- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Securonix Threat Labs has been continuously monitoring threats targeting and leveraging the crisis in Ukraine in recent weeks and seen a significant increase in cyberthreats. MuddyWater, HermeticWiper and SandWorm are actively being used to launch cyberattacks, including DDoS attacks targeting financial institutions, cyber espionage campaigns and infrastructure.
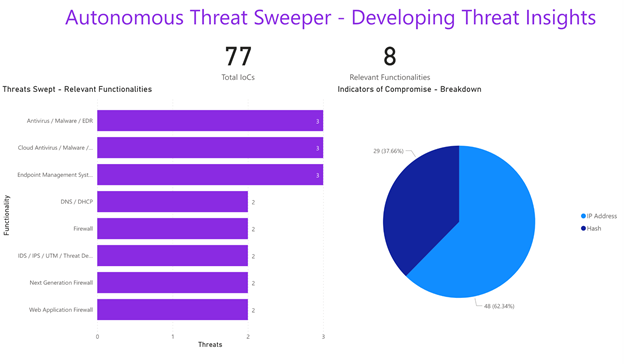
We provide guidance for detecting attacks by advanced persistent threats in this update. Of note are the top three data sources swept against on Autonomous Threat Sweeper that include antivirus/malware/EDR, cloud antivirus/malware, and endpoint management systems. For a full list of IOCs, search queries on Securonix SNYPR used on to detect MuddyWater, HermeticWiper, Cyclops Blink, malware, please refer to our updated Github page.
Updated March 1, 2022
Pro-Ukraine Conti Release
Last Friday, the Conti group, believed to be based in the city of Saint Petersburg, said it was announcing its “full support” for retaliation against a cyberattack against Russia. The Conti blog post stated that “If anybody will decide to organize a cyberattack or any war activities against Russia, we are going to use our all possible resources to strike back at the critical infrastructures of an enemy.” After the group’s leaders posted an aggressive pro-Russian message on their official site, a member of the Conti ransomware group believed to be of Ukrainian origin, has leaked details about the group’s communications, which contains some artifacts and sensitive details that can potentially aid detection.
IssacWiper, HermeticWizard and HermeticRansom targets Ukraine
(Originally Published on: March 1, 2022)
After Russia’s invasion on Ukraine researchers also noticed another wiper attack on Ukraine dubbed as IssacWiper along with HermeticWizard and HermeticRansom. Same code signing certificate was used for the other new malwares too. Researchers also noticed a decoy ransomware written in Go dubbed HermeticRansom to hide the wiper’s action. Currently Threat Labs was unable to attribute these kinds of attacks to a particular threat actor but seeing these geopolitical tensions there are chances these might be originating from Russian sponsored threat actors.
Threat Labs Summary:
- Hermetic Wizard spreads HermeticWiper across local networks via WMI and SMB.
- Considering the PE timestamp of IssacWiper which was dated October 2021 signifies that the malware might be present in the systems since last year.
- 8 IOCs are available on Github and have been automatically swept against for Securonix Autonomous Threat Sweeper customers.
- TTPs related to HermaticWizard include but are not limited to the following:
- Monitor for commands that gather known local IP addresses using the following Windows functions:
- DNSGetCacheDataTable;GetIpNetTable;WNetOpenEnumW(RESOURCE_GLOBALNET, RESOURCETYPE_ANY);NetServerEnum;GetTcpTable;GetAdaptersAddresses
- Monitor for commands that leverage Windows WMI or SMB services to further move laterally into the network:
- WNetAddConnection2W; CopyFileW; CoCreateInstance ; CLSID_WbemLocator samr; browser; netlogon; lsarpc; ntsvcs; svcctl
- Monitor for a new process creation on the systems with the argument: “C:\windows\system32\cmd.exe/cstartC:\windows\system32\\regsvr32.exe /s /i C:\windows\<filename>.dll”; “cmd /c start regsvr32 /s /i ..\\<filename> & start cmd /c \”ping localhost -n 7 & wevtutil cl System\””
MuddyWater Targets Organizations Worldwide
(Originally Published on: February 24, 2022)
Authorities from US and UK have released a detailed advisory about the recent cyber espionage campaign of MuddyWater which is allegedly state sponsored by Iran and works in the interests of MOIS. In this current campaign they have been mainly targeting government and private organizations from industries including telecom, defense, oil and gas located in Asia, Africa, Europe, and North America. This time they have come up with a variety of malwares ranging from PowGoop, Small Sieve, Mori and POWERSTATS and they have used their most preferred threat vector which is spear phishing campaigns in which they wheedle their targeted victim into downloading ZIP files, containing either an Excel file with a malicious macro that communicates with the actor’s C2 server or a PDF file that drops a malicious file to the victim’s network.
Threat Labs Summary:
- New Python backdoor dubbed Small Sieve got highlighted more as it can avoid detection by using custom string and traffic obfuscation schemes together with the Telegram Bot application programming interface (API).
- Use of a single byte XOR to encrypt communications with the key 0x02 to adversary-controlled infrastructure.
- PowGoop malware was used as the main loader in malicious operations which consisted of a DLL loader and a PowerShell-based downloader.
- Canopy/Starwhale malware was distributed through spear phishing campaign with malicious attachments
- Threat actors used the Mori backdoor which uses domain name system (DNS) tunneling to communicate with the group’s C2 infrastructure.
- The POWERSTATS backdoor was used to run PowerShell scripts to maintain persistent access to the victim systems.
- 29 IOCs are available on Github and have been automatically swept against for Securonix Autonomous Threat Sweeper customers.
- TTPs related to MuddyWater include but are not limited to the following:
- Monitor for the following rare processes being executed:
- gram_app.exe, index.ex
- Monitor for the following rare files / DLLs being created:
- Cooperation terms.xls, FML.dll, MicrosoftWindowsOutlookDataPlus.txt
- Monitor for persistence with any modifications to the current user startup folder
- file path contains \Windows\Start Menu\Programs\Startup
- Monitor for rare registry modifications:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\OutlookMicrosoft
- Monitor for the following rare processes being executed:
Tags: Adversary: MuddyWater, Static Kitten | Target Industries: Government, Telecom, Oil & Gas, Defense | Target Continents: Asia, Europe, NorthAmerica, Africa | Malware: PowGoop,Small Sieve, Mori and POWERSTATS
HermeticWiper Malware Targets Ukraine
(Originally Published on: February 23, 2022)
On the evening of February 23, 2022, the State Service of Special Communication and Information Protection of Ukraine declared that a number of government and banking institutions had undergone a massive DDoS attack. Soon after this announcement, the ESET Research team discovered a new data wiper malware (Win32/KillDisk.NCV) that attacked the Ukraine-wide computer network with the objective of destroying data and causing business disruption. The initial analysis of data wiper malware suggests that it is an executable file signed with a likely stolen certificate issued to Cyprus based company Hermetica Digital Ltd. Hence, the researchers named malware as ‘HermeticWiper’.
Threat Labs Summary:
- Upon execution, HermeticWiper enables process token privileges, which gives read access control to any file.
- It checks and verifies the operating system architecture, then drops the copy of the EaseUS Partition Manager driver accordingly.
- Again enables the process token privileges to load and unload device drivers.
- Disables crash dumps, volume shadow services (vss).
- It corrupts all master boot records (MBR) for every physical drive present in the system, and also corrupts all the available partitions including NTFS and FAT file systems.
- 58 IOCs are available on Github and have been automatically swept against for Securonix Autonomous Threat Sweeper customers. As this is a developing threat, the Autonomous Threat Sweeper will be sweeping additional IoCs.
- TTPs related to HemeticWiper include but are not limited to the following:
- Monitor for registry key changes to disable crashdumps (CrashDumpEnabled = 0) from the path “HKLM\SYSTEM\CurrentControlSet\Control\CrashControl”
- Monitor for rare registry key changes to disable “ShowCompColor”, “ShowInfoTip” from the path “\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced”
- Monitor for rare privilege escalation attempts related to the following privileges (SeShutDownPrivilege,SeBackupPrivilege,SeLoadDriverPrivilege)
- Monitor for rare commands executed to identify the operating system version ( i.e. command line contains VerSetConditionMask; VerifyVersionInfoW)
- Monitor for rare processes spawned from command prompts such as “expand.exe”
- Monitor for rare sys files created on system folders (Eg: %WINDIR%\system32\driver\<random_2chars>dr.sys)
Tags: Malware Family: Disk-wiping | Target Industries: Government, Financial Organizations, Aviation, IT services | Target Countries: Ukraine, Latvia, Lithuania
Sandworm From Russia Uses Cyclops Blink Malware
(Originally Published on: February 23, 2022)
Authorities from US and UK have come across a new strain of malware dubbed as Cyclops Blink which is said to be a replacement of a very infamous malware called VPNFilter which created havoc by infecting half a million routers a few years back. This malware has been attributed to a famous APT group called Sandworm who is formally connected to Russia’s GRU unit and was associated with a major power outage in Ukraine in 2015. Cyclops Blink has been deployed since 2019 and has already been infecting the WatchGuard Firebox manufactured by Seattle based firm WatchGuard and possibly infecting SOHO routers too.
Threat Labs Summary:
- Cyclops Blink is a malicious Linux ELF executable, compiled for the 32-bit PowerPC (big endian) architecture.
- It is generally deployed as part of a firmware update which achieves persistence when the device is rebooted and makes remediation harder.
- 1% of active WatchGuard firewall appliances have been affected until now.
- Sandworm has the capability to create a huge set of botnets from these firewall devices.
- 37 IOCs are available on Github and have been automatically swept against for Securonix Autonomous Threat Sweeper customers.
- TTPs related to Cyclops Blink include but are not limited to the following:
- Cyclops Blink executes downloaded files using the Linux API function execlp.
- Monitor rare command line parameters for the process “kworker” with the command line “/proc/self/exe”
- Cyclops blink communicates over non-standard ports on HTTP and HTTPS protocols
- Monitor for C2 communication on HTTP and HTTPS protocols for non-standard ports
- Cyclops Blink is capable of uploading files to a C2 server.
- Monitor for exfiltration to C2 server over covert channels such as SSH, TELNET, RDP, DNS
- Cyclops Blink executes downloaded files using the Linux API function execlp.
Tags: Adversary: SandWorm, VoodooBear | Target Industries and Products: Energy, WatchGuard Firewall, Routers| Target Countries: Ukraine, Georgia
Please refer to our Github page that is updated daily. We also invite you to send your questions regarding critical security advisories to the Securonix Critical Intelligence Advisory team and look forward to being of assistance.
Search Query References:
| Attacker Group | Search Query | Functionality |
| HermeticWiper Malware | Summary:Monitor for Registry key changes to disable crash dumps (CrashDumpEnabled = 0) from the path “HKLM\SYSTEM\CurrentControlSet\Control\CrashControl”
“rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) AND resourcecustomfield1 CONTAINS “”HKLM\SYSTEM\CurrentControlSet\Control\CrashControl”” AND resourcecustomfield1 CONTAINS “”CrashDumpEnabled”” AND resourcecustomfield1 CONTAINS “”0″”
Summary: Monitor for Rare registry key changes to diable ShowCompColor, ShowInfoTip from the path “\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced”
rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) AND resourcecustomfield1 CONTAINS “”Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced”” AND (resourcecustomfield1 CONTAINS ShowCompColor OR resourcecustomfield1 CONTAINS ShowInfoTip) AND resourcecustomfield1 CONTAINS “”0″”
Summary:Monitor for rare files created and/or executed from known windows system folders
rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) AND resourcecustomfield1 CONTAINS “”C:\Windows\system32\Drivers”” | Rare resourcecustomfield1
Summary:Monitor for rare commands executed to identify the operating system version
rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) AND (resourcecustomfield1 CONTAINS “”VerSetConditionMask”” OR resourcecustomfield1 CONTAINS “”VerifyVersionInfoW””)
Summary:Monitor for Rare processes spawned from command prompt
rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) AND sourceprocessname contains “”cmd.exe”” and resourcecustomfield1 contains expand
rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) and resourcecustomfield1 contains EPMNTDRV
Summary: Monitor for rare sys files created on system folders (Eg: %WINDIR%\system32\driver\<random_2chars>dr.sys)
rg_functionality = “”Endpoint Management Systems”” AND (deviceaction = “”Process Create”” OR deviceaction = “”Process Create (rule: ProcessCreate)”” OR deviceaction = “”ProcessRollup2″” OR deviceaction = “”SyntheticProcessRollUp2″” OR deviceaction = “”WmiCreateProcess”” OR deviceaction = “”Trace Executed Process”” OR deviceaction = “”Process”” OR deviceaction = “”Childproc”” OR deviceaction = “”Procstart”” OR deviceaction = “”Process Activity: Launched””) AND resourcecustomfield1 contains “”C:\Windows\system32\”” and resourcecustomfield1 contains “”dr.sys””” |
Endpoint Management systems |
| MuddyWater | Summary: Monitor for Rare privilege escalation attempts by acccounts within the ADFS
rg_functionality=””microsoft windows”” and (baseeventid=4672 OR baseeventid=4673 OR baseeventid=4674) and sourceuserprivileges IN(SeShutDownPrivilege,SeBackupPrivilege,SeLoadDriverPrivilege) | Rare accountname Summary: Monitor for Rare processes spawned from command prompt rg_functionality=””microsoft windows”” and baseeventid=4688 and sourceprocessname=cmd.exe and destinationprocessname =expand.exe rg_functionality = microsoft windows and baseeventid=4688 and baseeventid=4663 and sourceprocessname contains EPMNTDRV or destinationprocessname contains EPMNTDRV Summary: Monitor for the following rare processes being executed:gram_app.exe, index.exe rg_functionality = “Endpoint Management Systems” and (sourceprocessname =”gram_app.exe” or destinationprocessname =”gram_app.exe” or sourceprocessname =”index.exe” or destinationprocessname =”index.exe”) Summary: Monitor for the following rare files / DLLs being created:Cooperation terms.xls, FML.dll, MicrosoftWindowsOutlookDataPlus.txt rg_functionality = “Endpoint Management Systems” and (filename = “Cooperation terms.xls” or filename =”FML.dll” or filename = “MicrosoftWindowsOutlookDataPlus.txt”) Summary: Monitor for persistence with any modifications to the current user startup folder: file path contains \Windows\Start Menu\Programs\Startup rg_functionality = “Endpoint Management Systems” and filepath CONTAINS “\Windows\Start Menu\Programs\Startup” and filename ends with “.wsf“ Summary: Monitor for rare registry modifications : HKCU\Software\Microsoft\Windows\CurrentVersion\Run\OutlookMicrosoft rg_functionality = “Endpoint Management Systems” and devicecustomstring2 CONTAINS “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\OutlookMicrosift” |
Microsoft Windows
Endpoint Management systems |
| Cyclops Blink Malware | Summary: Monitor rare command line parameters for the process kworker
rg_functionality = “Unix / Linux / AIX” AND (sourceprocessname CONTAINS “kworker” OR deviceprocessname CONTAINS “kworker” ) | RARE devicecustomstring1 rg_functionality = “Unix / Linux / AIX” AND (sourceprocessname CONTAINS “kworker” OR deviceprocessname CONTAINS “kworker”) AND ((devicecustomstring1 CONTAINS “execl” AND devicecustomstring1 CONTAINS “/proc/self/exe”) OR (customstring2 CONTAINS “execl” AND customstring2 CONTAINS “/proc/self/exe”)) |
Unix / Linux / AIX |
| Summary: Monitor for C2 communication on HTTP & HTTPS protocols on non-standard ports
rg_functionality = “Next Generation firewall” AND (applicationprotocol = HTTP OR applicationprotocol = HTTPS) AND destinationport != 443 AND destinationport != 80 rg_functionality = “Firewall” AND (applicationprotocol = HTTP OR applicationprotocol = HTTPS) AND destinationport != 443 AND destinationport != 80 Summary: Monitor for exfiltration to C2 server over covert channels such as SSH, TELNET, RDP, DNS. rg_functionality = “Next Generation Firewall” AND destinationport IN(“22″,”23″,”3389″,”53”) AND destinationaddress != 10.0.0.0/8 AND destinationaddress != 172.16.0.0/12 AND destinationaddress != 192.168.0.0/16 | STATS SUM(bytesout) rg_functionality = “Firewall” AND destinationport IN(“22″,”23″,”3389″,”53”) AND destinationaddress != 10.0.0.0/8 AND destinationaddress != 172.16.0.0/12 AND destinationaddress != 192.168.0.0/16 | STATS SUM(bytesout) |
Next Generation Firewall & Firewall | |
| Pro-Ukraine Conti Release | index=activity AND rg_functionality=”Next Generation Firewall” AND ipaddress NOT NULL AND ipaddress IN (“138.124.180.94”, “45.14.226.47”, “193.203.203.101”)
index=activity AND rg_functionality=”Firewall” AND ipaddress NOT NULL AND ipaddress IN (“138.124.180.94”, “45.14.226.47”, “193.203.203.101”) index=activity AND rg_functionality=”Web Proxy” AND ipaddress NOT NULL AND ipaddress IN (“138.124.180.94”, “45.14.226.47”, “193.203.203.101”) index=activity AND rg_functionality=”Web Application Firewall” AND ipaddress NOT NULL AND ipaddress IN (“138.124.180.94”, “45.14.226.47”, “193.203.203.101“) index=activity AND rg_functionality=”DNS / DHCP” AND ipaddress NOT NULL AND ipaddress IN (“138.124.180.94”, “45.14.226.47”, “193.203.203.101”) index=activity AND rg_functionality=”IDS / IPS / UTM / Threat Detection” AND ipaddress NOT NULL AND ipaddress IN (“138.124.180.94”, “45.14.226.47”, “193.203.203.101”) |
Next Generation Firewall & Firewall
Web Proxy IDS / IPS / UTM / Threat Detection |
| HermeticWizard Worm | Summary: This query detects the indicators for the presence of possible Hermetic Wizard while the worm is deployed in the system and performs recon within the network.
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND (resourcecustomfield1 CONTAINS ” DNSGetCacheDataTable ” OR resourcecustomfield1 CONTAINS “GetIpNetTable” OR resourcecustomfield1 CONTAINS “WNetOpenEnumW” OR resourcecustomfield1 CONTAINS “NetServerEnum” OR resourcecustomfield1 CONTAINS “GetTcpTable” OR resourcecustomfield1 CONTAINS “GetAdaptersAddresses” OR resourcecustomfield1 CONTAINS “OpenRemoteServiceManager” OR resourcecustomfield1 CONTAINS “Wizard.dll”) | Rare resourcecustomfield1 Summary: This query detects the indicators of Hermetic Wiper spread via WMI or SMB : rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = |
Endpoint Management Systems |
Note: These queries in Silo may be prone to false positives and we recommend leveraging it with other stages of the attack progression to increase the likelihood of true positives.