- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
By: Oliver Rochford
Twitter: @OliverRochford
Ransomware has steadily grown to become the most talked-about external cyber threat for enterprises in 2021. We have published several urgent and critical advisories for the community, including on the recent Conti ransomware insider leaks and the Darkside Ransomware group behind the Colonial Pipeline breach, as well as more general guidance on using our SIEM for preemptive ransomware detection. In this article, we outline six major trends that are driving the ransomware threat landscape, and taken together means that ransomware will be with us for some time yet. We then provide some best practices around early, preemptive ransomware detection.
Background
Ransomware is malware that encrypts or otherwise blocks access to data to extort money or favors from victims in return for restoring their access. Sometimes also called cyber extortion, other variants steal sensitive data threatening to share it with 3rd parties to blackmail victims.
Ransomware is not a new phenomenon. The first documented example, the PC Cyborg Trojan, was in 1989, in the age of floppy disks. The longevity and popularity of ransomware are based on the fact that the attack is simple yet effective, and has become even more potent as digital devices have proliferated and become more interconnected.
The average ransomware payment in Q2 2021 was $136,576.00, with 32% of ransomware victims paying the ransom in 2021. Already by April 2021, at least $18 billion had been paid out for ransoms, creating strong incentives for cybercriminals and fueling the further growth in the volume of attacks.
As a consequence, cyber insurance premiums have increased by 32%, with losses mounting for insurance providers. Enterprises that have been compromised with ransomware have experienced an average of 23 days downtime after an attack, and even when paying the ransom were only able to fully restore their data in 8% of cases, with 80% falling victim to another attack afterward.
Since the Colonial Pipeline breach, ransomware has also become a national security concern, with governments feeling the need to step in. Orders and actions from the Whitehouse, FBI, CISA, and various other US agencies have followed, accompanied by diplomatic efforts at the highest level.
Ransomware operators have reacted by being more discriminate in selecting their targets, nominally to avoid confrontation with national security agencies.
While the initial boom phase for ransomware is waning, especially due to increased scrutiny from law enforcement and national security agencies, it will continue to represent an acute threat for many organizations. Below you will find six trends that are converging to ensure that ransomware is here to stay.
Six Major Threat Trends Driving Ransomware Evolution
Six current trends mean that the next wave of ransomware will be harder to prevent, detect, and recover from.
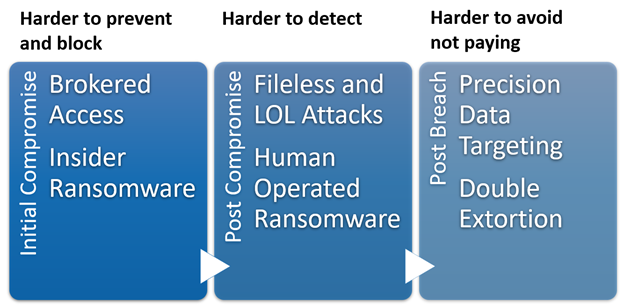
Strategic Victim Profiling
The Colonial Pipeline breach triggered a serious reaction from the US government, including some stark warnings to criminal cyber operators, cybercrime-as-a-service vendors, and even to any countries hosting them, that a ransomware attack may lead to a kinetic response or even inadvertently trigger a war.
Not long after, the criminal gang suspected to be behind the attack resurfaced under a new name, BlackMatter, and posted a request that they are buying access from brokers with very specific criteria. Seeking companies with revenue of at least 100 million US dollars per year and 500 to 15,000 hosts, the gang offered $100,000 but also provided a clear list of targets they wanted to avoid, including critical infrastructure and hospitals.
Impact: Some of the more high-profile cybercrime operators, especially those with affiliations with nation-states or organized crime, will avoid targeting victims providing critical infrastructure, or with strong government, emergency services, or political ties. While this is great news for those types of organizations, for everyone else it means having an even bigger target on their backs. And with the big players like ReVIL/BlackMatter or Conti out of the game, less scrupulous actors will arise to prey on healthcare and energy providers.
Access Brokering
Access brokers sell stolen credentials or other forms of entry to an already compromised system or environment. As we saw above, ransomware operators are buying targeted access based on granular firmographic data such as revenue, employee count, or industry vertical.
This frees up ransomware operators to specialize, develop, and innovate their core tooling, and also adds another layer of obfuscation against attribution.
Impact: Active compromises can be resold and reused, with existing malware repurposed through the deployment of specialized loaders. This means that a relatively benign attack, for example, crypto mining, can morph into a business-crippling ransomware incident almost in real-time. The interval between individual stages of an attack, from initial intrusion to data exfiltration, can also be delayed, with the possibility that little activity takes place in the intervening time to allow preemptive detection.
Human-Operated Ransomware
The earliest forms of ransomware were opportunistic in terms of who to target and what data to target. Improvements in defensive strategies, for example, more reliable detection, preemptive threat hunting, and increased resilience through disaster recovery mean that cyber extortion based on targeting single systems alone is rapidly declining in effectiveness.
Instead, we are seeing an increase in operator-driven cyber extortion attacks typified by longer reconnaissance phases leading to strategic targeting of systems and data to maximize the damage potential and success of obtaining a ransom payment.
Impact: A human operator driving the intrusion will build out their foothold through lateral transfer and privilege escalation under the cover of evasive techniques with the objective of extending the dwell time and spread of compromise, especially to critical or high-value targets.
This makes an intrusion harder to detect and contain, and especially to fully eradicate. Damage potential is also amplified with targets selected strategically for maximum disruption.
Living off the Land and Fileless Attacks
Living-off-the-land attacks (LOL) have been around for a few years now and have consistently grown in prevalence, with over 40% of attacks now estimated to include LOL techniques. Instead of deploying malware or downloading offensive hacking tools, attackers abuse and repurpose otherwise benign applications and tools that already reside on a system or in an environment.
Typical examples include PowerShell, a command-line shell and scripting language used to automate configuration management on windows systems, or PsExec, a utility designed to allow administrators to execute commands remotely over the network.
Impact: LOL attacks are challenging to detect. You can’t rely on static signatures or known-bad indicators such as file hashes for software that is common on many systems and has legitimate uses.
Precision Asset and Data Targeting
A disgruntled insider from the Conti ransomware team recently leaked a trove of data relating details about how the group operates. In addition to indicators of compromise and tradecraft, the leaked documents also gave insights into how the group trains associate operators to identify targets of value.
Operators are advised to search for financial information like revenue and sales data to be able to estimate a realistic ransom sum. They are also told to search for cyber insurance policy documentation to verify coverage. The strategic precision targeting also extends to identifying high-value targets, for example compromising backup servers to sabotage disaster recovery, and file servers containing sensitive data.
Impact: Ransomware attacks are more difficult to recover from if the most business-critical assets and data have been compromised, especially if they are critical to the success of the disaster recovery plan to regain operations. Similarly, an adversary doesn’t need a lot or all of a business’s data. Sensitive or secret data is sufficient. Strategically focusing on data that is less in volume but higher in value also means less noisy data exfiltration and file encryption, making detection and autonomous blocking more difficult.
Double Extortion
Improved detection and response, and the low data recovery rate from paying ransoms, as well as more investment in disaster recovery and cyber resiliency mean that encrypting data and extorting money for the decryption key is becoming less effective over time.
Smart cybercriminals are instead increasingly leaning on double extortion attacks. Not only is the data made unusable through encryption – but it is also first stolen. Victims are scared into paying the ransom through the threat of otherwise leaking the data. The Conti ransomware group, for example, are prolific leakers of data.
Impact: What this means for the average business is that just restoring your data from backup will not be enough to avoid the fallout from a breach. A ransomware attack can lead to the loss of valuable IP, sensitive customer data, and hefty regulatory fines if the data should fall under GDPR for instance.
Conclusion – Keep Calm and Carry On

The six trends we just outlined above make for a formidable set of advantages for attackers, but even combined, these factors don’t pose insurmountable obstacles for defenders.
If preventative controls have been breached, early detection is still the best strategy to minimize the impact of a breach. Multi-stage ransomware attacks take time to unfold before ultimately exfiltrating and encrypting data, and it is during these preliminary stages that we can take effective measures to limit the scope of the compromise.
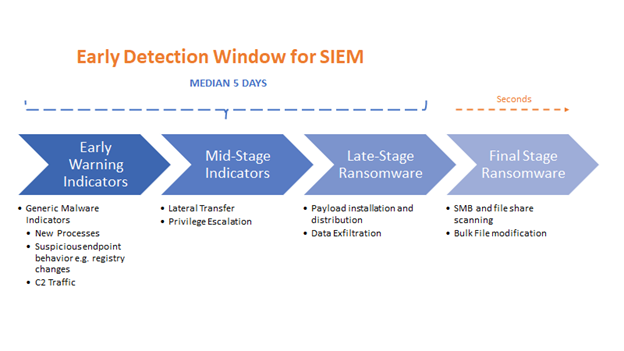
Ransomware Attack Lifecycle
Early Detection – Operational Best Practices
We already shared some best practices in our article on Preemptive Ransomware Detection, including which Detection and Threat Models are included in Securonix SIEM and UEBA and are designed to aid in early ransomware detection. Below we share some further recommendations.
24×7 Detection and Response
Ransomware can act at any time, and criminal operators are known to prefer holidays and weekends. It is also critical to minimize the time a ransomware operator has to identify and compromise strategic assets and data, interrupting the ransomware lifecycle before completion.
This makes coverage for nights and weekends crucial in early detection.
Recommendation: If you don’t operate 24×7, consider a managed service to extend your team and provide night and weekend coverage.
In the meantime, consider using SOAR to automate out-of-hours alerting and even response for detections with a high degree of confidence, and for detections in the later stage of the attack lifecycle, especially data exfiltration.
Threat Hunting
LOL, and other evasive techniques mean that reliable IoC’s are not always available for detection. Proactively hunting for threats, based on the hypothesis that we may already have been breached, can reduce the Mean Time to Detection and Response, and allow containment before the adversaries have had a chance to land and expand and deploy the ransomware loader.
Recommendation: Threat hunting is usually conducted by a human analyst as it is intended to find indicators of activity that automated detection approaches can’t detect, but some aspects of threat hunting can be automated, as we do for our Autonomous Threat Sweep (ATS) service that we offer to all our SIEM customers. You can also take a “crawl, walk, run” approach and slowly increase your threat hunting capability.
Behavioral Analysis and Threat Models
Without the luxury of indicators of compromise to rely on to simplify detection, the effective discovery of living-off-the-land and similar evasive techniques instead relies on identifying suspicious behavior.
To detect fileless and LOL attacks, for example, it is possible to compare which processes are routinely started by which users to identify rare and suspicious activity. To identify strategic data targeting we can look for someone accessing files that someone with a similar role generally doesn’t open.
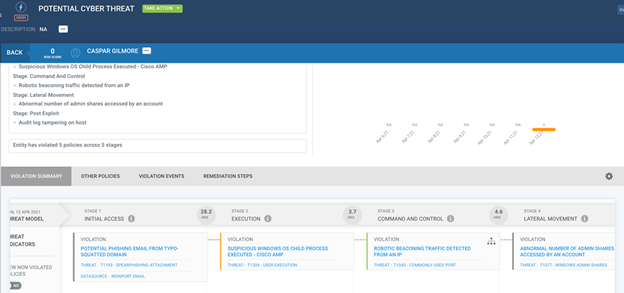
Behavioral Analysis and Attack Lifecycle Mapping Help Contain Early-Stage Ransomware
We can also use the MITRE ATT&CK framework and map activity to TTP’s to illuminate and identify attack lifecycles.
Recommendation: Our SIEM includes a comprehensive set of detections out of the box to help identify different “early warning” behaviors and TTP’s associated with common ransomware. Securonix Threat Labs continuously releases timely detections and threat advisories for emerging threats including ransomware.
Thanks to Sebastian von dem Berge for additional insights

Don’t forget to read our guidance on using Securonix for Preemptive Ransomware Detection.
Pre-Emptive Ransomware Detection







