- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Security Analytics
By Abhishek RVRK Sharma, Senior Technical Marketing Engineer at Securonix
In security, behavioral analytics allow you to find anomalous behavior which could point to an attack. For example, look at the school of fish in the picture above. Can you find the fish behaving oddly? Take a second or two and you’ll find them.
Finding behavioral anomalies is easy when everything is standing still, but both attackers and your company will not stand still while you hunt for threats. How then can you find out if somebody with access to your organization is behaving differently and creating problems? By using behavioral analytics.
Behavioral anomalies can be the first indication of a significant data breach or malicious attacker. Detecting relevant behavioral anomalies among the multitude of security events populating your Security information and event management (SIEM) solution is a nigh impossible task. With a legacy SIEM, detecting the disgruntled employee who decided to send your latest product requirements document to your competitor isn’t possible. Legacy SIEM solutions are unable to find behavioral anomalies because they lack the behavioral analytics required to do so. With Securonix’s behavioral analytics, however, it is a piece of cake.
The Securonix platform leverages industry-leading user and entity behavior analytics (UEBA) to understand and baseline user and group entity behaviors, and then use those baselines to identify anomalies. It enriches alerts with additional context in order to produce context-aware threat chains that your analysts can then act upon.
To achieve this industry-leading behavioral analytics capability, Securonix utilizes multiple analytics techniques. The analysis framework looks at multiple behavioral indicators in order to identify anomalous behavior, which may be indicative of a threat that is developing, or already present, in the system.
- Entity Behavior: The behavioral baseline of every entity is tracked, maintained, and updated. This enables the identification of anomalous behavior which may lead to a breach.
- Peer Group Behavior: The baseline behavior of the entity’s peer group (system administrators, finance department users, etc.) is benchmarked against individual members. Anomalies discovered (such as a user accessing an IP address that is not accessed by any other member of the group) are identified as possible risks.
- Rare Behavior: Behavior that is rarely seen from the user, such as a significant change in the amount of data downloads, is identified as a possible risk.
- Network Behavior: Suspicious behavior on the network, such as traffic on an unexpected port, related to an unexpected protocol, or packets being sent or received from a blacklisted or unknown IP, is identified as a possible risk.
- System Behavior: Unusual system behavior, such as open ports that are usually not seen to be open or unexcepted services or applications running on the system, are identified as possible risks.
- Robotic Behavior: Repetitive, pattern-driven behavior such as multiple login failures within a very short span of time is identified as a possible risk.
- Enumeration Behavior: Behavioral patterns that indicate enumeration-based information gathering, such as attempts to accessing user information from Active Directory, is identified as a possible risk.
Behavioral analytics work alongside threat chains to put behavioral anomalies in context and identify and prioritize threats. Even hard to find low and slow threats (that act progressively over a period).
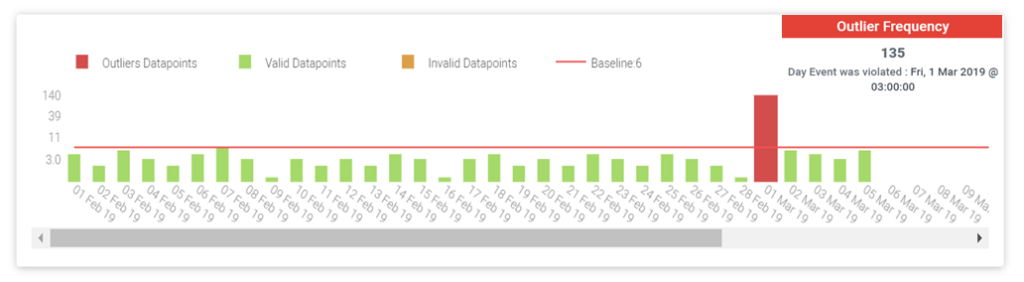
In the example below we have a baseline of failed logins per day for a user. As you can see, the average number of failed logins per day is around 5. Yet, on the 1st of March, there were 135 failed logins.
This clearly indicates a deviation from this user’s standard behavior, and points to a possible credential breach. Such events, which may not be detected by legacy security solutions that depend on signatures, are key discoveries that behavioral analytics can provide.
Behavioral indicators differ for different use cases, however, and the same patterns cannot be used to identify different types of attacks. Because of this, patterns relevant to each attack model have been identified and encapsulated within Securonix threat models.
Multiple algorithms are used to detect these anomalies, such as Adaptive Anomaly Detection. This algorithm compares real-time data to the current anomaly probability function, identifying behavior outliers that are then forwarded for risk analysis. The inliers within the real-time data are used to update the behavior profile, resulting in continued recalculation of the anomaly function to keep it current.
Learn more about Securonix User and Entity Behavior Analytics.
Don’t let legacy SIEM security slow you down.Download this whitepaper to learn more about intelligent threat analytics from Securonix. |