- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM

SWIFT is the primary method by which banks and financial institutions around the globe move money between one another. Swift has been in existence for over 40 years, and has had its share of high-profile security issues. As a consequence, SWIFT has been at the forefront of developing security and countermeasures. However, while SWIFT is more secure as a system, there are still considerable vulnerabilities in its users and clients.
In 2016 the Bank of Bangladesh was hit by a massive SWIFT infrastructure attack. Attackers implemented an elaborate plan to withdraw over $950 million from the bank’s account with the Federal Reserve Bank of New York. Of that, $81 million was never found again after it was laundered through the Philippine gambling industry.
This attack, though, was just the highest-profile one. The SWIFT transaction system has been the target of malicious attacks for years now, with close to $167 million stolen in eight high-profile attacks between 2013 and 2017 – amidst several other low-profile ones.
One aspect of these attacks stands out, though. In nearly all cases, the problem was not with the SWIFT infrastructure or messaging system, but the member financial organization.
A later review revealed that the Bank of Bangladesh attack was planted long before it happened, with a malware program sitting within the bank network, silently gathering information, and feeding the attackers. This was one of the biggest cyber heists in history, and forever changed the way security was considered by SWIFT.
The SWIFT System and Development of the Customer Security Program
Although SWIFT does not hold any funds, member institutions use the network to transfer billions of dollars every day. With an average transaction volume of 38.8 million messages per day, SWIFT is a prime target for malicious attacks. Realizing this, SWIFT has been developing a focus on cybersecurity with initiatives such as the development of the secure public key infrastructure (PKI) for SWIFTNet.
SWIFT also put in place the Customer Security Program (CSP) with the goal of improving the cyber-security maturity of its members and to make the overall SWIFT system more mature. The CSP mandates that customers are responsible for the security of their SWIFT environments, and it provides a security framework for member organizations to comply with – the Customer Security Controls Framework (CSCF).
From Q2 2017 onwards, all organizations using SWIFT were required to annually attest to SWIFT that they were in compliance. From 2018 onwards, full enforcement came into action, with non-compliance leading to a report to financial regulators and SWIFT partners.
Achieve CSCF Compliance With Securonix
The Securonix platform provides a wide range of capabilities to address SWIFT CSP requirements. Along with broad coverage of the CSCF v2020 controls, Securonix provides the following capabilities:
- Behavior baselining and identification of malicious activity by SWIFT users.
- Correlation and enrichment of SWIFT transaction data across multiple financial institutions, from both within and outside the SWIFT environment, in order to identify larger attack patterns.
- Detection of anomalies relating to network, database, application, and endpoint activity within the SWIFT infrastructure, such as process injections, DLL loading, and other attacks (such as ElectricPhish/PowerShell attacks by the Lazarus Group).
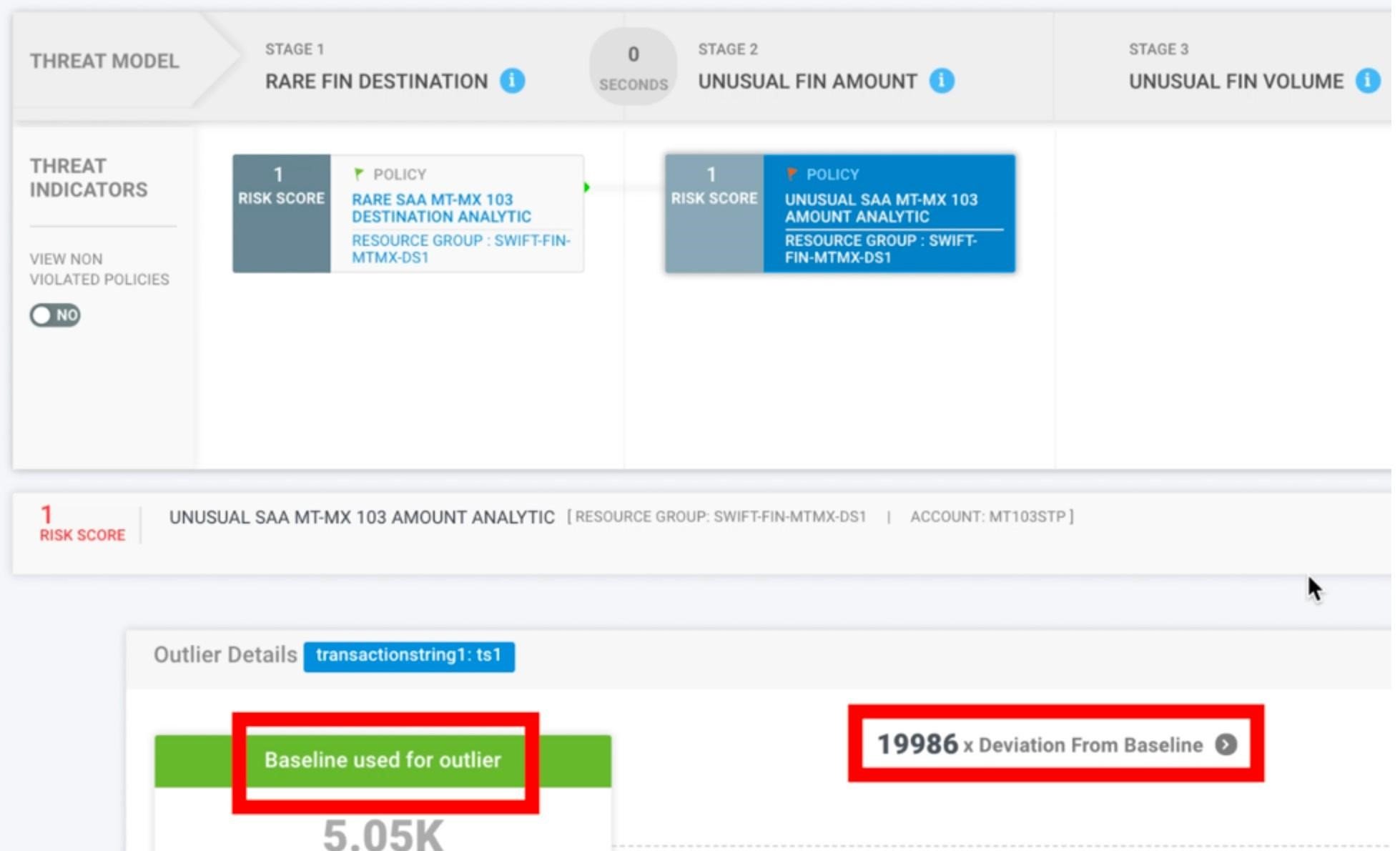
A SWIFT Attack Detection Example







