- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs
Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
Introduction
As malware authors continue to fine tune and re-tool their TTPs to avoid detection, finding unique and sometimes obscure methods for running malicious code can become a challenge. Unusual or even strange execution methods can confuse detection engines, thus increasing the malware’s chance of success of infecting the target system.
Today, we’ll be focusing on a rather interesting technique seen by the recent version of the QakBot, aka Qbot, malware where calls to the Windows binary Regsvr32 are obfuscated in creative ways. Sometimes, the binary is even stolen from its home in C:\Windows\System32.
QakBot is classified as an information stealer, or sometimes a loader malware, which is responsible for the initial infection phase of a target system. The first signs of QakBot appeared back in 2007 and it has evolved constantly in an attempt to stay ahead of modern EDRs and antivirus software.
Infection overview
Like most modern malware today, QakBot’s initial compromise method is pretty typical. A phishing email is sent to the target address with a URL in the message body which links to a remote password protected zip file. The password to the file is typically included in the body of the email which attempts to lure the victim into downloading, extracting, and eventually running its contents.
The zip file contains an image disk file (typically an .iso file) which is revealed after downloading and extracting its contents. Code execution begins when the user clicks the .LNK file contained inside the .iso file once mounted. .LNK file execution is becoming more popular as a method of code execution, which likely grew in popularity after Microsoft announced that VBS macros would be disabled by default for MS Office applications.
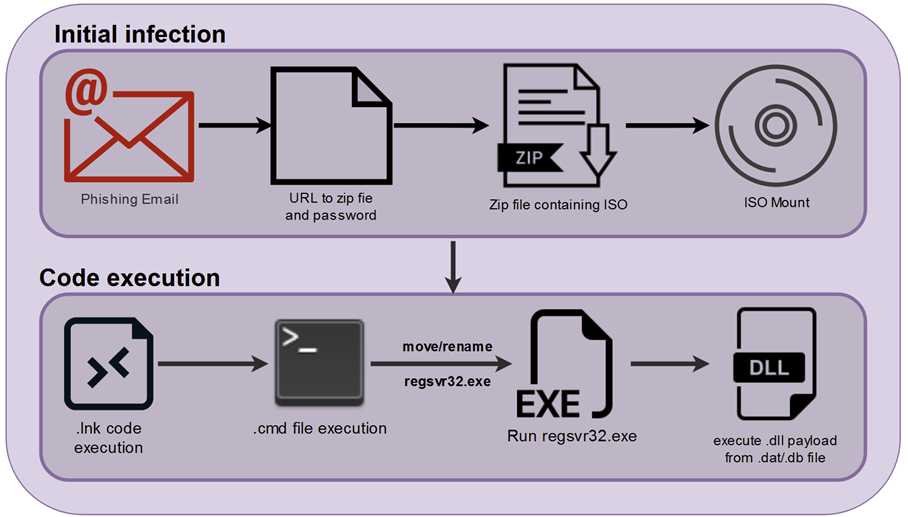
Figure 1: QakBot initial infection graphic
Regsvr32? Or is it?
Once the .LNK file is executed by the user, for the case of QakBot, this is where things take a turn and become much more interesting. At this point we have code execution, executed by the STRING_DATA portion of the shortcut file. We see cmd.exe executed with interesting command line parameters, in our case, the execution of an included .cmd file contained in the ISO file along with the shortcut file.
QakBot’s goal at this point is to execute another file contained in the ISO which is a disguised .DLL file. The DLL file will typically have a renamed file extension. For example, a few samples we analyzed contained DLL files with .dat, .scr, or .jpg extensions.
However, rather than executing the DLL using conventional methods, the QakBot loader takes a rather interesting approach to execute the DLL payload. The .cmd file, or batch file contains a few instructions which execute regsvr32.exe in some rather interesting ways.
The methodology varied from sample to sample. In some cases, portions of the “regsvr32.exe” binary name are stored as variables and called randomly towards the end of the script. We also observed, portions of the binary name being fed in as parameters when executing the .cmd file.
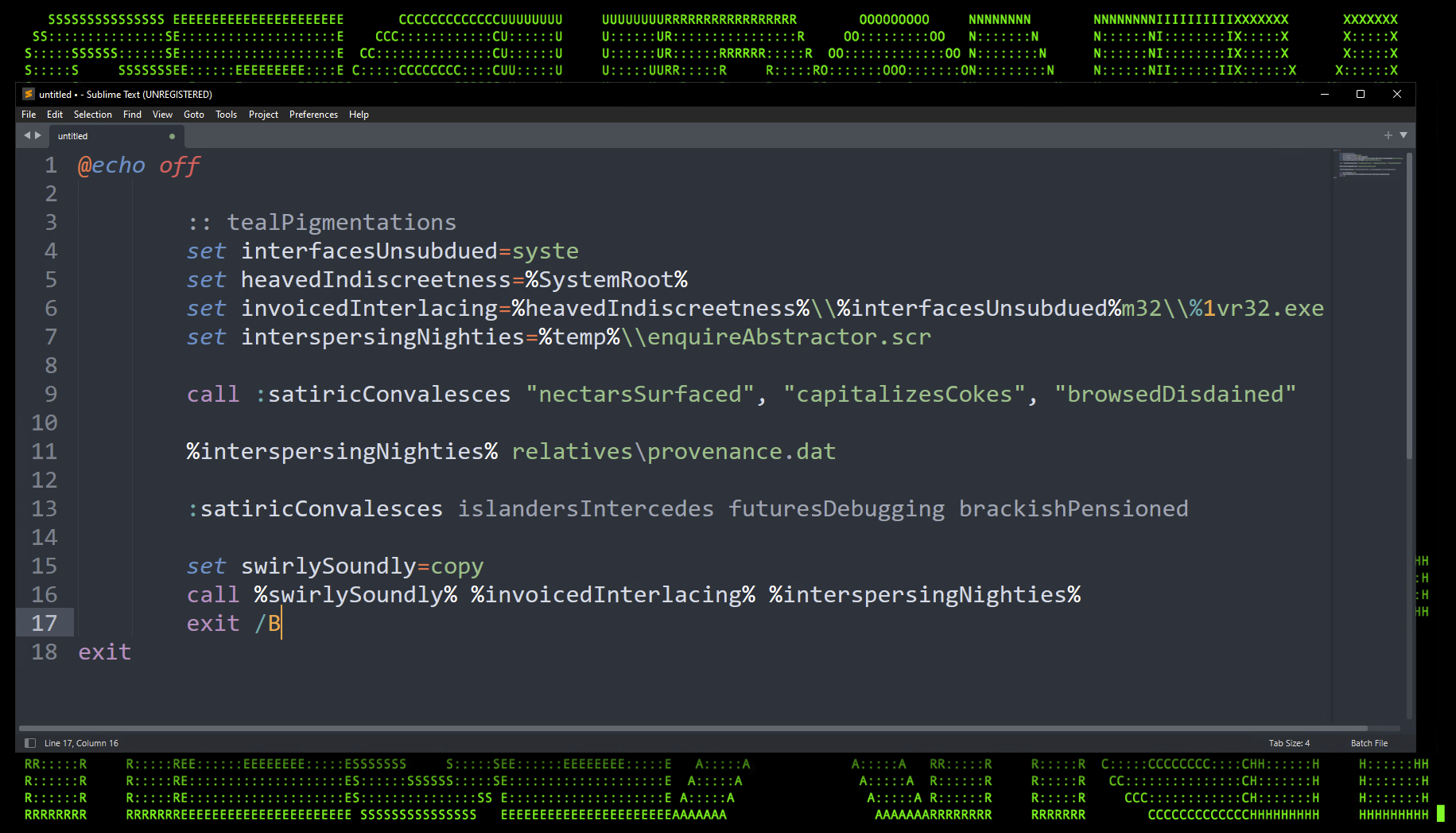
Figure 2: .cmd file: obfuscated regsvr32.exe execution
In the example above we can see that our goal is to get regsvr32.exe to run provenance.dat, our target DLL with the QakBot malware. In the end, the final executed code will be:
regsvr32 relatives\provenance.dat
But how did we get to that point? The batch file is doing a few interesting things: First, the path is being broken into several parts. The variable “interfasesUnsubdued” contains “system” which is parsed into the “%systemRoot%/System32/ path.
Regsvr32 appears as “%1vr32.exe”. In batch script, we can use the % sign plus a digit to pass in command line parameters. In this case, %1 would be the first passed parameter. So in order for this script to be executed properly, the .cmd file would need to be executed with “regs” as a parameter. For this particular situation we observed the following command:
C:\Windows\System32\cmd.exe /c relatives\membered.cmd regs
Regsvr32? Not anymore…
In another sample of QakBot, we observed a bit less obfuscation, and a bit more… theft. This particular use case hides its execution by completely copying the regsvr32.exe binary from out of the C:\Windows\System32\ directory, and placing it into the defined %tmp% directory:
C:\Users\username\AppData\Local\Temp
In one particular sample, as regsvr32.exe was copied from System32 to %tmp%, it was also renamed to “in.exe”. In the end, it produced a rather strange log that was quite well obfuscated, especially against detections that are looking specifically for ‘regsvr32’ execution.
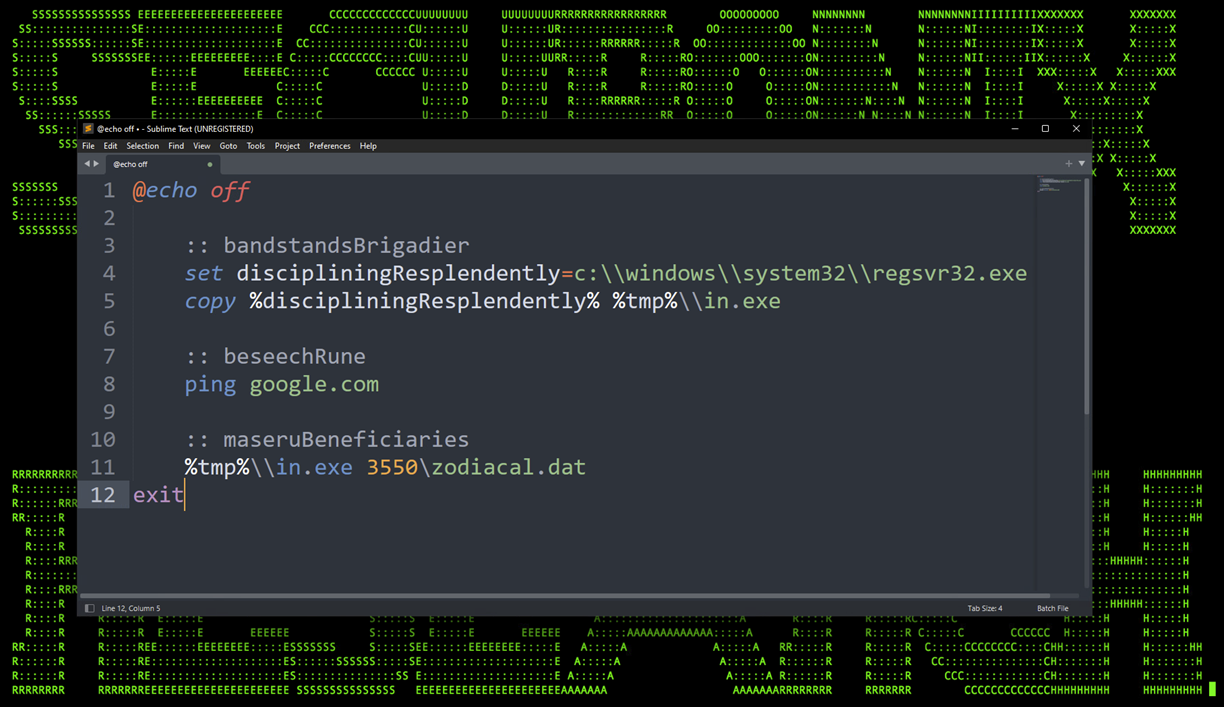
Figure 3: Moving and renaming regsvr32.exe prior to execution.
Between these two methods of obfuscating regsvr32.exe execution, we observed many samples and variations which follow most of these methodologies.
Pulling back the curtain
Let’s take a look at some Sysmon logs from another sample. This particular sample would heist regsvr32.exe from the System32 directory as we saw in a previous example. The file would be once again moved to the user’s %tmp% directory and renamed to “enquireAbstractor.scr”.
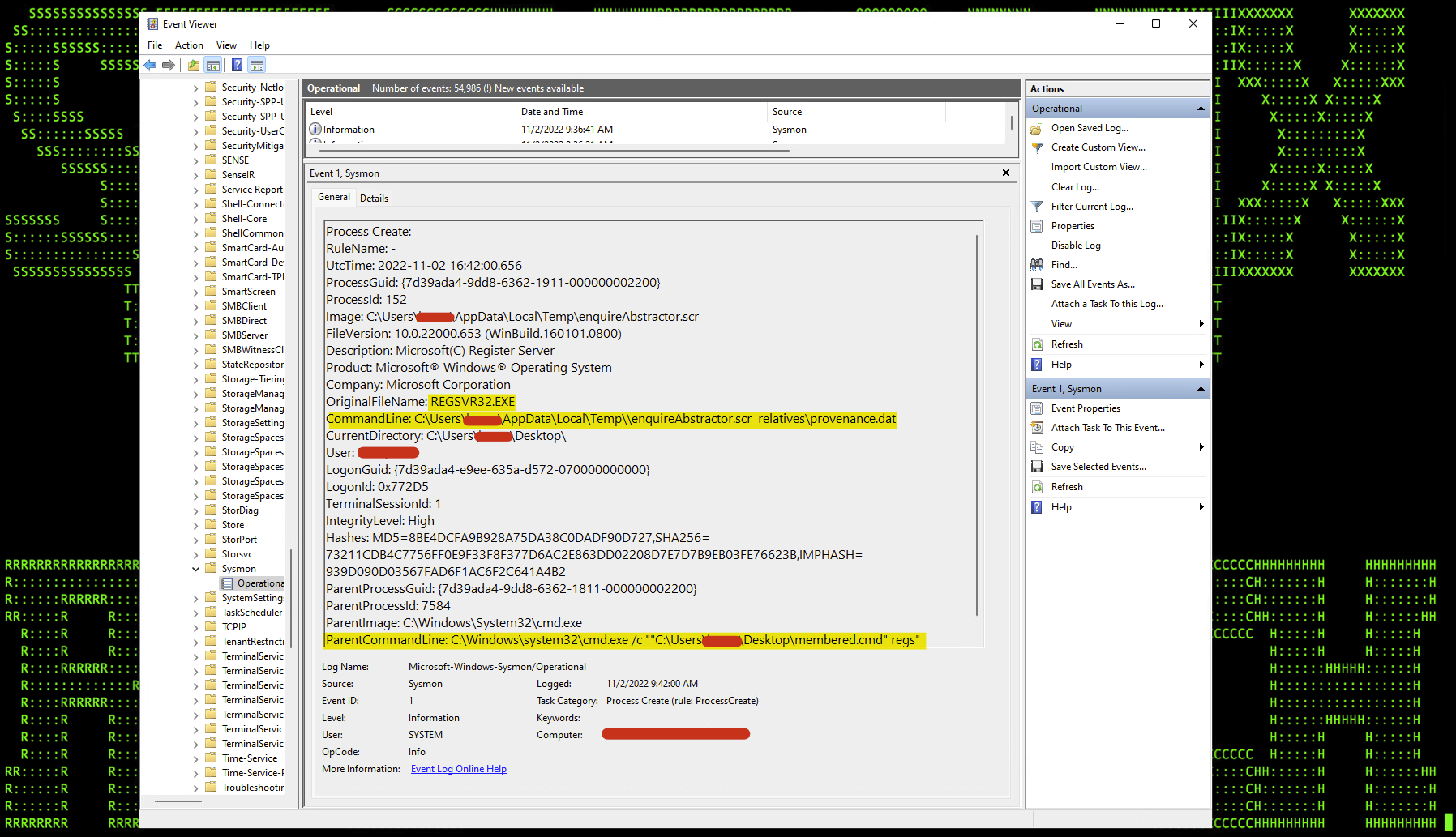
Figure 4: QakBot Sysmon logs
As seen in the figure above, regsvr32.exe (enquireAbstractor.scr) is executed by “membered.cmd” file which executes the QakBot malware’s DLL payload “provenance.dat”.
There are a few good detections here! First, since regsvr32.exe was simply renamed, we can look for Event ID 1 (process start) in Sysinternals: Sysmon logs where the OriginalFileName field is “REGSVR32.EXE” and the Image is NOT “regsvr32.exe”.
Another interesting detection is looking for regsvr32.exe execution where the image path is not “C:\Windows\System32\. This can trigger a violation from either the image name field or the OriginalFileName field.
Conclusion
QakBot’s initial attack vector is another example of just how far threat actors and APT groups are willing to go to bypass AV or EDR detection engines. Obfuscating regsvr32.exe calls, or moving binaries around would certainly skirt some detections. If anything, this particular use case is yet another reminder and use case advocating for a solid defense-in-depth strategy when it comes to detecting some of these more “unusual” TTPs.
Some examples of relevant Spotter queries
Suspicious Moved and Renamed Regsvr32 Execution
(rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”)) AND filename = “REGSVR32.EXE” AND ((customstring54 NOT CONTAINS “Windows\System32” OR customstring54 NOT CONTAINS “Windows\SysWOW64”) OR destinationprocessname != “regsvr32.exe”)
Possible Qbot Malware Regsvr32 to Explorer Process
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND sourceprocessname = “regsvr32.exe” AND destinationprocessname = “explorer.exe”
Some examples of relevant Securonix detection policies
- EDR-ALL-1159-RU
- EDR-ALL-1002-RU
MITRE ATT&CK
| Tactic | Technique |
| Defense Evasion | T1218: System Binary Proxy Execution: Regsvr32 T1036: Masquerading T1036: Masquerading: Rename System Utilities |
| Execution | T1059.003: Command and Scripting Interpreter: Windows Command Shell |
Analyzed file hashes
| SHA256 |
| be10d1f0565240319903cbbe2590d898721fbdd8ce2062e790185fbfd16486d2 |
| 37aff6406e6a0d5caccec17202737e4b0610d19560a6c791aad95385cb1581fb |
| ecef9075c8075eaf9163fa5ee12ccf6d72f1c241c6ca9c87f545925b2aea4f24 |
| 99b785c4820157cab314a0a46e00aad5daf0c4af21975ea1d2fe4e59972139ce |
| cbaf9a050e9ac61aa48a68284458dc296256b857c05c7f436329df8d2605bcc5 |
| 512c7d9380272efe0fdcb1735b22ef03b502924f495f5e075fe548c79bb3d44b |
References
- Microsoft: A closer look at Qakbot’s latest building blocks
https://www.microsoft.com/en-us/security/blog/2021/12/09/a-closer-look-at-qakbots-latest-building-blocks-and-how-to-knock-them-down/ - Intezer: How LNK Files Are Abused by Threat Actors
https://www.intezer.com/blog/malware-analysis/how-threat-actors-abuse-lnk-files/ - Microsoft: Macros from the internet will be blocked by default in Office
https://learn.microsoft.com/en-gb/DeployOffice/security/internet-macros-blocked - Microsoft: Sysmon – Download
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon







