- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Findlay Whitelaw, Field CTO, Securonix
In an era where cyber threats morph at an unprecedented pace, a startling statistic stands out from the recently published 2024 Insider Threat Report, commissioned by Securonix.
Over 70% of respondents of organizations feel that they lack the right tools to protect their sensitive information and systems from insider threats. These statistics are just not alarming; it’s a call for a deeper understanding and strategic response to an often overlooked aspect of cybersecurity.
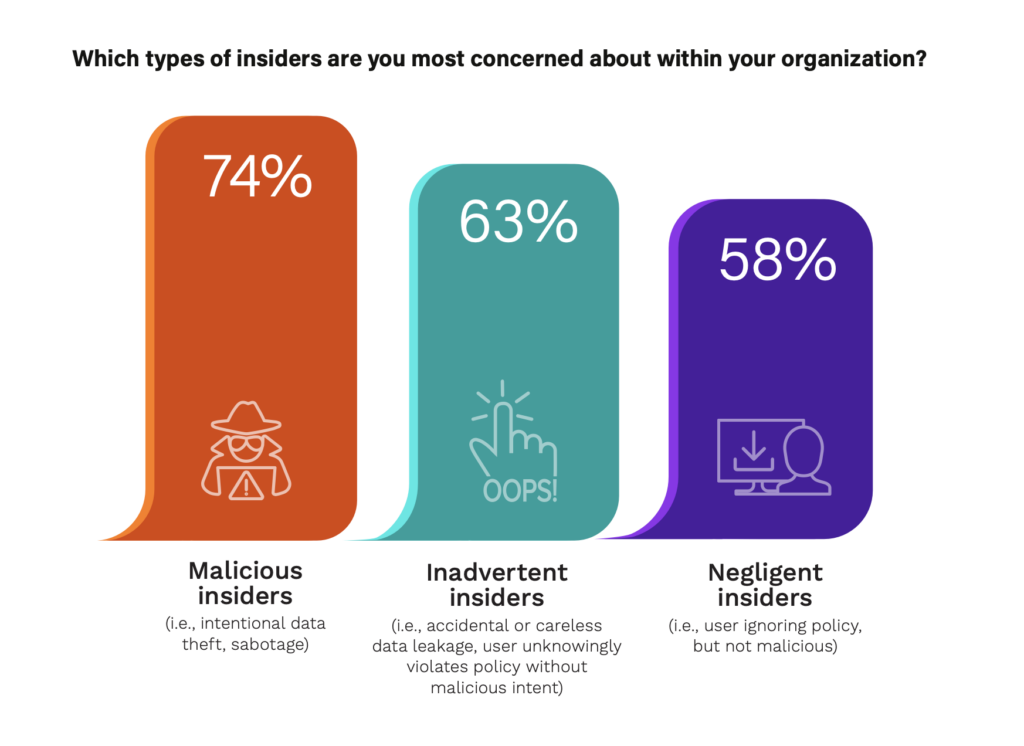
First, let us understand insider threats and where they come from. Insider threats can come from employees, contractors, or business partners with legitimate access to information, data, systems, security practices, and premises. The three types of insider threats can be categorized as:
- Malicious insiders – who intentionally seek to cause severe or material harm
- Inadvertent insiders – who unintentionally cause harm through carelessness or by accident
- Negligent Insiders – who ignore policies or procedures, but their intent is not malicious
While our survey found that organizations are concerned about these categories, 74% of respondents are most concerned about malicious insiders.
The threat from insiders is multifaceted and can be driven by disgruntled employees stealing data, negligent employees accidentally leaking or disclosing sensitive and confidential information or even someone who has infiltrated or coerced an unwitting employee as an accomplice.
There are several challenges in mitigating insider threats, including the complexity of detecting them. Unlike external attacks, insider threats are more challenging to detect as they often involve misusing legitimate access. The 2024 Insider Threat Report also found that respondents believe that 90% of attacks were either more difficult or about as difficult to prevent and detect as external cyber-attacks.
Lack of adequate tools may be one potential factor with traditional security tools tuned to guard against external threats, leaving a gap in monitoring and analyzing internal behaviors. To bridge this gap, advanced technologies like next-generation security information and event management (SIEM) and user and entity behavior analytics (UEBA) play a crucial role. Next-gen SIEM provides advanced analytics and machine learning capabilities, integrating real-time data analysis and AI from applications and networks and helping correlate diverse security events to spot anomalies that might indicate insider threats. UEBA focuses on user behavior, leveraging advanced analytics and machine learning to identify activities that deviate from the norm, and flag potential insider threats.
Integrating next-gen SIEM and/or UEBA can create a more robust defense mechanism against insider threats. SIEM, which correlates data sources across various sources, complements UEBA user-centric anomaly detection, offering a comprehensive view of potential security breaches.
As insider threats continue to be a significant concern, recognizing the limitations of traditional security tools is the first step toward better preparedness. Incorporating advanced technologies like next-gen SIEM and UEBA, coupled with robust security policies, employee education, and awareness programs, can significantly strengthen an organization as a defense against these covert threats.