- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Kayzad Vanskuiwalla, Threat Detection & Analytics, Securonix Threat Labs
Insider Threat Landscape
Organizations traditionally focus on external threat vectors, rigidly defining the perimeter as a walled-off subnet to segregate their internal production traffic from the external, untrustworthy Internet traffic.
The most sought-after target for attackers are privileged accounts or the means to elevate privileges within an environment. Beyond external adversaries, it is malicious insiders, if intentional or unintentional, who continue to be the bane of most security operations.
As attackers have become increasingly sophisticated, especially with funding from nation states, there is an even greater need to keep up with these attackers. The focus now is not only on the perimeter, but more in knowing if an attacker has already gained a foothold within the organization’s defined perimeter.
Insider Threat in the Cloud
With the move to the cloud that most organizations are now undertaking, the original perimeter has expanded to include a user population that has stretched beyond the organization’s boundaries/ locations, or as Forbes has rightly called out, “In the modern security landscape, people are the new perimeter”. Insiders in the current landscape are not only limited to the system administrators and 3rd party contractors, but also their extended supply chain including every cloud service and API that the organization is using but may not even be aware of as a security concern.
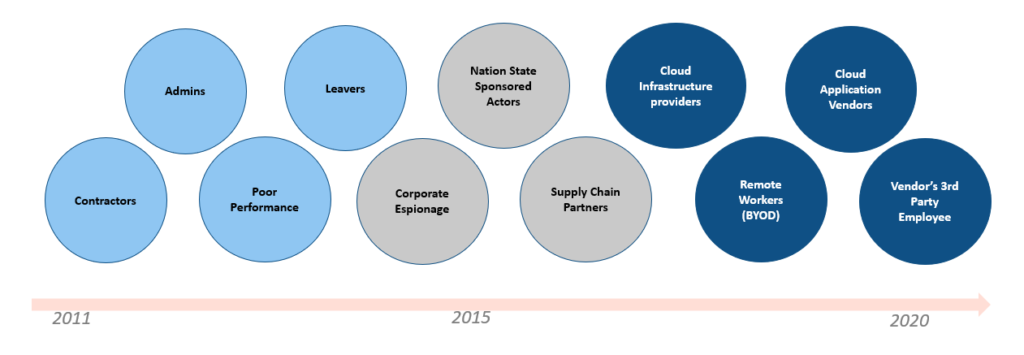
Threat Actor Landscape
Insider Threat – Enhanced Telemetry
While organizations have an understanding on what to do regarding traditional Security Monitoring, there is still a huge gap in comparable telemetry being incorporated for monitoring insider threats. CMU SEI provides a great reference of an insider threat program and how it should also integrate non-technical indicators to complement the traditional technical indicators. For insider threats, indicators such as flight risk and exiting risk behavior, poor performance indicators, and other personal risk indicators (PRIs) shown below should be continuously monitored (watch listed).
These PRIs can serve as watch listed entities that have a motive to either elevate privileges and ultimately lead to data being exfiltrated or even sabotaged / deleted.
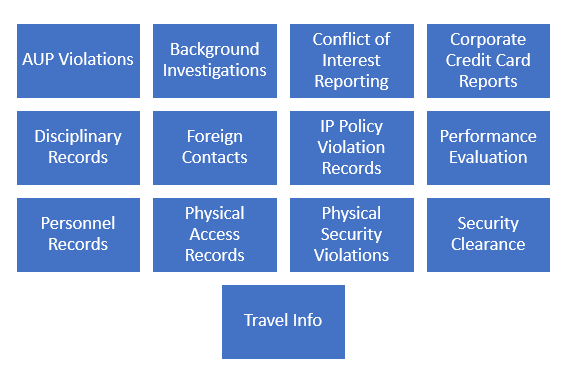
Monitoring Insider Threat in the Cloud
The traditional SOC is used to dealing with an IOC related to known malicious IPs/ domains (on the perimeter) or more recently with malicious file hashes that some EDR products provide. When dealing with insider threats, a key factor becomes intent. The intent can be in terms of an inherent risk via an intentional / unintentional insider. It becomes important to monitor the features related to inherent risk (PRIs) we just discussed under enhanced telemetry and tie it in with other indicators from more traditional security log sources including audit events from cloud infrastructure. Combining multiple features and aggregating risk for the entity (user) performing these actions across various datasets is key to a successful insider threat monitoring program. Below are a few examples of how insider threat-based models can be setup focusing on the inherent risk (privileged accounts or flight risk indicators or poor performance rating) tying that with aggregation leading to either exfiltration or impact.
Describing some of the building blocks of insider threat models:
- Inherent risk – Any of the personal risk indicators mentioned
- Collection – Aggregation of data over network sources (firewalls), content management systems, storage objects (buckets, databases), etc.
- Exfiltration – All channels of egress including email, network, cloud content management systems, removable media, etc.
- Sabotage – Any document repository or storage with file / object deletions being audited
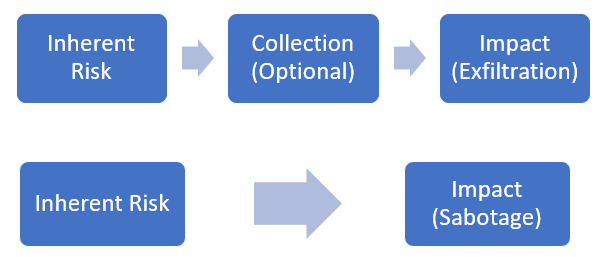
Insider Threat – Sample Threat Models
In the cloud specifically, insiders are not only limited to our own organization, but insiders in the cloud now also include cloud service provider and the entire supply chain an organization is leveraging. This includes third party APIs, where organizations usually lack visibility.
Referencing the risk that insiders pose from the previous article, we can see that insider threats can lead to an account compromise (either due to phishing or insufficient IAM) which in turn can lead to a lapse control.
Below is an example of a case study where a user exhibited flight risk behavior and created a backdoor account to access sensitive corporate documents post termination.
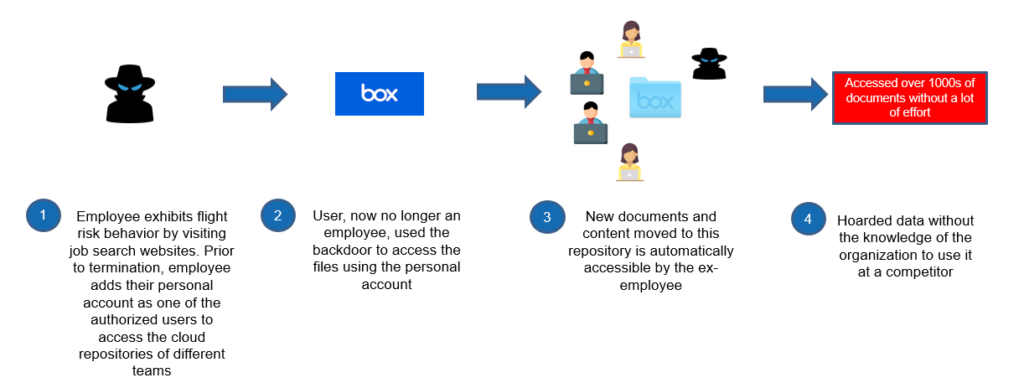
Real World Case Study – Malicious insider creates a backdoor access by abusing collaborative privileges
In the next and final part of the series we will go over what types of control issues or misconfigurations that insiders and other malicious entities can exploit leading to an impact in the form of data breach, data loss, or a misuse of cloud services.







