- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Predicting Attacks Is Not Easy
“Use the Force, Luke.”
The scene in Star Wars Episode IV: A New Hope – Luke Skywalker with a helmet over his head, being shot at by a training droid, with Han Solo chuckling away in the background.
Obi-Wan encourages Luke to use the Force to see the attack and block it.
Zap – Luke’s hit by a training laser!
Avoiding Problems Is Sometimes Better Than Facing Them
Today, facing an attack in an enterprise SOC is a lot like being Luke Skywalker with his helmet on. Threat intelligence is like the burn on Luke’s jacket. Threat intelligence may be able to keep you informed about security issues, but in a lot of cases, this information is provided only when you’re already under attack, and is rarely of much use except in hindsight.
Yet, in cybersecurity, we still rely on threat intelligence as a key defensive tool. Worse, threat intelligence only covers a subset of the threats that have already been found, while attackers constantly innovate – creating new malware executables, phishing domains, and attack strategies. Threat intelligence has strong value for reactionary incident response. It helps when pivoting during an investigation, identifying intent or other artifacts, and provides other similar investigative assistance. But it has limited value for detection, as threat actors avoid reusing their attack infrastructure from one target to the other. If the artifacts you will see are different than those known from previous attacks, what can you do to get ahead with your detection capabilities?
What if you could know what’s coming?
The Securonix ABA Solution: Predictive Cybersecurity
Fast forward to Luke Skywalker in Star Wars Episode VI: Return of the Jedi – he is able to predict Darth Vader’s attacks perfectly, even while facing off against the Emperor. His confidence, poise, and strength come from the surety of his knowledge and his Force-given ability to see what is going to happen. That is the ability that Securonix ABA brings to an enterprise.
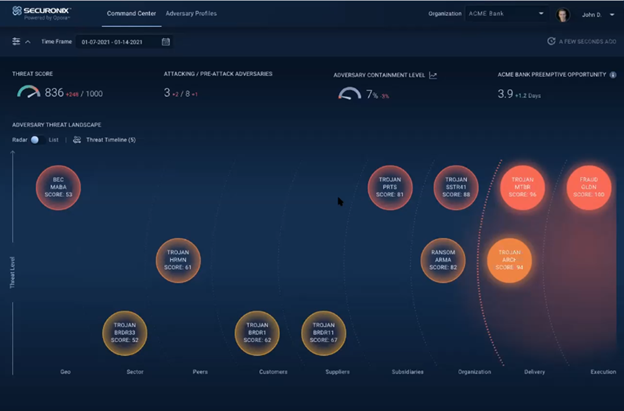
The Securonix ABA solution brings predictive analytics capabilities to cybersecurity. The solution maps adversaries, instead of threats, and analyzes their actions to predict behavior and artifacts used in their attacks. The analytics engine translates behavioral patterns into adversary attack infrastructure profiles, which indicate how (trojans, phishing, or other forms of attack) and where (subsidiaries, customers, partners, peers, sector, and geographies) attackers are planning to target your company.
ABA provides a preemptive attack map, which maps adversaries based on their stage of attack and current position within the extended enterprise landscape, along with information about the adversary, typical attack patterns, and possible countermeasures that can be taken in advance – allowing you to nullify the threat before it materializes.
The Securonix platform provides predictive detection capabilities against internal and external threats with the combination of user, entity and adversary behavior analytics. Securonix Next-Gen SIEM uses an analytics-driven approach to threat detection, while Securonix ABA provides visibility into the crucial early stages of an attack – when cyber actors are targeting, planning, and preparing the infrastructure for an attack. With this level of pre-attack visibility, SOC teams can preempt attacks and systematically contain attacks in progress. Pre-attack visibility allows defenders to tune their systems against the attack infrastructure, such as by building blacklists that include the IP addresses and hostnames of the instances being used for the attack. Other measures include fortifying enterprise systems against the specific malware that is being used to target them, making the attack impotent when it happens.
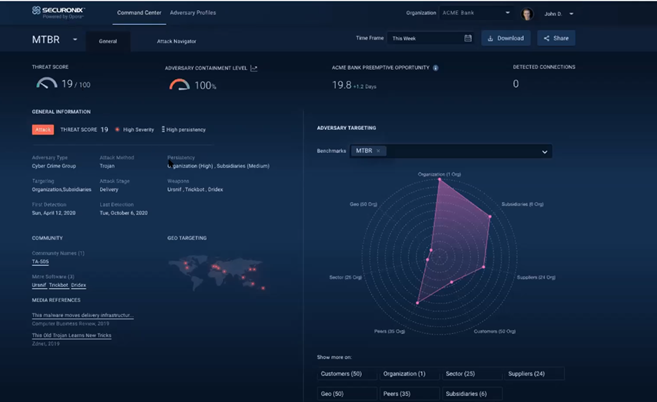
Adversary behavior analytics extends the Securonix Next-Gen SIEM’s capabilities by continuously delivering an updated analysis of adversary information and their behavior, including the entire attack infrastructure, for dynamic and preventative threat protection. Securonix ABA automatically translates adversary pre-attack behavior into pre-emptive actions or countermeasures that you can take against phishing, business email compromise, ransomware, fraud, and many other common threats.
Common use cases include:
- Adversary Threat Chaining – Correlate violations coming from the same adversary/campaign into one cohesive threat, even if different pieces of attack infrastructure are used for each event.
- Preemptive Prevention and Defense – Preemptively block an adversary’s complete attack infrastructure, such as newly created phishing domains, for preemptive defense.
- Strengthen Vulnerable Assets – Focus on and secure the most vulnerable parts of your infrastructure based on information that identifies which areas are possible targets.
The information provided by Securonix ABA is ingested by the Securonix platform and used to add greater context to existing threats, as well as providing intelligence about attacks that have not yet been realized or are in the early stages, such as reconnaissance. This allows direct action to be taken against evolving threats and a more robust defense.
Conclusion
After Luke blocks the lasers skillfully, Obi-wan Kenobi says to Han Solo, “In my experience, there is no such thing as luck.” Relying on luck to catch threats is folly, as the recent SolarWinds attack has showed us. Make your own luck with the Securonix ABA solution, ensuring that you see threats before they happen and are ‘lucky’ enough to thwart them.
Read more about how Securonix ABA can help you prevent attacks before they happen, take concrete action against adversaries, and deter attacks against your enterprise by hardening your infrastructure.
You can also reach out to schedule a demo or to discuss your specific needs.