- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Findlay Whitelaw, Senior Director, Insider Threat Program, Solution Engineering
Against the current backdrop of global economic, organizational, and societal disruptions we believe that organizations will face an increase in insider threat incidents throughout 2023, as outlined in the webinar ‘Navigating Cybersecurity Threats, Challenges and Innovation in 2023.’
With the growing and persistent global concerns around insider threats we recognize that organizations are actively looking to set up or strengthen their existing insider threat programs to mitigate them. While organizations must adhere to legal, regulatory, and ethical considerations when setting up their insider threat programs, they also need to ensure that their security monitoring and countermeasures are legitimate, purposeful, and compliant. Most importantly, they need to respect the personal privacy of one of their most important assets — their employees — within the boundaries of jurisdictional regulations and laws. Successful insider threat programs are attuned to balancing security and organizational interests to maintain employee trust while also demystifying the intentions or purpose of an insider threat program. Striking the right balance will avoid any unintended consequences of creating a poor organizational culture. When employees feel that they are not trusted, or that big brother is watching them, it can potentially reduce positive employee trust, create resentment, and raise concerns about breaching privacy rights.
To ensure that any unintended consequences or detrimental impacts to creating or maintaining a positive organizational security culture are minimized, organizations should look to incorporate the following steps into their insider threat deployment program plans:
Define a clear purpose statement for your insider threat program
The primary aim of your insider threat program is to legitimately protect organizational confidentiality, integrity, and availability of assets and interests while safeguarding organizational personnel and physical assets. Organizations must be transparent and clear on their insider threat program’s aims, objectives, and intentions. Focusing on personnel; physical and cyber security; the well-being and resiliency of employees, customers, stakeholders; and broader organizational interests is critical. Caution should be taken to ensure that your insider threat program should not be used to monitor productivity. However, organizations should openly acknowledge that misuse of their resources and potential conduct issues may be detected through insider threat program countermeasures and controls. Appropriate processes and remediation strategies should be established or aligned with integrity and conduct policies and procedures for transparency and completeness.
Develop your engagement plan
As outlined in our previous blog post, ‘Using a Risk Management Approach to Your Insider Threat Program,’ managing communications and stakeholder interest is critical. I suggested creating a stakeholder map and a RACI matrix to ensure that all stakeholders and interested parties understand the program’s purpose and their participation. It is widely recognized that, within a holistic insider threat program, several vital stakeholders have vast interdependencies, including responsibility, accountability, consultative, and informative priorities or interests.
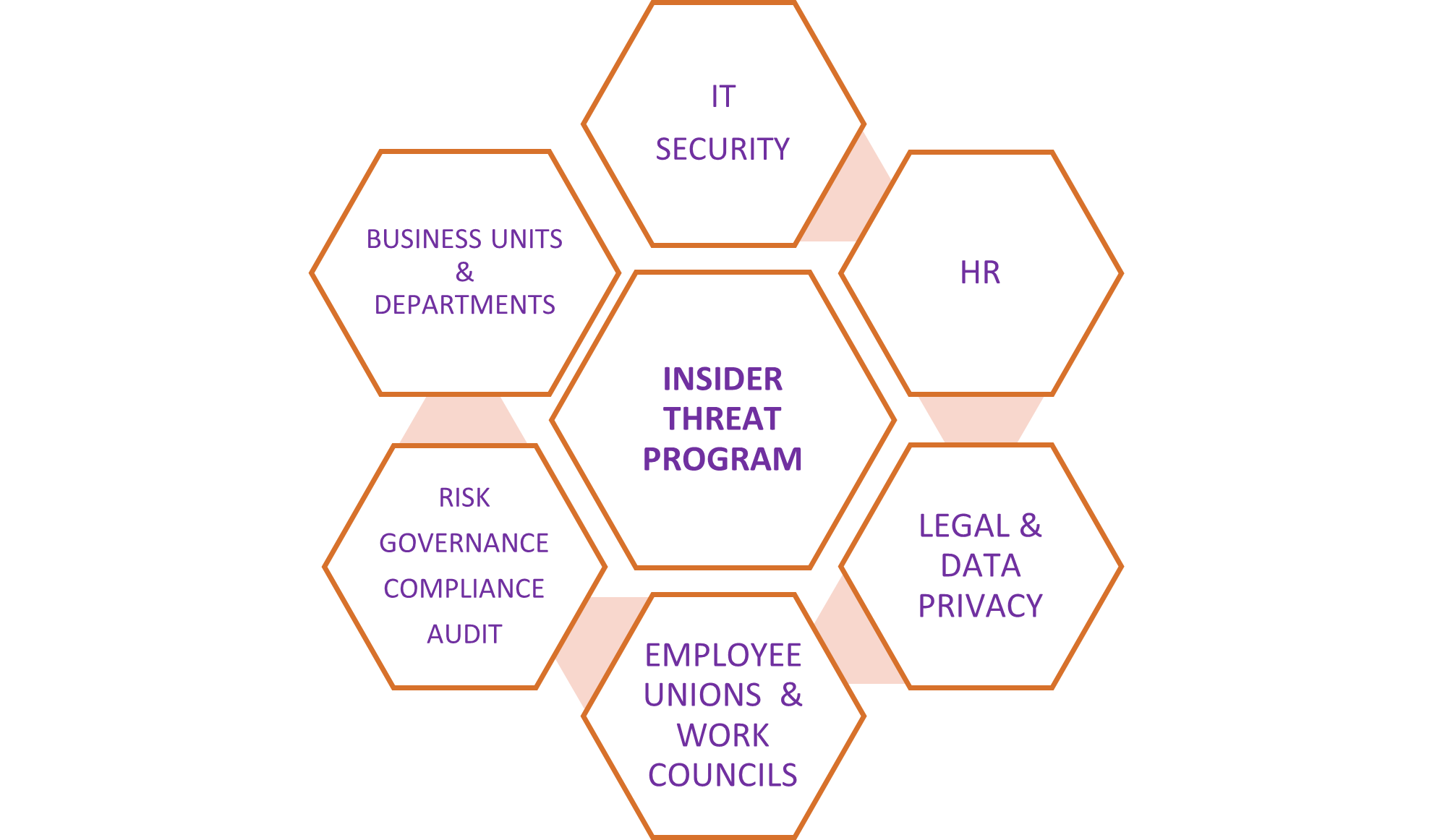
Example of an insider threat program stakeholder map
Notwithstanding the diverse organizational structures, industries, hierarchies, size, scale, and jurisdictions, there will be varied approaches to setting up your insider threat program. The HR department may be responsible for the organizational people risk or personnel controls, for example, along with employee screening and vetting, where adverse outcomes may be flagged for criminal, credit, or fraud checks. In contrast, IT security departments would typically be responsible for technical detection and preventative controls, such as data loss prevention (DLP), user entity behavior analytics (UEBA), multi-factor authentication (MFA) controls, and phishing tests, to name a few.
As you develop your engagement plan, the jurisdictional footprint of the organization and associated data privacy obligations need to be well understood and factored into the development of the overall program. For example, updating data privacy is necessary in a manner that employee rights and protections are not contravened. Establish robust processes to ensure that data handling, processing, and storing requirements are purposeful, legitimate, and proportionate to the identified organizational insider risks. Consideration, for example, should be given to balancing employee privacy with anonymizing or pseudonymizing data to protect employees’ identities throughout the investigation process. Engage early with workers’ unions and works councils to establish open communication lines. This will ensure employees have a voice at the table and are central to discussions about insider threat program monitoring and proposed safeguarding processes. Cross-organizational buy-in and collaboration between and across your stakeholder map are vital to deploying and operationalizing your insider threat program.
Go beyond deploying traditional compliance-based security training and awareness programs
As mentioned in our previous blogs and webinars, people are our first line of defense. Sometimes referred to as the human layer, it is often acknowledged that humans are the weakest link in the security chain. This is because humans are susceptible to making mistakes and we are vulnerable to social engineering attacks. As social beings, we have the predisposition to trust readily, thus being open to exploitation. Given these risk factors, investment in creating the right communication message is paramount to building and maintaining positive organizational employee trust outcomes.
Identifying and segmenting your employee population and understanding who, if targeted, could potentially cause significant harm or damage to your organization can help deploy targeted or enhanced mitigating controls. Identifying employees with privileged access to systems, premises, or access to the most sensitive and confidential organizational data is prudent. Therefore, considerations to supplement your current security training and awareness program by segmenting your organizational populations with additional, tailored content is advantageous. This will help strengthen a better security culture and understanding. Highlight the reasons why this population is targeted by criminals or threat actors who want to gain access to data, systems, or property through exploiting social media platforms and social engineering, including targeted phishing campaigns, vishing, and smishing.
While traditional security training and awareness security programs aim to provide a framework of policies and procedures to manage and minimize risk to people, processes, assets, and premises, the critical success of your program must go beyond the so-called ticking of the training and awareness compliance box. This security training and awareness approach can leave individuals feeling disengaged, disinterested, and inconvenienced but feel they must comply with little to no impact on positive organizational security hygiene. Your security training and awareness program must inspire long-term, sustained behavioral and cultural changes across the organization with appropriate measures of effectiveness. Compliance, command, and control security training and awareness programs are ineffective. Educating, learning, and providing advice about emerging and real-life threats by focusing on industry-specific trends and putting your organization at the center of the security training and awareness program brings to life the importance of security controls, including the insider risk and threats. Most importantly, it highlights how individuals play a significant part in protecting organizational assets, feeling engaged, equipped, informed, and aligned with organizational security goals.
Understand your Insider threat program processes from an employee journey perspective
Outlining your insider threat program purpose only goes so far in providing employee confidence and trust. Considering how security monitoring and personnel controls will impact your employees needs to be assessed, including an end-to-end process review around the organizational approach, responses, and remediation strategies that are in place or need to be in place through an employee lens.
While acknowledging that security measures are in place to safeguard organizational, employee, stakeholder, and customers (notwithstanding the data privacy and employment obligations), we must recognize that some safeguards can and may impact employees adversely from a health and well-being perspective. This may result in employees feeling threatened, vulnerable, and anxious due to additional or enhanced security precautions and measures in place, thus having a counterproductive effect on the insider threat program’s purpose. The insider threat program should consider not only insider threat detective controls but also preventative and supportive measures. Pre-empting and identifying potential gaps in your insider threat program processes that can diminish employee trust will provide long-term benefits. Having transparent communication, support, and preventative intervention strategies underpinned with support aids and materials to limit and minimize potential conflicting employee sentiment can positively influence continued employee trust.
Conclusion
The four steps outlined above will aid in establishing foundational steps to maintaining employee trust when setting up your insider threat program. In summary, the key takeaways are:
- Establish a clear purpose
- Prioritize engagement
- Promote collaborative consultation and inclusion and strive for sustainable behavioral and cultural security hygiene factors
- Demonstrate sincere organizational commitment to supporting individuals throughout their employment lifecycle
Following these steps will inevitably make for a happier, more motivated, resilient, safer, empowered, and educated organization resulting in fewer insider incidents or breaches.
Sources:







