- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Cybercriminals are very sophisticated and aggressive in their efforts to infiltrate your environment and seek out your sensitive information, hold your critical systems ransom, or simply cause havoc. The reality is that the humans behind an attack may not necessarily have a deep knowledge of coding or technology. With botnets, zombie computing, and ransomware-as-a-service anyone with enough cryptocurrency can lease malware and other pieces of infrastructure required for attacks and campaigns. These pay-to-use cyberattack services allow threat actors to have a virtual army at their disposal and end up introducing new attack signatures and TTPs at an accelerated rate.
As an organization that is already taxed in terms of personnel and resources, how can you defend against this virtual army? The key is collaboration. However, bringing together intelligence and knowledge from not only your organizations, but from the greater industry is not an easy feat.
Cybersecurity experts have long been seen as being collaborative and willing to share what they know with their peers and partners. When knowledge is shared organizations can more effectively defend against cyberattacks as an industry at large. In fact, the Cybersecurity and Infrastructure Security Agency (CISA) released its strategic plan for 2023-2025 to improve the ways in which industry and the federal government collaborate to bolster the United States of America’s national cybersecurity.
In concept, collaboration makes sense. In practice, with attacks happening so quickly, proactively locating and bringing together all the intelligence that exists in systems, security tools, and your experts’ heads so it can be shared with others is a difficult task. Taking the time to stop and document what was done during an investigation is often a forgotten, but critical task.
Effective collaboration must come from internally curated intelligence, industry intelligence, and intelligence continuously delivered by your system vendors.
Bringing together intelligence from anywhere and everywhere
Effective collaboration requires bringing together knowledge from team members across your organization, gathering intelligence from peers within other organizations, and leveraging threat research from your vendors.
Additionally, as you develop new insights, you must be able to memorialize information derived from investigations and contribute intelligence to the broader industry. This must all be done without placing an additional burden on security analysts who need to focus on investigating and remediating potential threats. Securonix Unified Defense SIEM enables collaboration while making it easier on your security analysts.
Share threat intelligence across peers and partners
Autonomous Threat Sweeper (ATS) has the ability to look for newly identified threats by sweeping historical data leveraging new content delivered by Securonix. But what about threat intelligence developed by other security experts? Once the source of a threat is identified an organization will create a query based on their own intelligence and submit that intelligence to ATS. This allows them to sweep their historic data to look to see if the threat exists within their historical data. What is unique is that once that intelligence is submitted, ATS will also sweep all other organization’s environments that subscribe to ATS for the threat. If the threat is identified the other organizations will be notified that a threat exists. In this scenario, analysts could be notified of threats they weren’t necessarily looking for thanks to other security experts from other organizations.
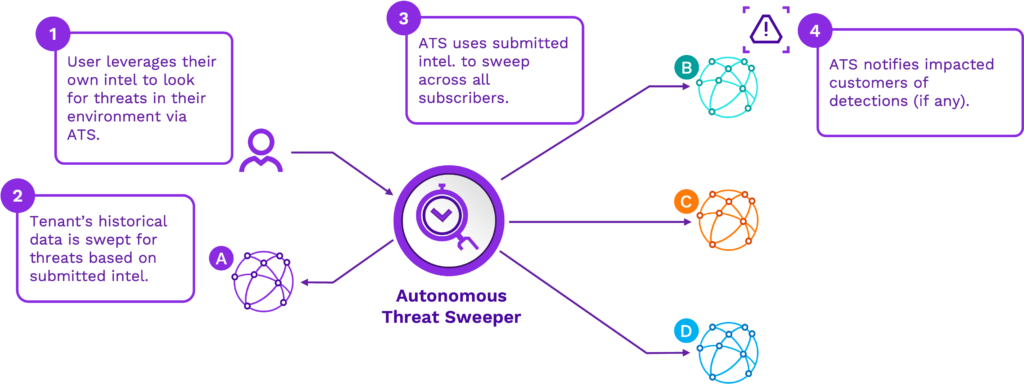
Figure 1: Securonix Autonomous Threat Sweeper allows you to leverage intelligence from other subscribers.
Build a knowledge base across your team
It can be just as difficult to foster collaboration across your team or organization. Security analysts often communicate across multiple channels: They may send some information over email, some by instant messenger, while other information may be within the ticketing system. The use of multiple channels is inefficient and context about the investigation can easily be lost. These communication channels require the analyst to move away from the investigation to send the details and insights to the recipients, further slowing the investigation.
Additionally, over time top-tier security experts develop a wealth of knowledge based on their knowledge of the environment and past investigations that is rarely captured and shared across the team. When those security analysts leave, all that knowledge is lost if it’s not properly documented. Because of the hectic routine of security operations, documentation is often overlooked.
Security teams need to be able to quickly document findings, communicate them to all or a trusted group of recipients and then memorialize the information for future use. Using third-party tools outside the security operations platform is ineffective and extends the investigation time.
One way Securonix is improving collaboration within security teams is through Securonix Investigate. Securonix Investigate enables the users of Securonix Unified Defense SIEM to pull in details about an entity under investigation automatically or on demand. These details are sourced from internal systems such as CMDBs, incident response systems, Malware databases, threat intelligence repositories and other external sources like YouTube, Google Drive, LinkedIn and Github. Investigate consolidates this information so you can get a near instant understanding of the nature of an entity.
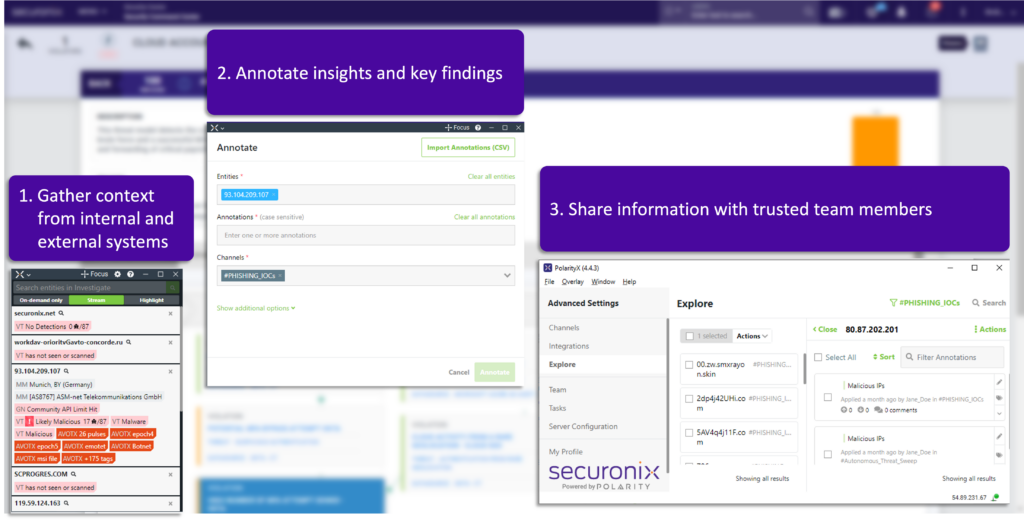
Figure 2: Gather context, note findings, and share across the team without ever leaving the investigation.
Once these details are collected, analysts can note findings and key details that are stored for future reference and delivered when the entity appears again in another investigation. Security analysts can then share insights and transfer knowledge to other members of the team. This process allows you to develop a knowledge store that retains learning that in the past would only be known by more senior analysts. Less experienced team members can leverage these learnings to improve their skill set and maintain continuity during times of analyst turnover.
The less obvious form of collaboration: vendor-delivered threat content
When you think of collaboration you often think of a back-and-forth sharing of ideas and information. In cybersecurity, collaboration is almost exclusively related to sharing threat intelligence, often in the form of TTPs and IOCs. But one area that is rarely considered, but should be, is the role of the security technology vendors in providing more than just plain threat intelligence to their customers.. There has been a movement where vendors are continuously delivering new threat detection content to supplement an organization’s lack of resources or skill set to research and create new threat content. These industry experts collaborate with other experts across the industry to identify threats in the wild, qualify threat intelligence from third-party vendors and produce new rules, analytics and models on behalf of the solution users. The goal is to continuously deliver new and updated threat content that can be quickly deployed to identify new and emerging threats before they have an impact on the environment.
In fact, Securonix’s global team of security experts, called Threat Labs, perform their own threat research, monitor and vet community developed threat intelligence, and qualify threat intelligence from third-party vendors. Once vetted, new content is made available. This is all done without the consumption of the end-users resources. It is delivered via the cloud and as-a-service. This threat content- as-a-service is leveraged by the Securonix Unified Defense SIEM as new detection rules. Additionally Autonomous Threat Sweeper (ATS) leverages the new threat content to sweep your historical data to determine and notify your analysts if newly identified threats have been present in your environment.
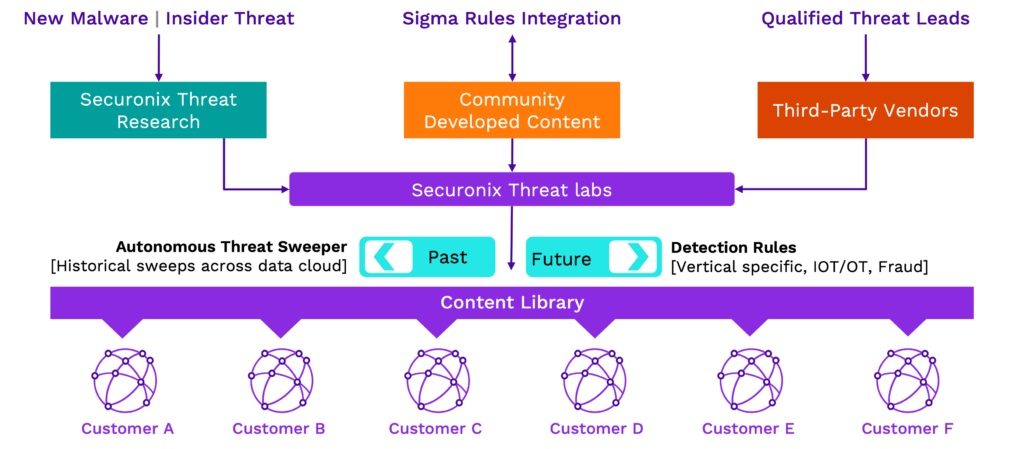
Figure 3: Securonix Threat Labs serves as an extension of your security operations team, by performing threat research and delivering timely threat content to stay ahead of new and emerging threats.
A multi-pronged approach to defending against threats through collaboration
As mentioned at the beginning of this blog, collaboration is key to defending against the virtual army of threat actors. However, collaboration doesn’t happen on one front. True collaboration takes in intelligence and knowledge from multiple sources.
- Peer and partner shared intelligence: This allows one organization to leverage the threat intelligence or queries from another organization to detect newly identified threats.
- Cross team or internal intelligence sharing: This allows your team to share information without leaving an investigation while also memorializing the information for future investigations.
- Vendor-based threat content and intelligence: This allows system vendors to deliver timely new threat content and intelligence as a service, outside of the normal system upgrades or patches. Making it easier and faster to employ new threat models and other information to address emerging threats.
If you want to learn more about the Securonix Unified Defense SIEM please watch our demo here.







