- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs, Threat Research: Den Iuzvyk, Tim Peck
July 5, 2022
Introduction
A new malware loader named BumbleBee is actively being used to target businesses using mass phishing or spear-phishing campaigns as an initial attack vector. Malware loaders (or droppers) are commonly used by ransomware groups and other APTs to distribute payloads as they are extremely effective during the initial stages of compromise. BumbleBee in particular, appears to be a popular method of delivery for the Conti, Quantum and Mountlocker ransomware groups which seem to be moving away from other popular loaders such as Emotet, Trickbot and BazarLoader.
While early samples are still coming to light, analyzed variations of BumbleBee appear to follow a similar delivery mechanism which we can use to detect the initial foothold of the loader.
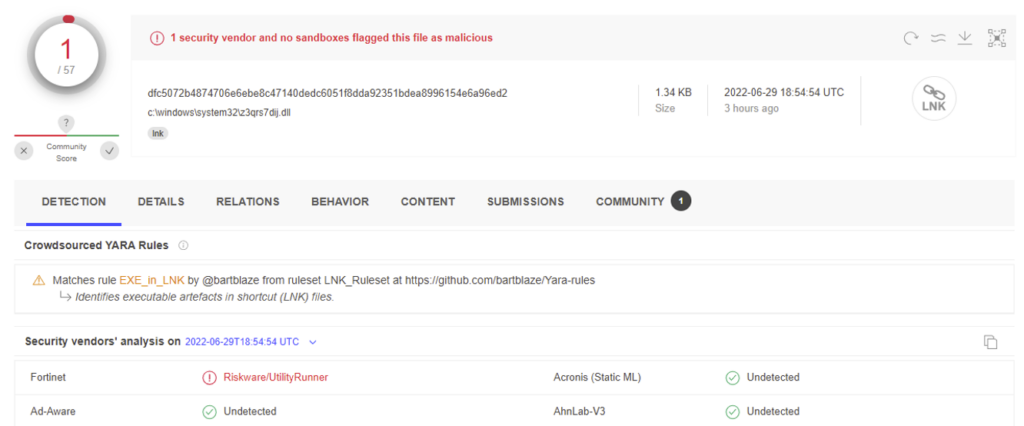
Currently, AV detection of the BumbleBee loader is very weak as vendors work to update their signatures and heuristic detections. As you can see in figure 1, the main DLL payload of this loader is very much capable of evading EDR detection at the time of publication.
Figure 1
Analysis: initial compromise
As with most loader malware, initial compromise originates from a phishing campaign which attempts to lure the victim to opening a specially crafted email attachment.
The phishing email would contain an image file (.img) as an attachment along with text which would attempt to lure the user to open and run its contents. Once the attachment is opened, the user is presented with the contents of the newly mounted drive. In this particular BumbleBee sample, the files “project requirements” “project.rsp” and “start.dll” were present.
These files and the initial attack chain can be seen in figure 2 below.
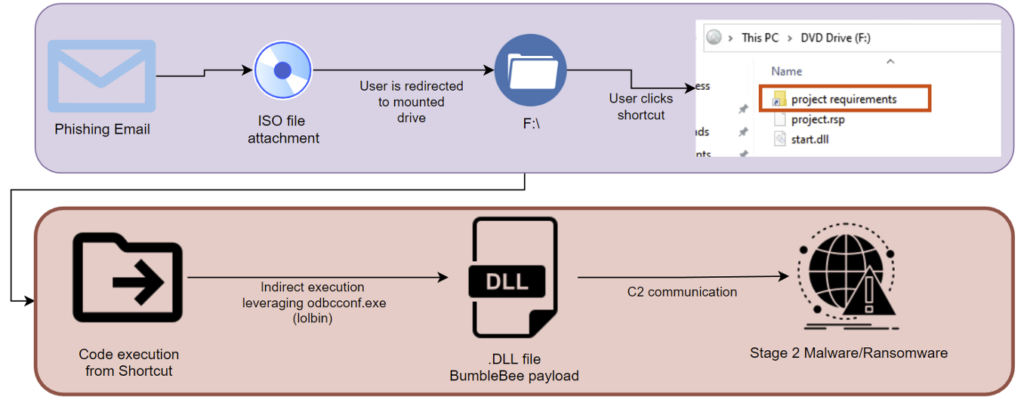
Figure 2
The project requirements.lnk file leverages a technique that executes code within the shortcut file itself. This technique is not new and has been employed by other loaders including Qbot, Emotet, and Icedid. What makes Bumblebee unique is that this particular loader leverages a known LOLbas (living off the land) technique that uses the Microsoft signed binary “odbcconf.exe” to run a specified DLL file.
ODBCconf is a Microsoft signed binary that is used to configure ODBC drivers and sources. It accepts the flag “/f” which an attacker can leverage to import a response file ending in the .rsp extension. These files can act as a pointer file to a .DLL file and contain a simple instruction set which in one particular sample was “REGSVR start.dll”.
In this case, the DLL is present alongside the shortcut. The RSP file is a pointer file needed to carry out the indirect command execution by odbcconf.exe.
We can see this inside the shortcut file’s header in figure 3 below:
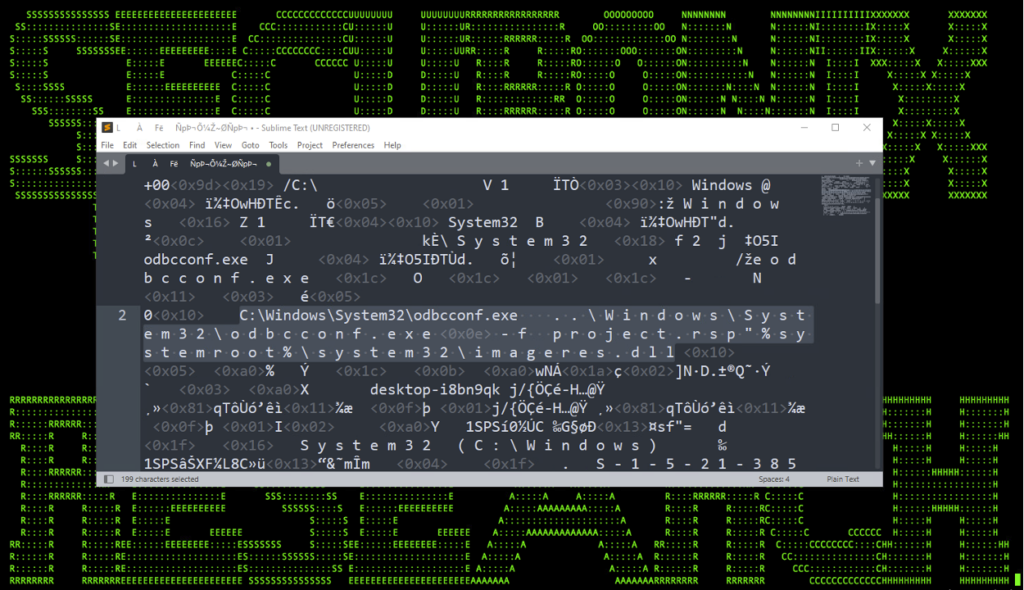
Figure 3
After cleaning up the code a bit, we can see the LOLbin technique which uses odbcconf.exe a bit easier:
C:\Windows\System32\odbcconf.exe ..\Windows\System32\odbcconf.exe -f project.rsp
BumbleBee loader: impact
The sole purpose of any piece of malware that is classified as a “loader” is to provide for initial compromise to a target system. Once the loader has successfully breached the system’s defenses, the original goal of the attacker is carried out. This end goal could be ransomware or even a Cobalt Strike beacon which could allow for data exfiltration or lateral movement.
While this particular loader is still very new, evidence linking BumbleBee to specific ransomware groups is becoming more and more apparent. One in particular, Quantum ransomware which adopts a ransomware-as-a-service (RaaS) model for targeting and exploiting organizations, has recently been tied to the new BumbleBee loader.
The Conti ransomware gang, which historically has leveraged the BazarLoader, has recently been shifting to BumbleBee. Conti was one of the more prolific ransomware groups this and last year targeting government agencies, healthcare, and financial institutions.
In addition to delivering ransomware on the target host, implanting a Cobalt Strike beacon is also one of the more common goals attackers will pursue to compromise a host. Cobalt Strike will allow the attacker full command and control on the victim machine which includes the ability to run reconnaissance, move laterally, steal credentials, or eventually deliver ransomware.
Securonix mitigations and recommendations
- When it comes to any type of malware, Securonix strongly recommends that AV definitions as well as operating systems are patched and up to date
- Avoid opening any attachments especially from those that are unexpected or are from outside the organization
- Implement an application whitelisting policy to restrict the execution of unknown binaries
- Restrict the mounting of disk images on endpoints as this is becoming a common attack vector for loader malware
Hashes Analyzed
- dfc5072b4874706e6ebe8c47140dedc6051f8dda92351bdea8996154e6a96ed2
- 70c247eeafac74d7e571465a1ba48d80981922a66dfec0deacb430db97fe53c9
IOC
40.126.50.56
185.62.58.175
3.27.187.15
28.236.100.216
75.72.64.79
156.148.26.226
104.83.15.21
199.236.144.121
6.23.156.239
211.73.200.45
240.230.245.154
209.141.58.141
35.225.143.246
212.151.132.229
163.192.104.228
138.84.254.103
52.100.187.210
74.205.65.255
233.96.129.4
114.35.182.27
103.175.16.116
146.70.106.52
199.89.92.124
11.24.35.141
113.180.124.216
59.22.171.98
132.67.3.106
108.62.118.145
171.44.250.79
72.212.122.103
183.61.204.160
120.192.237.112
97.203.17.22
19.237.111.47
185.99.166.162
230.120.141.53
26.212.209.119
129.22.123.8
149.22.209.252
154.56.0.112
193.79.90.141
237.129.109.124
68.36.136.74
153.11.154.143
70.138.179.40
235.7.231.55
39.19.205.215
212.67.196.127
185.82.152.12
158.148.141.98
180.242.239.7
218.198.206.120
46.98.104.253
172.93.193.187
216.92.5.162
144.178.219.18
Securonix detection policies
- Suspicious DLL Execution Via ODBCconf Process Analytic
Hunting queries
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND destinationprocessname ENDS WITH “odbcconf.exe” AND ((resourcecustomfield1 CONTAINS ” -f ” AND resourcecustomfield1 CONTAINS “.rsp”) OR (resourcecustomfield1 CONTAINS ” /F ” AND resourcecustomfield1 CONTAINS “.rsp”) OR (resourcecustomfield1 CONTAINS ” /A ” AND resourcecustomfield1 CONTAINS “REGSVR”) OR (resourcecustomfield1 CONTAINS ” -a ” AND resourcecustomfield1 CONTAINS “REGSVR”))
Note: If you are an Autonomous Threat Sweeper subscriber, all of the above TTPs have been swept and a summary detection report will be shared with the recipients.
For the latest threat intelligence and updates please refer to our Github page that is updated daily. We also invite you to send your questions regarding critical security advisories to the Securonix Critical Intelligence Advisory team and look forward to being of assistance.
Conclusion
While we are noticing a huge shift from ransomware groups to the new BumbleBee loader we can only posit that its popularity will only continue to rise. It leverages a lesser-known living-off-the-land technique which we highly recommend organizations be on the lookout for (see threat hunting queries below).
Since BumbleBee appears to be particularly adept at avoiding AV detections, we recommend organizations be extra vigilant around phishing email attempts and blocking known malicious file types such as .iso files.
References
[1]: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/bumblebee-loader-cybercrime
[2]: https://lolbas-project.github.io/lolbas/Binaries/Odbcconf/
[4]: https://blog.cyble.com/2022/06/22/quantum-software-lnk-file-based-builders-growing-in-popularity/
[5]:https://blingeach.com/rise-of-lnk-shortcut-information-malware/
[6]: https://docs.microsoft.com/en-us/sql/odbc/odbcconf-exe?view=sql-server-ver16
[8]: https://www.zdnet.com/article/this-new-malware-is-now-at-the-heart-of-the-ransomware-ecosystem/