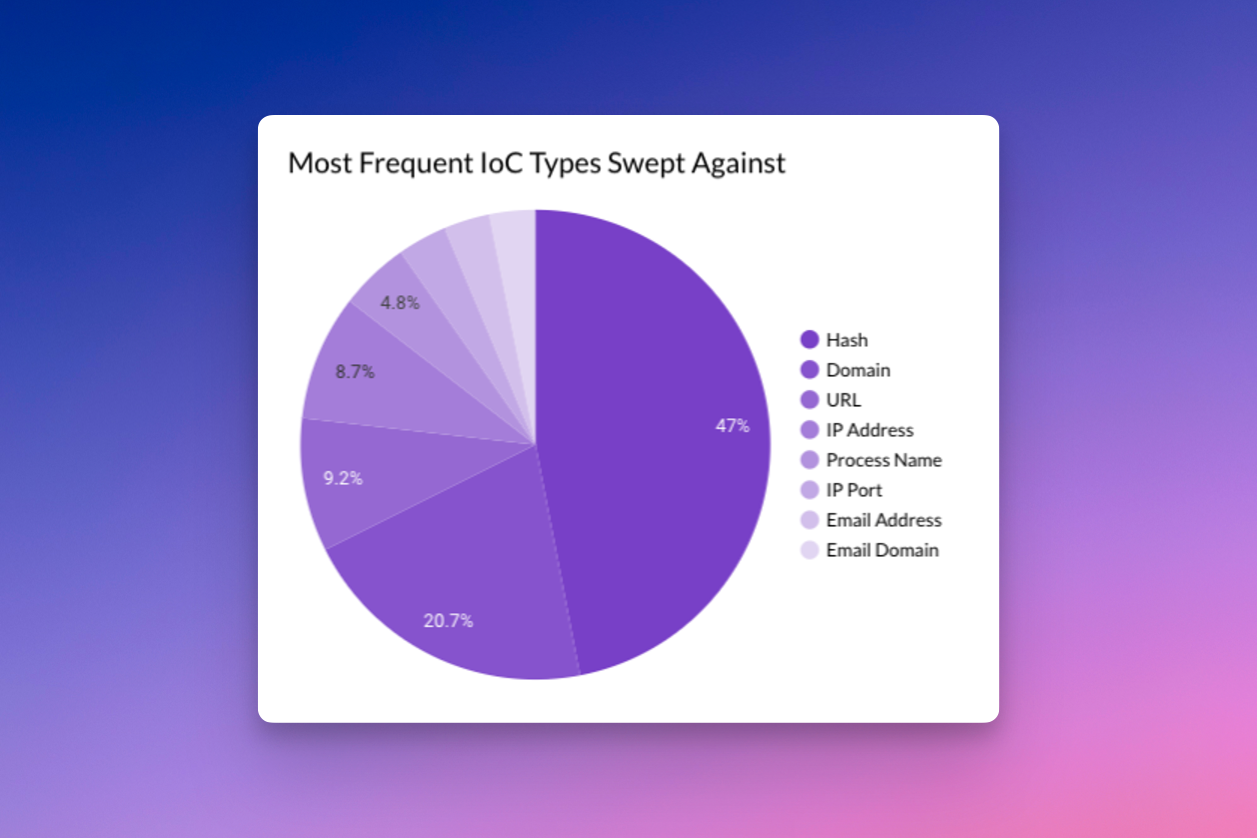
Last month Securonix Autonomous Threat Sweeper identified and analyzed 3,195 TTPs and IoCs, 161 emerging threats, investigated 84 potential threats, and elevated 24 threat incidents. The top data sources swept against include Cloud Application Audit, Cloud Content Management, Cloud Antivirus/Malware/EDR, Data Loss Prevention, and Email/Email Security.
The XZ backdoor activity
(Originally published in April 2024)
This month multiple researchers found and published CVE-2024-3094, the XZ Utils library vulnerability campaign by. One of them was CrowdStrike which is actively protecting its customers from potential exploitation. The research provides an overview of the vulnerability, its impact, and how it can be detected and prevented using CrowdStrike’s Falcon platform. The article also offers guidance for organizations to defend against the exploitation of the vulnerability, along with relevant hashes and additional resources for further information.
RedHat has issued a warning about this flaw in XZ Utils, Uptycs said in their blog. A set of XZ format compression tools commonly found in Linux distribution indicates it could potentially allow a nefarious individual to compromise SSHD authentication and obtain remote unauthorized system access. Developers need XZ Utils because it provides lossless compression for kernel images, initramfs images, software packages, and release tarballs. Because of its usefulness, XZ Utils is installed on Linux and macOS systems virtually and universally for convenience. A serious security risk raised by the backdoor has been found in XZ Utils versions 5.6.0 and 5.6.1, particularly for systems with open SSH ports.
Later this month, researchers from Securelist thoroughly examined the XZ backdoor and documented the backdooring procedure for liblzma (XZ). It is clear that this backdoor is extremely intricate and uses cutting-edge techniques to avoid detection. These include the complex code that is present in the binary itself and the multi-stage implantation in the XZ repository. The particular danger of the backdoored library is in use by the OpenSSH server process SSHD. On several system-based distributions, including Ubuntu, Debian, and RedHat/Fedora Linux, OpenSSH is patched to use system features. The purpose of the threat actors was most likely to introduce a remote code execution capability to sshd that, so far, nobody has exploited yet.
The XZ backdoor activity didn’t stop, hackers intended to Introduce further vulnerabilities using the XZ backdoor. SentinelOne researchers examined the technical details of the XZ backdoor’s implementation as well as the variations between the two variants. After looking into it, they explain and discuss how the threat actor’s minor adjustments to the code commit suggest that further backdoors were being prepared.
Threat Labs summary
Securonix Threat Labs recommends caution against these attacks and deploying the following protective measures against increased threats from the XZ backdoor:
- It is imperative to take immediate action and implement a comprehensive set of security measures. This includes promptly applying patches to address known vulnerabilities, conducting thorough code reviews and audits, and implementing strict access controls and authentication mechanisms to prevent unauthorized access to critical project repositories.
- Furthermore, continuous monitoring of community interactions and contributions for suspicious behavior, coupled with the deployment of vulnerability scanning tools and threat detection mechanisms, is essential to identify and respond to potential threats in real-time. Establishing formalized processes for evaluating third-party dependencies and conducting due diligence assessments of vendors and partners involved in the software supply chain are also critical steps in mitigating supply-chain risks.
- Additionally, organizations should prioritize training and awareness initiatives to educate project contributors and maintainers about common security threats and best practices for secure coding. Collaborating with industry peers and participating in information-sharing initiatives can further enhance the collective ability to detect and respond to supply-chain attacks effectively.
- By adopting a proactive and collaborative approach to security and implementing the recommended measures, organizations can strengthen the security posture of open-source projects and mitigate the risk of supply-chain attacks.
- 45 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the XZ backdoor include but are not limited to the following:
- Monitor for the presence of the following filenames in the directory – /usr/lib64/seahorses/
- – ‘kbioset’
- – ‘cpc’
- – ‘kkdmflush’
- – ‘soss’
- – ‘sshod’
- – ‘nethoogs’
- – ‘iftoop’
- – ‘iptraof’
Tags: Vulnerability: CVE-2024-3094 | Vulnerability Discovered: the open-source library XZ Utils, which is caused by malicious code injected by one of its maintainers.
Zero-Day exploitation of unauthenticated RCE vulnerability in GlobalProtect
(Originally published in April 2024)
Palo Alto Networks issued a warning on active wild exploits of a critical flaw in the PAN-OS software used in its GlobalProtect gateways. The vulnerability, tracked as CVE-2024-3400, has a maximum severity of 10.0 on the CVSS.
For certain PAN-OS versions and feature configurations, a command injection vulnerability in the GlobalProtect feature of Palo Alto Networks PAN-OS software may allow an unauthorized attacker to run arbitrary code on the firewall with root privileges.
The following PAN-OS versions are affected by the bug.
- PAN-OS < 11.1.2-h3
- PAN-OS < 11.0.4-h1
- PAN-OS < 10.2.9-h1
Additionally, the company stated that the problem only affects firewalls with enabled configurations for both device telemetry (Device > Setup > Telemetry) and GlobalProtect gateway (Network > GlobalProtect > Gateways).
The vulnerability was discovered and reported by Volexity first. CVE-2024-3400 has since been added to the Known Exploited Vulnerability Catalog by the Cybersecurity and Infrastructure Security Agency (CISA).
Zscaler’s global intelligence network detected activities directed towards appliances across numerous customers from various known malicious sources. This activity was noticed as soon as the exploitation script was made public on GitHub.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this vulnerability.
- We strongly advise customers to upgrade to a fixed version of PAN-OS immediately to protect their devices even after workarounds and mitigations have been applied.
- PAN-OS 10.2.9-h1, PAN-OS 11.0.4-h1, PAN-OS 11.1.2-h3, and all subsequent PAN-OS versions have this bug resolved. Upgrading to these versions will provide customers with complete protection.
- Additionally, as a favor for other frequently deployed maintenance releases, Palo Alto has made more hotfixes available to ensure the smoothest upgrading path possible for customers.
- PAN-OS 10.2:
- – 10.2.9-h1 (Released 4/14/24)
- – 10.2.8-h3 (Released 4/15/24)
- – 10.2.7-h8 (Released 4/15/24)
- – 10.2.6-h3 (Released 4/16/24)
- – 10.2.5-h6 (Released 4/16/24)
- – 10.2.4-h16 (Released 4/18/24)
- – 10.2.3-h13 (Released 4/18/24)
- – 10.2.2-h5 (Released 4/18/24)
- – 10.2.1-h2 (Released 4/18/24)
- – 10.2.0-h3 (Released 4/18/24)
- PAN-OS 11.0:
- – 11.0.4-h1 (Released 4/14/24)
- – 11.0.4-h2 (Released 4/17/24)
- – 11.0.3-h10 (Released 4/16/24)
- – 11.0.2-h4 (Released 4/16/24)
- – 11.0.1-h4 (Released 4/18/24)
- – 11.0.0-h3 (Released 4/18/24)
- PAN-OS 11.1:
- – 11.1.2-h3 (Released 4/14/24)
- – 11.1.1-h1 (Released 4/16/24)
- – 11.1.0-h3 (Released 4/16/24)
- Due to naming convention limitations, “-h” hotfix versions on Azure marketplace are instead named via the addition of an extra “0”. Ex: 11.1.2-h3 is published on Azure as 11.1.203.
- 28 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
- PAN-OS 10.2:
Tags: Vulnerability: CVE-2024-3400 | Target Product: GlobalProtect
Brute-force attacks on VPN and SSH services
(Originally published in April 2024)
Cisco Talos has detected a significant increase in brute-force attacks targeting various VPN services, web application authentication interfaces, and SSH services globally since at least March 18, 2024. These attacks, originating from TOR exit nodes and other anonymizing tunnels and proxies, utilize both generic and organization-specific usernames. Depending on the target environment, successful attacks of this type can result in unauthorized network access, account lockouts, or denial-of-service conditions. These attacks have generated more traffic over time, and this trend is likely to continue.
The targets appear indiscriminate, affecting a range of industries and regions. Known affected devices are:
- Check Point VPN
- Fortinet VPN
- SonicWall VPN
- RD Web Services
- MikroTik
- Draytek
- Ubiquiti
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against an increased threat from these malicious campaigns.
- This development coincides with the networking equipment warning about “reconnaissance efforts” that include password spray attacks aimed at remote access VPN services.
- Cisco has blocked known related IP addresses to mitigate the impact of these attacks and offers specific security recommendations for Cisco remote access VPN services. Organizations are encouraged, therefore, to maintain vigilance and put strong security measures in place to fend off changing threats.
- Users should be aware of DDoS botnets and implement fixes as soon as possible to protect their network environments from infection and prevent them from becoming bots for malicious threat actors.
- It is noteworthy that there is a possibility these traffic’s originating IP addresses are changing.
- 3930 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the brute-force to attack VPN and SSH services include but are not limited to the following:
- Monitor for rare filenames with extension – .HLJkNskOq
Tags: Attack: Brute-Force | Target: VPN services, web application authentication interfaces, and SSH services | Target Location: Globally
The latest MuddyWater attack framework
(Originally published in April 2024)
The Iranian threat actor MuddyWater has been linked to a new command-and-control (C2) infrastructure known as DarkBeatC2, which is the latest tool in its arsenal following SimpleHarm, MuddyC3, PhonyC2, and MuddyC2Go. While MuddyWater occasionally switches to a new remote administration tool or changes its C2 framework, its tactics stay consistent.
It is estimated that MuddyWater, also known as Boggy Serpens, Mango Sandstorm, and TA450, is connected to Iran’s Ministry of Intelligence and Security (MOIS). It has been actively involved in spear-phishing attacks since at least 2017, which resulted in the installation of different reputable remote monitoring and management (RMM) programs on infected systems.
The threat actor resumed spear-phishing attacks in February 2024, employing new techniques. These attacks, primarily observed in Israel, Africa, and Turkiye, leverage compromised accounts to distribute malicious files via spear-phishing emails. The group’s toolkit includes Atera and ConnectWise ScreenConnect software, facilitating remote administration management. They tailor their attacks by creating specific mail templates and malicious files named after the target, increasing their persuasiveness.
MuddyWater’s activities between October 2023 and April 2024 reveal an escalation in their campaign, particularly focusing on the misuse of the legitimate remote monitoring and management (RMM) tool, Atera Agent. MuddyWater has refined its tactics, utilizing sophisticated spear-phishing emails to distribute Atera Agents, often exploiting compromised business email accounts. The report outlines various distribution methods, including file-sharing platforms and even leveraging customer support chat services like Zendesk. Targets span across multiple sectors and countries, highlighting the actor’s broad scope. The report emphasizes the significance of compromised email accounts as a crucial component of MuddyWater’s strategy, enabling them to blend in with legitimate traffic and enhance their spear-phishing efforts.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these malicious campaigns.
- Provide the appropriate security awareness training to your personnel as MuddyWater uses spear phishing.
- Regularly apply security patches and updates to the software.
- Apply the least privilege approach across the network, with a focus on important systems and services.
- Apply best practices to secure domain controllers (DC).
- Set up multifactor authentication (MFA) to prevent lateral movement.
- 101 IoCs are available on our Threat Labs home page repository and have been swept for Autonomous Threat Sweeper customers.
Tags: Threat Actor: MuddyWater | Threat Actor Location: Iran
Securonix Threat Labs
(Originally published in April 2024)
Securonix Threat Research Labs has published several discoveries this month, such as the DEV#POPPER attack campaign, the FROZEN#SHADOW attack campaign, and the detection of DLL sideloading techniques.
An ongoing attack campaign that uses phishing emails to transmit the SSLoad malware, the FROZEN#SHADOW campaign also uses the ConnectWise ScreenConnect remote desktop software and Cobalt Strike. Phishing emails with links that download a JavaScript file that starts the infection process are used in attack chains to target organizations in Asia, Europe, and the Americas at random.
An ongoing social engineering campaign is using fake npm packages disguised as job interviews to mislead software developers into downloading a Python backdoor. The activity is being monitored by Securonix under the name of DEV#POPPER, and the campaign has been connected to North Korean threat actors. During these bogus interviews, developers are frequently requested to do tasks that include downloading and running software from seemingly trustworthy sites such as GitHub.
To comprehend a common attack technique’s variations, mechanisms, and methods of detection, Securonix Threat Research delves deeper into the “DLL sideloading” they have been observing in real-world attacks, including many of those they have identified.
Since DLL sideloading has a proven track record of evading EDR detections, it’s likely one of the most tried-and-true strategies used by threat actors to run malware and evade detections. Despite being a part of their toolkit for more than 15 years, the technique shows no signs of slowing down, underscoring the need for companies to adopt detection solutions that can aid in identifying these kinds of attack chains.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from these malicious campaigns.
- DLL sideloading:
- DLL sideloading has a proven track record of evading EDR detections and is likely one of the most tried-and-true strategies used by threat actors to run malware and evade detections. Despite having been used for more than 15 years, it shows no signs of slowing down. Organizations need to use detection tools that can aid in the identification of these kinds of attack chains.
- FROZEN#SHADOW campaign:
- Avoid downloading files or attachments from unauthorized sources. The most common file formats are pdf, iso, rar, and zip. Zip files were used in this campaign.
- Keep an eye out for common malware staging directories, particularly for any activity involving scripts in world-writable directories. In this campaign, the threat actors set up shop in the user’s %APPDATA% and C:\ProgramData subdirectories.
- To avoid detection during the FROZEN#SHADOW campaign’s multiple phases, threat actors used encrypted channels via port 443. For this reason, we highly advise implementing comprehensive endpoint logging features. To increase log detection coverage, use process-level logging tools like Sysmon and PowerShell logging.
- DEV#POPPER campaign:
- Raise awareness that individuals are targets of social engineering attacks. To completely avoid the problem, extra caution and ongoing protection are essential, even in high-stress circumstances.
- In case of code execution, keep an eye on popular malware staging folders, particularly script-related activity in world-writable directories. In this campaign, the threat actors are staged in subdirectories within the user’s%APPDATA% directory.
- Look out for non-default programming languages, such as Python, on servers and endpoints that shouldn’t ordinarily run them. Use extra process-level logging, such as Sysmon and PowerShell logging, to help with this by providing more log detection coverage.
- 86 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to detecting DLL sideloading techniques include but are not limited to the following:
- Monitor for potential DLL sideloading
TTPs related to the FROZEN#SHADOW attack campaign include but are not limited to the following:
- The TTPs for PsExec created in an abnormal location and regsvr32.exe executing a .dll remotely from SYSVOL are easy wins from a detection standpoint.
TTPs related to the DEV#POPPER attack campaign include but are not limited to the following:
- Monitor for persistence, and leverage network communication to detect.
Tags: Campaign: DEV#POPPER, FROZEN#SHADOW | Malware: SSLoad | Threat Actor Location: North Korea | Targets: Software Developers
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R