- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
Ever heard the idiom, ‘the walls have ears?’ This phrase supposedly originates from the ancient Greek story of Dionysius I of Syracuse, where he is said to have engineered ear-shaped curves in walls to eavesdrop on his guests. Today, this phrase has a whole new meaning in our connected world – where people can hear everything without even being nearby. There are a ton of internet of things (IoT) devices such as security cameras, printers, HVAC devices, smart TVs, and wi-fi routers – that can be used to eavesdrop on and attack a corporate network.
Enterprises keep increasing the number of IoT devices on their network, even as the security team struggles to gain visibility into them. Most of these devices, however, cannot be monitored – even with an agent. In fact, in 2019, 69% of enterprises surveyed estimated that over half of the devices on their network are unmanaged or IoT based.
Why Are IoT Devices Insecure?
Most IoT and other unmanaged devices use older operating systems, or limited versions that were designed for embedded hardware and are hard to update. Furthermore, most of these devices utilize security protocols with weak authentication management, making them a prime target for attackers.
Healthcare and manufacturing organizations are especially vulnerable to IoT-based attacks, as they utilize a large number of IoT devices. While most of these organizations run a structured security program to monitor their manageable assets such as endpoints, network devices, email gateways, application servers, and more, few have the tools necessary to review unmanaged or IoT devices. This creates a huge security blind spot.
Keeping Malicious ‘Ears’ Away From Your Networks
Integrating Securonix Next-Gen SIEM and the Armis Security Platform provides you with end-to-end visibility into your enterprise network – across IT, IoT, and unmanaged devices. Armis provides an agentless approach to monitor IoT and unmanaged devices. Post discovery, Armis matches current device behavior with baselines for over 11 million distinct devices and premium threat intelligence sources. Passively (without an agent), the Armis platform tracks any deviations from the norm, such as configuration issues, policy violations, and behavioral deviations (such as excessive network traffic, connections on unusual ports, and more).
Securonix leverages the asset inventory and information (including MAC addresses, manufacturer, model, operating system, and more), along with alert data from the Armis platform and uses it for IoT analytics, compliance reporting, and adding contextual data to investigations.
By combining entity information from Armis with information provided by other managed device data sources, Securonix is able to see end-to-end attacks that may not be visible with just a managed or unmanaged/IoT device viewpoint.
Solution Benefits
Improve Threat Detection
Combine event telemetry from unmanaged devices with the rest of your network data to provide a holistic view and improve threat detection.
Decrease Overall Response Times
Respond quickly to threats using integrated Securonix SOAR capabilities, enabling automatic device shutdown for faster remediation.
Faster Search and Threat Hunting
Securonix analyzes IoT and unmanaged device events together with managed device data in order to provide historical search capabilities for threat hunting and fast live search for active threats.
How the Magic Happens
Once Armis detects unmanaged/IoT devices, the data is ingested by Securonix and analyzed, along with data from other sources such as firewalls, endpoint detection and response (EDR), and email gateways. Securonix then uses advanced analytics to tie together relevant information. For example, Securonix can link an IP address that is sending traffic to a blacklisted IP (recognized by a firewall) with a printer device which Armis shows to be infiltrated.
Once Securonix identifies a threat, relevant action, such as taking the printer off the network, can be taken immediately.
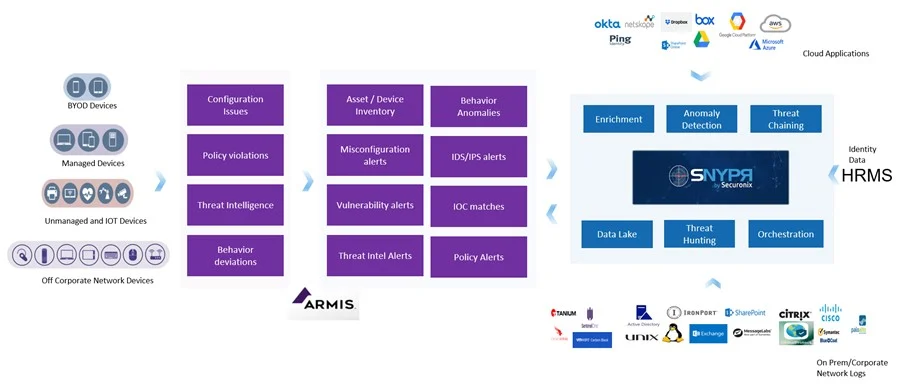
The combined solution enables a complete, holistic view of threats to the enterprise – including IoT and unmanaged devices – for end-to-end threat identification and response in a single solution.
Context-Driven Threat Modelling
Securonix adds critical contextual data to ingested events. Each event is correlated with contextual information such as MAC addresses (from Armis), user information (from a HR system), IP attributes, and multiple other data points. Securonix provides you with content for specific threat detection use cases, also allowing you to take action to mitigate threats.
This integration combines the unparalleled visibility into IoT and unmanaged devices provided by the Armis platform with managed asset information from other data sources. By correlating Armis asset data with data from other sources, Securonix enables appropriate actions across the network, such as blocking beaconing traffic from infected IoT devices. Securonix’s highly scalable and economical storage also enables the retention of important Armis data for compliance and threat hunting.
IoT and Unmanaged Device Threat Hunting
Using contextual information from Armis, Securonix SearchMore enables fast search for quicker security investigations and proactive threat hunting. Search on historical data for threats that already have a foothold in your network, or on live data to find new, active threats to your enterprise.







