- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
High costs are a frequent point of contention when discussing long term storage with SIEMs. Many CISOs have suffered with a SIEM bill that keeps growing as their organization expands their technology footprint and produces more security telemetry to analyze and store. It seems to be an equation that makes SIEM unviable: To detect more, you need more data; more data means more money. But it doesn’t have to be like that.
First, we’ve been learning over the years about being smarter when ingesting data on SIEM. Gone are the days where deploying a SIEM was essentially “collect everything, then figure out what to do”. Best practices indicate that you should not start collecting everything. You must define what you need to accomplish first, then figure out what is the data required to get there. This simple change in the approach can save a SIEM deployment from failure and help with better time to value. It also helps with the cost challenge because you avoid collecting data you don’t need, saving money.
Unfortunately, best deployment practices are not enough to keep SIEM costs under control. Some organizations are subject to very strict data retention regulatory requirements, so they are forced to collect and store a lot of data. Take, for example, the recently published memorandum on “Improving the Federal Government’s Investigative and Remediation Capabilities Related to Cybersecurity Incidents” by the U.S. Office of Management and Budget (OMB). The memo details security event management requirements for federal agencies. Although it outlines a maturity model for organizations to follow, in the end it still requires them to deploy retention periods of 30 months for logs from a series of systems and event classes.
We have seen that requirements like these would often drive the implementation of logging infrastructures where “logs go to die”: Cheap and inefficient storage systems with no practical use apart from putting a checkmark on a checklist. But regulators have apparently learned their lesson. The same OMB memo, for example, does not mandate only for logs to be retained, but it also requires organizations to implement security monitoring capabilities that actually use the collected data, such as behavior analytics capabilities to detect user account compromise. What should an organization subject to these types of regulatory requirements do?
An Architecture That Brings Analytics to Data
The answer requires new architectures and deployment models. Security analytics solutions capable of delivering the monitoring use cases required can only achieve the required scale in the cloud. The cloud SIEM, which was already becoming the standard deployment model because of the general trend of moving workloads to the cloud, is now the only practical solution to deal with the volume of data to be collected. But cloud doesn’t always mean cheaper. And that is where the “Bring Your Own Snowflake” deployment model comes in. How to provide a SIEM with the scalability and elasticity of the cloud while storing huge amounts of data in a cost-effective manner.
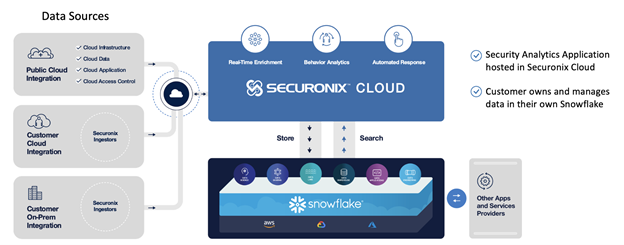
Since we released BYOS we’ve been working with many organizations looking for ways to keep their SIEM costs under control. In some of those cases we were able to provide this solution with a price 50% smaller than one of the most visible SIEMs in the market. And that’s while providing additional capabilities when compared to that competitor, such as our cloud based best of breed analytics.
Snowflake provides multiple advantages to organizations with high volumes of data. Cost savings are achieved with a smart architecture that separates processing from storage costs. This allows organizations to put more money on data queries that require faster results, while keeping the less sensitive ones running in more cost-efficient computing instances. You also don’t pay for processing when not running any queries. This makes the pricing even more efficient.
Eliminate Storage Tiers – No Warm/Cold/Frozen Storage
One thing CISOs do not want to worry about when regulators or law enforcement comes knocking and asking for data is if restoring that cold archive will in fact work as expected. And even if it works, restoring, or “rehydrating” the data may take a very long time. During critical investigations, having to wait for hours to have the data reloaded so it can be searched is something that you really don’t want to go through. With BYOS, the data in Snowflake is always available, searchable. You do not have to worry about moving data to cold, frozen or archive layers.
More Than Just a Cheap Place to Store Data
At the early stages of the big data revolution, many organizations saw Hadoop as the ideal technology to create cheap security data lakes. But most of those experiences did not produce the expected results: Adding data to Hadoop may be easy but storing data in a way that is useful for security investigations and threat hunting is not simple. Securonix provides the collection, enrichment and formatting capabilities that allow data stored in Snowflake to be valuable to those use cases, simplifying one of the most challenging aspects of implementing a security data lake. You can learn more about it on this recent webinar we did together with Snowflake.
Cost Efficiency With Securonix’s Split Pricing Model
Securonix recognizes that when customers are bringing data into long-term storage, not all of that data is relevant for analytics. Securonix has created a usage-based pricing model that enables customers to differentiate the data going to SIEM vs. long-term storage, improving cost efficiency by over 70%.
| Functionality | Savings Compared to SIEM | Approx. Cost Savings @ 100,000 EPS |
| All Data to SIEM | 0% | $0.00 |
| 50% Data for Search Only | 37% | $1.1M |
| 75% Data for Search Only | 55% | $1.65M |
| 100% Data for Search Only | 73% | $2.2M |
Utilize Existing Snowflake Credits?
Another important factor for organizations considering BYOS is the ability to incorporate their security data into their overall planning for a data cloud. To achieve the best cost they will often pay for usage up front, so it’s common to find organizations with unused Snowflake credits available. These credits can offset the cost to store and use the security data ingested, making it even cheaper. In a scenario like this, your SIEM can help you maximize the resources available and achieve an economy of scale for your data needs that are just not possible when your security data is kept in a separate silo, charged separately from your other data.







