- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs, Threat Research: Den Iuzvyk, Tim Peck
May 31, 2022

Introduction
A new RCE 0-day exploit in Microsoft Office products has been recently discovered and is currently being exploited in the wild. Dubbed “follina” the initial detection was identified by Twitter user @nao_sec who identified a malicious Office document coming out of Belarus.
The attack is carried out via phishing or spear phishing campaigns. What makes this particular exploit interesting is that compared to traditional attack vectors involving MS Office products, macros do not need to be enabled, or even leveraged for remote code to be executed.
The exploit works by taking advantage of how OLE objects are embedded and called within the document code in relation to how errors are handled with MSDT (Microsoft Support Diagnostic Tool).
Exploit Overview
A typical attack would most likely be carried out by a malicious threat actor targeting an organization via phishing emails. These emails would contain a carefully crafted .docx file for example. Next, once the document is opened, the exploit code would run regardless of whether or not the document was in protection, or read-only mode, making this exploit particularly dangerous.
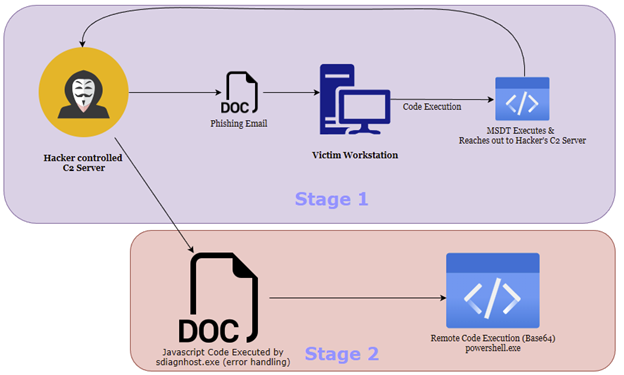
(Figure 1)
The exploit works by leveraging a few small code changes inside the document which reference how embedded OLE objects are contained in the document. In a nutshell, Microsoft Office files are considered compound container files. Inside these files, the two that we’re interested in are document.xml and word/document.xml.refs. The reference code to an OLE object can be modified to connect to a remote HTML file on a remote server as seen in Figure 2 below.
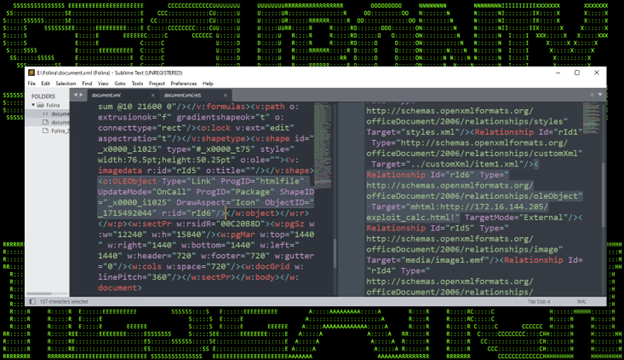
(Figure 2)
The next piece of the puzzle is to carefully craft the “exploit.html” file the aforementioned OLE object will call when MSDT is triggered.
MSDT (Microsoft Support Diagnostic Tool) is a support tool from Microsoft which uses the ms-msdt protocol. This protocol is used for troubleshooting basic Windows errors and can pass strings to the msdt.exe program to execute. This isn’t the first time we’ve seen this service being exploited, however.
At this point, any code could be executed by the attacker ranging from a simple process call, to base64 encoded payloads.
The exploit code is simple, the embedded JavaScript uses a special flag [ms-msdt] which sets the stage for how MSDT will process the error. An example of this HTML file can be found in Figure 3 below:
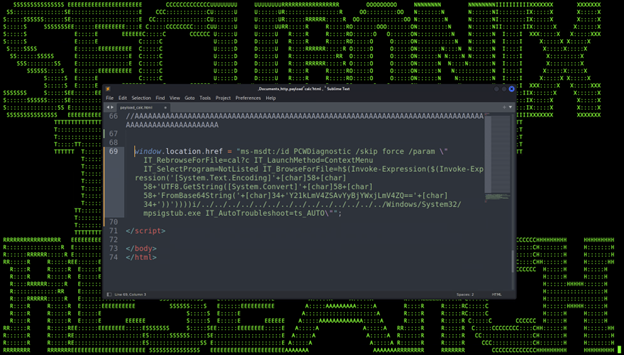
(Figure 3)
When the document file is opened by the victim, since it was originally modified by the attacker, MSDT will run and execute the malicious code in the remote HTML file. Since this file is under the control of the attacker, it is up to the attacker’s imagination as to what will execute. From what we’ve seen in the wild, the most likely scenario would be base64 encoded PowerShell. The PowerShell could really run anything ranging from opening up a backdoor to downloading and running malware.
Detection – Analysis
When the malicious document is executed, we notice some interesting process activity coming from Sysmon logs. Some of this activity can be used for building out reliable detections. The first is Microsoft Word (winword.exe) executing MSDT as a child process (msdt.exe). When command line logging is enabled, we can see the entire command string that would have been present in the attacker’s remote HTML file passed from ms-msdt as seen in figure 4.
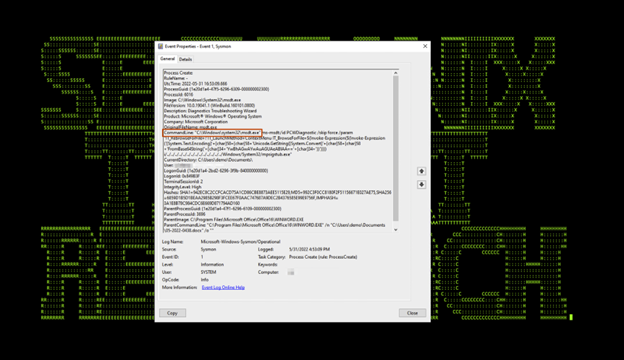
(Figure 4)
The next unusual pattern we identified was the Microsoft Scripted Diagnostic Native Host process (sdiagnhost.exe) executing the attackers intended process as seen in Figure 5.
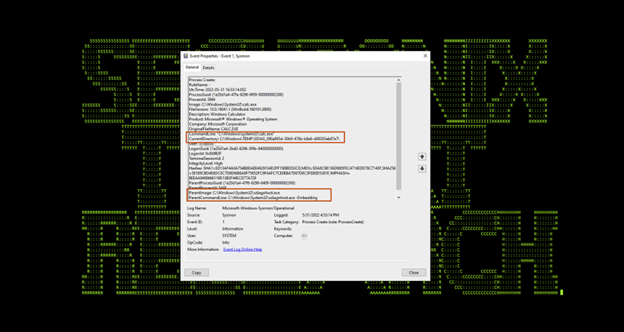
(Figure 5)
Conclusion
As of today, Microsoft has officially acknowledged the exploit and has provided mitigation steps to prevent this particular CVE from executing.
The scope of the exploit is very broad and impacts current versions of MS Office products. In addition to this exploit being used in the wild, automation tools which can generate both payload and document without too much effort have already been spotted on GitHub.
We recommend scanning your environments to check for signs of past compromise. Until Microsoft has a patch available, we recommend implementing Microsoft’s official mitigation strategies.
Securonix Recommendations and Mitigation
- Avoid downloading unknown email attachments from unknown sources
- Follow Microsoft’s recommendation guidance for CVE-20922-30190:
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename“
- Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
- Scan endpoints using the Securonix Seeder Hunting Queries below
- Prevent Office products from spawning child processes using MS Defender ASL:
- Set-MpPreference -AttackSurfaceReductionRules_Ids d4f940ab-401b-4efc-aadc-ad5f3c50688a -AttackSurfaceReductionRules_Actions Enabled
Hunting Queries
Title: Rare process spawned by Microsoft Office
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND (sourceprocessname ENDS WITH “Excel.exe” OR sourceprocessname ENDS WITH “Excelcnv.exe” OR sourceprocessname ENDS WITH “Msaccess.exe” OR sourceprocessname ENDS WITH “Mspub.exe” OR sourceprocessname ENDS WITH “Onenote.exe” OR sourceprocessname ENDS WITH “Onenotem.exe” OR sourceprocessname ENDS WITH “Outlook.exe” OR sourceprocessname ENDS WITH “Powerpnt.exe” OR sourceprocessname ENDS WITH “Visio.exe” OR sourceprocessname ENDS WITH “Winword.exe”) | rare destinationprocessname
Title: Rare Process Spawned From Scripted Diagnostics Native Host Folder Analytic
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND (filepath CONTAINS “SDIAG_” AND sourceprocessname ENDS WITH “sdiagnhost.exe”) AND (destinationprocessname NOT ENDS WITH “csc.exe” OR destinationprocessname NOT ENDS WITH “cvtres.exe” OR destinationprocessname NOT ENDS WITH “conhost.exe”) | rare destinationprocessname
Title: ms-msdt malicious CommandLine
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname ENDS WITH “msdt.exe” AND resourcecustomfield1 CONTAINS “ms-msdt:/id” AND resourcecustomfield1 CONTAINS “IT_BrowseForFile”
Title: Rare process spawned by sdiagnhost.exe
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND sourceprocessname ENDS WITH “sdiagnhost.exe” | rare destinationprocessname
Title: Microsoft Office Directory Traversal
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND (sourceprocessname ENDS WITH “winword.exe” OR sourceprocessname ENDS WITH “excel.exe” OR sourceprocessname ENDS WITH “outlook.exe”) AND (resourcecustomfield1 CONTAINS “..//..//..//” OR resourcecustomfield1 CONTAINS “..\\..\\..\\” OR resourcecustomfield1 CONTAINS “../\../\../\” OR resourcecustomfield1 CONTAINS “../../../”)
Title: ms-msdt malicious CommandLine – Microsoft Windows eventid 4688
index = activity AND rg_functionality = “Microsoft Windows” AND baseeventid = 4688 AND destinationprocessname = “msdt” AND resourcecustomfield1 CONTAINS “IT_BrowseForFile”
Title: msdt.exe spawned by Microsoft Office – Microsoft Windows eventid 4688
index= activity AND rg_functionality = “Microsoft Windows” AND baseeventid = 4688 AND (destinationprocessname = “msdt” OR resourcecustomfield1 CONTAINS “msdt.exe”) AND ( sourceprocessname = “winword” OR sourceprocessname = “excel” OR sourceprocessname = “outlook” )
Title: msdt.exe spawned by Microsoft Office – Endpoint Management Systems
index=activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND (customstring59 ENDS WITH “winword.exe” OR customstring59 ENDS WITH “excel.exe” OR customstring59 ENDS WITH “outlook.exe”) AND (customstring54 ENDS WITH “msdt.exe” OR resourcecustomfield1 CONTAINS “msdt.exe”)
Securonix Policies:
- Possible Phishing document – Rare process spawned from Office Applications
- Microsoft Office ms-msdt code execution vulnerability CVE-2022-30190
- Rare Process Spawned From Scripted Diagnostics Native Host Folder Analytic
- Potential Office Applications Path Traversal Exploitation Attempt Analytic
Note: If you are an Autonomous Threat Sweeper subscriber, all of the above TTPs have been swept and a summary detection report will be shared with the recipients.
For the latest threat intelligence and updates please refer to our Github page that is updated daily. We also invite you to send your questions regarding critical security advisories to the Securonix Critical Intelligence Advisory team and look forward to being of assistance.
References
- [1] https://twitter.com/nao_sec/status/1530196847679401984
- [2] https://github.com/JMousqueton/PoC-CVE-2022-30190
- [3] https://github.com/chvancooten/follina.py
- [4] https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
- [5] https://benjamin-altpeter.de/shell-openexternal-dangers/
- [6] https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide
Updated: June 7, 2022







