- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
How Securonix Investigate is changing how we investigate and hunt for incidents
The Need for Context and Collaboration
As you work to effectively detect and respond to incidents, investigation plays a major role in uncovering valuable details about incidents. Gathering context throughout the investigation process is critical to accurately determine the nature of an incident. WIthout this understanding of an incident, it is nearly impossible to take the precise action needed to mitigate the threat.
To resolve issues more effectively, you just need to gather all the context around the incident, right?
To say you need as much context as possible is simple in theory, but difficult in practice. Consider the number of entities in your environment multiplied by the vast number of systems that can contain context about those entities. The result equates to an unfathomable amount of data that would need to be collected, organized, and stored. However, only a relatively small amount of that data would be needed or used. Also, investigations are not always sequential in nature. In other words, as you move through the steps of an investigation the need for more context may be uncovered as shown in Figure 1. This need for additional context may require you to go look within different systems that you would not have previously considered.
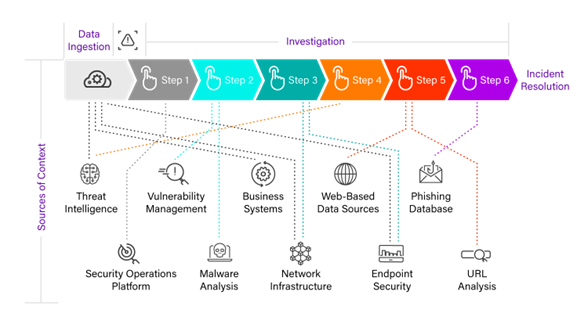
Figure 1
Securonix Next-Gen SIEM has long been able to enrich content with context from IT, security, and business systems. This allows us to provide a certain level of context around incidents or alerts at the time of ingestion.
However, what do you do when you are in the middle of an investigation, and you need more details or updated details about an entity? In the past, you would have two options, neither of which are efficient and require a lot of time and effort on the analyst’s part:
- Option 1: Manually go to each source to find context then stitch it all together to try to understand details about the entities involved in the incident.
- Option 2: Develop and launch playbooks to go to these sources of context and extract data that relates to the entities involved in the incident.
Security organizations also need to build a collective knowledge base across teams and quickly share insights to accelerate investigations. To do this, security analysts need to capture information discovered during investigations without pivoting to external tools like ticketing systems, email, or instant messengers. This pivoting to external tools delays progress. Additionally relying on these external tools does not connect insights to specific entities or retain those insights for future use.
Enter Securonix Investigate
Securonix has delivered a new solution that offers a more eloquent and effective option called Securonix Investigate. Securonix Investigate expedites incident investigation and response with on-demand context and analyst collaboration.
Securonix Investigate automatically extracts context from internal and external sources for in-flight investigations. This means as investigations progress analysts can gain the context they need without having to manually search and correlate it. Analysts can also annotate findings within the investigation workflow to share knowledge without pivoting to external tools like ticketing, email, or messaging platforms. This annotation capability aligns insights to specific entities and builds a knowledge base that can be applied to future incidents.
Securonix Investigate enables instant and dynamic enrichment of any workflow via a free-floating overlay window during triage, investigation, and hunting as shown in Figure 2. You can gather context from your security operations, threat intelligence, penetration testing, endpoint security, internal data repositories, and many more systems that store relevant data.
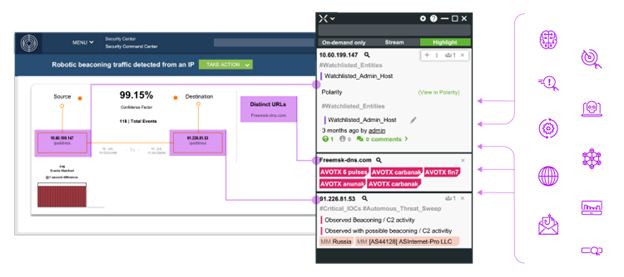
Figure 2
You can add details to investigations in flight by automatically gathering new or updated contextual data when and where you need it. This timely context brings threat details to light to speed incident mitigation. With Securonix Investigate you can note key findings directly within the context window to share knowledge and collaborate across teams. This information sharing is done by annotating context strings with relevant insights.
Securonix Investigate allows you to:
- Take advantage of on-demand data enrichment adding or refreshing context about alerts or entities at any time to keep details up-to-date and relevant.
- Annotate within workflows providing the ability to comment, document and share observations made during investigations to improve efficiency.
- Collaborate across teams by sharing specific information within trusted groups, such as red, blue, and purple teams, through dedicated channels.
Securonix Investigate accelerates threat mitigation by dynamically enriching incidents under investigation with context and intelligence. You can better understand threats by bringing key context forward by integrating Securonix Investigate with internal and external data sources. This context is presented in the local language regardless of where it originated. More effectively communicate knowledge across teams by annotating, documenting, and sharing observations across trusted groups within investigation workflows.
If you would like to learn more about Securonix Investigate please visit our webpage here.







