- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Alignment, not mapping, is the only way to truly adopt the MITRE ATT&CK Framework. Here’s how.
By Abhishek RVRK Sharma, Senior Technical Marketing Engineer at Securonix
One Minute TakeawayDo you only have a minute to spare? Here’s what you need to know: MITRE methodology alignment vs. MITRE alert mappingMost solutions will simply map the alerts that their SIEM solution records to the MITRE ATT&CK framework. Useful? Maybe. But, without aligning to the actual MITRE methodology (which is based on multi-stage threats, of which the techniques are only individual steps), alignment to just the alert IDs is useless. Securonix is the only platform which, using integrated threat chaining methodology, aligns with MITRE’s methodology by mapping threats, not just alerts. So instead of seeing a thousand MITRE-mapped alerts, you will see 10 real, MITRE attack stage mapped threat chains which are instantly actionable. With automated, constantly learning algorithm-based threat chaining, Securonix provides faster and more accurate response then rule-based SIEMs that need constant rule updates and provide no threat chaining. |
The new cyberattack landscape
“One Month’s Free Membership for The PLAYBOY ClUB 1080P HD VIDEOS 100,000 PHOTOS
4,000 MODELS Nude Celebrities,Playmates,Cybergirls & More! Click
Here To Get a Free Plus Member Now & Never Miss Another
Update. Your Member referrals must remain active. If anyone getting “Promotion not available”
for 1 month free membership, you might get the issue up to 48 hrs once your membership is
expired and make sure to Clear out cookies or use another browser or use another PC.”
Interesting proposition? It was to quite a few people, apparently. This was the text of a phishing email sent out by APT3 as part of Operation Double Tap, a spearphishing campaign to establish command and control capabilities on sensitive systems through the exploitation of multiple vulnerabilities. It was a complex, well thought out attack.
In the ‘good old days’ of computers, hacking was a term associated with adolescents living in their parent’s basement or with specialized professionals with long experience in infiltrating systems. Security systems were decentralized and typically took a backseat to more important pursuits such as development.
Not anymore, though. Today’s attackers are patient, organized, determined, and numerous. Attacks are multi-layered, with multiple levels of planned activities to ensure success. Each layer of the attack gives the attacker several options. All of the information needed to exercise these attacks is easily available, both on the public Internet and on what is known as the dark web. One glance at the MITRE ATT&CK’s Groups page, and the extent of the danger is plain to see.
This is why securing the enterprise is no easy task. The volume, complexity, and diversity of attacks means that it is next to impossible for an analyst to be able to know an attack when they see it, because the same attack is seldom experienced by the same analyst. When multi-stage, complex, and diverse attacks happen at the same time it becomes impossible to identify the signs of attack for what they are. The APT3 attack described earlier, for instance, has 10 distinct steps – each of which could show up as an individual alert.
The worst part is, most of this information is just a Google search away. But keeping track of every video, every WikiHow article, and every walkthrough guide for a hack isn’t possible.
Or, it wasn’t possible. It is now, with the MITRE ATT&CK framework.
The MITRE ATT&CK Framework
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. The MITRE ATT&CK framework addresses the need for setting a baseline for attack identification and protection. It provides a blueprint for attack techniques mapped to various stages of the attack, or the ‘kill-chain’ as it is popularly called. It is a free, globally accessible knowledge base of adversary tactics and techniques based on real-world observations of cyberattacks. It gives insight into the real-world attack surface arranged by attack stages, from initial system access to data theft to sabotage.
MITRE also provides a PRE-ATT&CK framework, which looks at pre-attack activities conducted by malicious agents.
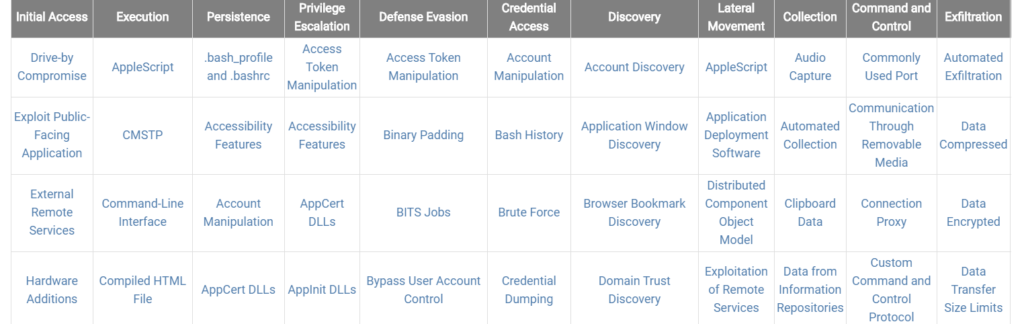
Here’s a snapshot of what the MITRE ATT&CK framework looks like:
In the table above, each of the headings describes a stage of attack – and every item under it is a technique for navigating that stage. The snapshot above shows only a small portion of the matrix; each of the stages has at least 9 techniques, with some having in excess of 25. Each of these techniques is described in detail. The page on Hooking, for example, describes the method, examples of it being used by known groups, and mitigation and detection techniques.
Here’s how a typical attack may happen –
- An attacker exploits a public facing application (typically an insecure or poorly secured web application open to the Internet) to gain initial access.
- They then use a compiled HTML file, placed in the web directory of the insecure application, to execute malicious code.
- The attacker then uses access gained through the code execution to create a user account on the target system for persistence.
- With their user account the attacker can perform a traditional remote login and work on privilege escalation through access token escalation.
And so on. With this wealth of information it becomes essential for security analysts to match the alerts coming into their SIEM with their relevance on the MITRE matrix.
Why isolated alerts based on MITRE are not enough
Every vendor wants to align with the MITRE framework. The problem they have is that the framework isn’t simply a list of alerts. The framework defines a new methodology for analyzing security threats, using a multi-level threat chain that links threat alerts by the stage of the attack. Most legacy SIEMs are focused on alerts and anomalies. They are not focused on putting together the pieces to identify the actual threat hidden behind multiple correlated alerts.
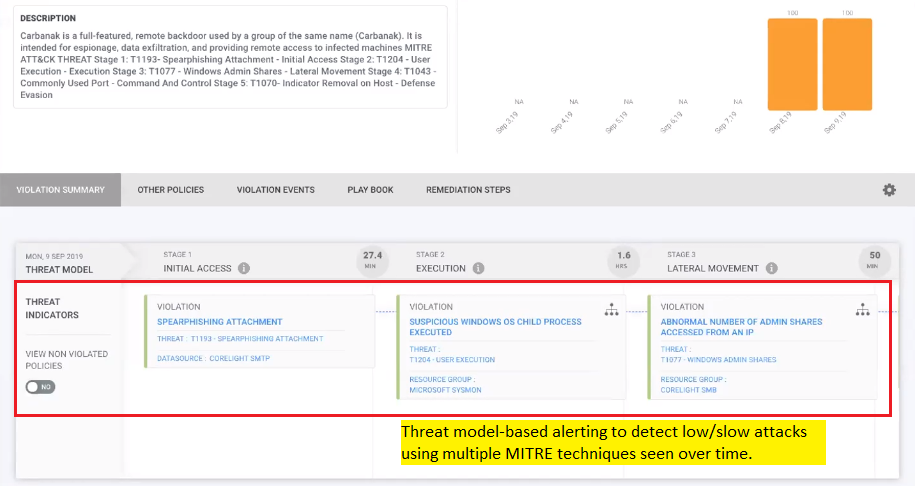
There is only one SIEM that is fully aligned with the MITRE framework. The Securonix platform does this through threat chains and behavioral analytics.
Built from the ground up to work with threats, not alerts, the Securonix threat library contains both behavioral models and threat chain definitions that have been mapped to MITRE. While other vendor products stop at gathering alerts, Securonix goes further. It combines relevant alerts together over time, using threat chains to detect and prioritize the highest risk threats. The Securonix platform uses a risk scoring algorithm that assigns appropriate risk values to each individual alert in order to determine attack priority. This underlying threat chain methodology is very similar to MITRE’s multi-stage ATT&CK definition.
Since the underlying methodology is the same as MITRE, the Securonix platform is almost perfectly matched with MITRE ATT&CK. 80% of the 364 use cases defined within MITRE are mapped within Securonix, with more being added all the time. Available Securonix content also includes additional predictive Securonix indicators like Flight Risk Behavior, Job Exiting Behavior, and traditional insider threat indicators like Activity from Terminated Users which are not part of the MITRE framework, but are clear threats, nevertheless.
Securonix has added multiple features to help analysts combine the information they see in to the MITRE matrices – not only helping identify threat risk levels, but also plan mitigation and defense.
Here’s how.
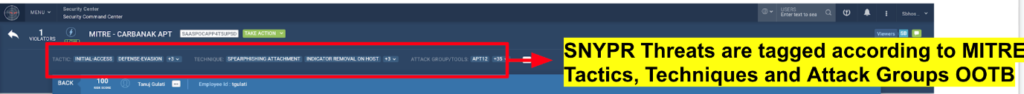
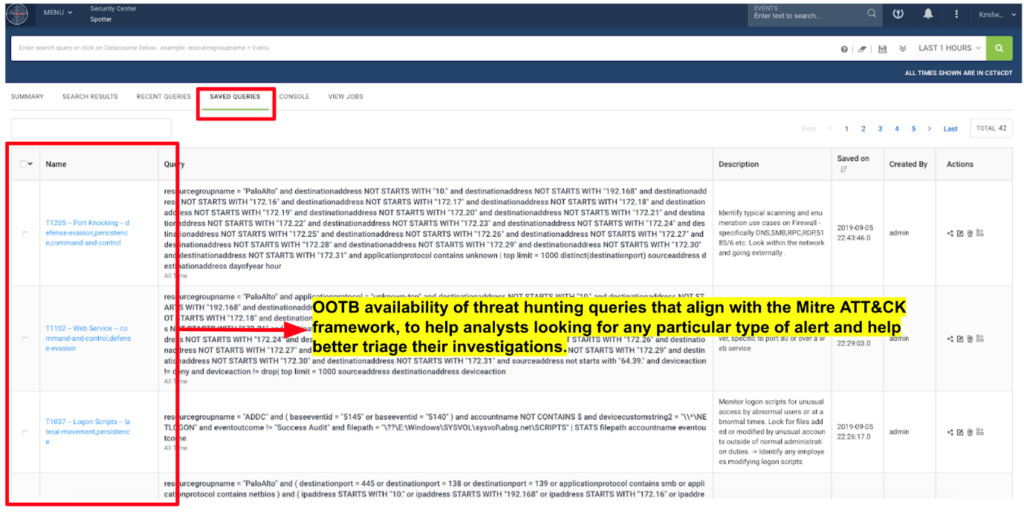
Threats that come into Securonix are tagged for MITRE compliance, while the threat model-based alerting indicates persistent attacks that are using multiple MITRE techniques. Additionally, the threat hunter reports also contain preconfigured queries that align with the MITRE framework.
Why is Securonix better?
Out of the box, Securonix provides the following MITRE-oriented feature sets:
- Prepackaged content aligning to MITRE techniques – including reports, use cases, and dashboards.
- Threat hunting queries based on MITRE techniques, tactics, and procedures (TTP) are available as a part of the threat hunting service (shown above).
- Ability to connect MITRE techniques as threat chains to prioritize risk (currently Securonix is the only SIEM to do this) along with comprehensive advanced persistent threat (APT) and additional threat information.
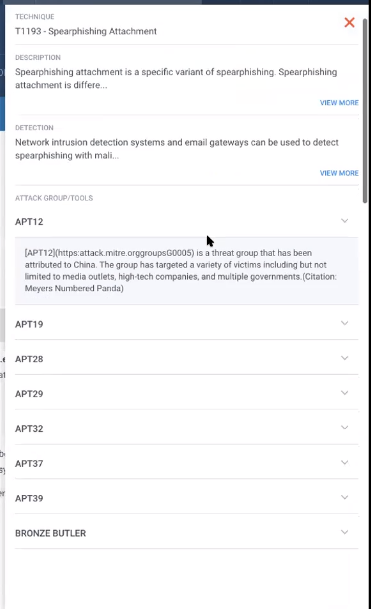
- Help with investigating an incident with references to attack groups or tools.
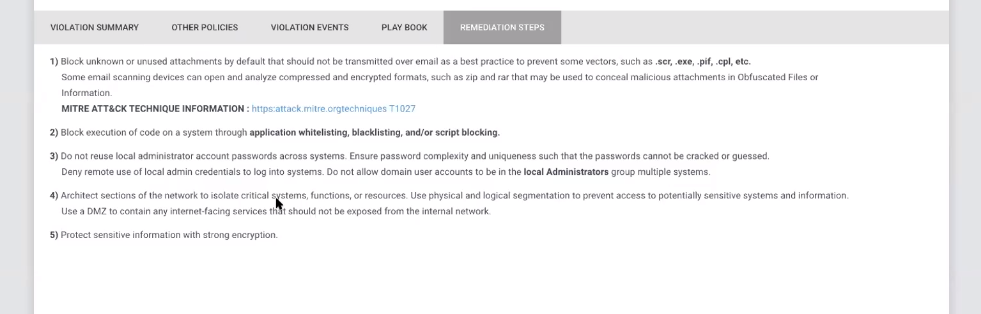
- Remediation steps for avoiding future attacks specified in the user interface.
- Based on community contributions, new TTPs will be added or updated in the content periodically.
All of these features are what differentiate the Securonix platform from other SIEMs.
Here’s a summary of the advantages of Securonix:
| Feature | Securonix | Other SIEMs |
| Threat Chains leveraging MITRE TTPs | Yes | No |
| UI representation with MITRE TTPs for investigation | Yes | No |
| Pre-packaged MITRE TTP based hunting queries | Yes | No |
| Remediation Steps for Threat Management based on MITRE | Yes | No |
Thanks to MITRE, security professionals now have the means to map their work. With Securonix and MITRE working together seamlessly, visibility for the security analyst into attacks is unparalleled.