- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Cybersecurity teams are navigating a sea of alerts and warnings making it difficult for SOC analysts to discern whether one signifies a serious concern. The majority of SIEMs concentrate on making logs available quickly with little context. Contextual data must be included as part of the data ingestion process to reduce investigation and detection times. Contextual data allows you to view the bigger picture while investigating an alert or incident. However, most SIEMs have to manually onboard data sources for ingesting data and collecting logs. Manual onboarding is a time-consuming process.
Simplify Data Ingestion for Faster Threat Detection
Automating the data onboarding process with auto discovery of log sources and devices increases SOC efficiency. This onboarding process features an intuitive flow and fewer clicks for better user experience and providing better visibility into device status. For example – alerts and notifies when a device goes off.
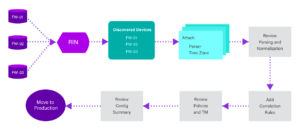
Figure1: Device Discovery
Securonix simplifies the data ingestion process by automating the onboarding of data sources to ensure faster detection and response. It provides intuitive workflows and makes it simpler for SOC analysts to easily drill down into specific events to start an investigation, assign tasks, or take actions.
In conjunction, putting log data into perspective, and how it all fits together, can aid your SOC teams in identifying genuine risks. When the security team has real-time context, they can recognize threats more quickly.
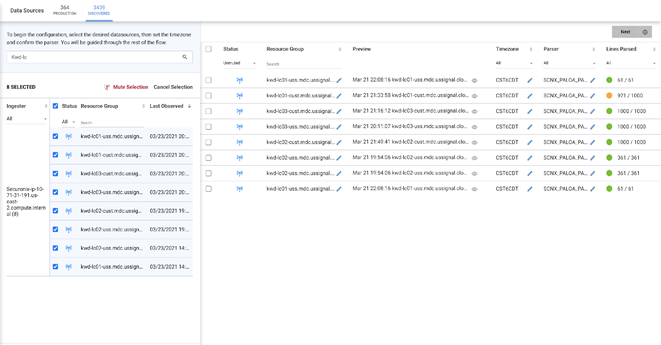
Figure 2: Securonix’s Auto-discovery of Data Sources Providing Geography, Time Zone, and Parser Information
Real-time Contextual Enrichment: Contextual enrichment is additional information gathered from your log sources to transform raw logs or alerts into meaningful insights. The data is enriched to add context for better analytics and search as the data enters Securonix. Security events can be enriched with contextual information such as user IP address, asset inventory, geo location, along with a host of other sources. When this enrichment is done in real time at the time of data ingestion, then you gain a faster incident response process every time.
Securonix adds critical contextual information to ingested events in real time. Each event is correlated with contextual information such as MAC addresses, user information, IP address, and multiple other data points. Securonix provides you the ability to search for threats on streaming data. Unlike the majority of SIEM vendors, Securonix provides real-time data enrichment and allows you to search for threats on live streaming incoming data.
How does real-time context benefit you?
Securonix provides you a narrative of users and their related events to make sense of your logs and helps you to correlate, prioritize alerts, and identify real threats. With real-time data enrichment, security logs with relevant contextual information helps SOC analysts reduce and lessen detection times. This also helps SOC teams to accurately identify stealthy and real-time threats early on.
Context is key for better incident detection and response!
Securonix simplifies data ingestion and enables organizations to gain centralized, comprehensive visibility by collecting, parsing, enriching, and normalizing data logs. Securonix provides a rich context on alerts by automatically linking contextual information through connected logs/incidents and helps SOC analysts to gain additional information from your log data of a potentially evolving attack scenario. Contextual information reduces investigation time and aids in the transformation of logs into data insights.
Securonix Nex-Gen SIEM equips you with best-in-class threat detection technology that helps your security teams to identify known threats, anomalies that may indicate unknown threats, and critical risks that may leave your sensitive data exposed.
To learn more, refer to Securonix Log Automation & Real-Time Context Enrichment
Download Solution Brief







