- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
Executive Summary:
The 2024 Annual Cyber Threat Report provides a comprehensive analysis of key cyber threats and attack trends observed throughout the year. This report highlights emerging threat actor tactics, new vulnerabilities, and critical incidents that have affected global organizations. Key topics covered include high-profile cyberattacks, zero-day vulnerabilities, and evolving tactics used by threat actors across diverse sectors, with an emphasis on state-sponsored and criminal activities.
Key Findings:
- Emerging and Evolving Threats: Cyberattackers are increasingly exploiting vulnerabilities in widely-used technologies, such as Ivanti Connect Secure VPN and GlobalProtect VPN (CVE-2024-3400). Attackers are also evolving tactics, as evidenced by LockBit ransomware’s use of new encryptors and sophisticated phishing attacks by groups like TA4903 targeting the US government and small businesses.
- Targeted Campaigns and Nation-State Actors: Chinese state-sponsored hackers continue to target defense and government entities, using ScreenConnect and F5 bugs to gain unauthorized access. New advanced persistent threat (APT) groups like Actor240524 have emerged, focusing on healthcare and financial sectors. Additionally, the DEEP#GOSU and PHANTOM#SPIKE campaigns are increasingly aimed at high-value organizations for espionage.
- Cloud and Malware Techniques: Cybercriminals are exploiting cloud services for malware distribution, utilizing Unicode tricks to deceive users and evade security filters. Meanwhile, new techniques like DLL sideloading are being employed to inject malicious code into legitimate software, making detection and mitigation harder.
- Advanced Backdoors and Malware: New threats like the SUBTLE-PAWS PowerShell backdoor in Ukraine and the EDRKillShifter malware are advancing in complexity. These tools disable security mechanisms like endpoint detection and response (EDR) and antivirus, giving attackers undetected access to networks.
- Disruptions and Vulnerabilities in Critical Infrastructure: Notable disruptions, such as the CrowdStrike outage, highlight the vulnerabilities in cloud-based security solutions. Additionally, vulnerabilities like the FortiJump bug and the SLOW#TEMPEST campaign (DLL path traversal vulnerability) underscore ongoing risks in critical infrastructure sectors, especially in telecommunications and defense.
Table of contents:
- Executive Summary
- Key Findings
- ATS paragraph and how it is tied to Threat Labs
- About Securonix Autonomous Threat Sweeper
- Securonix Threat Research 2024
- Top Vulnerabilities of 2024
- The Snowflake Breach
- LockBit Resumes Attacks with LockBit 4.0
- The CrowdStrike Crash
- Annual Overview of APT Group Activity and Threat Landscape
- Cyberattack on MITRE’s NERVE Network
- Conclusion
- Mitigations
ATS paragraph and how it is tied to Threat Labs:
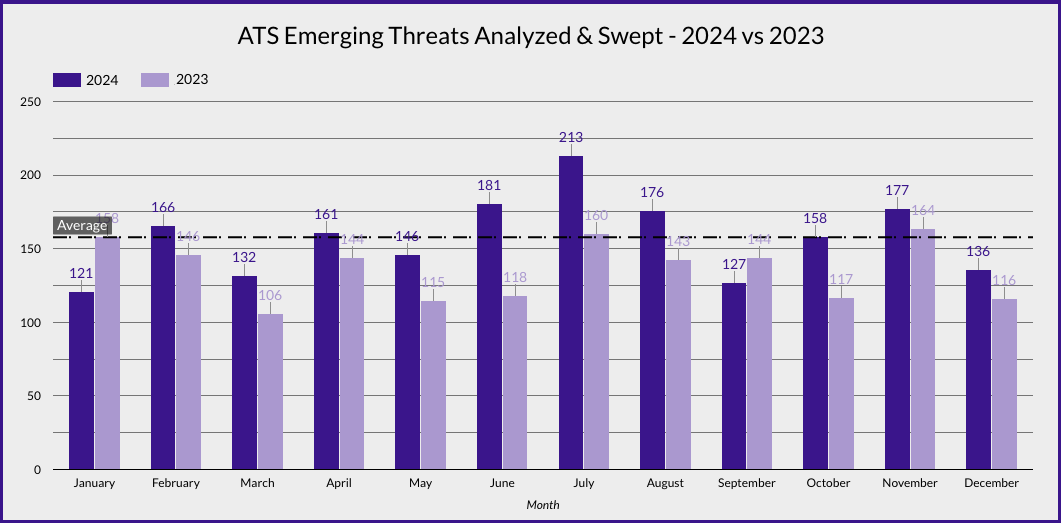
The bar chart above highlights the monthly count of emerging cyber threats analyzed and mitigated by ATS in 2023 and 2024. Threat activity saw a marked escalation in 2024, peaking mid-year with significant surges in June, July, and August. Overall, 2024 concluded with a 26% increase in threat activity compared to 2023, reflecting a more volatile cybersecurity landscape. Key incidents from 2024 include the June emergence of PHANTOM#SPIKE, a military-themed phishing campaign in Pakistan that leveraged documents from a Russian military forum to deploy backdoors via malicious CHM files. In July, a flawed update to CrowdStrike Falcon caused widespread Blue Screen of Death (BSOD) crashes, impacting critical sectors such as healthcare and banking, highlighting the inherent risks in security software updates. August brought the SLOW#TEMPEST campaign, a covert Cobalt Strike-based phishing operation targeting Chinese-speaking users with malicious ZIP files, employing advanced post-exploitation tactics to infiltrate business and government networks.
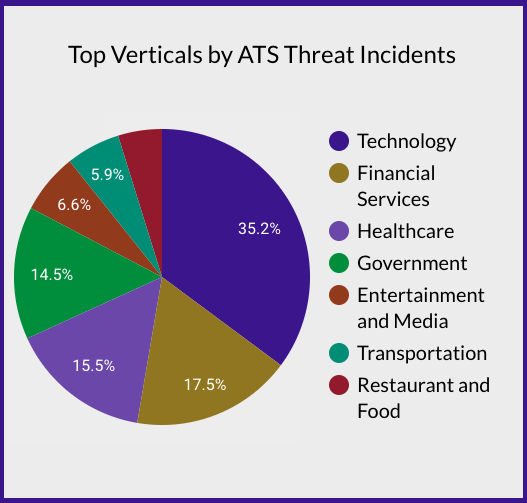
The pie chart above illustrates the distribution of sectors most impacted by these threats. The Technology sector (35.2%) and the Financial sector (17%) remained the primary targets, indicating that threat actors persist in prioritizing areas with high-value data or monetary potential. Healthcare, Government, and Entertainment and Media sectors also experienced notable incidents, likely driven by the increasing digitalization of these industries and the high value of their sensitive data.
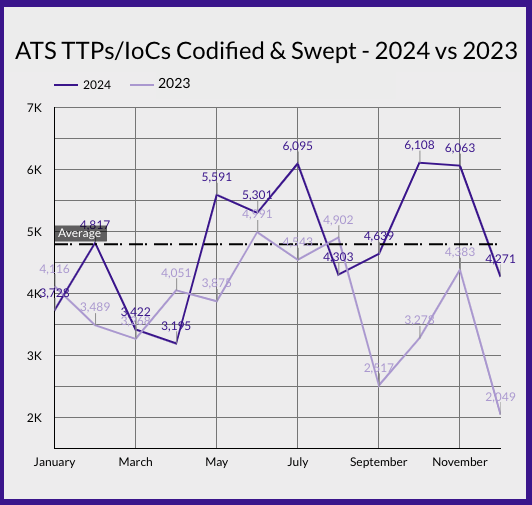
The above line graph compares the number of TTPs and IoCs codified and swept in 2024 against 2023. The trends reflect the heightened threat activity observed in 2024, particularly during July, October, and November. Despite month-to-month fluctuations, 2024 ended with a 25% increase compared to 2023, highlighting the ongoing evolution in both the frequency and sophistication of cyber threats. The surge in the identification of emerging threats, without a commensurate increase in successful detections, emphasizes the urgent need for continuous advancements in cyber defense systems.
This special edition of the Threat Labs Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in 2024. In 2024, the Autonomous Threat Sweeper (ATS) team continued our mission to remain vigilant against advanced cyber threats and challenges in a modern era that is increasingly reliant on digital solutions and big data. Over the past 12 months, ATS has analyzed and codified over 1,900 emerging threats, encompassing more than 56,000 TTPs and IoCs. Our efforts in investigating over 780 potential threats and addressing over 117 significant threat incidents have been crucial in maintaining the security posture of our client base during this period. The operational efficiency achieved by the ATS team has led to an estimated average of 324 hours saved per month this year, demonstrating both proactivity and effectiveness.
In this report, we have selectively highlighted the most significant cyber threats for each quarter, focusing on those with substantial global and business impact. By analyzing these pivotal threats, we aim to provide a clearer understanding of the threat landscape and how these incidents correlate with global economic trends and regional developments. Our evaluation is designed to share the insights needed to proactively align cybersecurity posture with the realities of the current global threat environment.

About Securonix Autonomous Threat Sweeper:
Securonix Autonomous Threat Sweeper (ATS) works by identifying threats in the wild, aligning indicators of compromise (IoCs) and the tactics, techniques, and procedures (TTPs) observed in these threats with pertinent data source fields, scanning for indicators of potential breaches. Based on the frequency of data sources swept, certain data sources increase in use compared to other sources. Over the past year, the data sources that have been most instrumental in revealing active threats include Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), Unified Threat Management (UTM), Endpoint Management Systems, Data Loss Prevention (DLP), and Email Security protocols.
Reflecting on the types of indicators of compromise (IoCs) employed in threat detection, certain IoC types have increased in use compared to other IoC types across the past year. Specifically, hash values have emerged as the predominant type of IoC in sweeps for threats in the wild. This prominence of hash values in identifying threats is due to a combination of factors. Hash values are inherently reliable for confirming the authenticity of files or data, owing to their computational efficiency and the difficulty of altering them without detection. Furthermore, the resistance to hash collisions—wherein two distinct inputs produce the same hash output—varies depending on the hashing algorithm, but generally contributes to their robustness as an IoC. Given these strengths, Securonix projects that hash values will continue to be one of the top identifiers for threats. Their rapid and accurate detection of known threats, along with their seamless integration into existing security frameworks, cements their status as an indispensable resource in cybersecurity defense strategies.
ATS continues to adapt to the ever-evolving threat landscape, leveraging Securonix’s core values of teamwork, customer-driven innovation, and agility. Innovations introduced this year, such as on-demand ATS intelligence submission and automatic case creation within environments, have significantly enhanced our threat detection and response capabilities. We deeply value the trust our customers place in us and are committed to continuously refining our services to meet evolving security needs. Our unwavering goal is to provide effective and efficient rapid responses to emerging threats in an ever-changing threat landscape. For additional information on related search queries used via Securonix Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
Although the specific cyber threats of 2024 have passed, threat actors continue to enhance their capabilities and sophistication, engaging in cyber warfare and espionage through the use of ransomware, loaders, stealers, and zero-day exploits. Below, we highlight the most significant threats identified in the year 2024.
To learn more about how Securonix ATS enables SOCs to be proactive, respond quickly, and efficiently deal with cyber threats by removing the manual investigations that are required to hunt and detect threats by retrospectively sweeping customer environments for IoCs and TTPs, visit: Autonomous Threat Sweeper
Securonix Threat Research 2024
The year 2024 saw a diverse range of cyberattack campaigns, highlighting an ongoing evolution of attack techniques, threat actor sophistication, and the targeted sectors. Key trends included advanced phishing campaigns, PowerShell and VBScript-based malware, as well as the exploitation of vulnerabilities in widely used platforms. Threat groups employed obfuscation, social engineering, and novel tools to bypass detection and gain persistent access to compromised systems. Below is a summarized overview of the notable campaigns and tactics identified by Securonix Threat Research:
- Shuckworm and SUBTLE-PAWS (February)
A PowerShell-based backdoor, SUBTLE-PAWS, was identified in an ongoing campaign targeting Ukrainian military personnel. The backdoor used obfuscated techniques, including infected USB sticks, phishing emails, and compressed files to deliver the malicious payload. The campaign is believed to be associated with the Shuckworm group (also tracked as STEADY#URSA), which has been linked to prior attacks against Ukraine.
- DEEP#GOSU – North Korean (March)
DEEP#GOSU, a sophisticated attack linked to the North Korean group Kimsuky, used PowerShell and VBScript malware to infect Windows systems and steal sensitive data. The attack involved multiphase threats designed to operate covertly, leveraging network monitoring tools and advanced obfuscation to evade detection.
- FROZEN#SHADOW (April)
The FROZEN#SHADOW campaign targeted global organizations using SSLoad malware, Cobalt Strike, and ConnectWise ScreenConnect remote desktop software. Phishing emails contained links to download a malicious JavaScript file, which initiated the infection process. This campaign was indiscriminate, affecting organizations across Asia, Europe, and the Americas.
- DEV#POPPER – North Korean (April)
In a social engineering campaign, threat actors used fake npm packages disguised as job interviews to trick developers into downloading a Python-based backdoor. The DEV#POPPER campaign, associated with Kimsuky, exploited developers’ trust in seemingly legitimate sources like GitHub.
- DLL Sideloading Attacks (April-May)
Securonix observed continued use of DLL sideloading, a long-standing and effective attack technique. Despite being in use for over 15 years, DLL sideloading remains a reliable method for evading endpoint detection and response (EDR) tools. Organizations are urged to implement solutions that can specifically detect this technique.
- CLOUD#REVERSER (May)
CLOUD#REVERSER involved phishing emails leading to a ZIP file with a disguised Excel file. Inside, the attackers staged scripts via trusted cloud storage platforms like Dropbox and Google Drive. The payloads involved heavily obfuscated VBScript and PowerShell scripts that fetched commands from the cloud, exploiting trusted services for command-and-control operations.
- PHANTOM#SPIKE (June)
In Pakistan, a military-themed phishing campaign used password-protected ZIP files to deploy the PHANTOM#SPIKE backdoor. The attackers leveraged documents related to a real Russian military forum to convince victims to open a CHM file, which secretly executed RuntimeIndexer.exe, establishing remote access.
- CrowdStrike BSOD Incident (July)
A flawed CrowdStrike Falcon update caused widespread Blue Screen of Death (BSOD) system crashes globally, affecting industries such as banking, healthcare, and transportation. While Securonix operations were unaffected, the incident highlighted the vulnerabilities in security software updates.
- SLOW#TEMPEST (August)
A Cobalt Strike-based phishing campaign, SLOW#TEMPEST, targeted Chinese-speaking users with a ZIP file containing a malicious shortcut file. This attack, which remained undetected for over two weeks, employed post-exploitation tools to establish persistence and move laterally within networks, likely focusing on Chinese business and government sectors.
- FortiManager Vulnerability Exploitation (October)
The CVE-2024-47575 vulnerability in FortiManager was exploited in attacks starting as early as June 2024. This critical flaw, affecting both on-premises and cloud versions, allowed unauthenticated remote attackers to execute arbitrary commands. Despite a patch being released, over 59,000 devices were still exposed, emphasizing the need for immediate forensic investigations by affected organizations.
- CRON#TRAP – Linux Backdoor via QEMU (November)
The CRON#TRAP campaign employed a novel approach using QEMU to emulate a Linux environment on compromised endpoints. This technique, delivered through phishing emails, marked the first known malicious use of QEMU outside of cryptomining. The attack created a backdoor that connected to a remote C2 server, ensuring long-term access to compromised systems.
- FLUX#CONSOLE – Tax-Related Phishing (December)
The FLUX#CONSOLE campaign used MSC files and advanced obfuscation to execute a stealthy backdoor. The phishing emails carried documents with tax-related themes, such as government tax forms, as lures. While the PDF documents appeared benign, they were used to distract the victim while a malicious payload was executed silently in the background.
Key Trends and Observations:
- PowerShell and VBScript Malware: These scripting languages were consistently used across campaigns to deliver and run payloads, often enabling stealthy and evasive attacks.
- Advanced Phishing Techniques: Campaigns increasingly employed socially engineered phishing tactics, with lures ranging from military documents to job offers, to convince victims to execute malicious files.
- Use of Trusted Platforms: Cloud storage services (e.g., Dropbox, Google Drive) and legitimate tools (e.g., QEMU) were abused for command-and-control and persistence, making detection more difficult.
- Exploitation of Vulnerabilities: Flaws in widely used tools and platforms, such as FortiManager and CrowdStrike Falcon, continued to be targeted, emphasizing the importance of timely patching and vigilance.
Top Vulnerabilities of 2024
The 2024 threat landscape witnessed the emergence of several critical vulnerabilities, leading to significant security risks for organizations across industries. The following three high-impact incidents highlight the threats to enterprise systems, underscoring the need for proactive vulnerability management and timely patching.
- Ivanti Connect Secure VPN exploited (January 2024)
In 2023 and early 2024, researchers discovered unusual activity within a client’s network. The investigation revealed the use of web shells on a number of internal and external web servers linked to the company’s Ivanti Connect Secure (ICS) VPN appliance.
Investigators found that the unusual activity began on December 3 and that the Ivanti Connect Secure VPN appliance had both disabled and erased its data.
Further research validated the deployment of an exploit chain using zero-day vulnerabilities reported as CVE-2023-46805 and CVE-2024-21887. By taking advantage of these flaws, the attacker was able to execute code remotely and bypass authentication.
With a high CVSS score of 8.2, CVE-2023-46805 was able to bypass authentication in the online component of Ivanti Policy Secure, 9.x, and 22.x versions of Ivanti Connect Secure. Bypassing control checks allows remote attackers to get access to resources that are forbidden.
CVE-2024-21887 (Critical, 9.1 CVSS Score command injection vulnerability exists in the web components of Ivanti Policy Secure and Ivanti Connect Secure (9.x, 22.x). It permits an authenticated administrator to use crafted requests to execute arbitrary commands.
A third party published a proof of concept (PoC) on January 16, 2024, which increased the scope of exploitation. In addition to the existing threat, Ivanti disclosed two additional vulnerabilities on January 31: CVE-2024-21888, which is a privilege escalation flaw, and CVE-2024-21893, which is an SSRF web vulnerability. These vulnerabilities increase the need for action and increased security awareness while the manufacturer continues to work on developing and delivering suitable mitigations.
- Critical Vulnerability in Palo Alto Networks PAN-OS (April 2024)
In early 2024, Palo Alto Networks issued a security alert regarding the exploitation of a critical vulnerability in its PAN-OS software, specifically affecting the GlobalProtect gateways. The flaw, identified as CVE-2024-3400, was assigned a maximum CVSS severity score of 10.0.
This vulnerability involved a command injection issue in the GlobalProtect feature of certain PAN-OS versions, which allowed attackers to execute arbitrary code on the firewall with root privileges. The flaw was present in the following PAN-OS versions:
– PAN-OS versions < 11.1.2-h3
– PAN-OS versions < 11.0.4-h1
– PAN-OS versions < 10.2.9-h1
The vulnerability only affected systems where both device telemetry (under Device > Setup > Telemetry) and the GlobalProtect gateway (under Network > GlobalProtect > Gateways) were enabled.
The issue was first identified and reported by Volexity and was subsequently added to the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerability Catalog. Zscaler’s experts also observed attempts to exploit this vulnerability, particularly after an exploitation script was made publicly available on GitHub.
- Operation Lunar Peek (November 2024)
In November 2024, Palo Alto Networks and Unit 42 tracked exploitation activities targeting CVE-2024-0012 and CVE-2024-9474 vulnerabilities. CVE-2024-0012, an authentication bypass in PAN-OS, allowed unauthenticated attackers with network access to gain administrator privileges, potentially exploiting other vulnerabilities like CVE-2024-9474. Initial exploitation, detected on November 18, 2024, involved targeting device management interfaces from IP addresses linked to anonymous VPN services. Post-exploitation activities included command execution and malware deployment, such as obfuscated web shells, on compromised firewalls. Fixes for both vulnerabilities has released, with recommendations to update to the latest patches (CVE-2024-0012 and CVE-2024-9474). To mitigate risks, it was advised to limit access to the management interface to trusted internal IP addresses and block external access from the internet.
Key Trends and Observations:
- Increased Focus on Remote Access and Network Perimeter Devices: Vulnerabilities like those in Ivanti Connect Secure and Palo Alto Networks PAN-OS underscore the increasing attention on remote access infrastructure as a vector for cyberattacks, particularly as hybrid work environments become more common.
- Ransomware and Espionage Campaigns: The exploitation of these vulnerabilities is closely tied to the rise of ransomware attacks and cyber espionage campaigns, with threat actors targeting valuable data and infrastructure.
- Patching Delays and Vulnerability Lifecycle: Delayed patching remains a significant challenge, with many organizations still not fully updating systems in a timely manner. This delay opens the door for attackers to exploit known vulnerabilities, especially in widely deployed systems like VPNs and firewalls.
- Growing Complexity of Exploits: The vulnerabilities in these cases show an increasing sophistication in attack strategies, from the use of zero-day exploits to the evasion techniques employed by APT groups, demonstrating that organizations must continuously adapt their security posture to defend against evolving threats.
The Snowflake Breach (June 2024)
In 2024, Snowflake, a cloud-based service for storing large datasets, became the target of a significant data breach campaign. In May, up to 165 of its customers had their databases accessed and stolen using valid login credentials. By June, the stolen data was offered for sale on BreachForums, a prominent English-speaking cybercrime forum that had been revived after a prior FBI takedown earlier in the year. The breach had a far-reaching impact, with publicly confirmed consequences for 110 million AT&T customers, 30 million Santander customers, 560 million Ticketmaster customers, 380 million Advance Auto Parts customers, and 190 million LendingTree customers.
Snowflake’s investigation revealed that the breaches were part of a deliberate campaign targeting users with single-factor authentication. The cybercriminals leveraged leaked credentials from infostealing malware. The investigation ruled out the possibility that the attack stemmed from compromised credentials of current or former Snowflake employees or from any vulnerabilities in the Snowflake product.
On a positive note, the cybercriminals behind the attack have been caught. In November, US authorities charged Connor Moucka and John Binns in connection with the Snowflake breach.
Key Trends and Observations:
- Exploitation of Weak Authentication Methods: The Snowflake breach underscores the vulnerability of single-factor authentication (SFA) in safeguarding sensitive data. Cybercriminals targeted users with weak security practices, highlighting the growing need for multi-factor authentication (MFA) as a standard security measure.
- Credential Theft via Infostealing Malware: The breach was facilitated by infostealing malware that harvested user credentials, pointing to an increasing reliance on malware to steal login information. This trend emphasizes the importance of endpoint security and vigilance against malware infections.
- Data Trade on Dark Web Platforms: Stolen data from the Snowflake breach was offered on BreachForums, an underground cybercrime marketplace. This trend of stolen data being traded on such platforms highlights the growing sophistication of cybercrime communities and the challenges of tracking and mitigating stolen data.
- Targeting of High-Profile Cloud Platforms: Cloud services like Snowflake are increasingly becoming prime targets for cyberattacks, given the valuable data they store. This trend signals the need for cloud providers and their clients to implement robust security frameworks and practices to defend against large-scale breaches.
LockBit Resumes Attacks with LockBit 4.0 (February 2024)
After the disruption on February 19th, 2024, by law enforcement, the LockBit ransomware group resumed operations, utilizing upgraded encryptors and new ransom letters pointing to different servers.
A few days earlier, the NCA, FBI, and Europol had coordinated a disruption against the LockBit ransomware campaign, known as “Operation Cronos.” During this operation, law enforcement had confiscated infrastructure, obtained decryptors, and, in a particularly embarrassing turn of events for LockBit, turned the group’s data leak website into a police press portal.
Following the disruption, LockBit had claimed that law enforcement compromised their servers through a PHP bug and issued a lengthy note to the FBI, stating that they had set up a new data leak website. Instead of rebranding, however, the group asserted that they would return with enhanced security and updated infrastructure to prevent law enforcement from accessing decryptors and carrying out operation-wide attacks.
LockBit appeared to have resumed its attacks by February 27, 2024. New encryptors and infrastructure for data leaks and negotiation sites had been established. It has been discovered that the group had added Tor URLs to the ransom letters attached to their encryptors. Later, samples of the new encryptor were uploaded to VirusTotal, revealing the latest ransom messages.
A few experts confirmed that LockBit had resumed operations following the disruption in February 2024. Their research also revealed potential imposters claiming to be LockBit 4.0 on VirusTotal. They identified five SHA256 hashes as indicators of compromise for the campaign.
In December 2024, cybersecurity experts reported that the LockBit ransomware group had launched LockBit 4.0, marking a full comeback after a year of law enforcement crackdowns. In related news, the U.S. Department of Justice had charged Rostislav Panev, a 51-year-old Russian-Israeli dual-national, for his alleged role in developing LockBit ransomware encryptors and the “StealBit” data-theft tool, as detailed in a criminal complaint unsealed in New Jersey.
Key Trends and Observations:
- LockBit’s Rapid Comeback: Despite a major law enforcement disruption in February 2024, the LockBit ransomware group quickly resumed operations, launching the upgraded LockBit 4.0 with improved encryptors and security measures.
- Enhanced Security Measures: LockBit implemented new infrastructure, including Tor URLs in ransom letters, to prevent law enforcement from accessing decryptors and interfering with their operations.
- Imposter Activity: There were reports of imposters posing as LockBit 4.0 on VirusTotal, with researchers identifying specific SHA256 hashes as indicators of compromise linked to the group’s new campaign.
- Legal Actions Against Key Members: The U.S. Department of Justice charged Rostislav Panev, a dual-national involved in the development of LockBit’s encryptors, highlighting ongoing efforts to dismantle the ransomware group at a criminal level.
The CrowdStrike Crash (July 2024)
In 2024, a significant global disruption occurred not due to a cyberattack but because of a failure within CrowdStrike’s endpoint detection and response (EDR) software for the Windows operating system. This event, often dubbed “WannaStrike” or the “Blue Falcon of Death,” stemmed from inadequate testing of patches before deployment and an over-reliance on a single software solution. The issue became a critical point of failure for numerous organizations, particularly in North America and Europe, where most of CrowdStrike’s clients are located. The disruption impacted various sectors, including businesses, airports, train stations, banks, broadcasters, and healthcare providers.
In the wake of the crash, cybercriminals took advantage of the chaos by launching phishing campaigns, registering malicious domains, and distributing malware. Some of these criminals impersonated CrowdStrike support in scam emails, preying on organizations seeking assistance. One prominent example of this activity involved the distribution of HijackLoader, a malicious tool delivered through phishing emails pretending to be an essential “hotfix” for LATAM countries. This loader installed Remcos, a remote access Trojan (RAT), giving attackers full control over compromised systems.
On July 23, 2024, CrowdStrike Intelligence detected a malicious ZIP file titled “CrowdStrike Falcon.zip.” The archive contained Connecio, a Python-based information-stealing program. This file emerged shortly after the initial software disruption, with the aim of tricking recipients into believing it was a legitimate CrowdStrike update although a fix was released.
Key Trends and Observations:
- Widespread Global Impact: The disruption affected numerous sectors across multiple regions, particularly in North America and Europe. Industries such as business, transportation (airports, train stations), banking, broadcasting, and healthcare were significantly impacted, showing the far-reaching consequences of a failure in critical cybersecurity infrastructure.
- Exploitation by Cybercriminals: Cybercriminals quickly capitalized on the confusion caused by the CrowdStrike failure. They launched phishing campaigns, registered malicious domains, and distributed malware while pretending to be legitimate CrowdStrike support. This underscores the need for heightened vigilance and rapid response to exploitations during disruptions.
- Phishing and Malware Distribution: A key strategy used by cybercriminals during this period was phishing. One example involved the distribution of HijackLoader via phishing emails that masqueraded as necessary updates or “hotfixes,” particularly targeting LATAM countries. The loader delivered a remote access Trojan (RAT), Remcos, which allowed attackers full control of compromised systems.
- Deceptive Tactics in Cybercrime: Cybercriminals employed sophisticated deception by creating fake files like the “CrowdStrike Falcon.zip,” which appeared to be legitimate updates. This reflects the increasing sophistication of cybercriminals in posing as trusted entities to deceive victims into installing malware.
Annual Overview of APT Group Activity and Threat Landscape
In 2024, several notable advancements in cyber threat activity were observed, particularly from emerging and established APT groups.
- Actor240524 (August 2024)
Actor240524, a new adversary group, emerged with an advanced toolkit for evading detection and maintaining persistence. In early July 2024, the group launched a spear-phishing attack targeting ambassadors from Azerbaijan and Israel. The attackers employed a malicious Word document, written in Azerbaijani, which masqueraded as official communication to steal sensitive information.
- TA4903 (March 2024)
Proofpoint researchers reported a significant increase in credential phishing and fraud campaigns throughout mid-2023 and early 2024. These campaigns targeted small and medium-sized businesses (SMBs) across various sectors, including manufacturing, energy, finance, food and beverage, and construction. A rise in Business Email Compromise (BEC) themes was also noted, with attackers using topics like “cyberattacks” to persuade victims to disclose banking and payment information.
- Lazarus Group (September 2025)
In 2024, the Lazarus Group, a North Korean APT group linked to the Reconnaissance General Bureau (RGB), intensified its cyber campaigns, particularly targeting developers with financially motivated attacks. One notable tactic, the “Contagious Interview,” involved luring job-seekers into downloading a compromised Node.js project containing the BeaverTail malware, which had evolved from a JavaScript variant into a native macOS version by July 2024. In August 2024, Group-IB researchers uncovered a fraudulent Windows video conferencing app, another instance of BeaverTail malware. Further investigation revealed new malicious repositories on code-sharing platforms, including an updated Python version of BeaverTail, enhancing its capabilities.
The Lazarus Group, which operates under multiple sub-groups, such as Bluenoroff, Citrine Sleet, Andariel, TEMP.Hermit, TraderTraitor, and Kimsuky, continued to conduct a wide range of cyber operations, including intelligence gathering, financial crime, and destructive attacks. Their activities have included high-profile incidents such as the 2014 Sony Pictures hack, the 2017 WannaCry ransomware attacks, and various cryptocurrency exchange breaches. The evolution of their tactics and tools underscores their ongoing role in supporting North Korean state interests, including espionage and geopolitical disruption.
Key Trends and Observations:
- Emergence of New and Sophisticated APT Groups: The rise of **Actor240524**, a new adversary group, highlighted the growing sophistication of APT groups, utilizing advanced evasion techniques and targeting high-value individuals such as diplomats.
- Surge in Credential Phishing and BEC Attacks: A notable increase in credential phishing and Business Email Compromise (BEC) campaigns was observed, with attackers using deceptive themes like “cyberattacks” to steal sensitive financial information from small and medium-sized businesses across various sectors.
- Focus on Developers with Financially Motivated Malware: The Lazarus Group intensified its cyber operations by targeting developers through the “Contagious Interview” tactic, distributing evolving malware such as BeaverTail in compromised job-related downloads.
- Fraudulent Software and Social Engineering Attacks: The use of fraudulent software, such as fake video conferencing apps and malicious code repositories, grew, showcasing the continued reliance on social engineering tactics by APT groups like Lazarus to distribute malware.
Cyberattack on MITRE’s NERVE Network
A cyber attack on a not-for-profit organization exploited zero-day vulnerabilities in Ivanti Connect Secure (ICS) and manipulated the VMware environment, demonstrating a high level of sophistication. The threat actor created rogue virtual machines (VMs) within the VMware infrastructure using compromised vCenter Server access. To establish covert communication channels, the attacker deployed a JSP web shell (BEEFLUSH) within the vCenter Server’s Tomcat server. This shell was used to execute a Python-based tunneling tool, facilitating SSH connections between the adversary’s VMs and the ESXi hypervisor infrastructure. This approach allowed the attacker to bypass traditional detection methods and operate undetected.
The motive behind the attack appeared to be two-fold: evading detection by masking malicious activities from centralized management interfaces like vCenter and maintaining persistent access while minimizing the risk of discovery. By leveraging existing infrastructure components within the virtualized environment, the attacker blended in with legitimate traffic and operations, making detection more difficult.
According to the VMware PSIRT team, enabling secure boot was identified as the most effective countermeasure against the persistence technique. Secure boot, a security feature that verifies the integrity of a host’s boot process, protected against malicious code injection and reduced the risk of unwanted changes. This countermeasure aligned with MITRE’s ATT&CK Mitigation: Boot Integrity (M1046), helping organizations strengthen their boot process and prevent unauthorized access or undetected modifications to critical systems.
Key Trends and Observations:
- Exploitation of Zero-Day Vulnerabilities: The attack utilized previously unknown vulnerabilities in Ivanti Connect Secure (ICS), highlighting the increasing use of zero-day exploits to gain unauthorized access to critical systems.
- Sophisticated Attack Techniques and Evasion: The attacker employed advanced tactics such as creating rogue virtual machines (VMs) and using covert communication channels (JSP web shell and Python tunneling tool), effectively evading traditional detection methods.
- Focus on Persistent Access and Virtualized Environments: The adversary aimed to maintain undetected, persistent access by leveraging virtualized infrastructure components like vCenter, blending malicious activities with legitimate operations to avoid detection.
- Importance of Secure Boot for Mitigation: Enabling secure boot emerged as a critical countermeasure, ensuring the integrity of the host’s boot process and protecting against unauthorized access and malicious code injection within the environment.
Conclusion:
The year 2024 saw an alarming increase in the sophistication and diversity of cyberattack campaigns, with threat actors employing a wide range of tactics, from advanced phishing and social engineering to novel malware techniques and exploitation of zero-day vulnerabilities. The attacks targeted various sectors, including military, finance, healthcare, and critical infrastructure, highlighting the need for enhanced cybersecurity measures across industries. The evolving tactics, including the use of obfuscation, PowerShell, VBScript, and DLL sideloading, demonstrate the increasing sophistication of adversaries and their ability to bypass traditional defenses.
Notable events such as the LockBit ransomware resurgence, the Snowflake breach, and the CrowdStrike crash underscore the vulnerability of even well-established cybersecurity infrastructures. Additionally, the exploitation of critical vulnerabilities in widely used platforms like Ivanti Connect Secure, Palo Alto Networks PAN-OS, and VMware further emphasized the importance of timely patching and vulnerability management.
APT groups, particularly from North Korea and newly emerging actors like Actor240524, have intensified their operations, employing highly targeted spear-phishing, credential theft, and malware campaigns to steal sensitive information, disrupt organizations, and achieve geopolitical or financial objectives.
Mitigations:
- Timely Patching and Vulnerability Management: Ensure that all critical systems and software, such as Ivanti Connect Secure, Palo Alto Networks PAN-OS, and VMware, are promptly patched to mitigate exploitation risks. Apply patches as soon as they are released and continuously monitor for new vulnerabilities.
- Multi-Factor Authentication (MFA): Enforce MFA across all systems, especially for remote access and high-value accounts, to significantly reduce the impact of stolen credentials, as seen in the Snowflake breach.
- Advanced Threat Detection Tools: Implement advanced endpoint detection and response (EDR) solutions that can identify and block sophisticated attacks like DLL sideloading, PowerShell-based malware, and obfuscated payloads. Regularly update and fine-tune these tools to keep pace with evolving attack techniques.
- Employee Training and Awareness: Regularly educate employees on the dangers of phishing, social engineering, and malicious attachments. Encourage vigilance when interacting with unsolicited emails or unfamiliar links, especially those disguised as official communications.
- Network Segmentation and Zero Trust Architecture: Implement network segmentation and Zero Trust principles to limit lateral movement and contain potential breaches. Restrict access based on the principle of least privilege and continuously monitor for abnormal behavior.
- Secure Software Development Practices: For organizations involved in software development, emphasize the use of secure coding practices, regular vulnerability assessments, and code reviews to mitigate the risk of malicious packages or backdoors being introduced into repositories.
- Enhanced Incident Response Plans: Develop and regularly update incident response plans to ensure swift containment and remediation of breaches. Include specific strategies for handling targeted ransomware attacks, supply chain disruptions, and compromised cloud services.
Contributors: Nitish Singh, Nikhil Kumar Chadha
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.