- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Security Analytics
By Abhishek RVRK Sharma, Senior Technical Marketing Engineer at Securonix
Mitigate a Major Cause of Data Breaches
Identities have traditionally been managed with dedicated identity management software. That made sense when enterprise applications were on-premise, in secure data centers whose keys were only handed over to trusted agencies. Enterprise application data today rests in multiple on-premise and cloud datastores, and API-driven application integrations have enabled enterprises to let go of single-vendor business software. As the identity-controlled perimeter has crumbled, the network security layers that protected enterprise identities has also disappeared, making the risk of identity-based attacks much higher.
According to the 2019 Verizon Data Breach Investigations Report, 29% of breaches involved the use of stolen credentials. However, according to the Cisco 2019 CISO Benchmark Study, only 19% of CISOs report encountering a security incident involving stolen credentials.
Keeping track of access permissions and activities conducted within applications, and establishing a security context based on that information, is a big problem for IT security. This is a problem that identity analytics and intelligence can solve.

Figure 1: Differences Between Traditional and Modern Enterprise Identity Management
The figure above contrasts the traditional enterprise and the modern, cloud-driven enterprise. In a traditional enterprise IT model, identities are used within the limits of the corporate network, keeping them secure and safe. The modern enterprise uses a cloud application ecosystem along with on-premise applications. This means that identities are in use across the cloud, making them much more vulnerable.
Identity analytics and intelligence is a better, smarter solution to dynamically manage access decisions as well as intelligently identify and manage user risk profiles based on application usage. This reduces the manual effort required and increases the pace and accuracy of security operations.
To address this challenge, Securonix has identified and created integrations with multiple identity and access management (IAM) tools. The integrated platform delivers identity analytics and intelligence, enabling several use cases that are otherwise difficult for IT security teams to manage.
The Securonix platform performs advanced behavior analytics on identity usage and access patterns identified by the IAM tool. This enables the creation of risk profiles for user behaviors, which can be used in context by the IAM tool to make dynamic, informed access decisions.
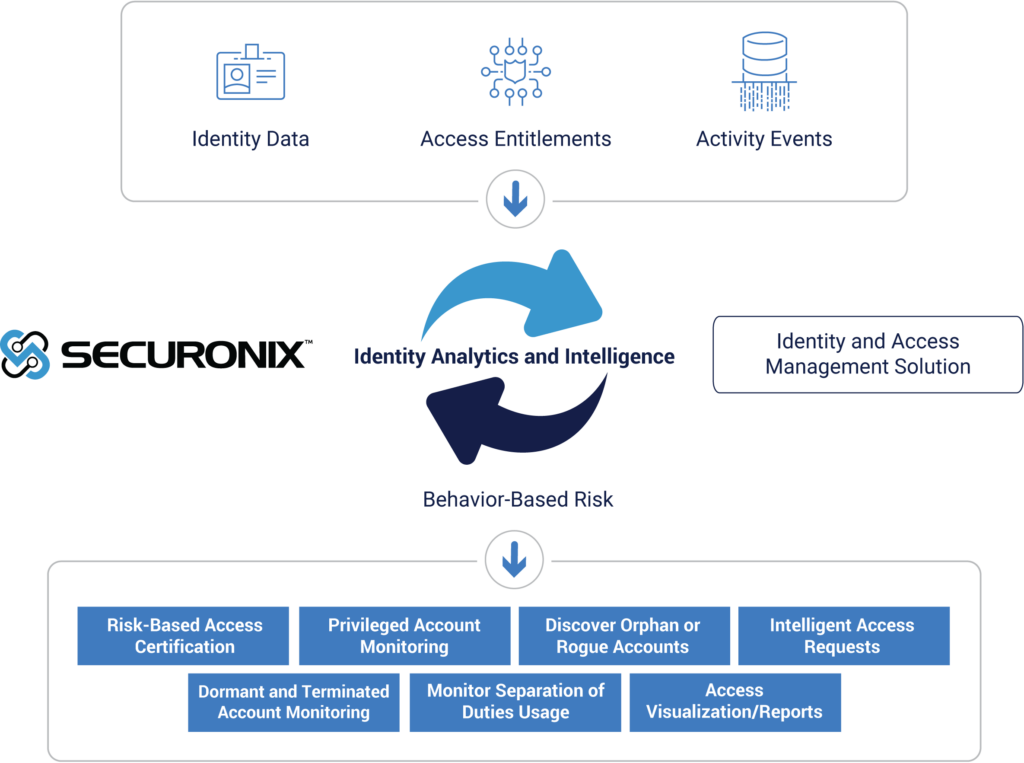 Figure 2: Benefits of the Integration of Securonix and IAM
Figure 2: Benefits of the Integration of Securonix and IAM
Use Cases Solved by Identity Analytics and Intelligence
Here is how you can use identity analytics and intelligence to close security holes.
Detecting Excessive Permissions
‘User profiles’ is a heavily abused term in IT. Having default user profiles that are assigned to users can be very dangerous. For example, assigning management-level access to a facilities manager in a remote office (just because he is a certain employee grade) can quickly cause a crisis if that manager is careless with his password.
By using identity analytics and intelligence and monitoring usage and correlating it with identified user task profiles, the appropriate level of permission required for a user’s tasks can be determined and any excessive permissions can be removed. This eliminates the chance of abuse of users with excessive privileges.
Enabling Risk-Based Access Clean-Up and Certification
The amount of data that a reviewer must deal with as part of an access certification review can be massive. Often, due to changing work responsibilities, user access rights will change, but the context of the change is rarely reported.
Behavioral analytics and access and usage monitoring enable the prioritization of high-risk entitlements and reduce the amount of data that needs to be handled during an access review, reducing the risk of reviewers rubber-stamping privileges. Risk-based clean-ups lead to an approximate revocation rate of 75%, reducing risk without affecting business operations. With identity analytics and intelligence, the security team can now perform more frequent and effective reviews.
Monitoring Privileged and Service Account Usage
Most systems have privileged, service, or system accounts that are normally used by operating system processes or administrative users. These accounts are prime targets for attackers due to the high level of security privilege that they provide.
By monitoring these accounts using identity analytics and intelligence unusual behavior such as privilege escalations, data exfiltration, credential sharing, and account compromise can be detected, and swift action can be taken.
Detecting Separation of Duties Usage Anomalies
Enterprises need to be on the lookout for credential compromise as well as access privilege escalation. Managing security requires monitoring identity usage and correlating that usage with security context.
Behavioral analytics provide an accurate context for access requests, which enables IAM platforms to accurately determine access requirements, illegal credential usage, and credential compromise. It also enables them to predict and block attacks such as credential escalation attempts. Anomalies, such as users who are accessing resources that are not relevant to their job role, are a key indicator of account compromise and can be detected swiftly using identity analytics and intelligence.
Discovering Rogue or Orphan Accounts
A security risk that enterprises must deal with is the possibility of rogue accounts with high-level privileges being created by internal agents, or the reuse of orphaned accounts that have lingered in the system after the users linked to them have left. These accounts are ripe for compromise.
Using identity analytics and intelligence to identify actions that cannot be traced back to specific accounts or entitlements enables both account revocation and lowers licensing expenses.
Monitoring Usage of Dormant and Terminated Accounts
Dormant and terminated accounts need to be purged from the system on a regular basis, but occasionally accounts are overlooked due to oversight or request backlogs. Such accounts could be misused to gain system access.
Both remediating the privileges for dormant and terminated accounts as well as detecting unusual activities are made possible using identity analytics and intelligence. This will reduce the misuse of credentials and improve the risk posture of the organization by removing high-risk credentials from the system.
Conclusion
Integrated identity and security management in the form of identity analytics and intelligence is the new reality for hybrid IT enterprises. If you want a safe enterprise, you need to make sure you’ve got eyes looking out for you, both inside and outside the organization.
You May Also Be Interested In
Find out how Securonix stands up to the competition in the 2018 Forrester Wave for Security Analytics Platforms.
Discover the many IAM solutions Securonix integrates with through the Securonix Fusion Partner Program.







