By Abhishek RVRK Sharma, Senior Technical Marketing Engineer at Securonix
Data enrichment is the key ingredient required for effective threat detection, investigation, and response. Using enriched data makes dealing with security threats easier and more efficient.

Security has evolved tremendously over the years. Today there are so many security devices in a typical enterprise environment that the problem is not an inability to detect, but not being able to evaluate all the available alerts and separate out the threats.
Simply put, security today is a big data problem. A multitude of security solutions supply information in different formats and at different times. At the center of this flood of information is your security information and event management (SIEM) platform. SIEM solutions are designed to collect massive volumes and varieties of data from both technical and non-technical data sources and display that data in visual formats that make the information easier to digest.
According to Cybersecurity Insiders’ 2019 SIEM Report, 76% of cybersecurity experts surveyed believed that SIEM was very to extremely important to their organization’s security posture. Furthermore, 75% say that their ability to detect threats has improved since they started using a SIEM.
What is the secret that helps a SIEM keep up with the sheer amount of security data available?
The Answer is Data Enrichment
The process of data enrichment adds event and non-event contextual information to security event data in order to transform raw data into meaningful insights. Security events can enriched with contextual information from user directories, asset inventory tools (such as CMDB), geolocation tools, third party threat intelligence databases, and a host of other sources.
Enriched data allows a SIEM to better perform threat detection, threat hunting, and incident response.
Threat detection is significantly enhanced by using real time enrichment. Business and threat intelligence context can be used to enhance detection analytics, improving the SIEM’s ability to identify threats. It can also be used to boost a threat’s risk score, prioritizing higher risk threats for investigation.
In threat hunting and incident response the additional context provided through enrichment allows for quick investigation and action. For example, additional context from a threat intelligence feed might identify an email attachment as a known malicious filename. Another example would be utilizing asset criticality. By being able to identify the criticality of given pieces of infrastructure (such as servers, VMs, and other devices), you can prioritize investigating threats to key infrastructure.
In each of these scenarios context plays a key role in weeding out noise and prioritizing high risk threats.
The typical contextual information used for security data enrichment includes:
- Identity context (such as identity and access management (IAM) systems, directories, enterprise resource planning (ERP) systems, and Active Directory (AD))
- Asset information (such as configuration management database (CMDB))
- Access privileges (such as AD group memberships)
- Non-technical feeds (such as background checks and badge data)
- Vulnerability context (such as scan reports)
- Social and online context (such as social media and chat)
- Network maps and geolocation (such as internal network classification for cross border analytics)
As the number of events and alerts skyrockets, enriching raw security events with relevant context is now a mandatory requirement for a modern SIEM solution. However, some SIEMs are challenged by scalability issues when handling big data.
How Securonix Data Enrichment Works
Securonix Next-Gen SIEM handles enrichment as a multi-dimensional issue. First, architecturally, Securonix is built on a big data architecture and uses the Apache Kafka ingestion bus to address the scalability issue. Securonix enriches events in real time, at ingestion. The enriched events are retained temporarily in Kafka topics in order to allow the data to be shared with the Securonix analytics tier, while also making the enriched data available to external applications outside of the SIEM.
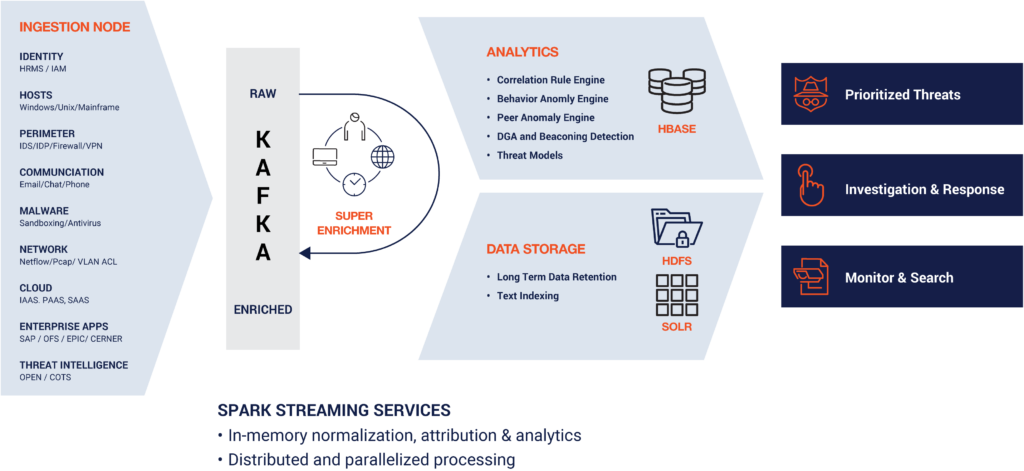
The enriched event data is compressed and stored in Hadoop and text indexed for search and visualization support. The open data model allows external applications to also use enriched events for custom analytics or other usages.
What Data Enrichment Can Be Used For
Several key enterprise security use cases can be enabled with real time enrichment. Highlighted below are some of the key use cases that outline the benefits of Securonix enrichment
Event and risk aggregation
When Securonix enriches the security data, the platform will also correlate it to the entity (such as a user, host, or IP address). This enables event aggregation and the ability to search enriched events across data sources by pivoting on any entity. It also enables risk scores to be aggregated and attributed to an entity, enabling threat prioritization.
Point in time context
Threat intelligence, vulnerability context, and IP addresses are all point-in-time information. For example, a domain may be bad today but clean tomorrow, and vice versa. Applying enrichment in real time enables Securonix to capture this point in time context. Enrichment done at search time or read time is inaccurate. Data from user directories (such as AD) is used to enrich the user context of a raw event. Similarly, CMDB data is used to enrich the asset context. The enriched data can be used in analytics and is searchable for threat hunting, where the use of contextual information significantly reduces the investigation time.
Threat intelligence for enrichment
Most SIEM solutions are capable of comparing events against threat intelligence to look for threats. However, what is extremely beneficial to the security operations team is when threat intelligence data is used to enrich security events in real time. Securonix adds threat intelligence context from sources like whois, virustotal, and several others to provide organizations with reliable, built-in intelligence for improved analytics and search. The contextual information can be used for real-time analytics, behavior profiling, risk boosting, and updating watchlists, look-up tables, and active lists.
Real-time analytics
Securonix uses Apache Spark analytics jobs on enriched Kafka topics to perform real-time streaming analytics. Doing this on enriched events enables Securonix to include the contextual data in the analytics.
User-IP-host mapping
Security events can be linked to a user, host, IP address, or multiple other identities. Securonix Next-Gen SIEM maintains a user-IP-host relationship table to enable the enrichment and aggregation of events irrespective of how they were initiated.
Organization risk scorecard
Securonix dynamically builds and maintains an organization hierarchy using the data from user directories such as AD. Threats identified are associated with individual organizations to create an organization risk scorecard.
Context for incident response
Securonix playbooks allow for automated enrichment of events with contextual data. With automated response options and integrated learning capabilities, the platform allows both automated responses based on past precedents for specific events (with a machine learning-based bot), as well as more complex response planning through playbooks.
Business context integration
Integrating business-relevant contextual information (such as organization hierarchy and risk tables, user office locations, user email addresses, and more) allows for unique analytics, such as peer analysis. This increases the ability to evaluate risk within individual organizations, and enables the isolation and remediation of more types of threats.
The Benefits of Data Enrichment
To illustrate the benefit of enrichment, look at this image.

This shows the amount of enrichment that Securonix can add to a raw event.
The raw event (at the bottom of the image) is one-line made up of numbers and text. Alone, this information is very difficult for an analyst to quickly parse. Enrichment translates this information into a detailed analysis of the entity, including the policy violated, details about the employee user ID, name, location, and even their management chain. This information makes it straightforward for analysts to quickly understand what is going on and initiate appropriate action.
In Summary
Data enrichment solves this problem, reducing false positives and empowering analysts and threat hunters in their investigations. Enrichment changes big data noise into intelligent analytics. The Securonix Next-Gen SIEM platform not only correlates and identifies threats, but also prioritizes them so that you can avoid being the next big data breach.
Don’t let legacy SIEM security slow you down.Download this whitepaper to learn more about intelligent threat analytics from Securonix. |