- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Cloud Security

Computing? Check.
Analytics? Check.
Artificial intelligence (AI)? Check.
Networking? Check.
Content delivery network? Check.
Storage? Check.
Load balancing? Check.
Third party applications? Check.
Robotics? Check.
Quantum computing? Check.
The array of capabilities that AWS offers today is mind-boggling. A self-sufficient, feature rich cloud environment, AWS makes it very easy to assemble technology infrastructure – be it AI/machine learning (ML) based analytics, multi-tier backup and storage, enterprise application farms, or even identity and access management (IAM) – in the public cloud.
AWS has a service for every use case and every workload. It is no surprise, then, that enterprises are relinquishing on-premises hardware for public cloud services, truly embracing cloud computing.
But there’s a catch.
Preferred Computing Model = Preferred Attack Target!
In the heyday of desktop computers, Windows was the dominant operating system. Naturally, it became the target of choice for hackers. The majority of users were using Windows, so it made sense to create attacks and use malicious tools that targeted Windows systems.
The top cloud vendors today face the same threat –targeted due to their popularity. As the most popular public cloud service, AWS is a prime attack target. With its own infrastructure, architecture, and operating model, AWS presents a unique security environment and a unique set of threats that traditional on-premises security information and event management (SIEM) platforms are unable to protect effectively.
Cloud-native, scalable, and AWS recognized –Securonix provides a mature, robust protection solution for AWS workloads.
Here is a list of the top 10 AWS threats that we’ve observed, along with how to detect and protect against them.
1: The Metadata Attack
The AWS metadata service is used to supply temporary credentials for applications requiring access to AWS resources, as well as to store user data to be used when launching applications.
This service, however, can be attacked when developers put sensitive information into user startup scripts. These scripts allow EC2 instances to be started with certain configurations – and some of those configurations may include usernames and passwords used to access various services. As the metadata service doesn’t need any parameters, fetching the metadata URL will provide the access key ID, secret access key, and token needed to authenticate into the account. In some instances, this can even grant root access to an attacker.
A successful metadata attack can give an attacker partial or, if the account has root privileges, complete access and control over the AWS account.
Securonix helps detect and prevent this attack through the CloudWatch agents (which provide OS level logs from EC2 instances) and CloudTrail logs (which provide the ability to monitor for unusual activities committed by a compromised account).
2. Amazon EC2 User Data Modification Attack
Attackers can modify Amazon EC2s user data (used to perform one-time automated configuration or run scripts on instance startup – but also possibly to run scripts on every restart) to establish persistence on an EC2 instance. Any script passed as part of user data is executed with root permissions.
This attack not only allows root privilege access and privilege escalation, but can also allow attackers to spin up high-privilege instances of their own, which, if unobserved, can open the floodgates for a massive attack.
Securonix helps detect and prevent this attack by integrating CloudWatch logs (OS level logging by the CloudWatch agent can help identify access to user data) and CloudTrail logs (modifications and access to user data can be identified in CloudTrail logs).
3. Crypto Mining
Once attackers gain access (possibly using one of the attacks described earlier), they can start up a large number of expensive (GPU based) EC2 instances or use CPU cycles on existing instances for crypto mining operations.
Crypto mining is a very compute-intensive process. The attacker’s usage can result in massive compute billing expenses in a very short time.
Securonix helps detect and prevent this attack by integrating CloudWatch logs (to monitor usage and performance on individual instances) and CloudTrail logs (to monitor EC2 instances launched by a user).
4. Open Public Access Bucket
AWS often stresses on the fact that security is a shared responsibility. That, unless customers secure their environment, even the best security they can provide will be insufficient. Sometimes, S3 storage buckets may be inadvertently made public by accident (or for data exfiltration or as part of a command and control (C&C) attack). This means that the data in these buckets is vulnerable to attack – and they have been targeted, often.
Confidential data leaks can be expensive, both through the monetary cost related to compensation for those affected or regulatory fines, as well as the brand value lost along with customer confidence. With data privacy regulations such as GDPR and CCPA becoming mainstream, the cost of a data breach can be prohibitive – even resulting in bankruptcy.
Securonix helps detect and prevent losses due to user negligence by integrating CloudTrail logs (to monitor activity on S3 buckets for public read/write permissions) and configuration logs (to detect changes in S3 access policy).
5. Misuse of Temporary Credentials After Disabling of Permanent Credentials
Even if you disabled the credentials of a compromised account the job isn’t done. Attackers using accounts with sufficient permissions can generate temporary credentials and keep them in reserve, using them to perform malicious activity even if the original credentials are disabled.
Temporary credentials can give attackers complete access to your AWS instance for several hours – and when permanent access is disabled, attackers will try to achieve maximum results in those hours. This could lead to massive breaches and data theft attempts that could overwhelm your security infrastructure.
Securonix highlights suspicious activities such as temporary account creation found in CloudTrail logs (which monitors IAM related activity for users and identifies suspicious behavior such as temporary credential creation).
6. Mismatch in User and Access Key Combination
Attackers can pair user accounts with access keys that are not usually used by the account to gain access. If both the user account and access key are valid, the attacker is granted access.
An attacker who has both user account information and access keys can perform several intrusions using different combinations of the two sets of credentials. This opens a huge number of attack opportunities.
Securonix helps detect and prevent losses by using CloudTrail logs to monitor user activities and compare user and access key usage with baseline parameters identified over time.
7. Detection Evasion
Once intrusion/persistence is achieved by an attacker, or after finishing their malicious activity, the attacker may try to avoid detection by modifying or disabling AWS CloudTrail/CloudWatch logging.
If undetected, this will allow the attacker to stay within the system for an indefinite period of time, as AWS logs will not show any compromise or malicious activity – nor will it be identified by any monitoring software.
Securonix detects such evasive tactics by monitoring CloudTrail logs for log modification or disable events triggered by a user.
8. AWS Infrastructure Scanning
Attackers conduct preliminary reconnaissance prior to an attack by scanning AWS VPCs, IAM users and roles, or S3 buckets. This allows them to find vulnerable assets such as poorly configured accounts, S3 data buckets open to public access (refer to number 4 above), or VPCs without proper firewalls.
Identifying vulnerable assets gives attackers a list of resources to infiltrate. Open S3 buckets, for example, would not even need the attacker to have credentials for access – allowing them to download data from the bucket without any authorization.
Securonix detects such reconnaissance attempts by monitoring VPC flow logs (monitoring scanning and enumeration activities) and CloudTrail logs (monitoring IAM scanning and enumeration activities).
9. Remote Code Execution
Once an attacker gains access to an EC2 instance, they can use the instance to run malicious processes and code or run malware and other exploits, as well as access restricted resources.
Once attackers gain a foothold within your AWS environment, they can unleash a wide range of attacks that they wouldn’t be able to from an external machine – such as malware attached to legitimate emails, C&C operations over ports that are inaccessible/blocked to external networks (such as SSH), and executing processes such as remote desktop protocol (RDP) to gain access to restricted resources such as application servers.
Securonix can detect and protect against remote code execution using information from three data sources:
- CloudWatch Logs: Operating system logs from the CloudWatch agent
- VPC Flow Logs: For monitoring external connections
- ALB/ELB Transactions: For monitoring external connections to ALB/ELB (load balancing services)
With this information, Securonix gains visibility into suspicious activity such as C&C activity on EC2 instance(s), including rare process execution, abnormal access to assets, and beaconing behavior (sending of short burst transmissions by an infected host to a C&C to communicate malware activation)
10. Privilege Escalation
Involves attackers looking to increase the privileges of compromised user accounts or gaining access to or creating user accounts with increased privileges or administrative access.
Attackers pose a lower threat when compromised accounts don’t have significant access rights. But if user management is badly configured, attackers may manage to increase their privileges, gaining access to more resources and increasing their potential for severe attack.
Securonix can detect and protect against privilege escalation using information from the CloudTrail logs, which allow for the monitoring of IAM related activity relevant to privilege escalation such as policy or role creation for users.
How Does Securonix Integrate With AWS To Enable Monitoring?
Securonix uses bi-directional integration with AWS components to provide end-to-end security monitoring, advanced threat detection, data retention, and automated incident response capabilities. In order to enable quick access to AWS-linked security events, Securonix has direct API integration with AWS, allowing Securonix to collect and analyze logs across various AWS products.
The Securonix platform integrates with multiple AWS security touchpoints, combining information and context in order to show you the security status of your AWS environment at a single glance. The Securonix platform integrates with:
- Amazon CloudTrail: Monitors API calls to the AWS platform from around 154 different services.
- Amazon CloudWatch: Performance monitoring, such as CPU and disk usage, as well as other log types.
- Amazon Simple Storage Service (S3): Log storage from multiple sources, such as CloudFront, web application firewall (WAF), Elastic Load Balancer (ELB), and CrowdStrike.
- Amazon GuardDuty: Monitoring and alert generation.
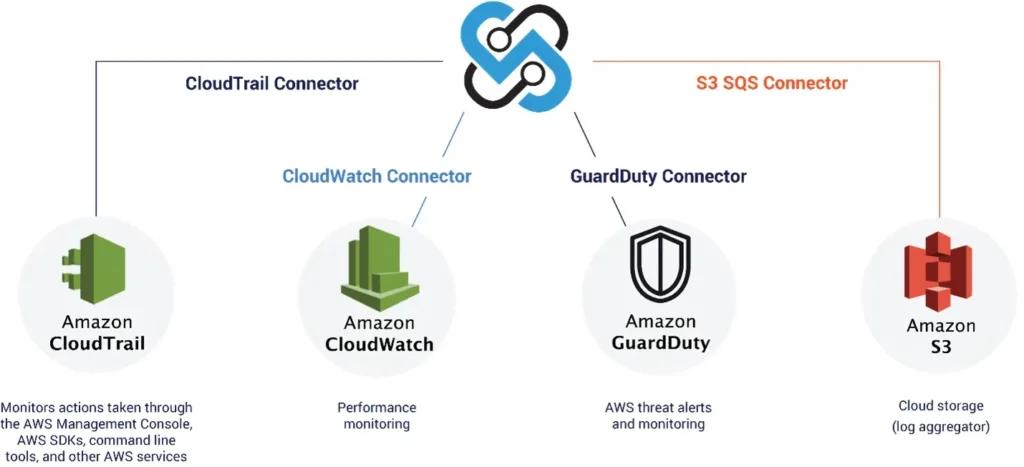
This information is processed by Securonix in order to identify tangible threats, including data compromise, unauthorized access attempts, suspicious traffic, and several others.
AWS CloudWatch Integration
AWS CloudWatch aggregates logs from multiple sources including Windows/Linux server instances, Amazon VPCs, Amazon Relational Database Service (RDS), and Amazon Elastic Kubernetes Service (EKS) for performance monitoring.
Securonix integrates with the Amazon CloudWatch connector, pulling performance information to correlate with events and identifying threats that may cause performance problems or resource misuse.
AWS CloudTrail Integration
AWS CloudTrail monitors actions taken within multiple AWS services by logging API calls from them. Securonix integrates with AWS CloudTrail in order to pull these logs for processing for context enrichment and security issue identification.
Amazon S3 Integration
Amazon S3 acts as a log aggregator, combining logs from various source such as ELB, Amazon CloudFront, CrowdStrike, and WAF (through Amazon Kinesis Firehose).
Securonix integrates with Amazon S3 and uses this logging information for both security monitoring and additional security context. Securonix is also able to write data back into Amazon S3, or retrieve it in real time through Amazon Athena, for searching and threat hunting.
AWS GuardDuty Integration
Securonix also integrates with GuardDuty, AWS’ internal threat detection service, to integrate threat events identified by AWS and add context to them. These threat alerts are also integrated into the larger Securonix event database to identify larger threats, of which the AWS threat may only be one part. With GuardDuty integration, Securonix can provide a more complete view of threats to the entire enterprise infrastructure – across on-premises, AWS, and hybrid systems.







