- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
This special edition of the Threat Labs Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in 2022. The report additionally provides a synopsis of the threats, indicators of compromise (IOCs), and tactics, techniques and procedures (TTPs) used by the threat actors. For additional information on related search queries used via Securonix Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In 2022, Threat Labs analyzed and monitored major threat categories, including multiple cyber campaigns involving ransomware and malware. Of note is the Russia-Ukraine cyber war which included phishing, denial of service, and taking advantage of software vulnerabilities. In addition, Threat Labs observed Follina zero-day and Atlassian Confluence remote code execution vulnerabilities. Ransomware dominated this year including the Yanluowang ransomware group that breached Cisco and LockBit’s new version LockBit 3.0 with new TTPs.
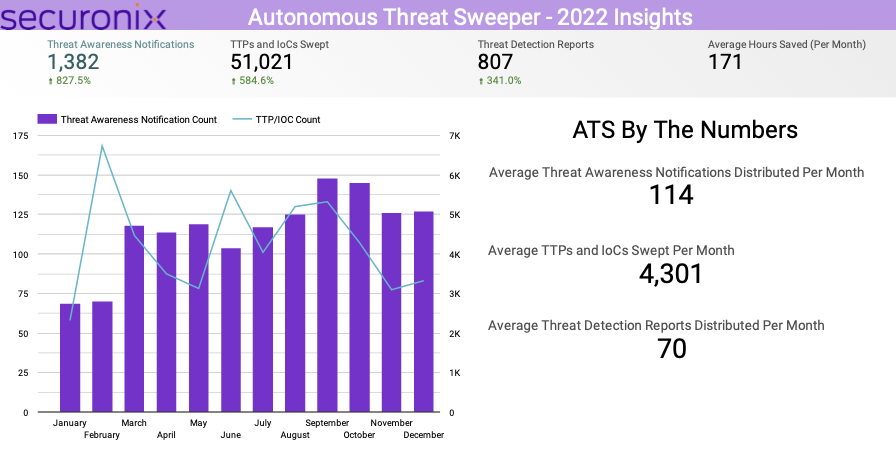
Securonix Autonomous Threat Sweeper (ATS) gave customers insights into threats in their environment through:
- 1,347 threat notifications (an 828% increase year over year)
- 807 threat detection reports (a 341% increase year over year)
By sweeping a total of more than 51,000 TTPs and IoCs, up 585% over last year, ATS saved each customer an average of 170 hours per month.
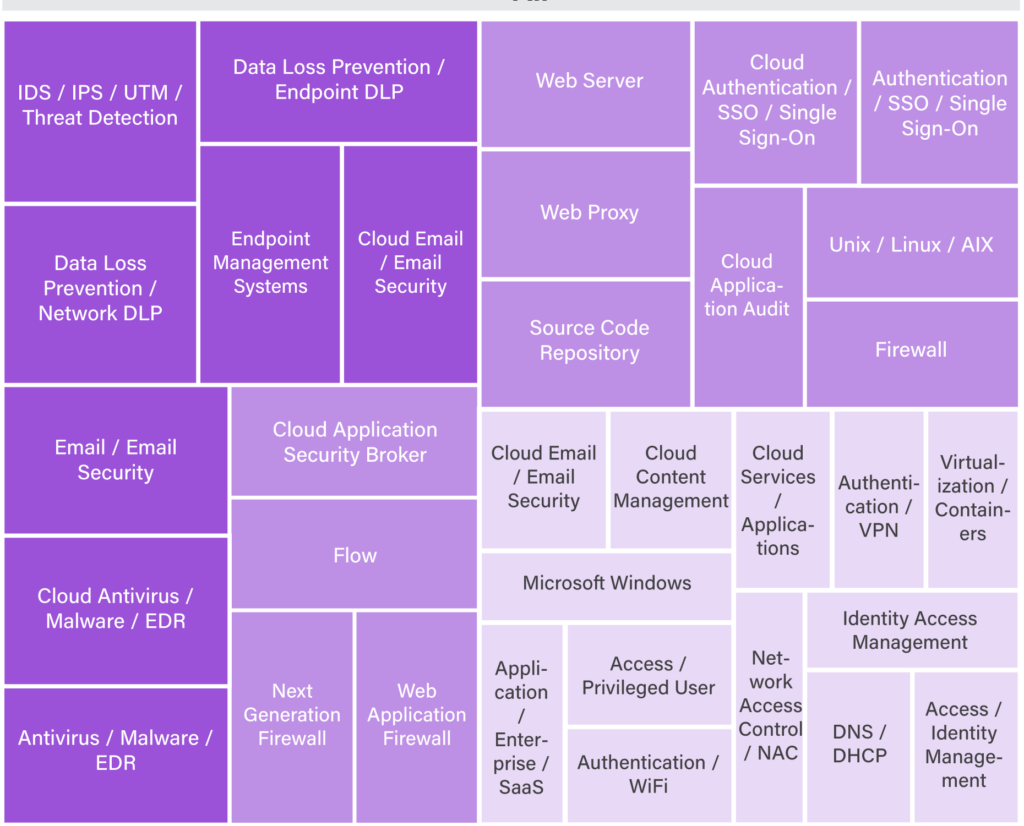
The most frequent data sources swept against were:
- Data loss prevention/endpoint
- Web server
- IDS/IPS/UTM
- Email/email security
- Content management
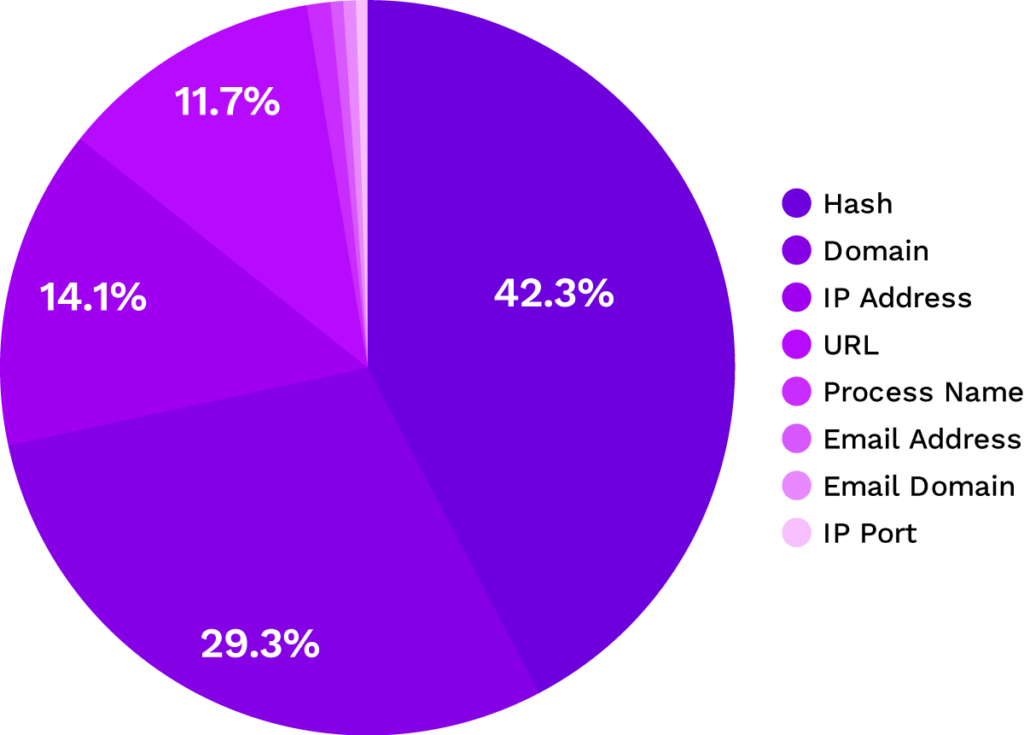
The most frequent IoCs swept by Securonix ATS included:
- Hash
- Domain
- IP address
Most Frequent IoC Types Swept Against
Threat landscape in 2022
(Originally published on December 2022)
Securonix covers global threats for the cybersecurity community in our Monthly Intelligence Insights reports. We summarize important industry alerts, advisories, and reports that the Securonix Threat Labs (STL), Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI) and the National Security Agency Central Security Service (NSA-CSS) published during the month.
The cyber threats for 2022 are over but threat actors continue to gain strength in skills and stealth by executing cyber warfare and espionage using ransomware, loaders, stealers and zero-day exploits: The following are the most prominent threats we identified each quarter of the year.
Q1 threat digest: Russia-Ukraine War
In the first quarter, Securonix Threat Labs observed a strategic overview of Ukraine’s threat landscape from cyber criminals and Russia-aligned threat actors in the form of nation-state activities.
Since the start of the war in February, Threat Labs observed an unprecedented number of adversaries driven by different motivations and of varying skill levels clustered in the same threat landscape. While escalated, Ukraine and its allies are familiar with this level of activity, since the country has defended itself from sophisticated cyberattacks since at least 2014. It has been difficult for defenders to respond to ongoing changes in adversary tactics, techniques, and procedures (TTPs) and new threats, and have difficulty attributing activity to specific groups because of the diverse actors involved in this most recent conflict. All of these actors have been active throughout the year.
In this threat space, cybercriminals are well known for being highly opportunistic. Threat actors have sent email lures related to the conflict, including humanitarian assistance and fundraising schemes. Moreover, cybercriminals used malware-infected offensive cyber tools to target Russian entities in an effort to exploit Ukrainian sympathizers.
We also monitored other sophisticated actors take advantage of the war to deliver malware to victims by creating themed lures. In February, Mustang Panda, a China-based threat actor, began conducting phishing campaigns against European companies and organizations, including those in Russia.
Many other threats, even those not attributable to specific actors, have been discovered or analyzed by Securonix, highlighting the diversity of adversaries and malware in the threat landscape. A series of destructive wipers and other malware were deployed against Ukrainian targets immediately following the war beginning with WhisperGate, HermeticWiper, CaddyWiper, DoubleZero, and CyclopsBlink. As part of the war, state-sponsored threat actors and other sophisticated adversaries have been highly active. For example, Gamaredon, a Russian state-sponsored threat group, has played a major role.
Q2 threat digest: Follina Zero-Day and Atlassian Confluence Remote Code Execution Vulnerabilities
The most prominent threats observed in the second quarter of 2022 involved two high severity vulnerabilities: Follina (CVE-2022-30190) and Atlassian Confluence Remote Code Execution Vulnerability (CVE-2022-26134). At the end of May, Microsoft announced a zero-day exploit named “Follina”, assigned CVE-2022-30190, that allows hackers to execute PowerShell commands across Microsoft Office applications by leveraging a bug in the Microsoft Support Diagnostic Tool (MSDT) and executing remote code. The vulnerability itself was first mentioned by a security research group named “Nao Sec” on Twitter on May 27 and acknowledged by Microsoft on May 31. Since then, it has been confirmed to have been spotted in the wild, being exploited by threat groups such as TA413 who are linked to the Chinese government.
The second vulnerability was reported on June 2 by Volexity which identified suspicious activity on two internet-facing servers running Atlassian’s Confluence Server application. After their analysis, Volexity determined the initial base was the result of a remote code execution vulnerability in Confluence Server and Data Center. The details were reported to Atlassian on May 31, and Atlassian has since assigned the issue to CVE-2022-26134. Atlassian issued a security advisory with the details. It appeared that the exploit is indeed an unauthenticated, remote code execution vulnerability. If the vulnerability is exploited, threat actors could bypass authentication and run arbitrary code on unpatched systems.
Q3 threat digest: Yanluowang ransomware group
At the beginning of the summer, Cisco confirmed that the Yanluowang ransomware group breached its corporate network.
According to Cisco Security Incident Response (CSIRT) and Cisco Talos, a Cisco employee’s credentials were compromised when threat actors gained control of their personal Google account, which was used to sync credentials stored in the victim’s browser.
As soon as attackers had credentials, they used a variety of techniques to bypass VPN client multifactor authentication. In addition to voice phishing, an attack known as MFA fatigue was used. This attack technique sends repeated push notifications to an individual’s device until the user either mistakenly or simply to stop receiving unwanted notifications accepts the request thereby triggering the attack.
By spoofing Cisco employees’ MFA, the attackers were able to run VPN software as the targeted Cisco employee. Once the attacker gained initial access to the Cisco VPN, they enrolled a series of new devices for MFA and authenticated successfully. Right after the actors gained administrative privileges, they logged into multiple systems. As a result, threat actors dropped multiple tools on the target network, including remote access tools such as LogMeIn and TeamViewer, as well as Cobalt Strike, PowerSploit, Mimikatz, and Impacket.
Cisco confirmed that the Yanluowang ransomware group’s data was authentic and was stolen during the intrusion in June. However, it pointed out that the stolen data did not contain sensitive information, so the security breach did not affect its business.
Q4 threat digest: LockBit 3.0 ransomware
LockBit 3.0, also called LockBit Black, is the newest version of the LockBit ransomware that was first discovered in September 2019. The ransomware family has a history of using the ransomware-as-a-service (RaaS) model and typically targets organizations that could pay higher ransoms.
By September 2022, a unique way for LockBit 3.0 to advertise was to pay people to get the LockBit logo tattooed on their bodies. Due to the high demand for tattooing the logo, the group announced on their website that it would only be available until September 11, 2022.
Soon after the tattoo publicity stunt, LockBit 3.0 made headlines as they attacked several companies within the technology and automotive industries. In October 2022, the group posted the attack on Pendragon, a UK car dealership, on their blog. As part of their ransom demand, LockBit claimed to have stolen more than two million files from the company and threatened to publish the data if the company failed to pay $60 million.
Also in October 2022, an affiliate of LockBit 3.0 attacked the Japanese tech company Oomiya with ransomware. The Oomiya group designs and manufactures microelectronics and facility systems. Attackers used LockBit’s ransomware to steal data and threatened to leak it by October 20, 2022, if the company refused to pay.
In addition to Oomiya, LockBit 3.0 also targeted Kingfisher insurance, a UK insurance company that operates eight brands in a variety of specialties. 1.4 TB of customer and employee data was purportedly stolen by the group. After infiltrating Kingfisher’s servers, the ransomware gang retrieved its data before demanding a ransom payment by December 28, 2022.
In early December 2022, Thales, a major defense and technology group in France, was additionally victimized by LockBit 3.0. LockBit may have stolen some of the company’s data and threatened to publish it by December 7, 2022, on their data leak website.
During the last quarter of 2022, LockBit 3.0 has been the most active ransomware gang, accounting for an estimated 37% of ransomware attacks worldwide. That number is likely to increase in the near future. So far, at least 1,000 people have been victimized by LockBit in the US, and tens of millions of dollars have been stolen in ransom payments.
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Kayzad Vanskuiwalla, Sina Chehreghani