- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
In our advisory, we detailed how the new PY#RATION attack campaign works. C2 communication is stealthy and detecting it might prove relatively difficult as many business applications leverage the WebSocket protocol to establish communication. Given the plethora of evasion techniques present in the malware, we have provided recommendations and mitigation techniques below for Securonix customers.
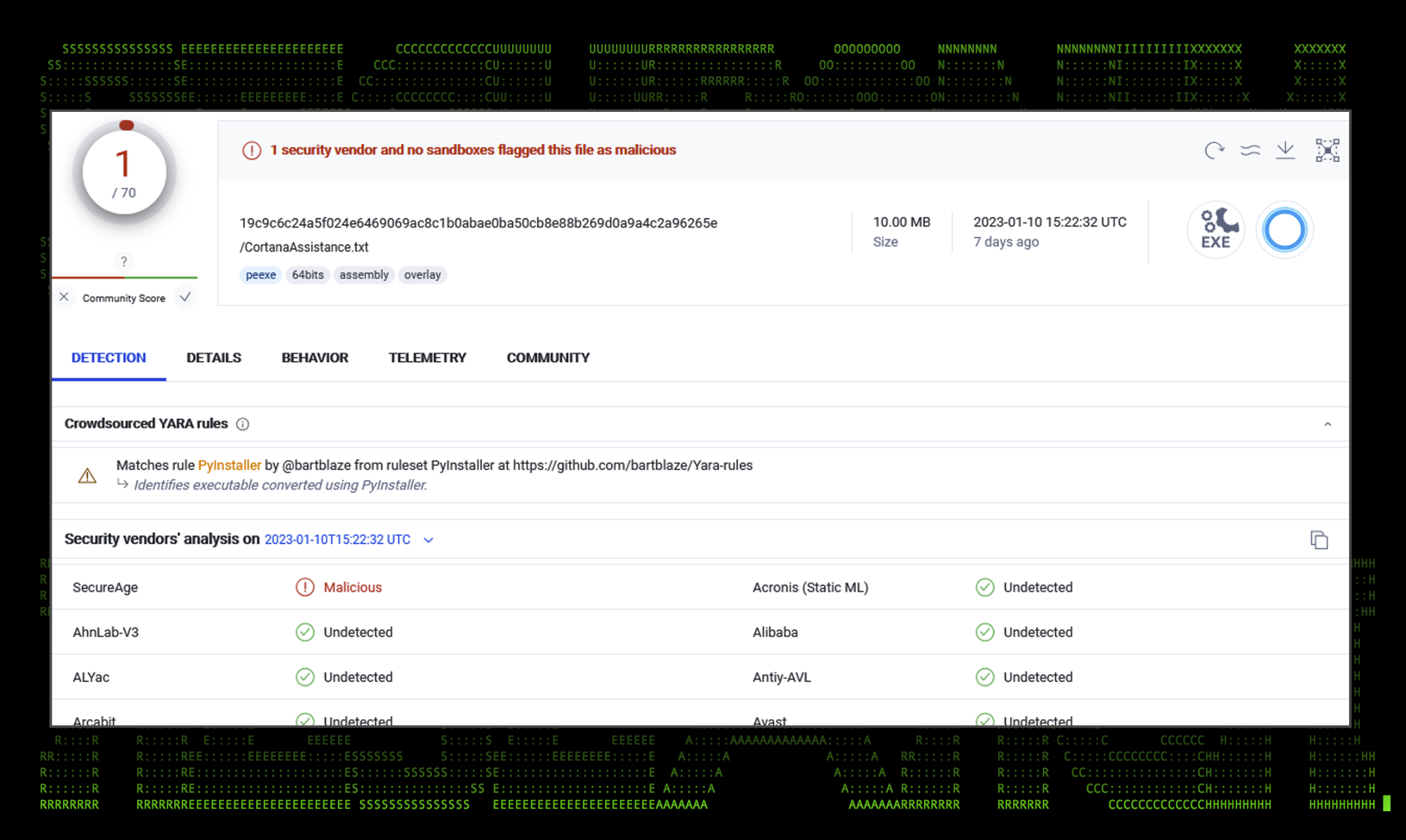
Figure 1: PY#RATION v1.6.0 VirusTotal detections
PY#RATION – MITRE ATT&CK techniques
| Tactic | Technique |
| Initial Access | T1566.001: Spearphishing Attachment |
| Execution | T1204.002: User Execution: Malicious File
T1059.005: Command and Scripting Interpreter: Visual Basic |
| Persistence | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1140: Deobfuscate/Decode Files or Information |
| Discovery | T1420: File and Directory Discovery
T1016.001: System Network Configuration Discovery T1426: System Information Discovery T1033: System Owner/User Discovery |
| Command and Control | T1071.001: Web Protocols
T1132.001: Data Encoding: Standard Encoding T1105: Ingress Tool Transfer |
| Collection | T1115: Clipboard Data T1185: Browser Session HijackingT1005: Data from Local System |
| Credential Access | T1555.003: Credentials from Password Stores: Credentials from Web Browsers |
| Exfiltration | T1041: Exfiltration Over C2 Channel |
Indicators of compromise
| Network-based IoCs |
| api.realproheros[.]com |
| install.realproheros[.]com |
| files.secureway[.]fun |
| login.secureway[.]fun |
| api.safeit[.]com/install/log?error= |
| 169[.]239.129.108:5555 |
| 169[.]239.129.108:5555/client/config |
| 169[.]239.129.108:5555/socket.io/?transport=polling |
| 169[.]239.129.108:5555/socket.io/?transport=websocket |
Analyzed file hashes
| File name | SHA256 |
| documents.zip | 4d297ebe3b607eb88a6c30a74a0ad23272f44ffbcf2b49f72444048b78c6e1b4 |
| front.jpg.lnk | 3b445be3da961379b11af1fee71fe4513e10832f77727b3a8bbe2eb7bd60b5c3
fd78f398e7cc8ced62deba213e0218d780357bcf89e01b748f8ed1e252ac3b21 |
| back.jpg.lnk | 4a32aa89a5250801c53d19370d98682e0561b642901bdd2987831bc983e0a544 |
| front.bat | c4cf65c95e68c6d610d8735d2922f89f98a6f37257b41ba01cf8179d5947298e |
| back.bat | e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 |
| b.bat | 5f72c5dde7cba7071193ee7053e1adde5ea570f0c4192ac350f5835766060e5a |
| c.bat | 6f8b208c3d4c1536ddf99304c880b939036a0725b1cc7fd44d768703da86fb68
180d61cbde7676c78b7b56b090f0c0d1ca5a69902ceaff26b0a1181351901011 06ecb59154d873889d92cead73238b5815358fa8a39c39868f735b24da0a3182 |
| 45b8f95j17.bat | 142b485d45344ff03c056ebf1bfe25eaeb0496338b5b2e0bb64bfef1ff81c4e6 |
| one.exe | fb592d344486d7c4d15df05ce58c84717b89dda7ae5bbd1aeccf49fbc7d47646
9501b38435b960d1a1f03785681345f9f215e9b799d3ae624b989df9e32e1b38 |
| ctask.exe | 95d2c8e6109f0ce1afb4b9d902b2f88b48ca41c6713855f3d0bf77d869a5c9a4 |
| cortanaassistance.exe | bba407734a2567c7e22e443ee5cc1b3a5780c9dd44c79b4a94d514449b0fd39a |
| CortanaAssistance.txt | 24d66c7d5c6250403a957c282772b01c9edab85a29bcea8e0690ad7672f74ddf
19c9c6c24a5f024e6469069ac8c1b0abae0ba50cb8e88b269d0a9a4c2a96265e |
Some examples of relevant Securonix detection policies
- EDR-ALL-1100-RU
- EDR-ALL-212-RU
- EDR-ALL-1098-RU
Hunting queries
- rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname = “cmd.exe” AND resourcecustomfield1 CONTAINS “-decode” AND resourcecustomfield1 CONTAINS “.jpg.lnk”
- rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname = “certutil.exe” AND resourcecustomfield1 CONTAINS “-decode” AND resourcecustomfield1 CONTAINS “Cortana” AND resourcecustomfield1 CONTAINS “.rar”
- rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname = “wscript.exe” AND resourcecustomfield1 CONTAINS “-decode” AND resourcecustomfield1 CONTAINS “Cortana” AND resourcecustomfield1 CONTAINS “.bat”
- rg_functionality = “Endpoint Management Systems” AND (deviceaction ENDS WITH “Written” OR deviceaction = “File created”) AND oldfilepath CONTAINS “\Windows\Start Menu\Programs\Startup” AND filename ENDS WITH “.bat”







