- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
Ransomware dominated cybersecurity news in 2021, as large-scale attacks plagued organizations both private and public. Perhaps the most widely publicized attack was on Colonial Pipeline, disrupting gas supplies from Texas to New Jersey and forcing the pipeline provider to pay a ransom of 75 bitcoin, which translated into about $4.4 million.
The good news is that while global cyberattacks rose in 2022, ransomware attacks were down about 8 % in the third quarter, compared with the same period in 2021, according to Check Point’s Cyber Attack Trends: 2022 Mid-Year Report. Sonicwall’s mid-year cyber threat report also reported that ransomware attacks were down 23% from January to June, though up significantly in Europe.
Ransomware is one of the topics covered in the Securonix 2022 Threat Report, which analyzes trends in cybersecurity threats and the SIEM-related tactics and techniques customer organizations use to protect their data. The report also adds valuable insight and advice, and real stories of techniques from the trenches that would be useful for any SIEM-enabled organization. This is our third blog installment on the report’s findings, in which we cover ransomware. The first two covered insider threats and cloud infrastructure.

Download the 2022 Securonix Threat Report
One of the points the report emphasizes is that all the categories it covers—insider attacks, cloud infrastructure, and ransomware—work together to challenge IT security. For example, the rise of the cloud is a key trend causing an increase in ransomware attacks, as organizations still struggle with cloud misconfigurations and inconsistent privileges in multiple cloud environments. Many are still trying to figure out how to balance cloud ease of use with the necessity for tight security. The lack of consistency leaves holes in cybersecurity protection that allow attackers to sneak in.
Catch ransomware early
The key with ransomware is to detect and mitigate an attack before it can encrypt and delete your data or make it inaccessible. To detect attacks early in the threat cycle, the report recommends robust endpoint telemetry captured in the SIEM, as without it the organization would have to rely solely on signatures and other detections their EDR or antivirus software provide.
Properly configured, a next-generation SIEM such as Securonix can correlate alerts from single sign-on systems, networks, and endpoints with individual entities (users or devices) and use the correlated information to prioritize the most important alert information and detect an attack in progress.
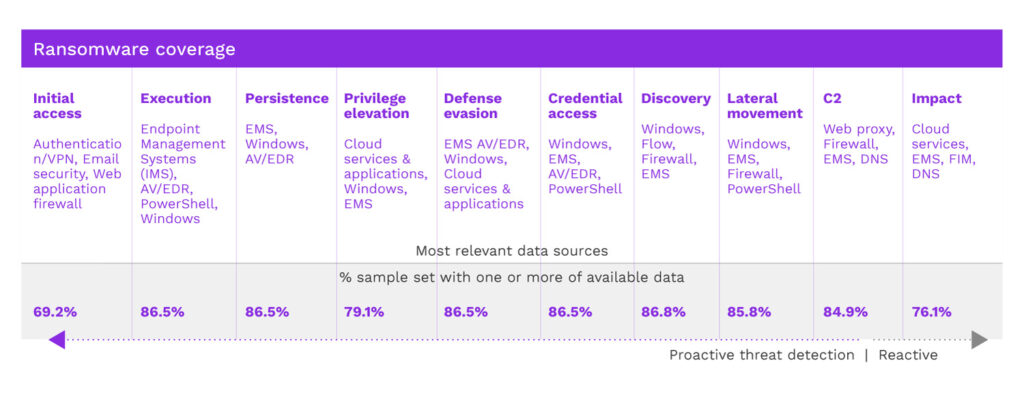
Compromised credentials and phishing are the primary techniques ransomware attackers use to penetrate most organizations. To detect ransomware early, a SIEM should ingest email security logs and look for indicators such as links with typo-squatted domains. The report found that only 40% of Securonix customers were doing this though two-thirds of respondents were ingesting cloud logs, which could be used to detect privilege escalation in the cloud.
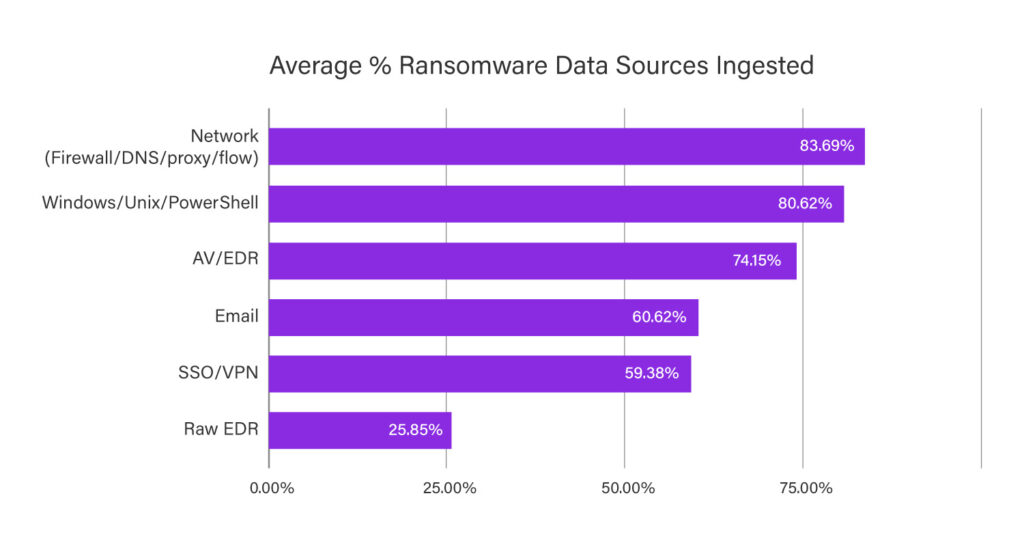
The report also shows that more than 70 percent of the ransomware tactics described in the MITRE ATT&CK framework can be detected by monitoring raw endpoint detection and response (EDR) data and network traffic analytics, yet only 25% of Securonix users were ingesting that data into the SIEM.
Put it all together
Monitoring single sign-on (SSO) systems and VPNs is critical for detecting attacks. In one case an organization discovered an account logging in from two geolocations simultaneously, including one from a new country—a dead giveaway of account sharing and compromise indicating an attack attempt. The perpetrator then requested an unusually high number of Kerberos service tickets, a sign of account misuse. Detecting both events helped an organization stop a large-scale ransomware attack.
In general, the top-four data sources customers were using their SIEMs to ingest were next generation firewall and Windows data, followed by cloud services and content management systems. All are valid for detecting early ransomware exploits, but customers would do better to add more EDR and email monitoring.
There’s a lot more information in the report that is very helpful for organizations combating ransomware, insider threats and cloud infrastructure misuse. Download your copy of the 2022 Securonix Threat Report.