- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
At Securonix we are always pushing the boundaries of what our Unified Defense SIEM can do for our customers. Our vision is to protect the world from cybersecurity threats, so we aim to continuously improve our product to help you stay ahead of emerging threats. As another quarter comes to a close let’s take a look back at some of the features we’ve added. Some highlights include:
- AI capabilities with integrated ChatGPT into Securonix Investigate
- Identified 408 emerging threats, codified and swept more than 13,534 TTPs/IoCs, and saved customers 175 average manhours per month with Autonomous Threat Sweeper.
- Increased threat content coverage with 10 new parsers, and 13 new SOAR playbooks.
- Published 8 advisories and threat research articles
While pushing innovation ahead we also invested in improvements that make cybersecurity less complex. Here’s a 10,000-foot view of some of the features and capabilities we added in Q3:
Better Scalability and Performance
Securonix Hub: The Securonix RIN evolved. Now the Securonix RIN has transformed into Securonix Hub bringing more scale, better visibility, and seamless upgrades to the Securonix Unified Defense SIEM. With the new Securonix Hub, you can ingest data and send response actions to effectively gain the visibility needed to keep pace with today’s modern threats and act to mitigate them. Securonix HUb delivers improvements over Securonix RIN with:
- Vertical scalability: No longer inhibits your Securonix SIEM because you can not add resources fast enough. Automatically scale when resources are added with the ability to support 80k EPS per data source.
- Modern orchestration: Easily deploy Securonix Hub in the cloud or on-premises using modern tools and the ability to deliver automated and silent upgrades that do not impact data collection.
- Health visibility: Understand the health and status of the Securonix hub, data collection, and devices to ensure data is being delivered efficiently and reliably
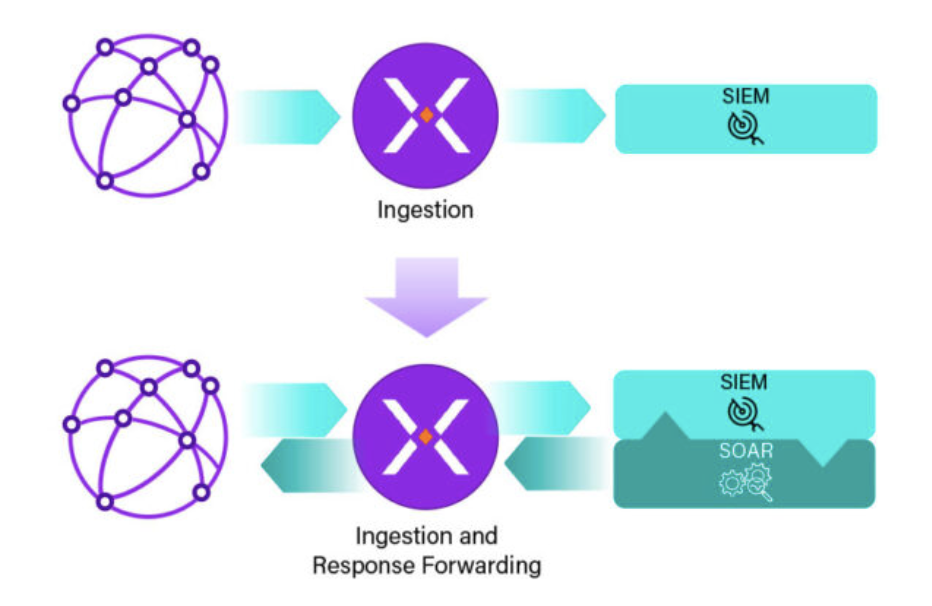
The ingestion function for SIEM has evolved from simply collecting data to now serving as a bi-directional connection point between the SIEM and the environment.
Analytics Threshold: We’ve simplified the analytic thresholds within the product that were previously complex. Improved analytic thresholds help unlock benefits around stability. For every policy, there is a threshold which we are simplifying to be based on violations. By default, the threshold is set to 100k violations and once that threshold is met it stops analyzing going forward. Users can choose to adjust these thresholds to meet their individual needs. By giving you the ability to set appropriate analytic thresholds we are helping your SOC filter out noise and focus on meaningful security events.
Autoscaling Pipelines: Securonix offers dynamic auto-scaling capabilities for the production pipeline as new data sources and analytics are introduced. Issues with poorly configured or failing data sources can create bottlenecks, slowing down data ingestion and affecting high-priority data flows. Data ingestion delays directly impact threat detection and response times. To resolve this bottleneck, Securonix automatically redirects slow-performing data to a diagnostic pipeline, ensuring that high-performance data reaches its destination without interruption. Additionally, the platform enables seamless transitions of data sources, analytics, and policies from sandbox to production, auto-scales to meet capacity demands, and efficiently diagnoses problematic pipelines to prevent disruptions to other traffic.

Securonix automatically moves slow-performing data to a diagnostic pipeline. This process of moving the slow data allows high-performing data to reach its’ destination without being impacted
Driving SOC Efficiency
Multi-Attribute Whitelisting: Previously analysts were only able to whitelist a single attribute at a time, but this new feature makes whitelisting less manual. Multi-Attribute Whitelisting now allows a SOC analyst to create and add a combination of up to 3 attributes to a whitelist. Multi-Attribute Whitelisting provides analysts with more granular control of which alerts are triggered to minimize noise. You have the ability to filter alerts for very specific combinations of attributes that can be fine-tuned to weed out acceptable violations or known safe scenarios. This reduces the time it takes to create whitelists and minimizes alert fatigue by narrowing the scope of the exact scenario that needs to be monitored.
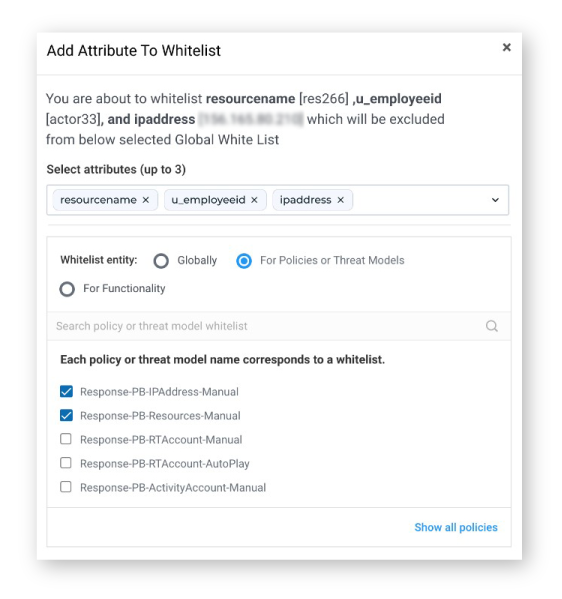
Multi-Attribution Whitelisting now allows you to select up to 3 attributes
Ipv6 Geolocation: Securonix now supports IPv6 to enrich Geolocation. If you are using IPv6 you can now take full advantage of geolocation capabilities as you would for IPv4. You can better triage incidents that originate from risky locations across the globe using IPv6 addresses.
SOAR support for Incidents: SOAR support for Incidents empowers users with the capability to seamlessly execute playbooks directly from the Incident Manager within the SIEM. With SOAR playbooks integrated into the incidents, users can effortlessly gather more context, prioritize incidents, and proactively address potential threats. SOAR support for Incidents goes beyond incident management by extending SOAR capabilities to encompass all types of alerts, including violations, threats, and incidents. As a valuable tool for Unified Defense SIEM customers, it serves as a starting point for efficient alert triage. Users can strategically limit automation to specific alerts, leading to cost savings while significantly reducing the Mean Time to Respond (MTTR) for incidents.
Better UI / UX
Policy Violation Redesign: You asked and we listened! Securonix users now have the ability to delete policies and violations within the system directly from the UI. This is helping to reduce delays and provide a better user experience.
Analytics Dashboard: The new analytics dashboard helps you understand the performance of your Securonix environment. The metrics dashboard shows graphs for how each policy is functioning and performing and allows SOC teams to easily communicate details across stakeholders,
Notable Connectors and Integrations Added
WIZ + Securonix Integration: Wiz helps organizations gain insights into their cloud infrastructure’s security by continuously monitoring and analyzing configurations, network traffic, and activity logs. Securonix collects and analyzes security data from various sources across an organization’s network, including servers, applications, firewalls, and more. By combining Securonix’s advanced security analytics and threat detection capabilities with Wiz’s cloud-native security posture management and vulnerability assessment expertise, you can take a unified approach to safeguarding your digital assets. This includes identifying risks and proactively addressing security threats in ever-changing and complex environments.
ChatGPT & Investigate Integration: The generative AI capabilities in Securonix Investigate enable you to seamlessly ask AI models questions using natural language and view it side-by-side with all the context gathered by Securonix Investigate. Because using ChatGPT without the proper security controls in place can cause data leaks, the Securonix Investigate integration with ChatGPT includes customizable security controls to prevent leakage of sensitive information, such as internal IP addresses and domain names. Security teams can control access by allowing only those with expressed permission to use the function. Securonix also scrubs sensitive information within the responses received from ChatGPT. It uses audit logs to configure detections that alert organizations of any compliance issues or sensitive data leaks.
We hope you are as excited about the new features we have rolled out as we are. We remain committed to providing you with the best possible service and solutions to meet your business needs. Existing customers can reach out to their account manager to learn more.







