- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
As a leading provider of security information and event management (SIEM), we are dedicated to helping you stay ahead of emerging threats. Last quarter we continued our tradition of innovation with the release of new features and capabilities that are pushing detection and response to new levels.
Some highlights include:
- Identified more emerging threats (428), codified and swept more TTPs/IoCs (11,132), and saved customers more average manhours per month (178) than any other quarter on record with Autonomous Threat Sweeper.
- Increased threat content coverage with 60 New Detections and 22 New Parsers.
- Published 12 advisories and threat research articles
While pushing innovation ahead we also invested in improvements that make cybersecurity less complex. Here’s a 10,000-foot view of some of the features and capabilities we added in Q1:
Better Scalability and Performance
- Data Processing Performance: Securonix offers an automated solution for scaling processing pipelines that eliminates data delays and ensures that the platform adapts to your current data flow needs. This feature includes an automatic detection mechanism to determine when sandbox data sources and policies are ready for production. This helps streamline the process and prevents any potential delays. By automating the scaling of processing pipelines, instead of relying on manual processes from operations, you now have a less manual and more effective data management solution.
Better Threat Coverage
- Real-Time Threat Sharing: Autonomous Threat Sweeper (ATS) enables you to automatically pinpoint new threat indicators across ingested data historically, and rapidly recognize your security posture against emerging threats. Now with the introduction of Real-time Threat Sharing, ATS subscribers can upload a custom .csv file containing IoCs and ATS will consume, analyze, and sweep against all relevant data sources. This can save your analysts hours in manual effort and provides an avenue for you to leverage the power of ATS on your own. By submitting custom internal intelligence to ATS, you can quickly understand your security posture against said intelligence across all relevant data sources.
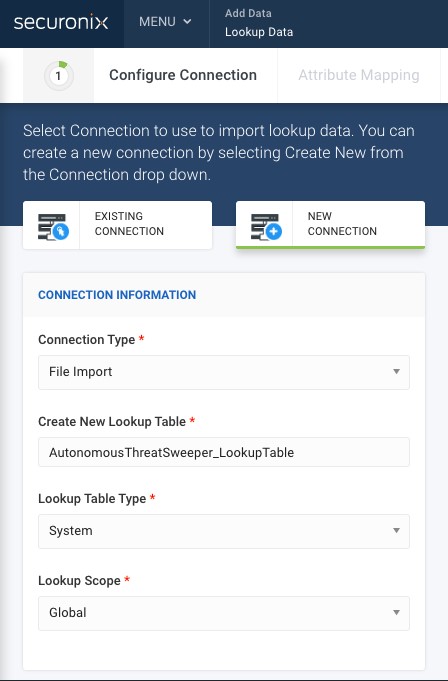
Import csv. files containing IOCs into ATS to sweep for threats.
- Risk Scoring: It is important to have a clear and comprehensive view of your entity’s risk profiles. That is why we utilize aggregate risk scores, that take all of your data sources into account to provide a unified view and better risk profiles for each entity. In the past, the accuracy of aggregate risk scores wasn’t as strong as it could have been resulting in negative scores and inconsistencies across the platform. Our team has worked diligently to fix the underlying problems related to risk scoring, and we have implemented changes that ensure that you can rely on the accuracy and consistency of your risk scores so you can make informed decisions.
- Sigma2Securonix Converter: Sigma2Securonnix is a revamped BETA version tool for converting Sigma detection rules to Securonix queries. Sigma is a community language that is used to describe any adversary TTP and translate it to detection code. With the inclusion of the Sigma2Securonix converter, you not only benefit from Securonix’s Threat library but also from content developed by the Sigma community.
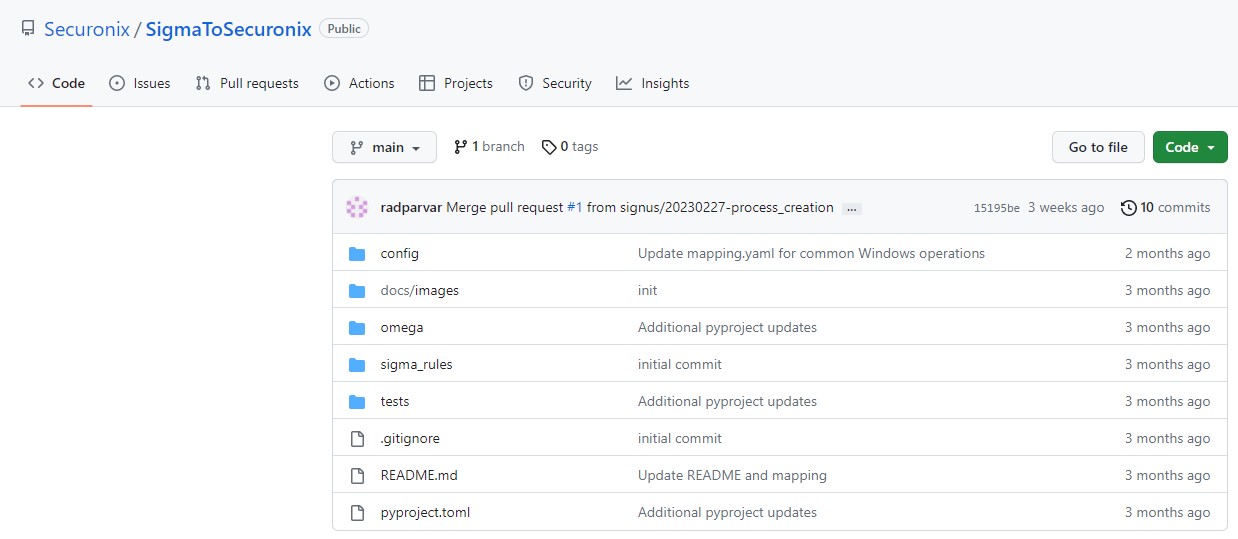
A simple tool for converting Sigma detection rules to Securonix queries.
Driving SOC Efficiency
- Query Availability in Incident API: This update allows you to retrieve all of the violations associated with an incident using the same query that is used by the console to generate the data. Query availability in the incident API provides you with more access to your data and allows you to pull specific information related to an incident in a more efficient manner, without having to manually sift through data or rely on third-party tools. Overall, this feature makes it easier to gather important information about security incidents.
- API Support for Lookup Data Management: Securonix launched API support for managing lookup data, which allows you to import lookup tables through APIs, resulting in increased efficiency through automation. With API Support for Lookup Data Management, you can now configure and import JavaScript Object Notation (JSON) structured data via API, instead of having to manually configure it in the UI and import a file. This new feature enables you to onboard lookup tables automatically through APIs, streamlining the process and reducing the need for manual effort. You can see the Lookup API Documentation here.
- Search consistency with Snowflake: Customers who are using our Bring Your Own Snowflake product can configure their system to only use Snowflake for activity data search, specifically for the indexes “activity/archive”. With search consistency for Bring Your Own Snowflake, you can now set the index to “activity/archive” and pull data directly from Snowflake, without the need to use the index=snowflake option. The benefit of this update is greater search consistency, as all searches will now be performed on the same platform, rather than being spread across multiple indexes and underlying technologies they are associated with.
Easier Operations Management
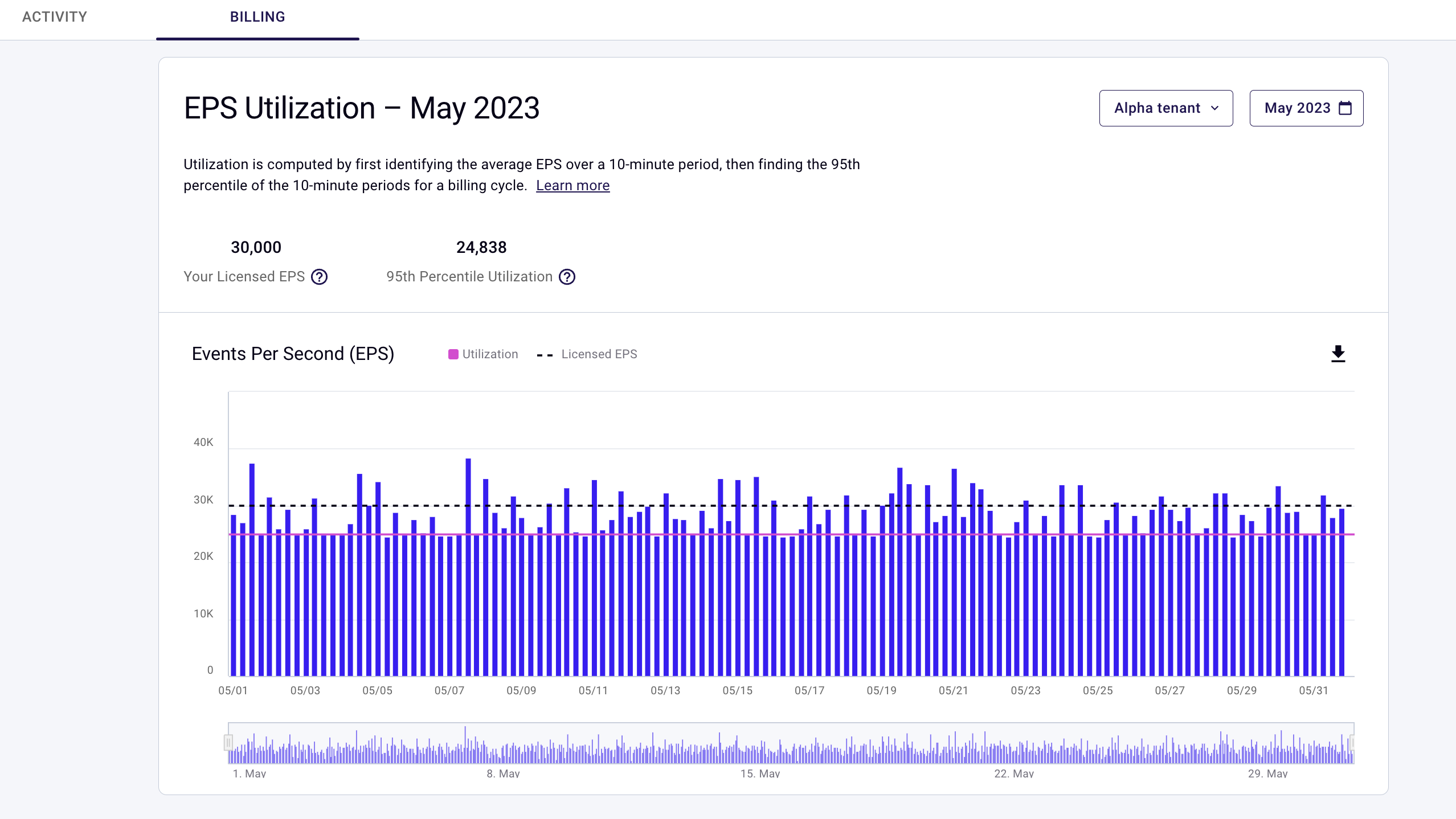
- License/Billing Overage Dashboard: Your Securonix dashboard now displays usage data for the current month and previous months against your licensed EPS entitlement. The licensing/Billing Overage Dashboard gives you the ability to more clearly see your EPS utilization and provides more transparency to your invoices.
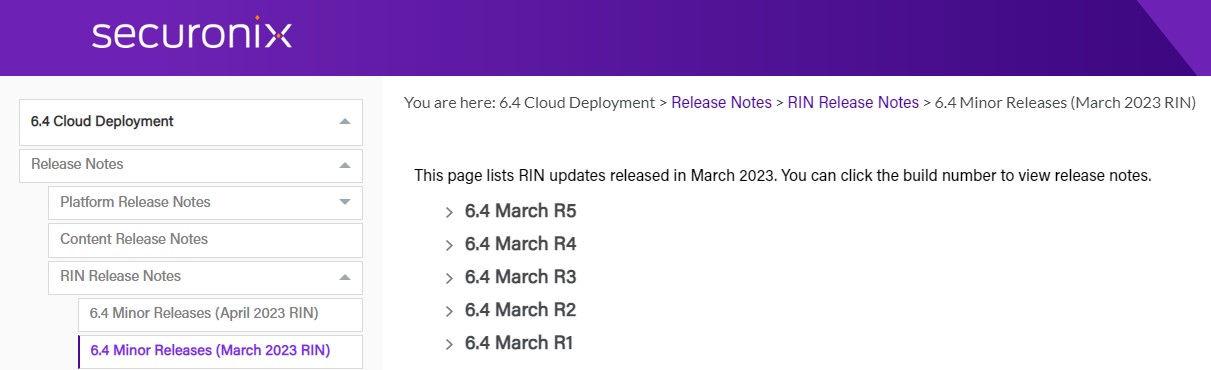
- RIN Release Notes: We have improved documentation by separating out release notes specific to the improvements we are making to our RIN. You can now easily view release notes for the RIN when making upgrade decisions.
Notable Connectors and Integrations Added
- Salipoint User Import Connector: Sailpoint customers can now ingest user data into Securonix leveraging our newly created API-based connector for Sailpoint. This connector helps you expand threat coverage with the ability to ingest Sailpoint user data (such as name, department, title, geolocation, and more). Securonix uses this additional user identity data to add context to events and activities. Additionally, this information is used during analysis to identify suspicious activities.
- Wiz Entity Metadata Connector: The newly created API-based connector for Wiz allows you to import entity metadata (such as assets on your network, IP addresses, and network activity). Metadata summarizes basic information about your data, which makes it easier for you to find and work with related data. Access to this entity metadata, and asset metadata, can be used at the time of ingestion to transform your raw events into meaningful information that is easy to understand, search, and investigate.
- Bi-directional XSOAR Integration: You can now manage security incidents directly from your XSOAR platform, leveraging Securonix APIs to create a two-way connection. The integration allows for mirroring between the two platforms, meaning that any changes made in one platform will be automatically reflected in the other. For example, if you close an incident in XSOAR, it will also be closed in Securonix, and vice versa. This feature streamlines incident management by allowing XSOAR and Securonix users to work within the platform of their choice, while still ensuring that both platforms are in sync with each other.
In addition to these updates, Securonix announced a new product called the Unified Defense SIEM that features the Snowflake Data Cloud as our backend. This new solution offers longer data retention for investigation and search and a single-tiered architecture that improves performance. With 365 days of Hot search, your security analysts improve efficiency and speed to reduce mean-time-to-respond to security events. You can learn more about this new offering here.
We hope you are as excited about all of the new features we have rolled out as we are. We remain committed to providing you with the best possible service and solutions to meet your business needs.







