- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Security Analytics
There are a number of security technologies in place to protect your business from threats and tools to assist you in identifying threat patterns. However, you are still vulnerable to unidentified risks and zero-day threats. Trying to sharpen new policies, new content, or algorithms in production can often create ‘noise’ in the form of false positives, false alerts, and policy violations. There is a vast gap of uncertainty that ranges from known good to known poor, or malicious code. In addition, there is an avalanche of incoming data and alerts from existing tools making it even harder for response teams to know which alerts signal a true threat.
Securonix Analytics Sandbox threat modeling helps you to test, tune, and validate threat use cases against real company data before deploying them to a production environment. Sandbox threat modeling helps fine tune and manage analyst alert fatigue by enabling the ability to run threat models in a sandbox. The threat model alerts can be fine-tuned for the highest efficacy and improve your TCO.
Analytics Sandbox Threat Modeling
Traditional security solutions are reactive and rely on signature detection, which searches for patterns in previously detected threats. Data scientists, threat detection engineers, and other security teams can utilize a sandbox to test use cases at scale against production data and analyze the impact in isolation. However, a lack of response resources and rising data storage and compute requirements limit legacy SIEM’s ability to do this.
Securonix leverages the dynamic resource allocation capabilities of its cloud platform, using AWS and Spark applications to allocate resources to the sandbox environment as needed. Sandbox threat modeling allows IT teams to test malicious threat patterns in an isolated testing environment to understand how it works, as well as more rapidly detect similar malware attacks.
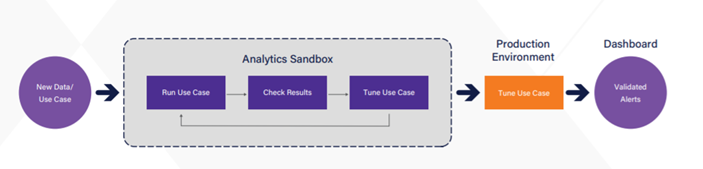
How Does It Work?
Securonix Analytics Sandbox was introduced to provide the ability to create, manage, and promote policies using production data, without impacting production or introducing analyst confusion. In Analytics Sandbox threat modeling, use cases are fine-tuned, validated, and then deployed to production.
Users can maintain entity risk ratings intact in the Securonix Analytics Sandbox until the new use cases are pushed to live production. The use cases are moved from the sandbox to production, and testers have three options:
- Delete violations (risk score) and delete meta-data (behavioral profile)
- Delete violations (risk score) and keep meta-data (behavioral profile)
- Keep violations (risk score) and keep meta-data (behavioral profile)
Analytics Sandbox helps in defending against unknown attacks, threats that have never been seen before or match any known malware on file. For example, even though standard email filters can scan emails for dangerous senders, file types, and URLs, zero-day threats can still pass unnoticed, bypassing traditional filtering. Analytics Sandbox gives a higher level of confidence, especially when a malicious email manages to get past your provider’s filters. The Analytics Sandbox widget contains all the policy violations that are used in your environment to experiment with, fine-tune, and develop policies against. Policy violations in the Sandbox widget are completely isolated from your live production environment, which means any action performed by the policy does not affect production or contribute to risk scores. For example, if a malicious email gets past your filters, then you can test new policies in Securonix Analytics Sandbox to figure out how to better catch that threat next time.
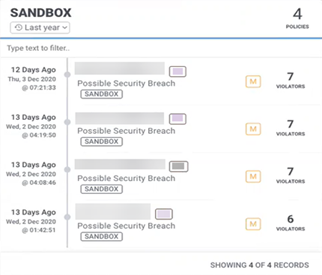
Separate Sandbox Widget in Security Command Center With Sandbox Threat Model
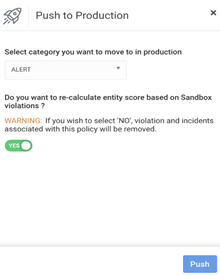
Push to Production With a Single Click
Securonix Analytics Sandbox gives security engineers the ability to test new content on their data without impacting live security operations. The sandbox widget is created to drive better focus on the type (e.g., category) of alert and lead to a focused investigation of sandbox alerts in the Security Command Center (SCC). Once a use case is sufficiently tuned, it can then be pushed to production with a single click. AWS EMR’s dynamic orchestration allows for the creation of resources for sandbox testing on the fly, deprovisioning resources once testing is completed. When your testing is complete and you’re satisfied with the results, you can move the policy violation directly to the production environment.
Benefits of Sandbox Threat Modeling
- Evaluate unknown and malicious threats: Helps you to test and work with new policies before implementing them.
- Find new threat variants: Enables the threat team to run variations of existing use cases and detect new variants.
- Build policies and test with production data, with no impact on security analysts until tuned and ready.
- Easy to push new policies to production with a single click.
Securonix Analytics Sandbox threat modeling helps security teams to replicate the behavior of real end-user systems to execute and even accelerate malicious code the way it is intended to be executed in order to detect it. Sandboxing is particularly effective at defending against unknown threats and zero-day attacks.