- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Cloud Security
The cloud has delivered a host of IT and business benefits, including fast ramp-up times and low startup costs for new business initiatives, and unprecedented agility, scalability, flexibility, and IT time savings managing hardware. However, the move to the cloud can present significant security challenges, particularly as organizations rely on multiple cloud services.
In our last post on the recently released “2022 Threat Report” we discussed its findings regarding insider threats. The report offers an overall analysis of cybersecurity threat trends and the SIEM related strategies and data sets customers have employed to address them, plus some valuable best practices advice and real-world examples of techniques from the trenches useful to other organizations.

Download the 2022 Securonix Threat Report
In this post we’ll discuss the report’s cloud infrastructure findings, which have an impact on the other topics discussed. For example, the growth in the use of public cloud services has made protection from insider threats and ransomware more complex as many organizations still find themselves struggling with the best balance of cloud ease of use and appropriate security controls.
Cloud infrastructure threats: misconfiguration
Overall, the report found that the cloud presents security challenges similar to those of on-premises infrastructure, but on a geographically wider cloud-sized scale, particularly with the growth of mobile and hybrid work employees.
Cloud misconfiguration is one of the biggest challenges, according to the report. Even minor cloud misconfigurations can be much more costly than with on-premises infrastructure, shutting down multiple cloud services completely, thanks to the cloud’s unprecedented elasticity and scalability. Achieving consistency in security controls can be a challenge across multiple cloud services with different settings and management tools.
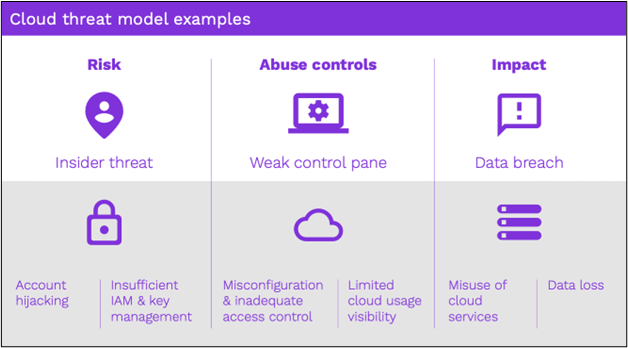
Figure 1: Cloud threat models or kill chains can be considered by grouping threat scenarios as described by CSA’s egregious 11.
Nation state actors have taken advantage of misconfiguration challenges to misuse cloud infrastructure and evade cloud defenses. In fact, many have taken advantage of the reach and scalability of the cloud to set up their own attack infrastructure running on Amazon Web Services, Microsoft Azure, and Google Cloud Platform cloud infrastructure.
Securonix is not alone in pointing out the perils of cloud misconfigurations. The Cloud Security Alliance’s Guide to Cloud Security Management and Best Practices cited cloud misconfigurations and change controls as one of the top cloud security challenges, in addition to insufficient identity, credentials, access, and key management, which are also highlighted in the Securonix report.
An April, 2022 ZDNet article, 7 Ways to Avoid a Cloud Misconfiguration Attack, stated that “Cloud security is all about configuration,” and points out Gartner’s prediction that, through 2023, at least 99% of cloud security failures will be the customer’s fault.
As with insider threats, the Threat Report recommends monitoring inherent threat indicators along with cloud services to weed out users who could potentially change control settings or update object settings intentionally or even unintentionally. This includes focusing on users exhibiting flight risk, users with upcoming termination dates, or users on watch lists for poor performance or not sharing the organization’s core values.
Insufficient IAM
Aside from misconfiguration in general, the report highlights insufficient identity access management (IAM) as one of the principal causes of cloud security breaches. This category includes disabled multifactor authentication and users misusing or elevating their roles and access privileges. Misusing IAM controls also encompasses the modification of access control lists and unapproved operations on the vaults that manage encryption, all of which can lead to data theft or loss. Compromising key management in particular could provide an attacker with total control over cloud services. IT should also look out for cloud account hijacking via phishing or compromised credentials. The report recommends SIEM monitoring of all cloud service, application, and IAM datasets.
In the next blog we’ll discuss the report’s ransomware findings, and then in a final blog highlight findings regarding the Internet of Things. Readers will find some interesting stories from the trenches in all areas the report covers that can help them craft the most effective SIEM strategies.







