- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
With 2022 in the rearview mirror, we wanted to take a look at the important product improvements Securonix delivered in the past six months for Next-Gen SIEM. Our focus has always been on customers, and what we delivered in 2022 is proof of that commitment. The updates we’ve made have enabled users to accelerate along the cybersecurity maturity curve and gain more value from their investments.
In the last six months, we have worked toward better scalability and faster performance while making it easier to manage content and simplify investigations. Here are three quick highlights:
- Increased content library support for 57 new parsers and increased detection content by 337 new policies
- Unlocked better visibility and accuracy with certified parsing, detections, and reporting for the top 86 most used data sources
- Added comprehensive support for 10 new compliance categories which added to our 170+ OOTB reports (including PCI, ISO, SOX, HIPP, SOC, GDPR)
- Improved search performance for archive and hot data stores by 70%
While pushing innovation ahead we also invested in UX improvements that make cybersecurity less complex. Here’s a 10,000-foot view of the major features and capabilities we’ve added in the last six months.
Better Availability & Scalability
To be a strong cybersecurity partner, Securonix needs to scale and grow with you. We need our platform to continue to deliver on the needs of small and large enterprises alike. That is we doubled down on enhancing platform availability and scalability while expanding coverage for better data management and search capabilities. Some of these new capabilities include:
Scaling improvements for AWS SQS S3 connector
You can now process data in near real-time with AWS SQS S3 connectors that can support ingesting data at 100K+ events per second (EPS). Previously, this connector supported ingesting data at 50-60K EPS. This improvement was made possible due to the introduction of a pipeline framework where compressing, splitting, and publishing data is done by different threads in parallel.
Azure Data sources on Gov cloud
Securonix now provides support for ingesting data from Azure data sources that run on Gov cloud. We understand how critical it is to eliminate blind spots and ingest data from all of the sources in your environment. In order to get the most out of your SIEM and boost your security posture you need full visibility into all data sources. This update allows those using Microsoft/Azure Government in their infrastructure to now ingest data from these instances into the SIEM, which eliminates gaps in visibility.
Microsoft Basic Auth Deprecation
Last year, Microsoft announced that all Azure services would support OAuth-based authentication only. Due to this mandate, we modified all existing integrations that leveraged basic authentication to meet this criterion. This update ensures that you can continue to ingest data from Microsoft services and will have added support for pulling data from new data sources.
Save Time with Easier Administration and Content Management
Security practitioners have a difficult job. Securonix aims to simplify content ownership, tracking, and management to save analysts’ time and eliminate manual updating or administrative tasks. Our goal is to continue to deliver new threat content regularly and to help you maintain a clean incident management system without complexity. Here are some of the capabilities we launched last year to save you valuable time.
Multi-Attribute Whitelisting (MAW)
Previously analysts were only able to whitelist a single attribute at a time, but this new feature makes whitelisting less manual. Multi-Attribute Whitelisting (MAW) now allows a SOC analyst to create and add a combination of up to 3 attributes to a whitelist. MAW provides analysts with more granular control of whitelists. You have the ability to filter alerts for very specific combinations of attributes that can be fine-tuned to weed out false positives or known safe scenarios. This reduces the time it takes to create whitelists and minimizes alert fatigue by narrowing the scope of the exact scenario that needs to be monitored.
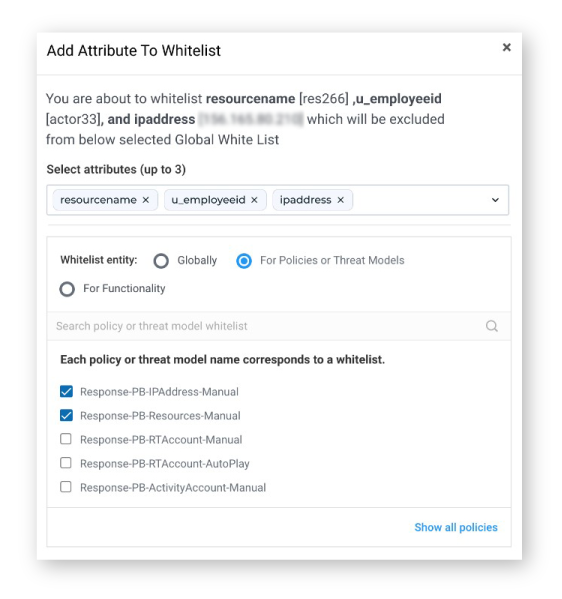
Multi-Attribution Whitelisting now allows you to select up to 3 attributes
Classless Inter-Domain Routing (CIDR) Enrichment and Lookups
Now, analysts can create a lookup table with CIDR ranges including enriching the CIDR range with additional data. Moreover, policies using CIDR ranges can be created to generate violations for further analysis. Previously, users had to input lookup tables with a single IP address per row, requiring them to manually list out IP addresses in individual lines. Now, you can choose to create a lookup table of CIDR ranges without the additional step of conversion.
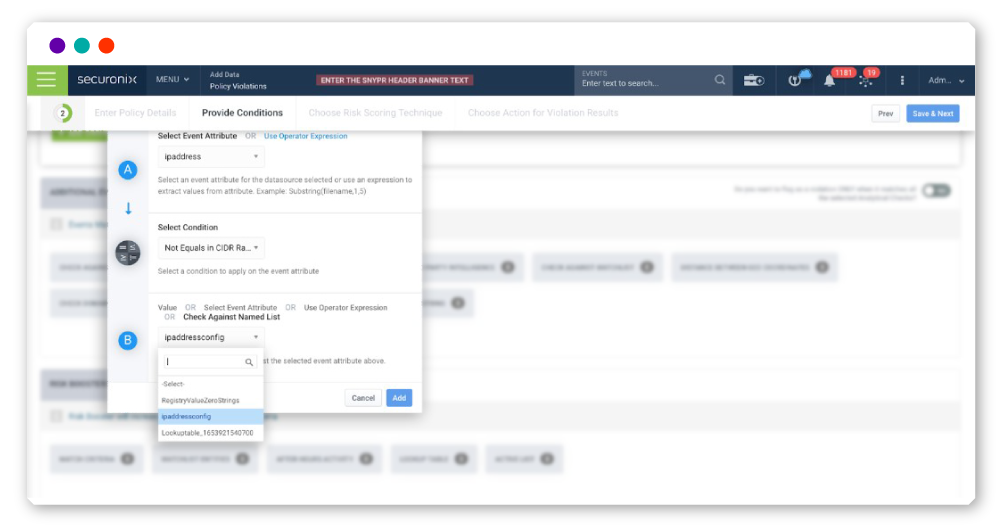
Policies using CIDR ranges can be created to generate violations for further analysis.
Auto Case Closure
Auto case closure is designed to help SOC Analysts and their Administrators keep the incident management system clean. Today, SIEM and SOAR platforms automate the creation of incidents in various forms. Although these platforms are successful at reducing manual efforts for analysts, alert fatigue can still be an issue for teams.
Last year Securonix introduced the Auto Case Closure feature that automates closing aging and inactive incidents based on a configurable period of inactivity. This means that incidents that have not been updated are automatically closed by the system. In order to ensure the right cases are being closed, we apply filters so you can observe the number of cases that are closed by the system, vs. by an analyst. This allows analysts to validate that closed cases do not need attention and that management can understand the workload. This insight may lead to the finetuning of policy configurations for optimal case management.
Managed Identity for Azure Event Hub
In this update, we built a custom authentication workflow for Azure Event Hub using Azure Key Vault that helps in the easy rotation of auth keys while also satisfying compliance mandates. This new feature provides support for using managed identity authentication for the Azure Event Hub Data sources. An earlier version of our connector only supported access key-based authentication which was cumbersome because it required changes to be made at both the Azure Event Hub and Next-Gen SIEM configurations to rotate the access key. On top of this, some compliance restrictions did not allow the access key to be stored outside of their systems.
Modifications/Customization of Policies
Modification allows analysts and detection engineers to customize or change policies at scale. In addition, source policy customizations are not overwritten by out-of-the -box updates which helps ensure policy integrity. Updates that are provisioned for the source policy will still be consumable and any modifications you make will still be preserved on top of it. Previously, there was not a dedicated section to modify/change multiple policies at once. For example, if you needed to exclude a set of IP CIDR ranges or account names then you would have to add the condition under each and every policy section.
You are now able to customize parameters such as risk boosters, risk criticality, and incident management for greater control and clarity. We will continue to expand this feature to individual event analytics in the future as part of any environment-specific inclusion/exclusion logic.
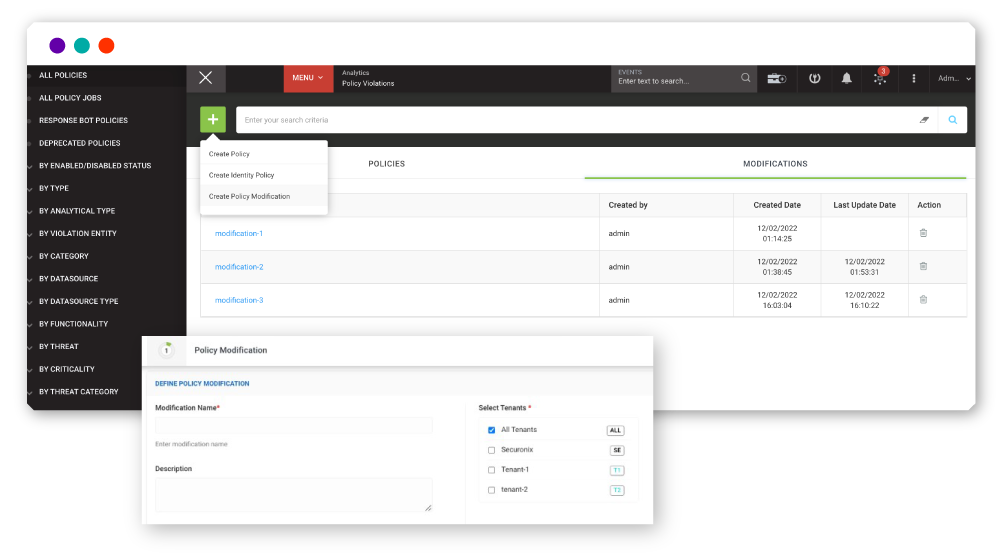
Modification is part of policy configuration and allows users and detection engineers to customize or change multiple policies at scale/in one click
Content Notification Widget
Staying up-to-date on the latest threat content (e.g., parsers, policies, threat models, etc.) is essential to detect advanced threats. The new Content Notification widget makes it easier to update detection content. This new widget allows you to get notified right in your Securonix solution dashboard. Now, SOC analysts and content developers have the latest releases and content from Securonix Threat Labs at their fingertips.
Additionally, you have better visibility on policies that are outdated and are no longer being supported. This will ensure you are always working on the latest content versions so you can prioritize the right threats.
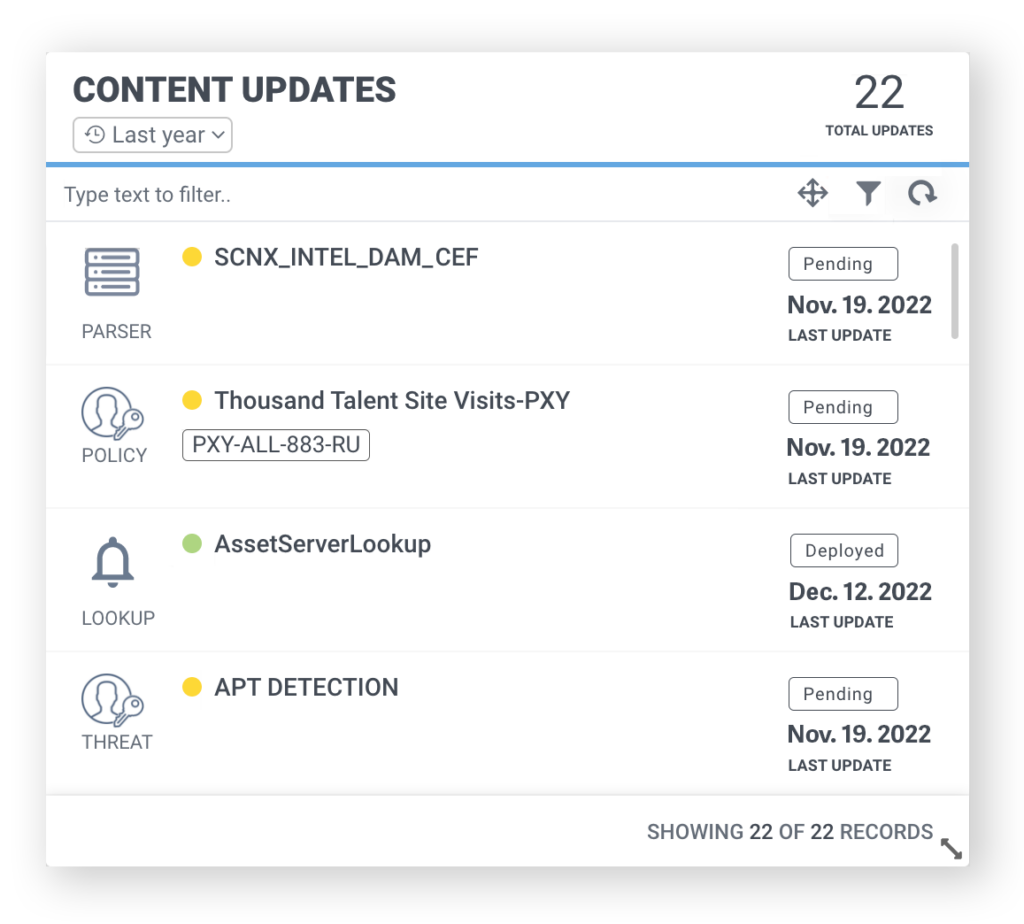
The content widget shows you the latest threat content right in the Securonix platform.
Accelerate Threat Detection & Investigation
We understand that every second counts in threat detection, investigation, and response (TDIR). That’s why we focused on helping expedite the analysis of incidents with integrated event context. We expanded our detection content availability with 330+ new policies in the last six months and also improved search performance to ensure faster remediation. Here are a few of the capabilities we launched to accelerate TDIR.
Improved Search Experience
We spent the last half of 2022 focused on improving the UX around Search. This focus brought many improvements in the consistency and handling of queries so you can spend more time resolving and less time hunting. EVAL operators for complex searches are now being pushed down to the underlying search layer instead of executing on top of the app, which delivered a 50% performance increase.
These updates allow you to run searches that have a faster return, and with more accuracy and relevance. This faster and more accurate performance is due to the improvements made to the query routing system that now redirects queries based on the fields and scope of the search you specify.
Base64 Encoded
This improvement allows derived fields that are encoded with Base64 to be decoded at the time of enrichment. Now, SOC analysts can apply policies and threat detection against fields that they could not previously. This lets you utilize encoded logs for better search and analytics.
SOAR Support for Threat Models
The addition of Securonix SOAR early last year was a major step in our journey to create a true end-to-end TDIR platform. One of the notable features we added allows you to automate the triage and remediation of threats using SOAR playbooks. Securonixc SOAR supports both policy-based and threat-based threat models and gives you the flexibility to pull the unique attribute values for the entire threat so you can build your desired response. This update lets you automate any user actions available on the Securonix dashboard for threats, so you can focus on more meaningful tasks.
On-Prem SOAR Support
Securonix recognizes the importance of supporting hybrid IT deployments. That’s why we launched SOAR on-prem support for Securonix SOAR which allows you to automate response actions for on-premise security devices with no significant changes. Notably, support for Active Directory and Palo Alto NGFW was also included as part of this release.
Want to know what’s next? Follow us on our journey as we continue to push boundaries and deliver on our promise of security analytics at cloud scale.
Get a demo to learn more about our new products and features.







