- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Tyler Lalicker, Principal Detection Engineer, Data Science
Insider risk teams are often at the forefront of protecting intellectual property for an organization. Each incident is different, but they tend to follow common themes. The story of the attack can be seen through different profiles of behavior with distinct sets of indicators.
In this post, we will discuss the Ambitious Leader profile which comes from research at PERSEREC (originally the Machiavellian/Avenger subtype), CMU’s Insider Threat Center and NATO where they call out the Ambitious Leader and the Entitled Independent as two distinct models of insider data theft. Stay tuned for the rest of our blog series on the top insider threat profiles and their risk indicators.
Threat Profile: Ambitious Leader
Impact area: Data theft
Severity: Critical
Description: Insider with a high level of access who recruits others to pursue their own interests at the expense of the organization.
The Ambitious Leader is a motivated individual seeking personal or professional advancement. Unlike the Entitled Independent, this profile type is less likely to show signs of dissatisfaction or work stress. Because of their strong work performance, the individual will often find themselves with high levels of access to resources including intellectual property, systems, and people. This profile type does not act alone; they recruit others to orchestrate a large theft of intellectual property and then leave the organization together. They often then leverage these resources to join a competing organization, form a new competitor, or form a consultancy that profits from the theft. While less common, the Ambitious Leader comprised approximately 1 in 5 of the cases reviewed by the CMU insider threat research.
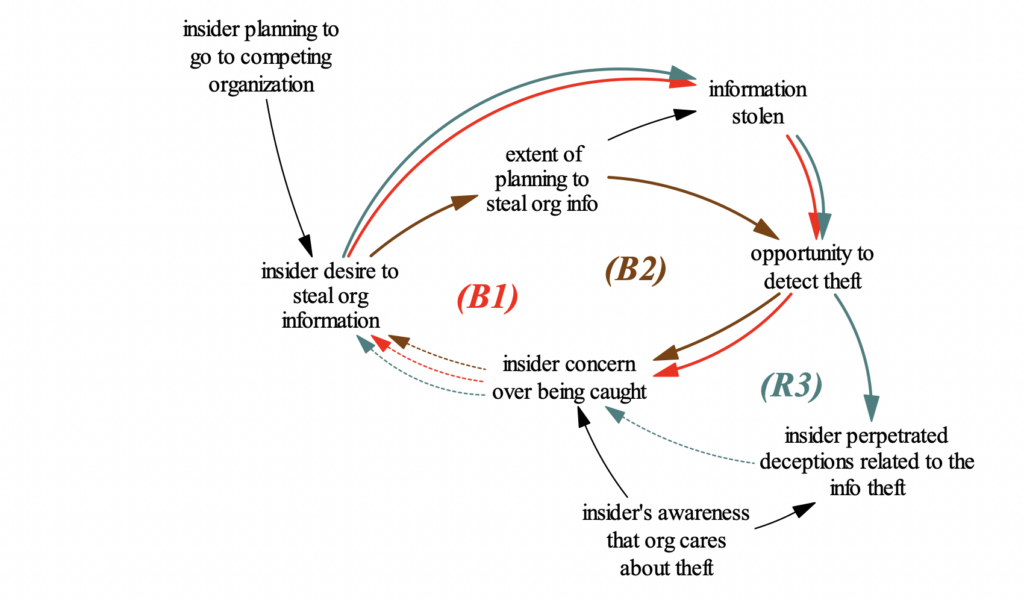
Figure 1: Theft planning by the ambitious leader
Image credit: “A Preliminary Model of Insider Theft of Intellectual Property”
The Critical Pathway to Insider Risk model shows that a variety of stressors can lead to an increased risk of negative action. Common ones include professional stressors such as poor performance or review, personal stressors such as financial or relationship issues, or community stressors like dealing with a global pandemic or war. This Threat Profile has a strong motivation for significance and personal or professional advancement, which opens a unique view into specific stressors and organizational responses that can increase risk.
For example:
- An ambitious individual may be quicker to be disappointed by unmet expectations due to setbacks with their career advancement. Poor performance may never be evident, but the insider could be facing large stress due to feelings of personal failure or loss of control.
- Their consistent high performance can lead to organizational over-reliance on the insider or leniency despite examples of bad behavior. The over-reliance on an individual can cause the organization to make missteps by failing to effectively sanction counterproductive workplace behaviors. Failing to effectively take action when something goes wrong both leaves the organization open to negative impact and often emboldens the Ambitious Leader.
- The Ambitious Leader’s strong drive and high level of access present a unique opportunity. They can choose to find personal success by leveraging their access to form a group of individuals who work together (sometimes unwittingly) to siphon important resources from the company. Then, they take the stolen information and people and form a competing company, a consultancy, or join a competitor.
The CMU study suggests some key differences between the Ambitious Leader and the Entitled Independent behavior profiles. The Ambitious Leader type is more likely to obfuscate their data theft activities and encourage their conspirators to do this as well. This may be because the Entitled Independents often don’t think they are doing anything wrong or don’t have specific intent to use the data after they take it, whereas the Ambitious Leaders and their conspirators are executing a heist with a specific purpose.
Case Study
Let’s consider a real-world example. In our case study, the Ambitious Leader was a great performer that worked on part of the core products of the victim organization before leading the pursuit of self-driving vehicles. This gave the insider access to incredibly valuable intellectual property, company engineers, and external vendors.
The malicious insider formed a separate company in the self-driving space with the intent to sell it to a competitor. While employed at the victim organization, the Ambitious Leader held interest group meetings to solicit participation from key members of the self-driving team and worked with them to steal hundreds of millions of dollars worth of intellectual property. Before leaving the victim organization, the Ambitious Leader met with leadership at another company to discuss selling the self-driving team and their intellectual property for “market value.” The team then conspired to delete critical data to hinder any investigation and created processes to obfuscate what they had done along the way.
In the end, the conspirators ended up selling the company for over $600M and 20% of future self-driving revenue. Fortunately, the scheme unraveled, and instead of getting rich, the leader found himself looking at an 18-month prison sentence after the investigation.
Once again proving that reality is stranger than fiction, the story took an unusual turn when our malicious insider founded a church where he planned on raising a “Godhead” artificial intelligence algorithm and leading humanity through the coming AI revolution. In an interview discussing his new church, the Ambitious Leader said, “We’re in the process of raising a god. So let’s make sure we think through the right way to do that. It’s a tremendous opportunity.” Next, let’s dive into the technical and behavioral indicators that are relevant to this story.
Personal predispositions
While many of the indicators revealed by the forensic investigation were technical in nature, public reports and interviews also shine some light onto the personality, concerning social skills and prior rule violations of the perpetrator.
Typically, the ambitious leader archetype shows consistent drive and motivation towards significance, and after reviewing public interviews and speeches this was also the case for our offender. In one speech at Berkeley-Haas School of Business, he spoke about some of his decisions that may indicate some moral flexibility:
“The car rental agencies also got back cars with bald tires and a few dents, but you got to take risks to get the job done.”
This issue with moral flexibility was also seen in a variety of other incidents including the decisions to alter programming to go on unapproved routes and to use unlicensed drivers for testing. He also drew ire from leadership by opting to get lobbyists to develop policies beneficial to his work without approval from his superiors.
His ambition and drive for significance were consistent and potentially caused some rifts in his interpersonal relationships. He founded a church, which is about raising a “God” where he envisions a future where he leads the human population on a safe transition towards AI supremacy.
In public interviews and speeches, he spoke in grandiose ways about his role in what he sees as an inevitable future where AI reigns supreme. He placed himself at the center of the ideology by talking about how he is a creator and teacher of the “Godhead,” an artificial intelligence algorithm.
His unusual behaviors seem to have had an impact on his interpersonal relationships. One of the conspirators in this plot was named the CFO of the church and when questioned about it he distanced himself from the Ambitious Leader, stating that he thought the church was simply a joke or PR stunt.
While some of this activity came up after the actual data theft, the observables point to some potential personality or interpersonal issues that are consistent with the Ambitious Leader threat profile and the Critical Pathway to Insider Risk.
Behavioral risk indicators: personality or social skills issues; previous rule violations
Stressors
The insiders involved in this case worked at the bleeding edge of technology, trying to solve incredibly difficult problems. This may have led to high levels of work stress, especially given that there was an organizational shift to spin off the moonshot project, resulting in changes that may have been stressful to the Ambitious Leader.
Generally, organizational stress that would be highly impactful to the Ambitious Leader profile would include:
- New leadership / management changes
- Organizational shifts including mergers, acquisitions, and spinoffs
- Company performance degradation
These particular stressors are impactful because they can interrupt professional advancement by introducing new impediments to advancement or remove some of the control that the insider needs to feel over their careers. Consider the combination of these stressors with conditions that impair judgment, certain personality disorders, or interpersonal and social skills issues. None of these factors alone can predict that an insider will turn on an organization, but together they can increase the probability of risk to the organization.
Behavioral risk indicators: spike in turnover by organizational unit or department; direct management change
Concerning actions
The malicious insider and his team did several things which were concerning before their exit from the victim organization. The Ambitious Leader formed a startup that was a direct competitor to the segment of the company he worked in, self-driving vehicles. The malicious insider team used internal resources to solicit additional people to join in on the conspiracy to steal this data. Right before his exit, some of his team looked into their NDAs, potentially to get an understanding of the implications of the intellectual property theft. They also looked into different methods of deleting evidence and evading detection. The team also showed multiple forms of communication during their employment with competing organizations.
Post-exit, the team made many connections to people from within the victim organization to solicit additional talent and intellectual property. Some also proceeded to continue accessing internal data even after they exited the organization.
Behavioral risk indicators: searching for NDA / employment agreements before leaving organization; searching the internet while on the company network to identify how to delete and “double-delete” data; communicating with competitors; access to internal resources post-employment; indicating organizational conflicts of interest
Organizational response
There is limited visibility into the victim organization’s response or sanctions against the conspirators. Post-exit, clearly there was legal action taken in the form of several lawsuits against the Ambitious Leader and the organization that purchased his company.
There is some specific evidence of maladaptive organizational response by the victim organization. Before announcing their exit, one of the software engineers at the victim organization was interrogated and accused of their intent to leave. The manager treated them with hostility stating they would “crush” them if they left (they left almost immediately after this conversation).
The Ambitious Leader also showed an escalating pattern of risky behavior for violating rules, regulations, and policies. It is unclear what (if any) actions that the victim organization chose to rein in the activities or mitigate risk. Given the high levels of autonomy granted to the Ambitious Leader, there is a potential that the organization acted too leniently because they relied so heavily on his work. This lack of effective mitigations or sanctions may have exacerbated these issues.
The organization’s failures include a lack of timely action to rein in the Ambitious Leader’s concerning workplace behaviors as they continued to escalate, and this specific escalatory action towards an employee has a tendency to make a bad situation worse. Effective organizational response is a difficult balance of decisive, timely action and enlightened management working together to help aid those at risk.
Technical indicators: direct management change; spike in turnover by organizational unit or department; maladaptive organizational response
Entity risk
The Ambitious Leader and his conspirators had access to massive amounts of intellectual property. They also worked directly with important engineers, managers, and external parties in the self-driving space. This level of access made it possible for them to cause serious damage to the victim organization’s prospects in self-driving if they were to leverage these resources inappropriately.
Technical indicators: correspondence with key contractors and vendors; sensitive file access; sensitive server access
Recruitment
The insiders used internal company communication and even on-site office space to solicit people to join their startup and participate in this data theft. While still employed at the victim organization, the team used internal email and calendars to invite employees and tell them about the opportunities at this startup. These interest meetings attracted a group of insiders who eventually joined the Ambitious Leader in his new venture. Meetings took place on site and off site and many insiders who elected not to join the competitor discussed the solicitations. Post-exit, multiple solicitations went out to internal emails to solicit those who may be interested in joining.
Technical indicators: correspondence with competing organizations; communication with departed employees
Exploration
According to a court filing, prior to exiting the victim organization the Ambitious Leader worked to gain access to a critical data repository that housed the most sensitive information for the self-driving division including blueprints and designs.
Technical indicators: privilege escalation; anomalous sensitive data access
Persistence
The insiders took a variety of actions to preserve their access to the sensitive data. They created backups of their machines in external and cloud storage. They also made use of public storage for their work, giving them access even after they exited the company.
Technical indicators: connections to public cloud storage sites; backups to unsanctioned mediums
Evasion
The forensic investigation revealed multiple interesting indications of evasive behavior used by this team. They had many lines of communication about deleting data, and had even created log artifacts that show they were trying to find out how to remove evidence from their actions including “double-deleting” emails.
This activity resulted in massive amounts of data destruction across email, endpoints, and removable media. One of the team members deleted over 57GB of data. Many of the deletions occurred right before exiting from the company and then after they had been alerted about the investigation into their activities.
Actions also included zipping files and using backups at home which may be harder to detect.
Technical indicators: spike in file deletions; spike in email deletions; spike in file modifications
Collection and staging
Dropbox was used as cloud storage to stage and collect important data, alongside physical media devices and email. One of the team members also accessed a shared drive after exiting the victim organization, indicating that they may have used internal resources as a staging ground and enabled external access.
Technical indicators: external account or dormant account resource access; connection of removable media; spike in download of source code file extensions from network repository; local data staging; remote data staging
Impact
In all, the team stole over 10k documents, 74k images, and nearly 200k source code files. They were able to sell their company to another company for $680M and a 20% stake in future profits from the self-driving sector in the new parent company.
The damage to the victim organization was not limited to just the loss of significant talent and intellectual property, but also to damage caused to their ability to compete in the self-driving space. One way to evaluate the damage caused by IP theft can be trying to compare it to what happens to company revenue on a product after a patent expires. One study on drug pricing points to approximately a 50% price decline in just the first year after generics are introduced due to patent expiry. This indicates that when additional competitors are capable of using the IP, pricing power weakens. The degree of this damage will likely vary by industry vertical, but this shows the potential damage of intellectual property loss to competitors.
Given the speculative nature of private equity and a significant lack of public information, it’s hard to comprehend the total economic damage attributed to just this one insider threat case. However, the victim company was valued at ~$175B in 2018 (one year after the initial lawsuit against the Ambitious Leader) and 18 months later was raising money at only a $30B valuation. While this insider’s actions are not the only negative impacts the organization may have had, it is certainly a significant part of the story.
As for the Ambitious Leader? In 2020, he was found guilty, charged hefty fines and slapped with an 18-month prison sentence and he closed his church in 2021.
Technical indicators: data upload via web; exfiltration to removable media; data exfiltration via email
Summary
The Ambitious Leader threat profile represents a large amount of risk to an organization. The group of indicators used to identify this threat profile overlaps with the Entitled Individual, but there are key behavioral and technical indicators that separate the two. The threat posed by the Ambitious Leader can cause greater organizational damage, so differentiation is helpful for insider risk teams to prioritize the higher severity-attacker.
Traditional technical indicators for data theft:
Anomalous data egress over network traffic, removable media, email
Data staging of sensitive documents to local and network repositories
Unauthorized access from dormant or expired accounts
Communication with competitors over email
Specific technical indicators for the ambitious conspirator:
High level of sensitive data access (entity risk)
Spike in data deletions or file modifications
Deletion of communication data
Cross-entity collusion to steal data
Specific behavioral risk indicators for the ambitious conspirator:
Organizational stress from turnover, management changes, or company performance
Searching the web for “how to delete/wipe data”
Searching internal network or web for NDAs and employment agreements
Correspondence with off-boarded employees
Organizational conflict of interest
Pattern of prior violations
The Ambitious Leader can be identified by combining the traditional indicators of data egress alongside indicators of violations, collusion, obfuscation, and organizational shifts that impact the stress of this insider threat profile. It’s important for insider risk teams to understand a complete history of rule, policy, regulation or social norm violations (and organizational responses) as indicators of risk. Due to leniency caused by organizational over-reliance, the Ambitious Leader’s violation history may not be fully documented. Combining all of these indicators together, we have a profile that can help us better detect and mitigate risk from this type of insider threat.