- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
By Augusto Barros, VP, Cyber Security Evangelist
In a previous post we discussed some of the salient points and conclusions in ThoughtLab’s May 2022 report, Cybersecurity Solutions for a Riskier World, which attempts to determine how organizations can drive the best cybersecurity performance in a world of escalating digital risks.
There were several interesting findings relevant to Securonix users, but perhaps the most important — and one that is likely to ring true with financial organizations — is that a risk-based approach to cybersecurity is key to success. According to the report, leaders in risk-based management saw fewer security incidents and material breaches in 2021 than beginners and organizations that were advanced in their NIST Cybersecurity Framework implementation employed a strategy centered on a risk-based approach and supply chain risk management.
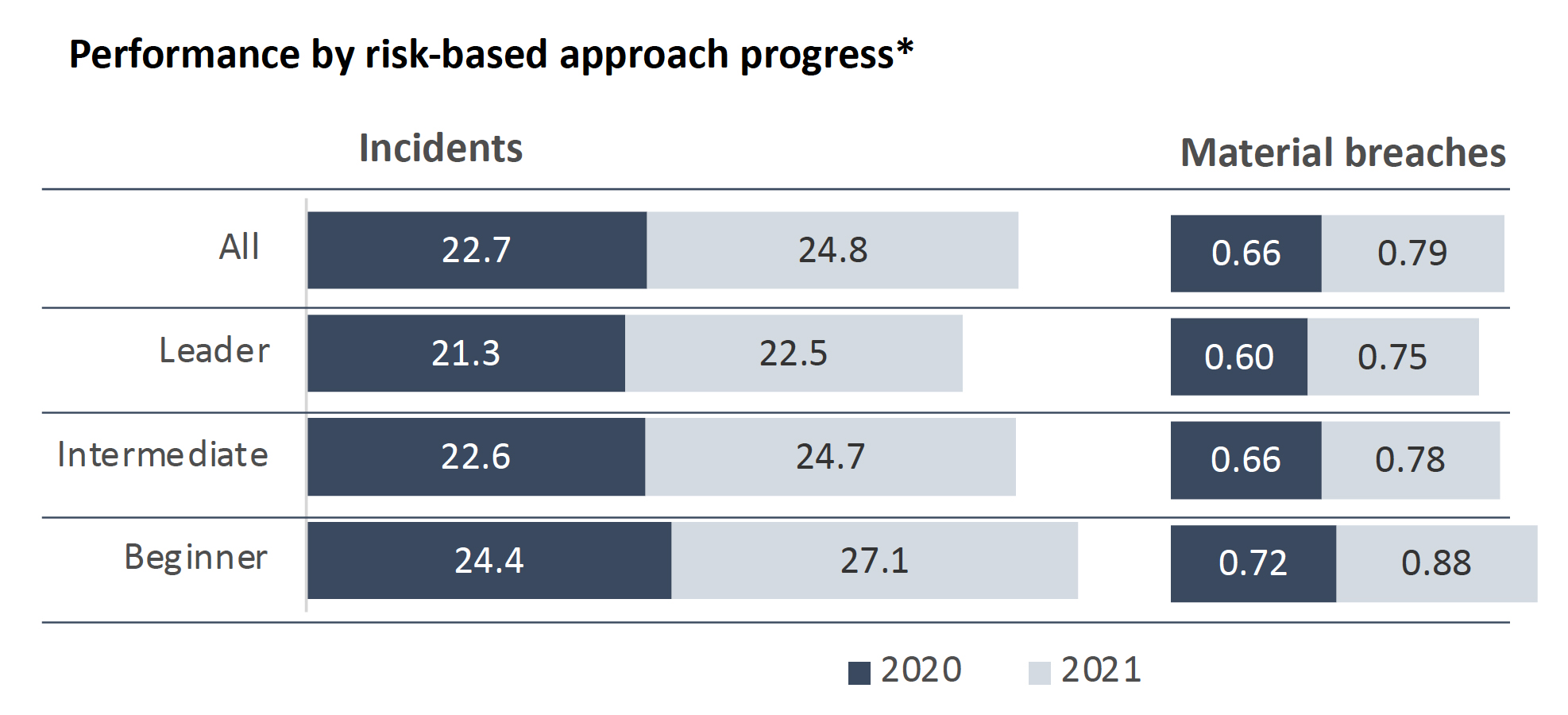
This is a good opportunity to delve deeper into what constitutes a risk-based approach to cybersecurity, where many organizations fall short, and how best to achieve it.
You can’t do it all
A risk-based approach to cybersecurity is based on the truth that an organization “can’t secure everything a hundred percent,” as Gary McAlum, Board Director of the National Cybersecurity Center, says in the report. Recognizing this unpleasant reality, organizations can achieve the best results by focusing investments and resources where their biggest cybersecurity risks lie, which means they must understand the business they aim to protect first. Identifying its greatest business risks and then determining their associated vulnerabilities and cybersecurity threats helps them decide where to direct cybersecurity resources and investments for maximum success.
McKinsey advises that businesses start by “identifying the largest sources of enterprise value across teams, processes, and technologies,” then identifying vulnerabilities across those categories. For example, as McKinsey discusses, a loan process might be most vulnerable to data leakage, while a payment process might be most vulnerable to fraud. Naturally, threats should also be taken into account; vulnerabilities where no threat activity exists or is anticipated will not generate as much risk as those being actively targeted by threat actors.
Unfortunately, according to the report, less than half of all firms have fully implemented the area of the NIST Cybersecurity Framework that covers developing and understanding of cybersecurity risks across the organization. Perhaps not surprisingly, insurance firms, whose primary business is risk management, are ahead of the pack with 49% of them fully implementing, while finance firms come in a close fourth at 47%, after telecom and aerospace firms.
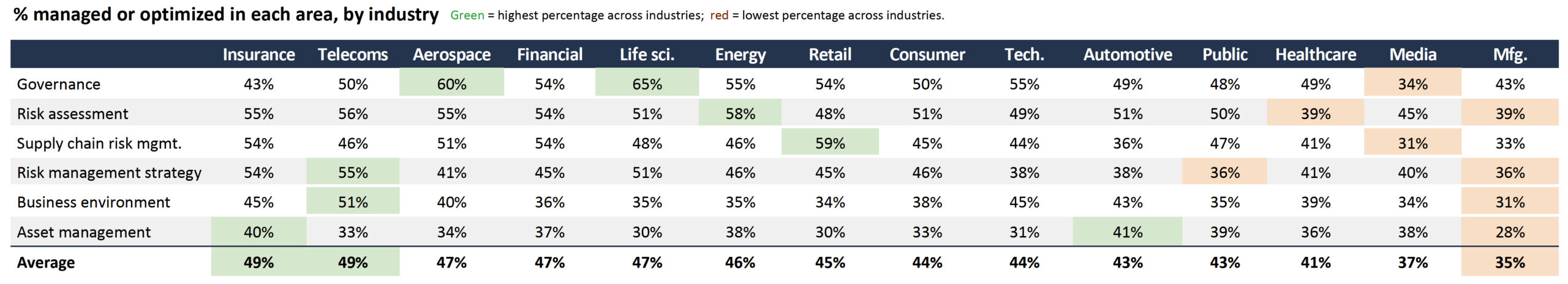
Watch your suppliers
According to the report, CISOs have increased their role in vendor and partner management, and in fact, organizations that are most advanced in supply chain risk management generate faster times to detect, mitigate, and respond.
Steve Durbin, CEO of the Information Security Forum cautions that organizations must move beyond understanding just their tier one and tier two suppliers to ensure that all their suppliers understand their security requirements. If a client needs to be more secure, then it’s up to you to show them how.
Duc Lai, CISO of the University of Maryland Medical System, advises applying a “least privilege principle,” allowing suppliers to access only what they absolutely need to, and ensuring there are no unused supplier connections and that suppliers are offboarded as soon as you stop using them. Zero trust approaches for network connections and continuous monitoring are good ways to ensure the principle is correctly and continuously applied across the supply chain.
Motorola Mobility CISO Richard Rushing says that your supplier contracts should have explicit provisions for reporting breaches and incidents within 72 hours, regardless of whether it involves your data or not, as time is precious when it comes to security threats.
Response planning lags
Unfortunately, in addition to identifying risks, most organizations also fall short in response planning, mitigation, and communications, according to the report, with less than half of the organizations surveyed in the managed or optimized stage for most response areas. Insurance firms come in first again in this category at 60%, but financial firms come in a distant fifth in response planning at 48%, behind life sciences, telecoms, energy firms, and public sector organizations.
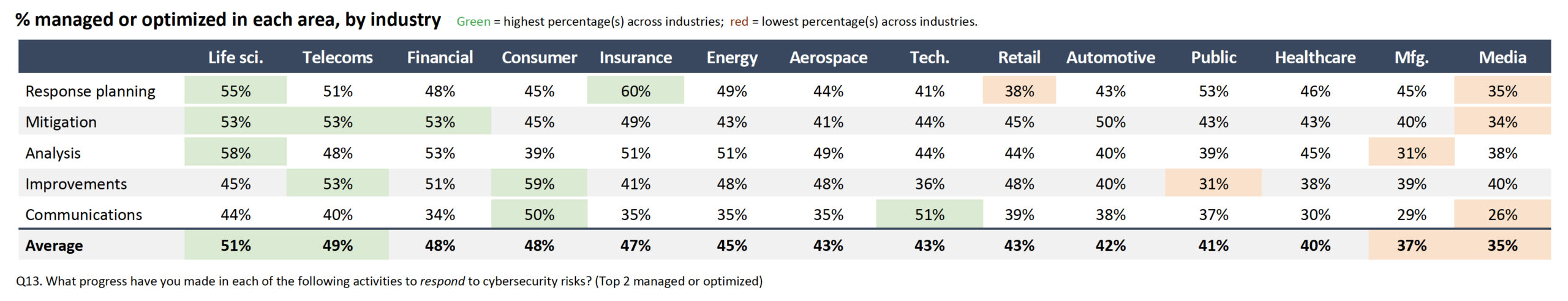
Communication is a widespread weak spot. Investing time and resources in developing clear and consistent communications protocols is critical for success.
Effective cross-team collaboration is another key to success. Only 37% of executives report that their cyber teams work with IT business teams when they develop tech enabled processes, products, and services.
To get the best results, according to the report, organizations also must combine a risk-based approach with the use of cybersecurity frameworks. Assessing event likelihoods and impacts as part of quantitative risk assessments is a complex undertaking, and frameworks can help reduce the number of points that must go through the entire process. Again, insurers are ahead of the game with a risk-based approach, as are all enterprises with over $20 billion in revenue.
Consolidate
Once you focus on the risks that are most important to your organization, consolidating tools to address them can make the whole mitigation process more efficient. According to the report, consolidating tools and infrastructure is often a better approach for most organizations than relying on disparate, disconnected solutions and systems and reducing costs. Again, insurance firms (41%) are ahead consolidating tools and infrastructure. A third of organizations are adopting technologies that bring together capabilities to work as a single platform. Solution providers are evolving their products to answer these expectations. Securonix, for example, allows organizations to combine SIEM, UEBA, security data lake, and SOAR on a single, fully integrated platform.
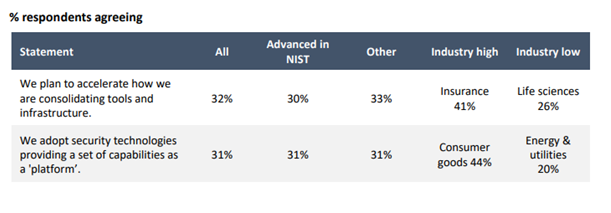
To get a deeper view of risk-based approaches to cybersecurity, download the ThoughtLab report here. You can also listen to a very enlightening webinar on how behavior analytics can be incorporated into an insider threat program to reduce the number of alerts and make investigations faster and easier here.







