- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
SIEM
by Aditya Tirumalai Sundararam and Akshay Nayak
What was once yours is now mine…
Deep dive into a series of cyberattacks involving phishing and account compromise
The information security is always in a state of flux. Both offensive and defensive techniques keep evolving. But as Ulysses S. Grant put it “War…War never changes.” Similarly, people never change when it comes to cyber incidents and data breaches. Humans are still the weakest link when it comes to the security of any organization. This is proven by the effectiveness of the techniques that threat actors use to take advantage of human psychology.
Securonix has recently discovered multiple phishing incidents involving Office 365 that employ a combination of account compromise and data exfiltration.
Threat Scenario
Here is an example of a typical phishing attack followed by an account compromise:
Initial Account Compromise Process
The attacker’s primary goal is to compromise the account details of a victim. There are a variety of methods that the attacker uses to achieve this, some of which can include:
Phishing
There are many types of phishing attacks that are used by attackers including: whaling phishing, which uses an email supposedly from a C-level company executive; emails pretending to be USPS or UPS package shipping confirmations; notification emails warning of bank account compromise; and more. There are even phishing attack emails that claim to be from Google, Microsoft, or other email providers that a company might be using.
Phishing doesn’t just occur over email, however, it can also occur over social networking websites. The cornucopia of phishing techniques are evolving much faster than the security controls designed to stop them.
Vishing
Short for voice-based phishing, vishing is when a scammer uses the phone to gain access to a victim’s personal and financial information. In a common form of vishing, the scammer calls the victim posing as a Microsoft Certified Professional or other licensed computer technician. They convince the unsuspecting user that their computer is infected with malware and offer to remove it. If the user accepts, the scammer may ask for payment information to remove the phony “infection,” thus acquiring the victim’s financial details. The scammer may also install a remote administration tool in order to “fix” the problem, which gives them a backdoor into the victim’s computer that they can use to exfiltrate data or install keyloggers or other malicious software. Scammers may even trick victims into providing account credentials for “troubleshooting” purposes.
Other Methods
Phishing and vishing are the two most common methods used to steal user credentials, but that does not mean that they are the only methods. An attacker can also grab user credentials by installing malware on a user’s system through an indiscriminate drive-by attack (when a random user simply visits an infected website) or a targeted watering hole attack (when an attacker targets a specific group of people by infecting a strategically chosen website which is visited by a large percentage of the targeted group). This malware can be programmed to install a keylogger and send credentials back to the attackers.
There are many more methods used by attackers to capture user credentials. However, capturing these credentials is merely the first step for the attacker. The real attack is what follows this credential theft.
Proliferating Infections
The plot thickens…
For an attacker, getting past the initial security is usually the hardest part. That’s because most organizations have multiple security controls deployed to stop an attack at the initial intrusion stage. Many security teams are so preoccupied with monitoring and blocking perimeter entry points that they overlook internal threats. These insider threats can be caused by sophisticated and unpredictable entities like advanced persistent threats (APT) and nation-state hacker groups, or even rogue insiders. As advanced as security controls like email gateways, next-generation firewalls, and endpoint solutions have become, attackers have also devised countless ways to bypass these.
If an organization does not properly monitor the applications it uses—whether they are on-premises or in the cloud—then that is a chink in the organization’s otherwise unbreakable armor. Here is a diagram of how an attacker takes advantage of this fact.
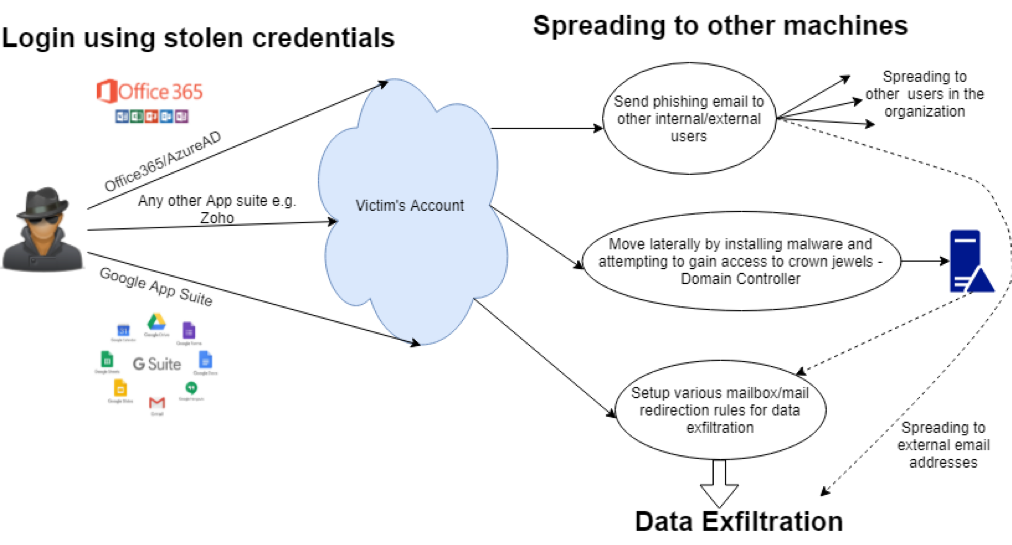
Figure 1: Account Compromise and Data Exfiltration
Once the attacker has the stolen credentials, they can now login to the user’s account to wreak havoc.
Some of the techniques attackers use are:
Harvesting the credentials of coworkers
The threat actor sends well-crafted phishing emails from the compromised account to other users in the organization. Since employees usually trust emails coming from their colleagues, this method works wonders for the attacker. There are Office 365-themed campaigns that make use of this technique, wherein attackers use informal subject lines like “FYI” and “Fw: Payments”.
Another internal phishing technique which is very effective is BEC (business email compromise) where an attacker sends emails from the compromised account of a high-level company executive. This yields the most results because almost every employee will respond to these emails with any information that was requested without blinking an eye.
Harvesting the credentials of external accounts
The attacker can also use a compromised account as a breeding ground for a phishing or malspam (malware delivered by email) campaigns by sending emails to external users. This creates a big liability issue where the company could potentially be blamed for cyber incidents in another company.
In fact, Securonix has discovered this kind of attack happening at one of our customers. An attacker was sending phishing emails from a compromised email account to multiple email addresses hosted on external domains.
Lateral movement via malware or backdoor installation
In cases where an app suite such as Office 365 is linked to Active Directory (Azure AD), the attacker could access the organization’s cloud desktop infrastructure. Then the attacker can move laterally using techniques like pass the hash or pass the ticket. Once the attacker has found a critical target such as a domain controller or a member server, the organization’s infrastructure is their oyster, and only their imagination limits what they can do.
Data Exfiltration
Once the attacker has access to a one or more accounts using stolen credentials data exfiltration can begin. There are a number of methods that threat actors use for this purpose, but in light of Securonix’s latest findings, the focus of this section will primarily be email-based exfiltration.
Mailbox rule manipulation
Once the attacker logs into the user’s mailbox they will try to create new mailbox rules, or modify existing ones, in order to exfiltrate data covertly. To give the devil his due, attackers get very creative to avoid raising the suspicion of both the user and the security controls that are in place.
In one such attack, Securonix found that the attacker had created an auto-forwarding rule that forwarded all emails to the attacker’s email address. But that’s not even the best part!
When a forwarding rule is created, any mail that gets forwarded will create a copy of the email in the user’s inbox, or other folder of the user’s choosing.
In order to prevent the user from noticing that many received emails were getting forwarded to a random email address, the attacker also deleted these emails from the user’s inbox after auto-forwarding them. This way a user would not even recall receiving those emails.
Privileged accounts – new possibilities
If an attacker succeeds in gaining access to the mail server, they can create even more devious mailbox rules.
Securonix had reason to believe that, in one such instance, the attacker had added themselves to one or more distribution lists. This meant that anytime an email was sent to that distribution list, it would also be sent to the attacker as well. In this attack, emails sent to the company employees by the system administrator’s email address were also being sent to the attacker’s email address. What was even more fascinating was that one of the emails was sent by the system administrator to educate the employees about a certain phishing campaign!
Detection Methods
Attacks consist of a variety of techniques and, as a result, require a multi-faceted approach to detection. The first step to detection is to enable auditing and logging of user activities wherever possible. The following log sources can be leveraged (Office 365 and Azure AD is used as an example here, but equivalent logs from other app suites such as Google can be used):
Email Logs
- Message trace/tracking logs – Contains information about email messages such as sender and receiver email addresses, subject lines, filesize, and more.
- Email gateway logs – Similar to Office 365 message trace logs, but with more detailed information.
- Exchange audit logs – Contains information regarding different activities performed on mailboxs. This includes but is not limited to login, mail box rule creation or modification, and adding or removing users from distribution lists.
Azure AD or VPN Logs
In case Office 365 credentials are used to login to the Azure cloud environment, any login activity can be found in these logs. If a VPN solution is deployed, it will also contain login information.
Proxy or Next-Generation Firewall Logs
Proxy or next-generation firewall logs can give information regarding any link that was clicked in a phishing email. Google provides its own set of logs to monitor mailbox activities or any other activity across all of its apps.
The table below describes the different phases of the entire attack, the corresponding logs created and the heuristic that can be used to detect the attack:
| Phase of Attack | Log Source(s) Leveraged | Heuristics |
| Phishing email sent by adversary | Message trace logs (Office 365)
Email gateway solution logs (Mimecast, Proofpoint, etc.) |
Emails from a domain that is visually similar to the company domain (resemblance/typosquatting-based phishing),
BEC (business email compromise) emails, emails containing suspicious subject lines. |
| User clicks on the email | Proxy or next-generation firewall logs | Domain rarely visited by a user or anyone else in the company. |
| Attacker logs into the user’s account using compromised credentials | Exchange audit logs
Azure AD VPN logs |
User logging in from a location not seen before.
Log on outside of normal work hours. Uncommon operating system or user agent used to login. |
| Attempt to steal more credentials by sending emails to other users in the organization | Message trace logs (Office 365)
Email gateway solution logs (Mimecast, Proofpoint, etc.) |
Abnormally large number of emails compared to behavior baseline. |
| Modifying inbox rules | Exchange audit logs | Suspicious mailbox rule changes such as forwarding to non-business email service providers like gmail, yahoo, aol, and others.
Modifying distribution lists to add emails hosted on an unusual domain. |
| Data exfiltration | Message trace logs (Office 365)
Email gateway solution logs (Mimecast, Proofpoint, etc.) |
Abnormally large number of emails being sent to external domains (associated with entities the company does not do business with). |
To detect data exfiltration, it is imperative that you check not just for email being forwarded to external domains, but also emails being sent to external domains. This is used to detect when attackers add themselves to distribution lists. This method is also able to detect data exfiltrated via an email redirection rule. Note that email redirection is different from email forwarding. In email forwarding, if A sends an email to B, and B sets up a forwarding rule to forward it to C, then C will see the email as coming from B (though the email body will contain information that A originally sent it to B). In the logs B is the sender and C is the receiver. If, however, B decides to set up a redirection rule to send any email coming from A to C, then C will see the email as coming from A, and everything in the email body will be preserved (including the subject line, which is modified to include the ubiquitous “FW”).
All the heuristics mentioned in the table above can be effectively implemented using a modern analytics or user and entity behavior analytics (UEBA)-driven security information and event management (SIEM).
Analytics-based SIEMs take advantage of a number of machine learning and behavior baselining algorithms that take into account the unique behavioral patterns of different accounts–whether it be service and administrative accounts, or even user accounts. Plus, they provide flexibility when it comes to creating policies that demand different anomaly detection scenarios. For example, a behavioral baseline for a user can be generated based on his or her past activity, the past activity of all accounts in the organization, or the past activity of his peers and colleagues in the same department.
Analytics-based SIEMs are also very good at identifying rare activities, making them great for creating policies centered around any rare activity that was not previously seen in a specific user or account. There is no way to implement any rare activity-based policies on a traditional SIEM.
Prevention
Organizations can take the following steps to protect themselves from the aforementioned attack:
- Enable multi-factor authentication on all accounts.
- Evolve security awareness training to keep up with the advances in phishing methods. For example, most traditional security awareness training programs teach users that if an email is coming from someone they know and trust then it’s probably ok. This teaching will fail to prevent the phishing attack described in this post. In addition to tweaking the security awareness training curriculum, security practitioners must also make sure to conduct a phishing simulation exercise to see if users are responding well to training.
- Follow the principle of least privilege. This control, if implemented correctly, can greatly limit the damage from an incident similar to the one described in this article.
This article mostly focuses on email-based exfiltration, but organizations should also make sure to monitor activities in other cloud-based apps, such as G Suite or Office 365. The first app to start with, in this case, should be cloud storage such as Google Drive or Sharepoint/OneDrive.







