- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Incident Response and Forensics
With the data breaches that we have seen through the course of 2017 so far, one would imagine that incident response teams threw up their hands in defeat. The Equifax breach, with a compromise of over 140 million records of extremely sensitive private information on virtually every American that operates in today’s financial, digital, and social system looms large. But Yahoo continues to disclose increasingly disturbing information about their compromise, Dun and Bradstreet found 33 million corporate contacts shared across the internet, there were at least three major ransomware attacks, Gmail was targeted by a well-executed phishing scam – the list goes on.
The Security Management Process
Hackers and cybersecurity alerts are unfortunately the norm now. Organizations will continue to be targeted by financially motivated hackers, corporate espionage, malicious (and careless) insiders, philosophically motivated groups and nation states. Every security team is charged with the following broad tasks. In smaller organizations, these functions may all be the responsibility of a small cross-functional team, or even a single cyber security analyst (“the security guy”).
- Detect cyber threats that are targeting the organization’s digital assets
- Investigate the alerts, escalate the valid alerts and dismiss irrelevant flags
- Respond to the cyber incidents
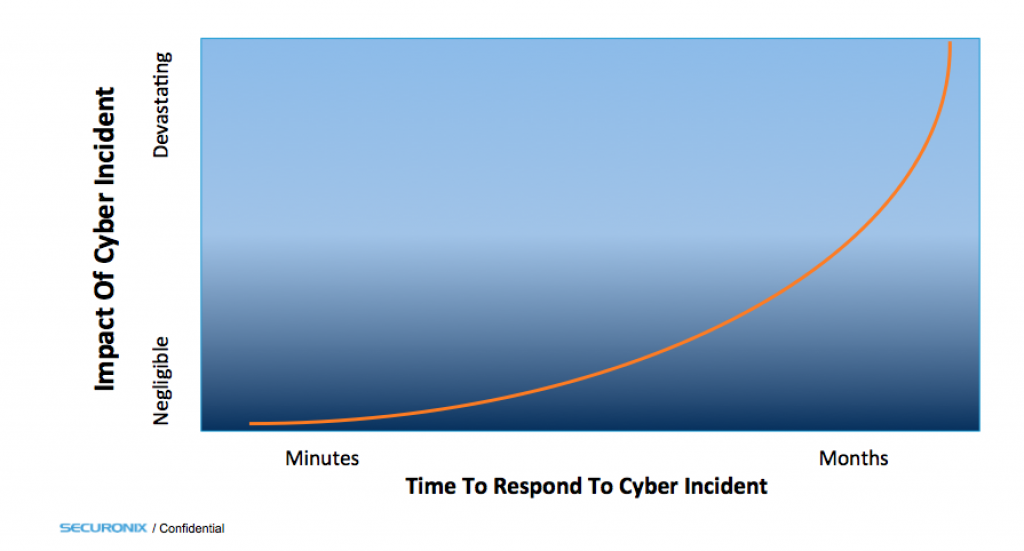
Response Time Vs. Overall Impact
Incidents, even legitimate validated incidents that could have a catastrophic impact on the organization will occur on a fairly regular interval. However, the actual impact and damage the organization will see because of a potentially catastrophic cybersecurity incident boils down to effectively one simple, single metric – the amount of time it takes to respond to that incident.
Mature security teams track the mean time to respond (MTTR) metric and couple this with a risk based prioritization of cyber incidents to optimally minimize their probability of having a materially impactful cyber incident. The way they do this is by focusing on their incident response processes, and ensuring that the amount of time it takes them to mitigate, investigate and remediate a cyber security incident is absolutely minimized. This involves thoroughly testing the avenues that hackers may have into the organization, documenting the steps and responsibilities of the CSIRT team when a cyber security incident is discovered, training the incident response team members on their roles and required actions, and finally practicing the response processes through drills that hone the response process to perfection.
Incident Response – More Involved Than You Think
“Fixing the problem” actually involves a lot more than is obvious, mainly because of the compliance aspects of any changes made to the IT infrastructure. The IR function is typically carried out a cyber security incident responder team (CSIRT) but often coupled with a forensics/investigations task as a #DFIR (digital forensics and incident response) role. Incident response team members are responsible not only for remediation, but also for isolating the problem, ensuring all the affected systems/services are covered by the response process, get the necessary approvals for any changes they need to make for remediation, effect the changes, documenting the steps taken to remediate the incident for tracking and compliance purposes and finally circling back to the detection function so that a repeat attack does not get through. This crucial set of steps ensures that the IR process not only fully tracks all the changes effected for compliance (or when needed, a rollback process), but the relevant workflow and approval steps are not neglected in the heat of a cyber security battle with the bad guys. It also ensures that the battle is not an insular event and that the organization is “inoculated” against attacks of a similar nature.
The Importance Of Automation
Responding to verified incidents is a multi-step process, and often involves similar, repetitive tasks for every incident. These include collecting the activity log data on the device that is reporting the incident, figuring out what machines this device was communicating with before during and after the time of the incident, what user users were logged on this machine and what activities were they performing when the incident occurred. The response process might even include response activities performed on the device, Network segment, or user account, like isolating the device into a separate VLAN, segmenting the network to separate it from systems affected by ransomware, botnets or other malware etc.
Automating and organization the incident response process allows the security team to address many more incidents, reduce the cyber risk profile and stay ahead of threats. Security teams should build out the necessary “run books” that step through the tasks necessary during the initial stages of an incident, and are prime candidates for automation.
Securonix SIEM
At Securonix, we have focused on improving the detection of critical cyber threats facing the organization, and optimized this through the use of big data analytics and machine learning. In addition, we have also focused heavily on this crucial, late stage process that is usually the difference between a simple corrective action, and a devastating data breach. The Securonix platform provides for smooth, fast and well-documented incident response via inherent capabilities as well as integrations with Security Orchestration and Automation vendors. You can learn more about Securonix forensics and incident response capabilities here.







