- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs, Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
April 7, 2023
tl;dr: Last week the popular VoIP desktop software 3CX was compromised due to a sophisticated supply chain attack which delivered malicious updates to potentially millions of devices. Now that the dust has settled a little, let’s take a look at some of the lessons learned and how we can monitor for malicious activity.

The 3CX attack is considered a supply chain attack because the software itself was not vulnerable to exploitation, or associated with any known CVE vulnerabilities. The attack was carried out by threat actors who compromised the 3CX update delivery system. This in turn, delivered malicious updates to the 3CX desktop application.
Crowdstrike initially discovered the attack on March 29th as they observed the 3CX desktop application (3CXDesktopApp.exe) behaving unexpectedly by following typical malware IoCs (iIndicators of cCompromise).
3CX acknowledged the attack the same day and has since released a post highlighting affected versions which are 18.12.407 and 18.12.416 on Windows and 18.11.1213, 18.12.402, 18.12.407 and 18.12.416 on MacOS.
Impact
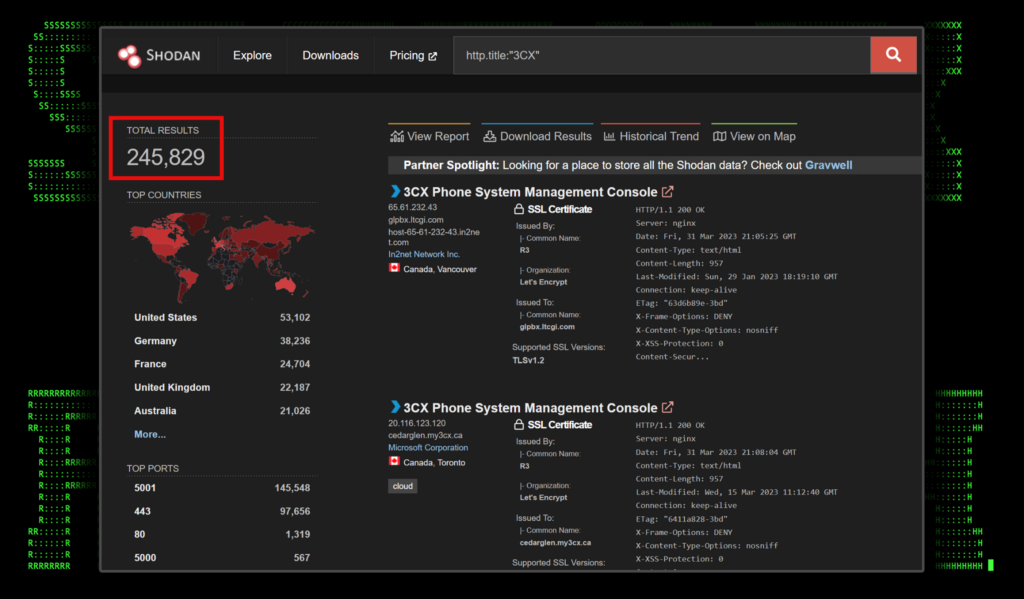
The 3CX VoIP system is hugely popular and used by hundreds of thousands of customers world-wide, includingand used by some large well- known organizations. A supply chain attack at this size has the potential for being one of the worst since the Solar Windows attack in 2020. At the time of writing, there are approximately 245,000 3CX management systems exposed to the internet according to Shodan.
Affected organizations today will need to remain extra vigilant as some malware can take time to manifest. Threat researchers at Huntress reported a 7-day time delay between time of infection, and when beaconing activity begins.
Detecting the current and potential future variants of the 3CX Smooth Operator attack
There are some relevant behaviors that we can leverage using the Securonix platform to assist in finding signs of compromise. First and foremost any deviation outside the norm from the 3CX desktop application behavior should be considered abnormal and warrant further investigation.
The Securonix Threat Research team has put together a few detection policies that Securonix customers can use to monitor for abnormal deviations in the desktop application’s behavior. Some examples of these include detections for abnormal process and DNS activity (see: Relevant Securonix detections below.)
As information surrounding the threat continues to come to light, these detections are designed to stay relevant ahead of new or changing data.
Vulnerable applications
Below is a list of vulnerable software installers affected that are currently affected by the Smooth Operator supply chain attack.
| File Name | OS | File hash (SHA256) |
|---|---|---|
| 3cxdesktopapp-18.12.407.msi | Windows | dde03348075512796241389dfea5560c20a3d2a2eac95c894e7bbed5e85a0acc |
| 3cxdesktopapp-18.12.416.msi | Windows | fad482ded2e25ce9e1dd3d3ecc3227af714bdfbbde04347dbc1b21d6a3670405 |
| 3CXDesktopApp-18.11.1213.dmg | macOS | 92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61
5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290 |
| 3cxdesktopapp-latest.dmg | macOS | B86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb
e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec |
Payload file details
There has been an ongoing effort to track malicious files downloaded and executed by the attackers once the initial infection phase has completed. Many of these come in the form of malicious .dll files masquerading as legitimate software.
| File Name | File hash (SHA256) |
|---|---|
| ffmpeg.dll | 7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896 |
| trololo.dll | aa4e398b3bd8645016d8090ffc77d15f926a8e69258642191deb4e68688ff973 |
| d3dcompiler_47.dll | 11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03 |
C2 and infrastructure
Analysts at Crowdstrike observed the following domains have been contacted by compromised versions of the software and were associated with beaconing activity. Monitoring for strange domain and IP activity coming from the 3CXDesktopApp.exe process should be considered a high priority for affected organizations.
| C2 Domains | |
| akamaicontainer[.]com
akamaitechcloudservices[.]com azuredeploystore[.]com azureonlinecloud[.]com azureonlinestorage[.]com dunamistrd[.]com glcloudservice[.]com journalide[.]org msedgepackageinfo[.]com msstorageazure[.]com msstorageboxes[.]com officeaddons[.]com officestoragebox[.]com pbxcloudeservices[.]com pbxphonenetwork[.]com pbxsources[.]com qwepoi123098[.]com sbmsa[.]wiki sourceslabs[.]com visualstudiofactory[.]com zacharryblogs[.]com |
Surviving the next supply chain attack
Any major supply chain attack such as this requires a massive amount of work from the attacker to implement and carry out. In the case of 3CX, there are some indications that the malicious activity associated with the attack dated as far back as Fall 20227. Embedding malware into a legitimate application and then delivering it to victim machines through a trusted source can be difficult to detect. This is oftentimes why these kinds of attacks can go undetected for long periods of time.
Some attack patterns can be predictable, regardless of the level of trust we have in any given software. Securonix provides many non-vendor specific detections looking for malicious activity coming from processes performing tasks that they were not designed to do.
An example of this would be a legitimate VoIP software product changing its behavior exhibiting unusual process and filesystem activity (WEL-ACC63-RUN), network resources (WOW-EDR5-ERI), and other less-specific behaviors, which can potentially help increase the chances of detecting future variants of the supply chain attacks like 3CX.
Additionally, when a threat actor gains access to a target host, whether through a supply chain attack, or through another method such as a spearphishing attachment, a predictable pattern of behavior is typically followed. An attacker may choose to install a backdoor application such as a RAT (remote access trojan), deploy an infostealer such as Gopuram backdoor, or simply run discovery commands on the target.
Having good detections in place that are able to detect discovery or enumeration commands, or detect behaviors associated with common RAT software can be crucial to catching compromised machines early before further damage can be done.
At this stage of the attack it is important to identify post-exploitation activity and likely compromised machines. 3CX outlined some recommendations based on operating system that 3CX customers can leverage to help reduce the impact:
https://www.3cx.com/blog/news/desktopapp-security-alert-updates/
Some examples of relevant provisional Securonix detections to help identify the current and potentially future variants of the threat:
- EDR-ALL-1199-ERR
- EDR-ALL-1200-ERR
- WEL-ALL-1178-RU
- WEL-ALL-1177-RU
Some examples of relevant Spotter queries to help hunt for activity associated with the threat:
- (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Proxy”) AND (destinationhostname = “akamaicontainer.com” OR destinationhostname = “akamaitechcloudservices.com” OR destinationaddress = “azuredeploystore.com” OR destinationhostname = “azureonlinecloud.com” OR destinationhostname = “azureonlinestorage.com” OR destinationhostname = “dunamistrd.com” OR destinationhostname = “glcloudservice.com” OR destinationhostname = “journalide.com” OR destinationhostname = “msedgepackageinfo.com” OR destinationhostname = “msstorageazure.com” OR destinationhostname = “officeaddons.com” OR destinationhostname = “officestoragebox.com” OR destinationhostname = “pbxcloudeservices.com” OR destinationhostname = “pbxphonenetwork.com” OR destinationhostname = “pbxsources.com” OR destinationhostname = “qwepoi123098.com” OR destinationhostname = “sbmsa.wiki” OR destinationhostname = “sourceslabs.com” OR destinationhostname = “visualstudiofactory.com” OR destinationhostname = “zacharryblogs.com”)
- (rg_functionality=”Endpoint Management Systems” OR rg_functionality=”Antivirus / Malware / EDR” OR rg_functionality=”Cloud Antivirus / Malware / EDR”) AND filehash NOT NULL AND filehash IN (“dde03348075512796241389dfea5560c20a3d2a2eac95c894e7bbed5e85a0acc”,”fad482ded2e25ce9e1dd3d3ecc3227af714bdfbbde04347dbc1b21d6a3670405″,”92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61″,”5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290″,”B86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb”,”e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec”,”7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896″,”aa4e398b3bd8645016d8090ffc77d15f926a8e69258642191deb4e68688ff973″,”11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03″)
References:
- Reddit:SITUATIONAL AWARENESS // CrowdStrike Tracking Active Intrusion Campaign Targeting 3CX Customers //
https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/ - 3CX DesktopApp Security Alert
https://www.3cx.com/blog/news/desktopapp-security-alert/ - 3CX Form: 3CX DesktopApp Security Alert
https://www.3cx.com/community/threads/3cx-desktopapp-security-alert.119951/ - 3CX VoIP Software Compromise & Supply Chain Threats
https://www.huntress.com/blog/3cx-voip-software-compromise-supply-chain-threats - Detecting SolarWinds/SUNBURST/ECLIPSER Supply Chain Attacks
https://www.securonix.com/blog/securonix-threat-research-detecting-solarwinds-sunburst-eclipser-supply-chain-attacks/ - Not just an infostealer: Gopuram backdoor deployed through 3CX supply chain attack
https://securelist.com/gopuram-backdoor-deployed-through-3cx-supply-chain-attack/109344/ - Initial Implants and Network Analysis Suggest the 3CX Supply Chain Operation Goes Back to Fall 2022 https://blogs.blackberry.com/en/2023/03/initial-implants-and-network-analysis-suggest-the-3cx-supply-chain-operation-goes-back-to-fall-2022