- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Information Security
By Aditya Tirumalai Sundararam and Sina Chehreghani
Threat actors and their love for exploiting unpatched vulnerabilities is a story that never gets old with time. Adding to the recent string of advisories from U.S. agencies about APT groups utilizing unpatched vulnerabilities over the recent months, the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory last Thursday that Russian Foreign Intelligence Service (SVR) actors have been actively scanning for and exploiting a multitude of vulnerabilities across vendors to compromise the networks of the United States and allies.
Just two weeks prior to that, the FBI and the CISA similarly issued a joint cybersecurity warning that advanced persistent threat (APT) nation-state actors have been actively exploiting known security vulnerabilities in the Fortinet FortiOS cybersecurity operating system, targeting Fortinet’s SSL VPN products. The warning was issued as a result of observations gathered around APT actors identifying and exploiting critical vulnerabilities including CVE-2018-13379, CVE-2019-5591, and CVE-2020-12812.
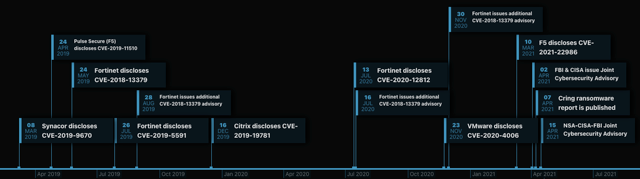
The vulnerabilities listed as part of the advisory potentially permit unauthenticated attackers to download system files, enabling them to intercept sensitive information by impersonating the LDAP server and most importantly allows attackers to authenticate, possibly bypassing the second factor of authentication. The interesting thing to note here is that attackers still continue to exploit a vulnerability like CVE-2018-13379 despite its first disclosure in 2019, and despite Fortinet issuing multiple subsequent advisories directing its customers to upgrade their systems because of its severity and ease of exploitation.
In the time since these advisories have been issued, Securonix’s Autonomous Threat Sweep Engine has identified multiple occurrences of threat actors attempting to identify and exploit these vulnerabilities. This activity demonstrates how some organizations are underestimating the gravity of these advisories and leave their platforms and systems unpatched as a result, making them hot targets for attackers to exploit. The data collected by the Autonomous Threat Sweep Engine demonstrates that the attackers are leveraging SSL VPN vulnerabilities not just limited to Fortinet, but also across other VPN products, given that organizations are continuing to invest in these platforms to support their remote workforce.
Cybersecurity and anti-virus provider Kaspersky recently cited how the Cring ransomware attacks were executed as a result of the Fortinet VPN vulnerabilities being exploited. Their report also demonstrated how attackers may have leveraged information available on the dark web that included a list of vulnerable Fortigate VPN devices. While there had been other factors identified, such as out-of-date antivirus systems and subpar privileged account configurations, that contributed to the attack, the primary cause still ended up being the vulnerability of the Fortigate servers.
Recently, there has been an uptick in attempts to exploit the unauthenticated remote code execution vulnerability (CVE-2021-22986) with the F5 BIG-IP and BIG-IQ systems. The critical severity rated vulnerability, which would enable attackers to take total control of an unpatched system, had a noticeable increase of exploit attempts occurring after proof-of-concept code was published publicly. The rapid turnaround time from proof-of-concept code to full chain exploitation continues to indicate that threat actors are eager to identify and leverage authentication bypass vulnerabilities that can ultimately lead to remote code execution.
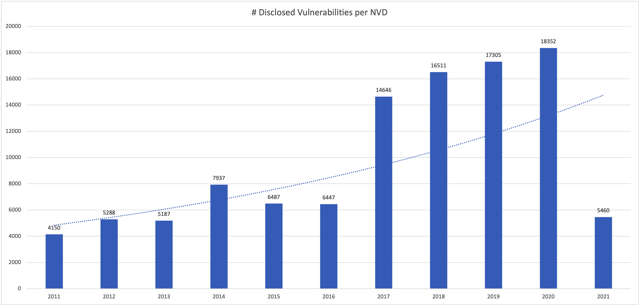
According to the National Vulnerability Database, the total number of vulnerabilities disclosed per year has increased every single year since 2017, and 2021 is showing no signs of slowing down with over 5,000 reported so far this year. Coupled with threat actors demonstrating that there is no vulnerability too old to leverage for exploitation, what should organizations be doing to reduce the risk from these threats?
- Is it time to revisit the vulnerability management program?
- Is it time to consider an agile risk classification model for assets and applications?
- Is it time to leverage SIEM platforms to provide a unified threat visibility across the environment?
These are questions that organizations should be posing to themselves in the wake of these attacks and threat actors targeting these vulnerabilities and unpatched systems. While phishing continues to be the favorite technique for attackers to gain initial access, the vulnerabilities identified in public facing applications and platforms are quickly catching up, representing a go-to vector for attackers.







