- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Improved Detections | Faster Implementation
Securonix is focused on providing a suite of capabilities, including powerful analytics and incident response, to the security operations center (SOC) to aid in detecting and responding to advanced attacks. We continue to improve the value we provide with our cloud-native SIEM solution.
Our latest release, Jupiter, introduces new capabilities to enable faster detection of advanced threats and offer better time to value for our customers and partners. Let’s explore the most exciting features.
What’s inside?
Improved Detection of Advanced Threats
Content Manager
Content is one of the most important components of a SIEM’s detection capabilities. Outdated, missing, or otherwise poorly configured content can cripple your SIEM.
Content Manager is a seamless mechanism to update and distribute content. It gives you the ability to download and deploy new policies from Securonix; update connectors, parsers, policies, threat models, lookups, and threat intelligence to the most current version; and to test new content before moving it to your production environment. This eases the burden of deploying new content and applying content fixes, which reduces the manual effort required to maintain your SIEM and in turn improves detection and alert quality.
Additionally, Content Manager gives MSSPs the ability to push content changes and updates to all or a subset of their customers using the user interface.
Next Level Cloud Content
Staying on top of cloud threats can be a challenge. The cloud offers organizations endless flexibility, but if the infrastructure isn’t secured properly attackers can access an organization’s environment and move laterally.
Thankfully, with our Jupiter release, we’ve created new cloud monitoring and detection content to help keep our customer’s environment safer. The new content primarily aligns with the MITRE Cloud Matrix tactics and techniques, especially for environments with Amazon Web Services, Google Cloud Platform, or Microsoft Azure.
Automated Threat Hunting for Newly Created Threats
Staying ahead of active threats is tough when you don’t have a dedicated threat hunting resource. To effectively detect new threats (such as HAFNIUM) you need to spend time to understand the threat, many times with very little information to go on, and then be able to search effectively across your organization’s environment.
Securonix provides automated threat hunting for new threats. When new threats are reported, our services can search across a customer’s environment (as long as they have opted-in for the service) for indicators of compromise (IOC). If any IOCs are found, the customer is notified immediately and given guidance on next steps from our Threat Labs team. This allows customers to focus on business priorities instead of circulating threats.
Live Channel
With limited visibility into data after it has been ingested but before enrichment, it’s challenging to search for a newly circulating threat or double check the ingestion pipeline to verify data sources are entering the Securonix platform correctly.
Live Channel provides real-time access to raw data so that you can search for threats or data pipeline issues with virtually no latency. Within seconds, data can be screened for priority threats. For larger customers, this live search capability is available across multiple tenants.
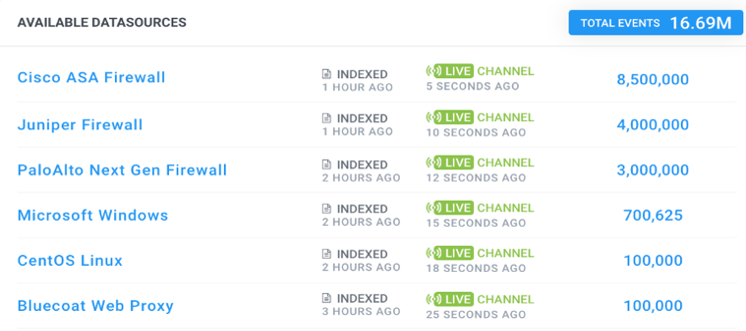
Figure 1: Example of Live Channel Availability
Phishing Analyzer
Due to the pandemic, working from home has become the new normal for many employees, and attackers have increased their phishing attempts – by 667% according to Barracuda Networks – to capitalize on this opportunity. These attacks are frequently an attempt to gain access to companies through business email compromise by impersonating trusted brands.
To combat this, Securonix has added new algorithms to our Phishing Analyzer feature to detect visual similarities or impersonation that may indicate a phishing attack. With our Jupiter release, we are specifically targeting typosquatting, where attackers send email from domains that appear visually similar to known and trusted domains.
While email gateway solutions provide basic protection from phishing attacks, Securonix adds a layer of detection so more sophisticated attacks do not go unnoticed.
In the figure below, the colored boxes below give you an idea of how Phishing Analyzer reviews email events. Red represents a higher risk event whereas yellow is potentially risky and green isn’t risky. You can see that BEC Sender and Typosquatted Domain are risky and Securonix will send an alert based on this activity to the security team.
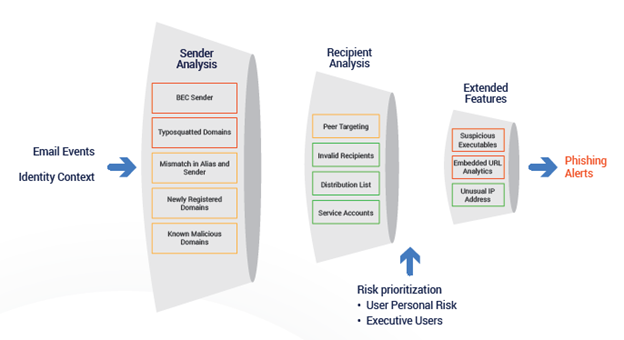
Figure 2: Phishing Analyzer Value Add
Sandbox-Based Threat Modeling
Testing threat models in a non-production environment is vital so that security analysts can fine tune new content without skewing existing risk scores. Securonix introduced our Sandbox feature in a previous release to help security teams do this with content.
With the Jupiter release, Sandbox capabilities have been upgraded to allow analysts to also QA Threat Models. Threat Modeling is an advanced technique that Securonix uses to help security teams detect complex threats. This update provides analysts the flexibility to build threat models and test them on production data, but separated from production results, until they are ready to deploy. The ability to fine-tune and test threat models before pushing them to production improves alert quality, analyst efficiency, and mean-time-to-respond.
Reduce Incident Response Times
Multi-Tenant Response
Large Securonix customers and partners told us they wanted a central display to add, edit, and manage incident response across multiple tenants instead of having to log in to individual customer accounts to manage, edit, and configure responses, which adds time and complexity to the response process.
The Multi-Tenant Response feature provides faster incident response by allowing you to search for incidents, violations, and events, as well as run associated playbooks in the Securonix UI without needing to navigate through multiple screens. This helps decrease overall incident response times.
MSSP partners can also configure and run custom playbooks and support different 3rd party integrations, all at the customer level, using tenant segregation.
On-Demand Cases
When an analyst is hunting for threats, they may need to open a case without attaching it to a specific violation. With our Jupiter release, analysts now have the ability to create a new case whenever they want, on-demand. Analysts can also attach evidence to the case giving them the flexibility to search and add real-time or historical evidence to enrich their investigations.

Figure 3: How To Create a New Incident From Anywhere in Securonix
Gain Better Time to Value and User Experience
Bring Your Own AWS
As organizations evaluate security in the cloud, they are looking for solutions that can be architected to optimize data-related costs while still providing best-in-class security capabilities.
Securonix is excited to announce we are collaborating with Amazon Web Services to provide customers a deployment model that enables them to maintain complete ownership of the data in their AWS account, while still benefiting from a fully managed SaaS SIEM solution. To learn more, join our Bring Your Own AWS webinar on April 28 for all the details.
New Ingestion Interface
The data onboarding process has been simplified to 3 steps. It begins with auto-discovery that automatically identifies new data sources and pre-populates a list. Then, auto-parsing identifies the most appropriate pre-built parser for the data, while also giving you the option to create a new parser or import the raw data as needed. Finally, the data is enriched to add context for better analytics and search.
Customers and partners save significant time onboarding new data sources with the new ingestion interface and automation steps.
Data Dictionary
Search and investigation can be confusing and frustrating for analysts due to the use of multiple data formats and the amount of unstructured data collected by enterprises. For example, there may be multiple sets of attributes and displays with obscure names like Customstring1 or Customstring2 instead of a descriptive label like LastReportedTotal or Duration.
Securonix Jupiter introduces Data Dictionary to provide a more consistent search experience. Data Dictionary introduces data labels to help eliminate confusion and make it easier to search across attributes reliably. For example, if an analyst wants to search for a file size, Data Dictionary labels the mapped attribute as Size across all inputs.
Activity Monitor
Most SIEM solutions don’t give you granular visibility into the amount of data ingested as it enters the SIEM. Also, if a customer wants to monitor their data usage by type of data source, time, or origination, they will need to contact their partner or the SIEM solution’s operations team for assistance.
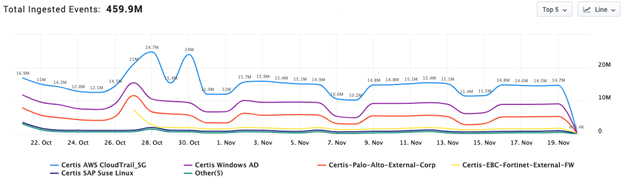
With Securonix Activity Monitor, you gain visibility into ingestion rates by data source and RIN statuses in greater detail. Administrators are able to identify trends in event data and quickly take appropriate actions as needed. You are able to view and analyze data ingestion by log source or filter by data source, as well as delay data ingestion by data source for more granular control. This reduces the time it takes to identify data ingestion issues and frees you up from having to rely on the Securonix Operations team for simple service disruptions.
Figure 4: Sample Data Ingestion Trend in Activity Monitor
Check it out!
Securonix is excited about our largest release ever, Jupiter. Like the planet, it’s so big that this blog post only covers a portion of what’s available. If you are Securonix customer and want additional details, please visit our documentation website to get the specifics.
If you’re not a customer, and you want to learn more, feel free to schedule a demo with our experts.